- Administering Oracle Cloud Identity Management
- Managing Oracle Single Sign-On
- Configuring Oracle Cloud as the Service Provider
Configuring Oracle Cloud as the Service Provider
To configure SSO, start with configuring Oracle Cloud as service provider.
To configure SAML 2.0 SSO between Oracle Cloud as service provider and the identity provider:
- Go to the My Services dashboard page and click Users. Then click the SSO Configuration tab.
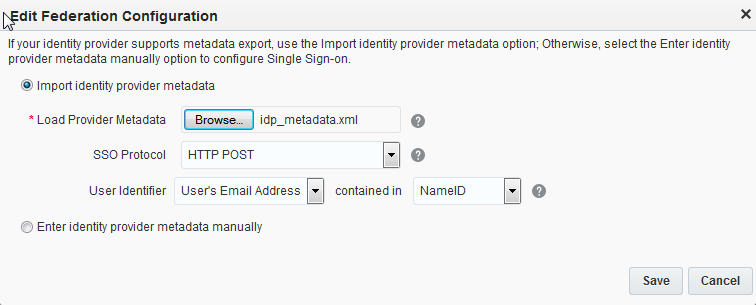
- Click Configure SSO.The Configure SSO page is displayed.
- Select whether to import identity provider metadata or enter provider the metadata manually. Your choice depends on whether your identity provider can export metadata.
- The next step depends on the selection that you made in Step 3.
- If your Identity Provider can export metadata, then you can import the metadata into Oracle Cloud. Select Import Identity Provider metadata. Click Choose File and upload the identity provider metadata file (such as idp_metadata.xml).
- For the SSO Protocol field, HTTP POST is recommended and is the default. The SSO Protocol field value refers to the SAML binding that’s used. SAML bindings define how the SAML protocols map to the type of transport used. Oracle Cloud supports HTTP POST and HTTP Artifact. The HTTP POST binding defines how SAML protocol messages can be transported with the base64-encoded content of a form control within an HTML form. The HTTP Artifact binding defines how a reference (or artifact) to a SAML request or response is transported over HTTP; the artifact (a small representation of a complete SAML assertion) can be embedded in a URL as a query string parameter, or it can be placed in a hidden form control.
- Select the User Identifier field. The user identifier is the Oracle LDAP directory attribute that’s used to map the user information contained in the incoming SSO SAML assertion to an Oracle Cloud user. It’s either the user's email address or the user ID. Select User's Email Address.
- Select the contained in field. If the User Identifier is the user's email address, then the contained in field must be NameID.
Note:
If the User Identifier value is the user ID, then the contained in field must be the SAML attribute and you must specify the name of the SAML attribute for the contained in field such as SamAccountName in the case of Microsoft Active Directory Federation Services.
- Click Save.
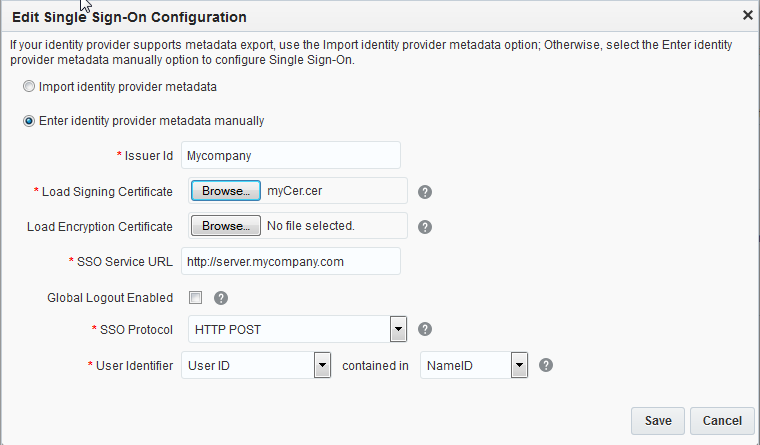
- If your identity provider can’t export metadata, then you must enter metadata information manually, which means you must also provide the Issuer ID and SSO Service URL (this is the SAML assertion consumer URL), and indicate whether Global logout should be enabled. You must also load your identity provider’s signing certificate and encryption certificate.