Connect to Data Integration
Before you use Data Integration, a user with administrator privileges configures security and networking, and then creates workspaces for different data integration solutions, for example, staging, testing, and production scenarios.
In this tutorial, you:
- Create access policies for users who don't have administrative privileges.
- Create a workspace for the Data Integration resources that you create and use.
- Get the workspace OCID to create the policies you need to restrict access to that workspace.
Before You Begin
To create a Data Integration workspace, you must have the following:
- An Oracle Cloud Infrastructure account with administrator privileges. Sign up for Oracle Cloud Infrastructure.
- A compartment
- A virtual cloud network (VCN) with at least one regional subnet
- A group for users in charge of a workspace
- Access to the Data Integration service.
1. Creating Access Policies
2. Creating a Workspace
- In the Oracle Cloud Infrastructure Console navigation menu, navigate to Analytics & AI. Under Data Lake, select Data Integration.
- Click Workspaces.
- Under List Scope, from the Compartment menu, select the compartment in which you created policies in the previous section.
- Click Create workspace.
-
In the Create workspace panel, complete the fields as follows, and then click Create:
3. Getting Workspace OCID to Create Policies
To create the policies that you need and restrict the policies at the workspace level, you need the workspace OCID.
To get the workspace OCID, perform either of the following procedures:
- From the Workspaces page, select the Actions menu (
 ) corresponding to the workspace, and then select Copy OCID.
) corresponding to the workspace, and then select Copy OCID.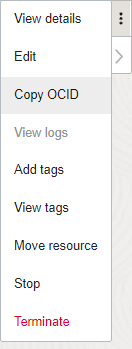
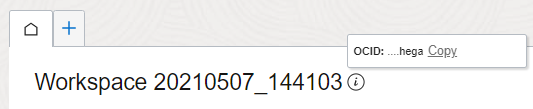
- From the Home tab in a workspace, click the Copy link in the tip that's next to the workspace name.
Additional Resources
What's Next
After the workspace is created, you can: