DNS
Learn about Oracle Database@Azure's managed DNS.
Oracle Database@Azure automatically manages DNS configuration for the VM Cluster. The domain name for the VM Cluster, oraclevcn.com, is preconfigured by the service. Note that Oracle Database@Azure supports custom domain name prefixes, which you can create when provisioning the VM Cluster.
Oracle Database@Azure have following DNS deployment options for Exadata Database, Autonomous AI Database and Exascale Database:
- Default DNS: This is default option where Oracle manages the DNS setup during the provisioning process, which created a record for the VM Cluster, and the scan uses the
*.oraclevcn.comFQDN. - Custom DNS: This option allows customer to specify any FQDN of their choice during the provisioning process, which require private DNS resolver under private views.
Oracle Database@Azure has the following DNS deployment options for the Network Anchor service:
- Enable Inbound DNS (OCI → Azure): Traffic originating from Database instance running in OCI resolving the DNS in Azure or on-premises
- Enable Outbound DNS (OCI → Azure): Traffic originating from Azure or on-premises resolving DNS for Network Anchor service running in an OCI child site.
- Bidirectional DNS (OCI ↔ Azure): Enable both Inbound and Outbound DNS
Default DNS (oraclevcn.com)
The default OCI domain oraclevcn.com is used for the Oracle Database@Azure deployment. You don't need to create this DNS zone as it's automatically generated and associated with your Azure subscription as a private DNS zone during provisioning. It's the most straightforward approach for environments where a custom domain isn't required.
Configuration on the Azure Portal
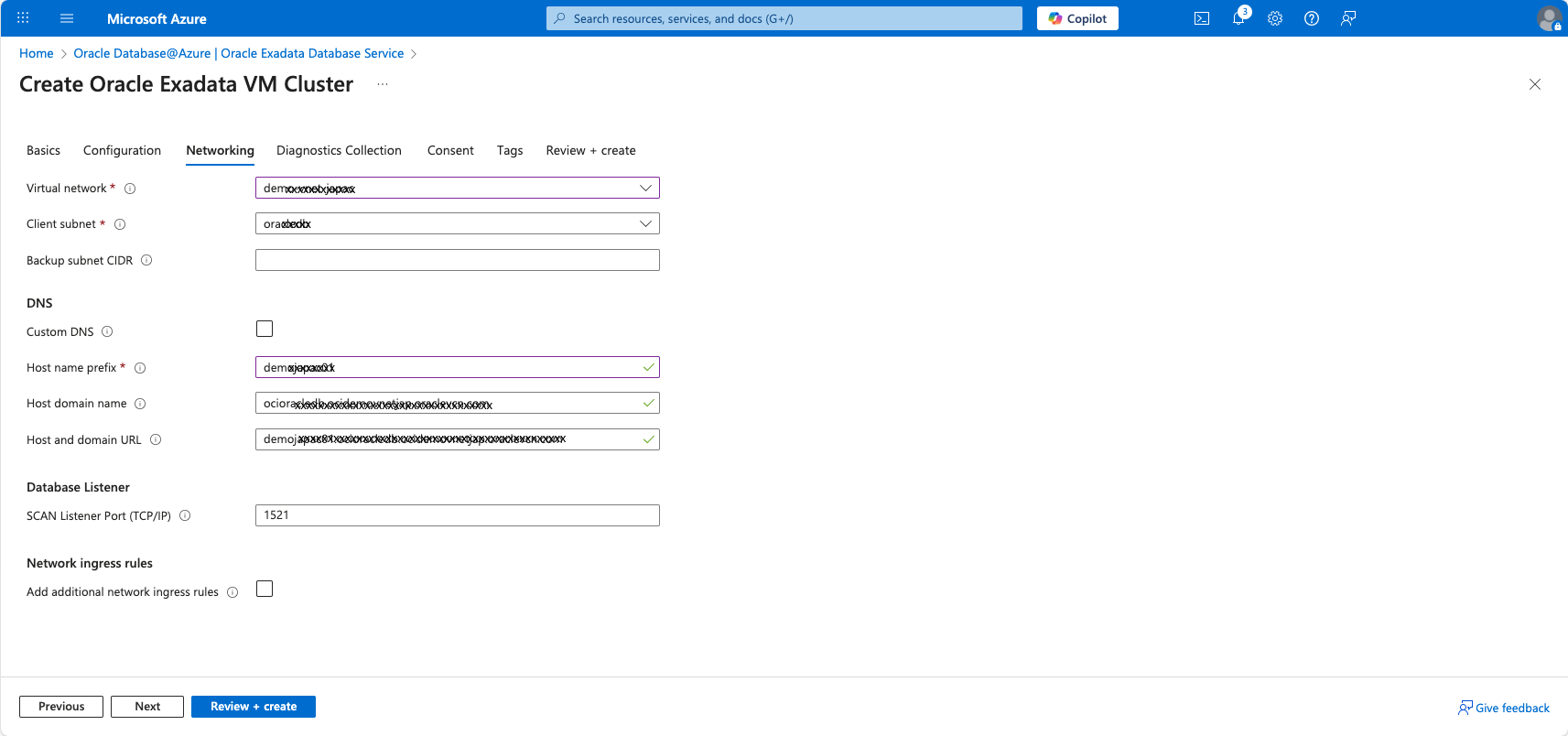
- Prepare Virtual Network (VNet): Create the VNet for Oracle Database@Azure with either Azure provided default DNS or custom DNS.
- Provision Oracle Database@Azure:
- Navigate to the Oracle Database@Azure blade to begin provisioning the infrastructure and Exadata VM Cluster.
- Provide a Hostname prefix (for example,
oradb) which is used for the logical database name. - Accept the system-generated default names for other settings.
- Automatic DNS Provisioning: During the deployment, the service automatically creates an Azure Private DNS Zone for oraclevcn.com and a virtual network link to the Oracle Database@Azure VNet.
Custom DNS
A custom DNS domain is used for all Oracle Database@Azure resources, integrating them into your existing corporate namespace when you need to use your organization's own DNS domain (for example, oradb.prod.dnsdemo.xyz) for the Oracle Database@Azure deployment.
Configuration on the OCI Console (Pre-Deployment):
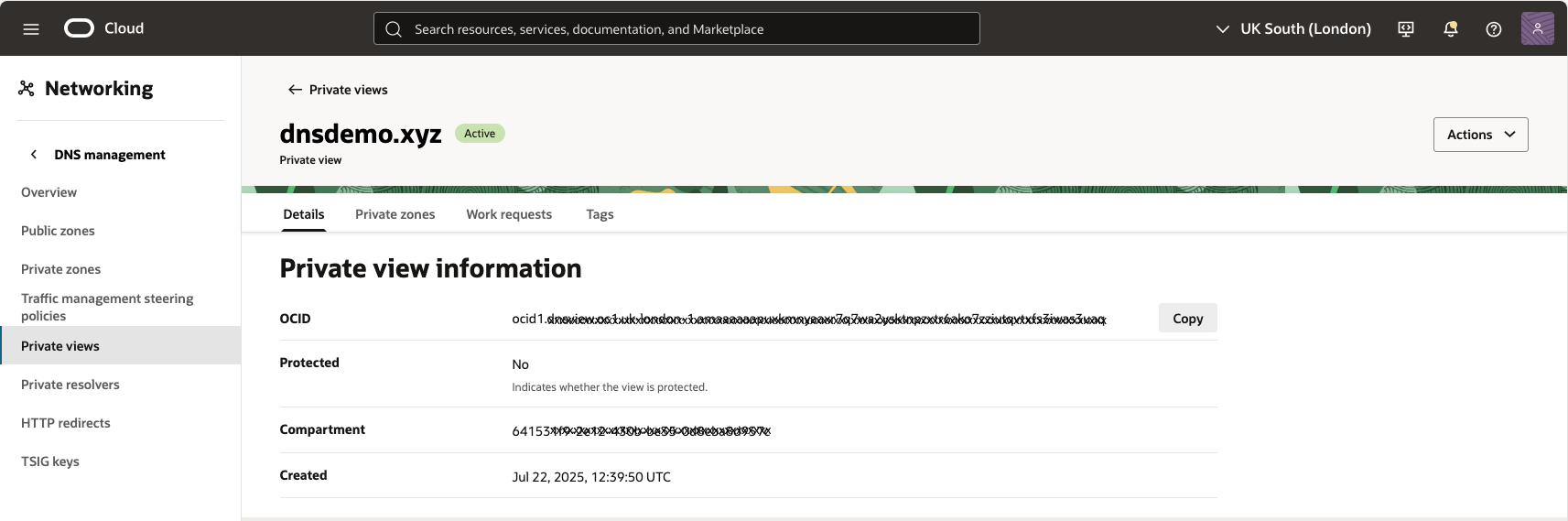
- Navigate to your OCI tenancy and the compartment designated for Oracle Database@Azure.
- Go to Networking > DNS Management > Private Views.
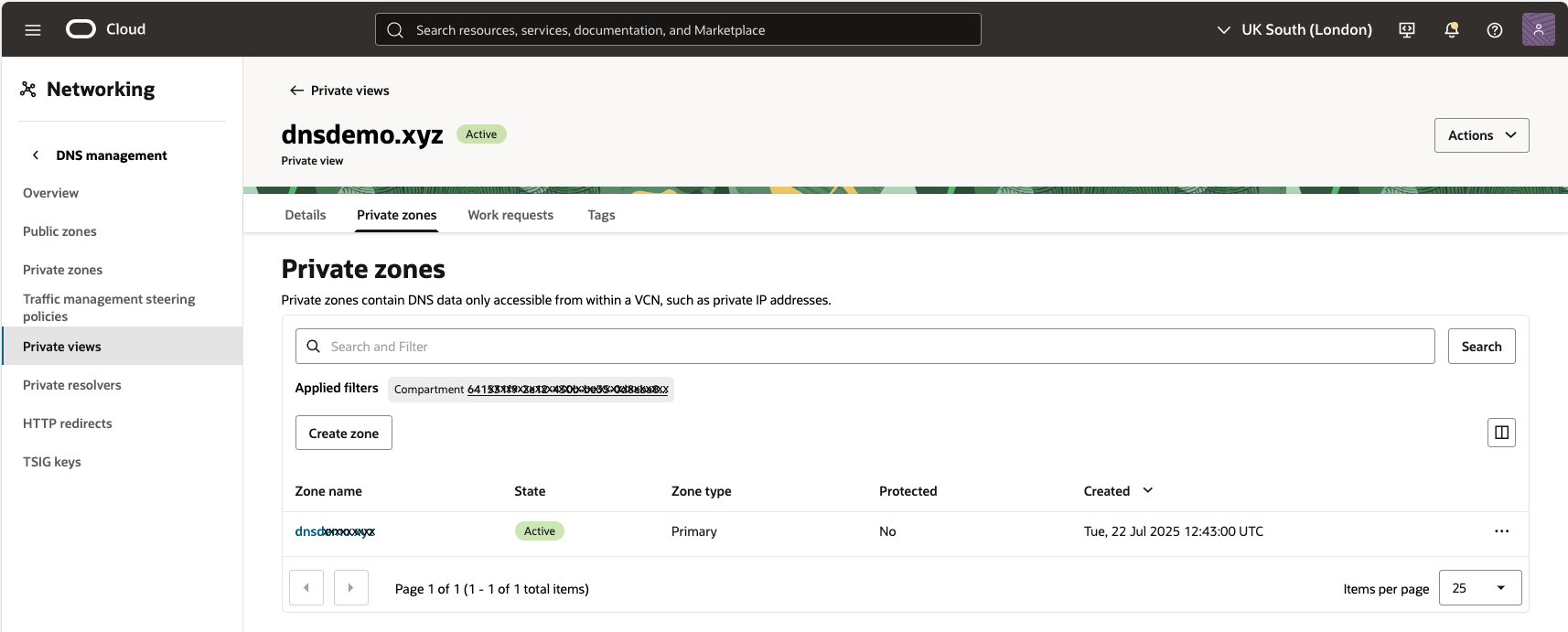
- Create a Private DNS Zone for your custom domain (for example,
oradb.prod.dnsdemo.xyz). This zone is used by Oracle Database@Azure to resolve external DNS names, including other Azure resources. You can add multiple zones and views as needed.
Configuration on the Azure Portal (Deployment):
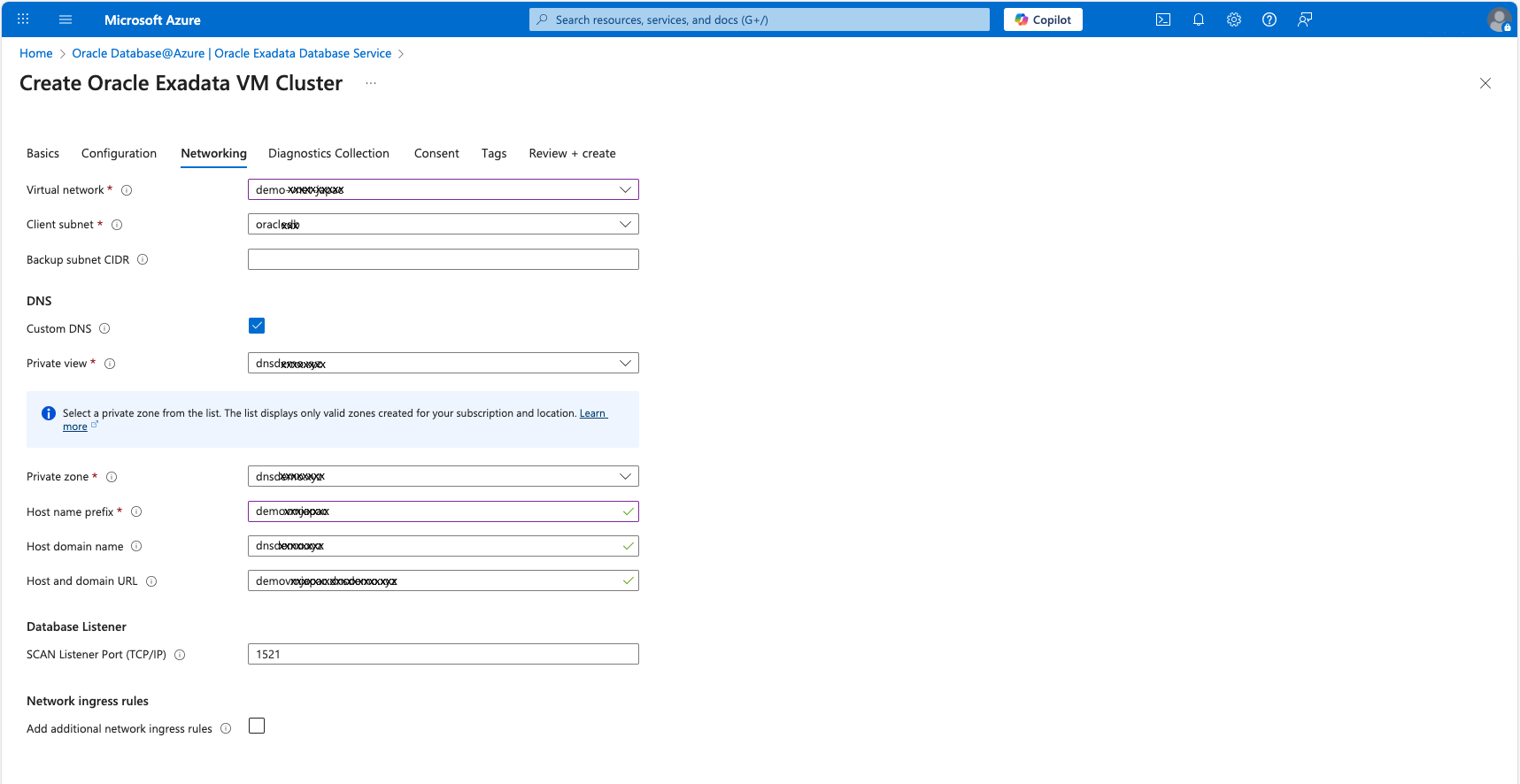
- Prepare Virtual Network (VNet): Create and configure the VNet for Oracle Database@Azure. Set its DNS servers to Custom or Azure-provided based on your environment's needs.
- Provision Oracle Database@Azure:
- From the Oracle Database@Azure blade, begin provisioning the infrastructure and Exadata VM Cluster.
- During configuration, select the Use custom DNS box.
- From the menu, select the private view containing your custom DNS zone (
oradb.prod.dnsdemo.xyz). - Provide a Hostname prefix (for example,
oradb). The database records is automatically added to your custom domain within OCI.
- Manual DNS Record Duplication: Because custom DNS was selected, the oraclevcn.com private zone will not be created in Azure. You must manually duplicate the DNS records for the Oracle Database@Azure SCAN and VIPs from OCI into your production DNS zone (
oradb.prod.dnsdemo.xyz) managed in Azure or your on-premises DNS servers.
Configuration on the OCI Console (Post-Deployment):
To enable communication from Oracle Database@Azure to other resources, update the OCI private view by adding zones that mirror your Azure private DNS zones or on-premises zones.
DNS Limitations
| Limitation Type | Scope | Description |
|---|---|---|
| OCI service limits (Private DNS) | OCI | Tenancies have limit of 1 Private DNS Zones per subscription. |
| Oracle Database@Azure delegated subnet limit | Oracle Database@Azure / OCI | By default, an OCI tenancy can use up to 5 delegated subnets for Oracle Database@Azure across all VNets in a specific region. This limit (azure-delegated-subnet-count) can be increased via Service Request. |
| Exadata hostname prefix constraints | Oracle Database@Azure Provisioning (Exa) | The hostname prefix specified during VM cluster creation has constraints: max length 23 chars, must start with a letter, alphanumeric and hyphens only, can't be localhost. |
| Exadata cluster name constraints | Oracle Database@Azure Provisioning (Exa) | The cluster name has constraints: max length 11 chars), alphabetic start, letters/numbers/hyphens only (no underscores). |
| Exadata host and domain URL | Oracle Database@Azure Provisioning (Exa) | The host and domain name has constraints: max length 56 chars, combined host name prefix + domain name. |
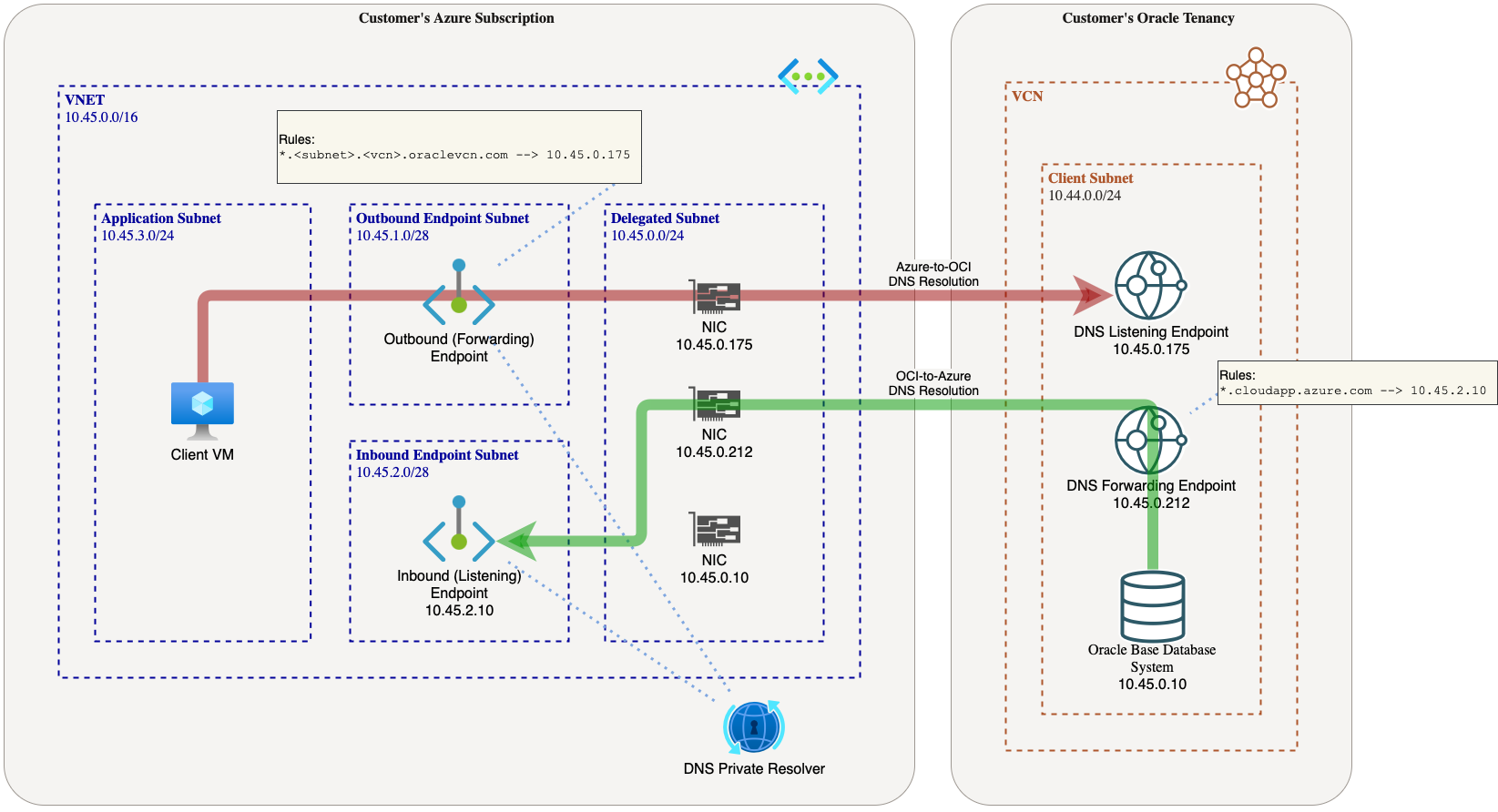
DNS Resolution Options in Network Anchors
Network Anchors provide options to enable DNS resolution between Azure and OCI. You can configure inbound DNS (OCI to Azure), Outbound DNS (Azure to OCI) or enable both directions
This DNS resolution option is only available for Network Anchors applied to Oracle Base Database Service instances in Oracle Database@Azure.
Reference Architecture
Enable Inbound DNS (OCI → Azure)
Inbound DNS allows resources running in an OCI child or parent site, such as databases and database hosts, to resolve hostnames in Azure or on-premises environments.
- As part of the Resource Anchors creation, it provides the option to list of DNS forwarding rules for domains that need to be resolved from OCI to Azure.
- The Network Control Plane performs the following tasks:
- Creates a forwarding DNS endpoint in the network link VCN.
- Adds the forwarding rules you provide.
- Synchronizes DNS Records from OCI to Azure if the outbound DNS isn't enabled.
Enable Outbound DNS (OCI → Azure)
Outbound DNS allows resources on the Azure side ( such as VMs or on-premise systems) to resolve DNS names for Oracle Database@Azure.
- The Network Control plane performs the following tasks:
- Creates a listening DNS Endpoint in the network link VCN.
- Updates the network security group to allow inbound DNS traffic from the VNet CIDR (for example 10.45.0.0/16) using both UDP and TCP on Port 53.
- Exposes the listening endpoint IP address in Network Anchor, which you can access in the Network Anchor overview page.
Note
DNS Records synchronization is skipped when using this option. - After enabling this option:
- You must manually configure outbound DNS rules in Azure for the following domains because different DNS solutions are possible:
- oraclecloud.com
- oraclecloudapps.com
- These rules can be set using any DNS solution available in Azure or on-premises, such as:
- Subnets delegated to Microsoft.Network/dnsResolvers with an Azure DNS private resolver.
- Azure VMs configured as DNS forwarders.
- On-premises DNS servers.
- You must manually configure outbound DNS rules in Azure for the following domains because different DNS solutions are possible:
Bidirectional DNS (OCI ↔ Azure)
Enabling both inbound and outbound DNS provides full bidirectional resolution:
- OCI resources can resolve hostnames in Azure.
- Azure resources can resolve OCI database DNS names.
- Both inbound and outbound configuration steps are applied.
Terminology
The following table lists and describes the terminology used for Network Anchors:
| Name | Description |
|---|---|
| OCI listening DNS endpoint | In OCI, a listening endpoint receives queries from sources within the VCN or other VCN resolvers to resolve the DNS. |
| OCI forwarding DNS endpoint | In OCI, a forwarding endpoint forwards DNS queries to the listening endpoint for resolvers in other peered VCNs or your on-premises network's DNS. |
| Azure inbound DNS endpoint | In Azure, DNS queries sent to the inbound endpoint are resolved using Azure DNS or other DNS resolvers (it's equivalent to OCI listening endpoint). |
| Azure outbound DNS endpoint | In Azure, outbound endpoints egress from Azure (it's equivalent to OCI forwarding endpoint). |
| Azure DNS private resolver | An Azure service that enables you to query Azure DNS private zones from an on-premises environment and vice versa without deploying VM-based DNS servers. |