Managing Security Lists
About Security Lists
A security list is a group of Compute Classic instances that you can specify as the source or destination in one or more security rules. The instances in a security list can communicate fully, on all ports, with other instances in the same security list using their private IP addresses.
When you add an instance to a security list, the inbound and outbound policies of the security list are applicable to that instance.
- The inbound policy controls the flow of traffic into the security list. The inbound policy is always set to
deny, so by default traffic from any source outside the security list can’t access the instances that are part of the security list. - The outbound policy controls the flow of traffic out of the security list. For example, if the outbound policy is set to
deny, packets can’t flow out of the security list. To allow instances in a security list to communicate with hosts outside the security list, set the outbound policy topermit.
By default, a security list has its inbound policy set to deny and outbound policy set to permit. However, you can specify a different outbound policy when you create a security list. If you specify the outbound policy as deny, then you can set up security rules to override that policy. Similarly, you can create security rules to permit inbound traffic from specified sources, over specified protocols and ports, to the instances in that security list.
Note:
A security rule acts only on a policy that is set to deny. If a security list has its outbound policy set to permit (the default), then you don’t need to define security rules to enable outbound traffic from instances in that security list.
When you create a security rule, you can specify a security list as a source or destination in that security rule. A security list can be specified as the source or destination in up to 10 security rules.
The following diagram shows the relationship between instances and security lists.
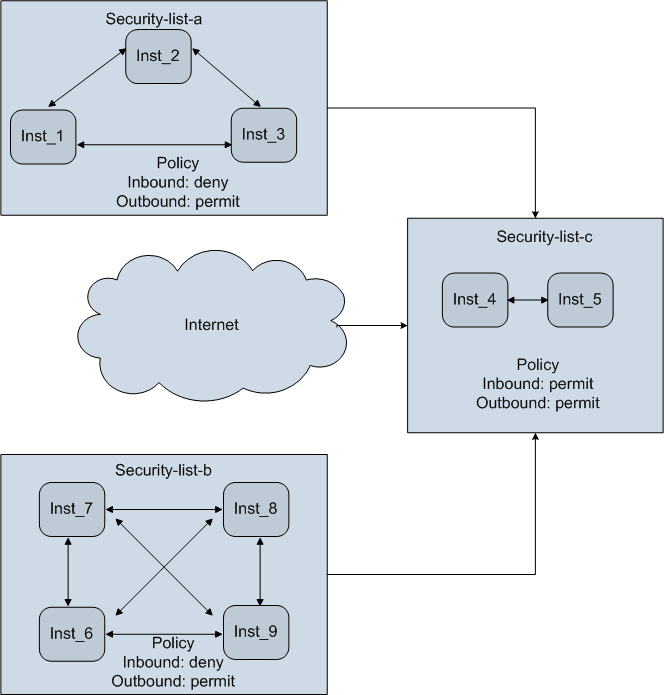
-
Security-list-chas the inbound policy set topermit. So traffic from the other security lists can reach the instances in this security list, as indicated by the arrows. Traffic from the Internet can also reach the instances in this security list.Note:
The web console doesn’t allow you to specify the inbound policy as
permit. This is because setting the inbound policy topermitin effect disables the firewall. If you need to specify this inbound policy, use thePUTorPOST/seclist/API method, or theopc compute security-list addoropc compute security-list updateCLI command. -
For
Security-list-aandSecurity-list-b, the inbound policy isdeny. So the instances in these security lists can’t receive traffic from any host outside their security lists.
You can add an instance to up to five security lists.
Note:
If an instance is added to multiple security lists that have different policies, then the most restrictive policy is applicable to the instance. For example, in the previous diagram, Inst_4 is in Security-list-c, which has the inbound policy permit. If you were to add Inst_4 to Security-list-b as well (inbound policy is deny), then the effective inbound policy for Inst_4 would be deny.
Remember, however, that all instances in a security list can communicate with each other across all protocols and ports. So in this scenario, Inst_4 would be able to communicate with Inst_5 in Security-list-c, as well as with Inst_6, Inst_7, Inst_8, and Inst_9 in Security-list-b.
Creating a Security List
A security list is a group of Compute Classic instances that you can specify as the source or destination in one or more security rules. The instances in a security list can communicate fully, on all ports, with other instances in the same security list using their private IP addresses.
To complete this task, you must have the Compute_Operations role. If this role isn’t assigned to you or you’re not sure, then ask your system administrator to ensure that the role is assigned to you in Oracle Cloud Infrastructure Classic Console. See Modifying User Roles in Managing and Monitoring Oracle Cloud.
- Sign in to the Compute Classic console. If your domain spans multiple sites, select the appropriate site. To change the site, click the Site menu near the top of the page.
- Click the Network tab.
- In the Network drop-down list, expand Shared Network, and then click the Security Lists.
- Click Create Security List.
- Enter or select the required details—a name and description, and the inbound and outbound policies—and click Create.
To create a security list using the CLI, use the opc compute sec-list add command. For help with that command, run the command with the -h option. For the instructions to install the CLI client, see Preparing to Use the Compute Classic CLI in CLI Reference for Oracle Cloud Infrastructure Compute Classic.
To create a security list using the API, use the POST /seclist/ method. See REST API for Oracle Cloud Infrastructure Compute Classic.
You can also create a security list by using an orchestration. See Orchestration v1 Attributes Specific to Each Object Type or Orchestration v2 Attributes Specific to Each Object Type.
Updating a Security List
After creating a security list, at any time, you can update it to change its description as well the inbound and outbound policies.
Prerequisites
-
To complete this task, you must have the
Compute_Operationsrole. If this role isn’t assigned to you or you’re not sure, then ask your system administrator to ensure that the role is assigned to you in Oracle Cloud Infrastructure Classic Console. See Modifying User Roles in Managing and Monitoring Oracle Cloud.
Note:
You should always use your orchestrations to manage resources that you’ve created using orchestrations. Don’t, for example, use the web console or the CLI or REST API to update an object that you created using an orchestration. This could cause your orchestration to either attempt to re-create the object and associated resources, or to go into an error state. See Workflows for Updating Orchestrations v2.
- Sign in to the Compute Classic console. If your domain spans multiple sites, select the appropriate site. To change the site, click the Site menu near the top of the page.
- Click the Network tab.
- In the Network drop-down list, expand Shared Network, and then click the Security Lists.
- Identify the security list that you want to update. From the
 menu, select Update.
menu, select Update. - Make the required changes, and click Update.
To update a security list using the CLI, use the opc compute sec-list update command. For help with that command, run the command with the -h option. For the instructions to install the CLI client, see Preparing to Use the Compute Classic CLI in CLI Reference for Oracle Cloud Infrastructure Compute Classic.
To update a security list using the API, use the PUT /seclist/name method. See REST API for Oracle Cloud Infrastructure Compute Classic.
Adding an Instance to a Security List
You can add an instance to a security list either when you create the instance or later by updating the instance.
Removing an Instance from a Security List
To prevent other hosts from accessing an instance, you can remove the instance from the security lists that it is attached to. This may be useful when you want to perform maintenance activities, change or upgrade applications, and so on.
See Updating an Instance.
Deleting a Security List
You can delete a security list that isn’t being used by any instance or security rule.
Prerequisites
-
To complete this task, you must have the
Compute_Operationsrole. If this role isn’t assigned to you or you’re not sure, then ask your system administrator to ensure that the role is assigned to you in Oracle Cloud Infrastructure Classic Console. See Modifying User Roles in Managing and Monitoring Oracle Cloud. -
Ensure that no instance is attached to the security list that you want to delete.
-
Ensure that no security rule uses the security list that you want to delete.
Note:
You should always use your orchestrations to manage resources that you’ve created using orchestrations. Don’t, for example, use the web console or the CLI or REST API to delete an object that you created using an orchestration. This could cause your orchestration to either attempt to re-create the object and associated resources, or to go into an error state.
If you created the object using orchestration v1, then you can delete the object by terminating the orchestration. See Terminating an Orchestration v1.
If you created the object using an orchestration v2, then you can delete the object by suspending, terminating, or updating the orchestration. See Suspending an Orchestration v2, Terminating an Orchestration v2, or Updating an Orchestration v2.
Procedure
- Sign in to the Compute Classic console. If your domain spans multiple sites, select the appropriate site. To change the site, click the Site menu near the top of the page.
- Click the Network tab.
- In the Network drop-down list, expand Shared Network, and then click the Security Lists.
- Identify the security list that you want to delete. From the
 menu, select Delete.
menu, select Delete.
To delete a security list using the CLI, use the opc compute sec-list delete command. For help with that command, run the command with the -h option. For the instructions to install the CLI client, see Preparing to Use the Compute Classic CLI in CLI Reference for Oracle Cloud Infrastructure Compute Classic.
To delete a security list using the API, use the DELETE /seclist/name method. See REST API for Oracle Cloud Infrastructure Compute Classic.