Configuring SSL on the IBM HTTP Server
SSL requires a Signed Personal Certificate. You can either request a CA-Signed Personal Certificate directly from IBM, or you can generate a Self-Signed Certificate yourself. This task describes how to generate and use a Self-Signed Certificate. For production environments, we recommend you request one from CA. For instructions to request a CA-Signed Personal Certificate, refer to the IBM Info Center.
Create a folder named
keysin the HTTP Server installation directory.Start the Key Management Utility by navigating the following path:
Start > Programs > IBM HTTP Server > Start Key Management Utility
Alternately you can use a script found in this directory
Z:\IBM\HTTPServer\binStart the
ikeyManutility which is located in the bin directory of your HTTP Server. For example:/u01/IBM/WebSphere/AppServer/binIn the IBM Key ManagementikeyMan utility, create a Key Database File by navigating Key Database File > New.
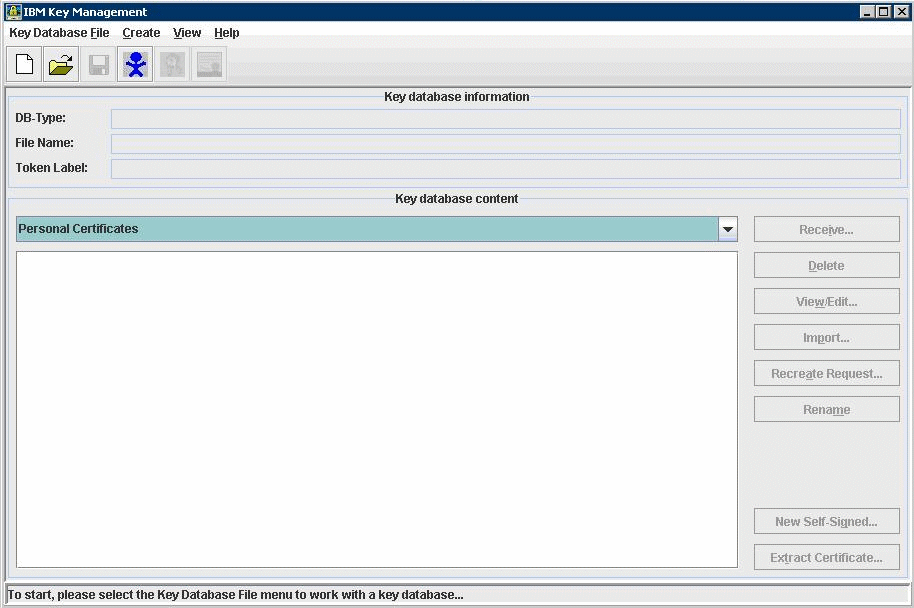
At the prompt, enter the following information:
Key Database Type = CMS
Only CMS is supported with the IBM HTTP Server.
File Name = serverkey.kdb
Location =
x:\IBM\HTTPServer\keys/u01/IBM/HTTPServer/keyswhere
x:is the drive on which you installed the IBM HTTP Server.
Enter the password (for example, "serverkey") and select the option stash the password file.
Click the OK button.
From the drop down box, select Personal Certificates.
Click New Self-Signed.
Enter following information on the screen that appears:
Key Label= Enter any label (for example, server_cert)
Version= X509V3
Key Size = 1024
Common Name = Fully Qualified Server Name (for example, denicint2.mlab.jdedwards.com)
Organization = your organization name (for example, Oracle).
Country or region = US
Validity Period = 365 days
A sample screen shot is provided below:
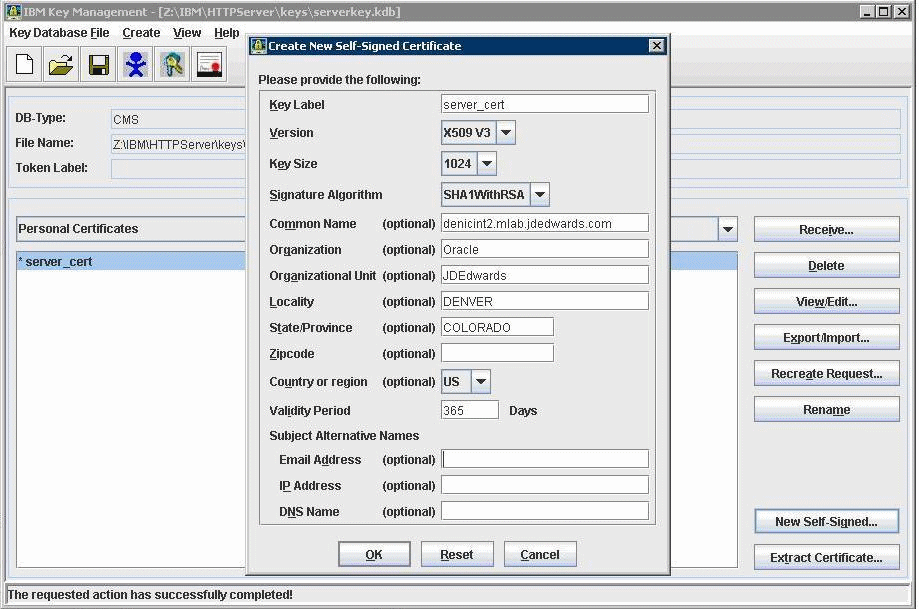
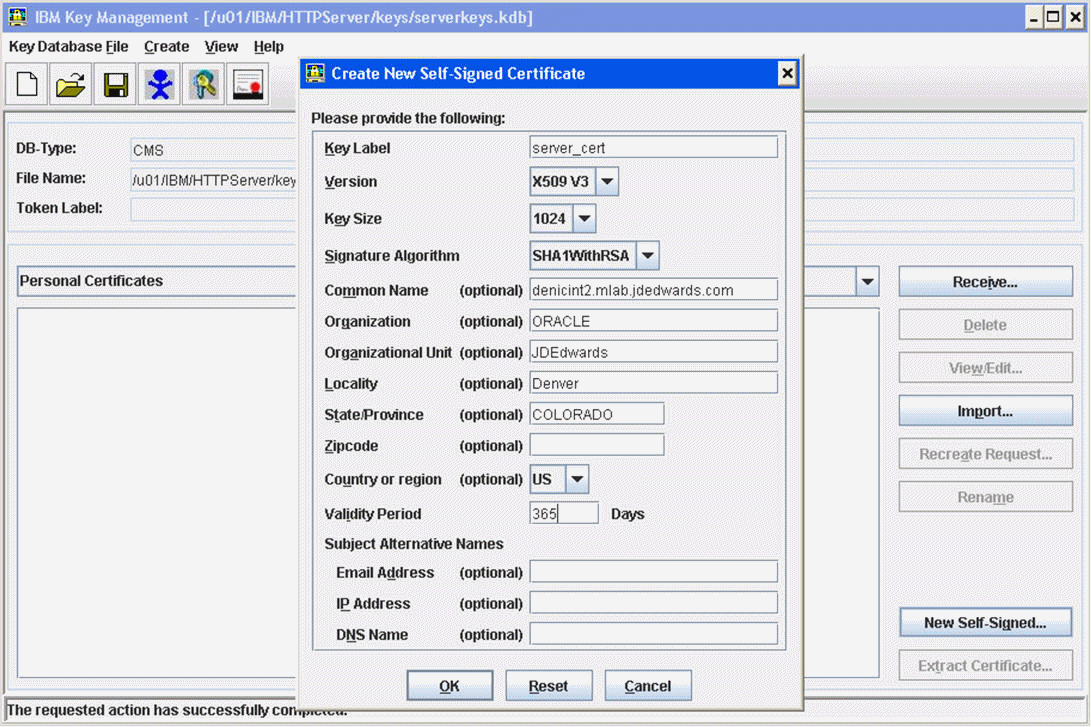
On Create New Self-Signed Certificate, after the fields are complete click the OK button.
The program displays your certificate in the list.
Delete all the other certificates.
Open the
httpd.conffile in a text editor, and add the following virtual host definition.Note: The text in thehttpd.confis case sensitive; type the host definition exactly as shown.If you have already configured a port on the HTTP Server (for example, port 91), the file will include an Alias. Use the same alias under your Virtual Host definition as described here.
ServerKey
For version 8.5.x. make the changes listed below:
# Example SSL configuration which supports SSLv3 and TLSv1 # To enable this support: # 1) Create a key database with ikeyman # 2) Update the KeyFile directive below to point to that key database # 3) Uncomment the directives up through the end of the example # Note: The IPv6 Listen directive must only be uncommented if # IPv6 networking is enabled. # # uncomment below line to enable ssl LoadModule ibm_ssl_module modules/mod_ibm_ssl.so <IfModule mod_ibm_ssl.c> Listen 0.0.0.0:443 # IPv6 support: # Listen [::]:443 <VirtualHost *:443> Alias /jde "/u01/IBM/WebSphere/AppServer/profiles/AppSrv02/installedApps/denicint2Node01Cell/EA_JS_9x.ear/webclient.war" SSLEnable SSLProtocolDisable SSLv2 </VirtualHost> <Directory "/u01/IBM/WebSphere/AppServer/profiles/AppSrv02/installedApps/denicint2Node01Cell/EA_JS_9x.ear/webclient.war/WEB_INF"> Order Deny,Allow Deny from All </Directory> <Directory "/u01/IBM/WebSphere/AppServer/profiles/AppSrv02/installedApps/denicint2Node01Cell/EA_JS_9x.ear/webclient.war"> Order Deny,Allow Allow from All </Directory> </IfModule> KeyFile /u01/IBM/HTTPServer/keys/WebServerKeys.kdb SSLDisable # End of example SSL configuration
ServerKey
For version 8.5.x. make the changes listed below:
# Example SSL configuration which supports SSLv3 and TLSv1 # To enable this support: # 1) Create a key database with ikeyman # 2) Update the KeyFile directive below to point to that key database # 3) Uncomment the directives up through the end of the example # Note: The IPv6 Listen directive must only be uncommented if # IPv6 networking is enabled. # # uncomment below line to enable ssl LoadModule ibm_ssl_module modules/mod_ibm_ssl.so <IfModule mod_ibm_ssl.c> Listen 0.0.0.0:443 # IPv6 support: # Listen [::]:443 <VirtualHost *:443> Alias /jde "Z:\IBM\WebSphere\AppServer\profiles\AppSrv02\installedApps\denicint2Node01Cell\EA_JS_9x.ear\webclient.war" SSLEnable SSLProtocolDisable SSLv2 </VirtualHost> <Directory "Z:\IBM\WebSphere\AppServer\profiles\AppSrv02\installedApps\denicint2Node01Cell\EA_JS_9x.ear\webclient.war\WEB_INF"> Order Deny,Allow Deny from All </Directory> <Directory "Z:\IBM\WebSphere\AppServer\profiles\AppSrv02\installedApps\denicint2Node01Cell\EA_JS_9x.ear\webclient.war"> Order Deny,Allow Allow from All </Directory> </IfModule> KeyFile Z:\IBM/HTTPServer\keys\WebServerKeys.kdb SSLDisable # End of example SSL configuration
For version 9.x onward make the changes listed below:
# Example SSL configuration # To enable this support: # 1) Create a key database with ikeyman # 2) Update the KeyFile directive below to point to that key database # 3) Uncomment the directives up through the end of the example # Note: The IPv6 Listen directive must only be uncommented if # IPv6 networking is enabled. # # uncomment below line to enable ssl LoadModule ibm_ssl_module modules/mod_ibm_ssl.so <IfModule mod_ibm_ssl.c> # IPv6 support: Listen 0.0.0.0:443 <VirtualHost *:443> Alias /jde "/u01/IBM/WebSphere/AppServer/profiles/AppSrv02/installedApps/denicint2Node01Cell/EA_JS_9x.ear/webclient.war" SSLEnable </VirtualHost> <Directory "/u01/IBM/WebSphere/AppServer/profiles/AppSrv02/installedApps/denicint2Node01Cell/EA_JS_9x.ear/webclient.war/WEB_INF"> Require all denied </Directory> <Directory "/u01/IBM/WebSphere/AppServer/profiles/AppSrv02/installedApps/denicint2Node01Cell/EA_JS_9x.ear/webclient.war"> Require all granted </Directory> </IfModule> SSLDisable KeyFile /u01/IBM/HTTPServer/keys/ServerKey.kdb # End of example SSL configuration
For version 9.x onward make the changes listed below:
# Example SSL configuration # To enable this support: # 1) Create a key database with ikeyman # 2) Update the KeyFile directive below to point to that key database # 3) Uncomment the directives up through the end of the example # Note: The IPv6 Listen directive must only be uncommented if # IPv6 networking is enabled. # # uncomment below line to enable ssl LoadModule ibm_ssl_module modules/mod_ibm_ssl.so <IfModule mod_ibm_ssl.c> # IPv6 support: Listen 0.0.0.0:443 <VirtualHost *:443> Alias /jde "Z:\IBM\WebSphere\AppServer\profiles\AppSrv02\installedApps\denicint2Node01Cell\EA_JS_9x.ear\webclient.war" SSLEnable </VirtualHost> <Directory "Z:\IBM\WebSphere\AppServer\profiles\AppSrv02\installedApps\denicint2Node01Cell\EA_JS_9x.ear\webclient.war\WEB_INF"> Require all denied </Directory> <Directory "Z:\IBM\WebSphere\AppServer\profiles\AppSrv02\installedApps\denicint2Node01Cell\EA_JS_9x.ear\webclient.war"> Require all granted </Directory> SSLDisable KeyFile Z:\IBM/HTTPServer\keys\WebServerKeys.kdb # End of example SSL configuration