Prerequisites to Use Customer-Managed Encryption Keys on Autonomous AI Database in OCI Vault
Perform these prerequisite steps to use customer-managed keys on Autonomous AI Database in OCI Vault:
You must replicate the vault and keys to use customer-managed encryption keys with Autonomous Data Guard with a remote Standby database. Customer-Managed Encryption Keys are only supported with a single cross-region Autonomous Data Guard standby. Multiple cross-region standbys are not supported because Oracle Cloud Infrastructure Vault only supports replication to one remote region.
See the following for more information:
- Create Dynamic Group and Policies for Customer Managed Keys with Vault in Same Tenancy as Database
Create dynamic group and policies to provide access to the vault and keys for customer-managed keys when the vault and keys are in the same tenancy as the Autonomous AI Database instance. - Create Dynamic Group and Policies for Customer Managed Keys with Vault in Different Tenancy than the Database
Perform these steps to use customer-managed keys when the Autonomous AI Database instance and vaults and keys are in different tenancies.
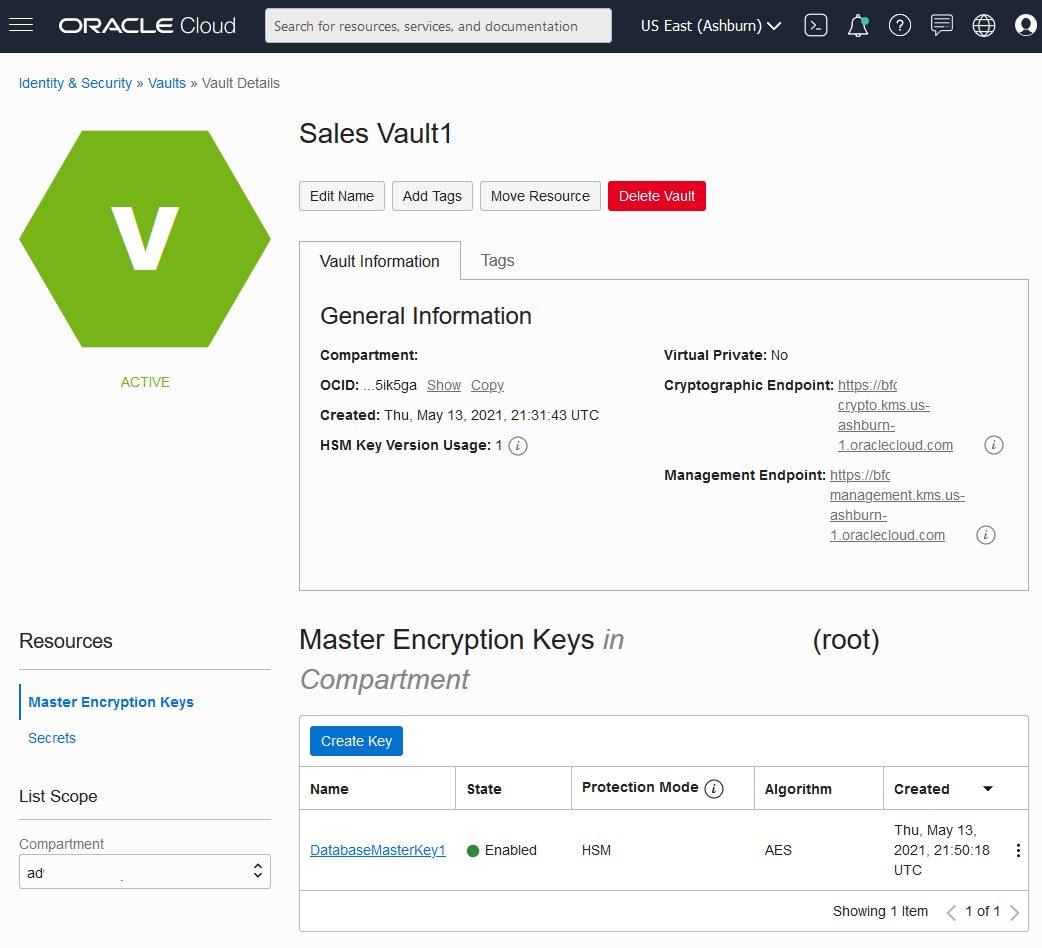
Parent topic: Manage Master Encryption Keys in OCI Vault
Create Dynamic Group and Policies for Customer Managed Keys with Vault in Same Tenancy as Database
Create dynamic group and policies to provide access to the vault and keys for customer-managed keys when the vault and keys are in the same tenancy as the Autonomous AI Database instance.
Create Dynamic Group and Policies for Customer Managed Keys with Vault in Different Tenancy than the Database
Perform these steps to use customer-managed keys when the Autonomous AI Database instance and vaults and keys are in different tenancies.
In this case, you need to supply OCID values when you change to customer-managed keys. In addition, you need to define dynamic groups and policies that allow the Autonomous AI Database instance to use vaults and keys in a different tenancy.
- Copy the master encryption key OCID.
- Copy the vault OCID.
- Copy the tenancy OCID (the remote tenancy that contains vaults and keys).
- On the tenancy with the Autonomous AI Database instance, create a dynamic
group.
- On the tenancy with the Autonomous AI Database instance, define the
policies to allow access to vaults and keys (where the
vaults and keys are on a different tenancy).
- Copy the tenancy OCID (the tenancy that contains the Autonomous AI Database instance).
- Copy the Dynamic Group OCID (for the Dynamic Group you created in Step 4).
- On the remote tenancy with vaults and keys, define a dynamic
group and policies to allow the Autonomous AI Database instance to access vaults and
keys.