2 Prepare to Migrate DevCS to Oracle Cloud Infrastructure
Before you migrate your service instance from Traditional to Oracle Cloud Infrastructure (OCI), you should create and configure required resources, and learn about the required identity domain roles for the migration.
In this documentation, DevCS on Traditional is referred as the source DevCS instance and DevCS on OCI is referred as the target DevCS instance. A project in the source or target DevCS instance is referred as the source project or the target project.
To prepare for migration, you'll do the following:
- Migrate users and roles from Traditional to Identity Cloud Service
- Assign the required identity domain roles to yourself in the source and the target Oracle Cloud account
- Create the target DevCS instance in the OCI region
- Set up the required OCI connections in the target Oracle Cloud account
- Set up an OCI Object Storage bucket in the target Oracle Cloud account.
You'll use the bucket to export the data of the source DevCS projects.
Migrate Users and Roles
You can migrate traditional cloud accounts to cloud accounts with Identity Cloud Service by migrating users and their roles. Make sure that you have administrative privileges to export users and role memberships from the traditional cloud account and to import users and role memberships in Oracle Identity Cloud Service.
To migrate users and roles, see Migrating Users, Migrating Role Memberships, and Migrating Identity Domain Administrator Roles in Administering Oracle Identity Cloud Service. To learn about how DevCS roles are mapped between a traditional cloud account and Identity Cloud Service, see Mapping Between Traditional Cloud Roles and Application Roles in Oracle Identity Cloud Service.
Required Identity Domain Roles
Make sure you're assigned the identity domain roles required for the migration.
| You need this role: | To: |
|---|---|
DEVCS_APP_ENTITLEMENT_ADMINISTRATOR (Administrator Role for Developer Cloud Service Provisioning)
|
Create the target DevCS instance
You need this role in the target Oracle Cloud account. |
DEVELOPER_ADMINISTRATOR (Developer Service Administrator)
|
Get VMs and VM templates details from the source DevCS instance and create them in the target DevCS instance
You need this role in the source as well as the target Oracle Cloud account. |
OCI_Administrator (OCI Administrator)
|
Set up the OCI account
You need this role in the target Oracle Cloud account. |
To find out how to grant an identity domain role, see Add Users, Assign Policies and Roles in Getting Started with Oracle Cloud.
Create the Target DevCS Instance in the OCI Region
If your source and target instances are located in the same Oracle Cloud account, remember that they can't have identical instance names.
Set Up the OCI Connections on the Target Oracle Cloud Account
After creating the target DevCS instance, set up your target Oracle Cloud account to host DevCS resources and connect to OCI Compute and OCI Object Storage. DevCS runs builds on OCI Compute VMs, and stores build and Maven artifacts on the OCI Object Storage buckets.
Set Up the OCI Account
Get the Required OCI Input Values
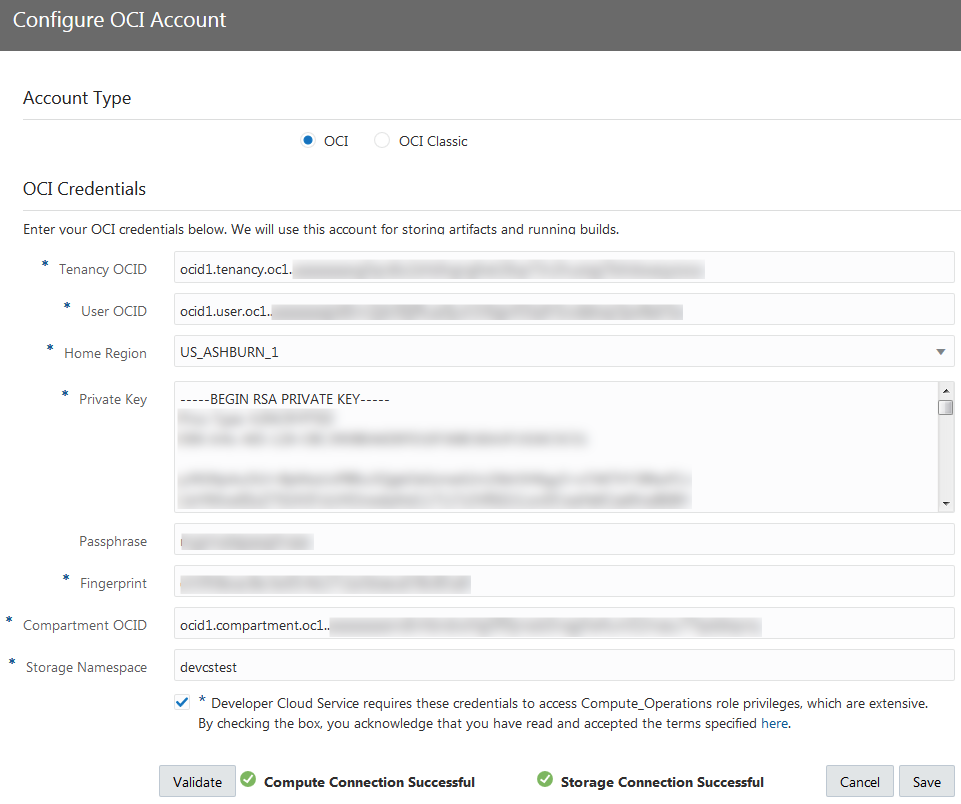
Every Oracle Cloud Infrastructure resource has an Oracle-assigned unique ID called an Oracle Cloud Identifier (OCID). To connect to OCI, you need the account's tenancy OCID, home region, the compartment's OCID that hosts DevCS resources, and the OCID and fingerprint of the user who can access the DevCS compartment. To connect to OCI Object Storage, you need the Storage namespace. You can get these values from the OCI Console pages.
This table describes how to get the OCI input values required for the connection.
| To get these values ... | Do this: |
|---|---|
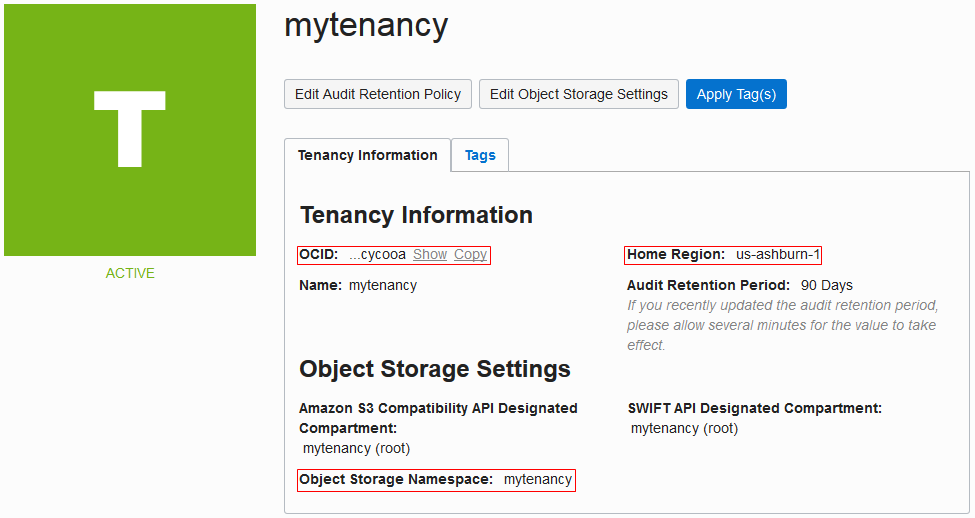
| Tenancy OCID, Home Region, and Storage Namespace | On the OCI console, from the left navigation bar, select Administration > Tenancy Details.
The Tenancy Information tab displays the tenancy OCID in OCID, home region in Home Region, and the storage namespace in Object Storage Namespace. Here's an example: |
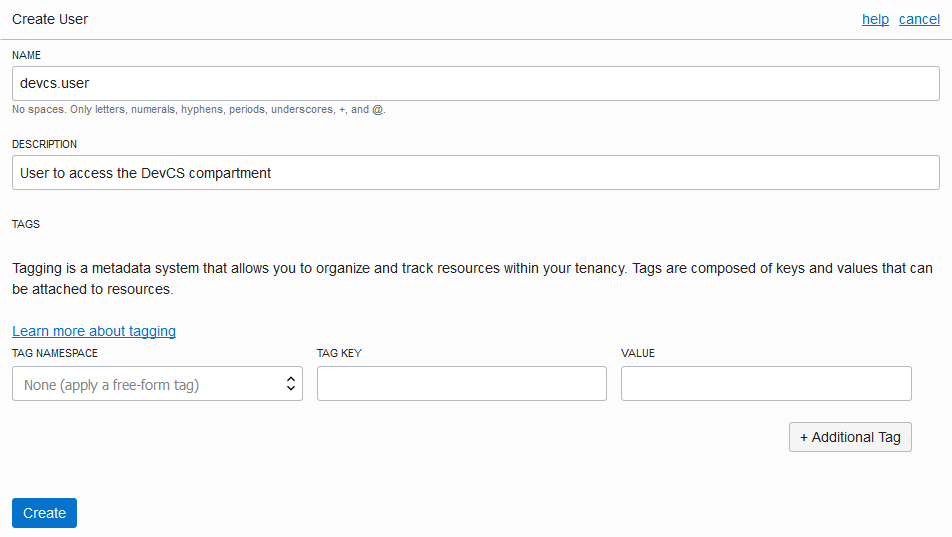
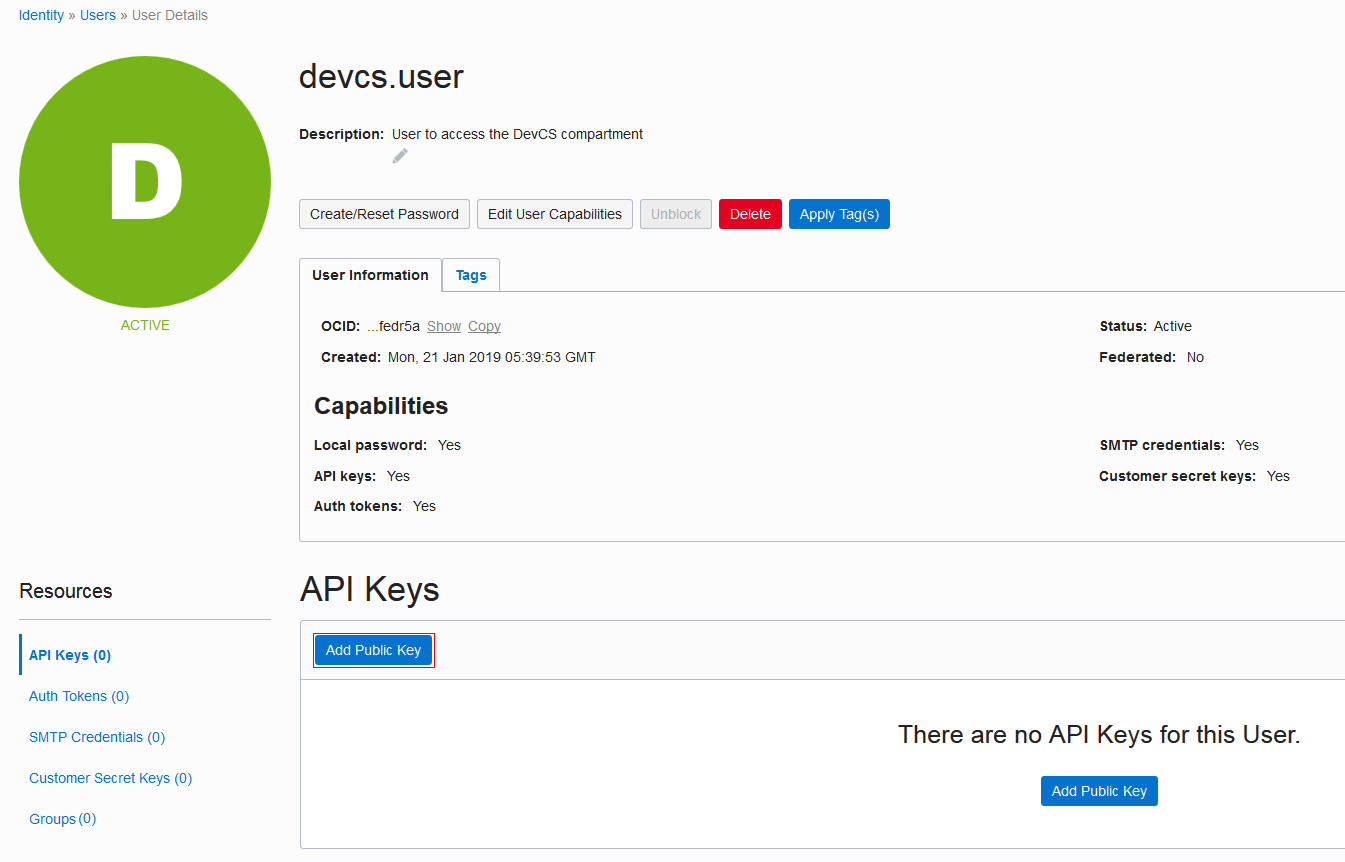
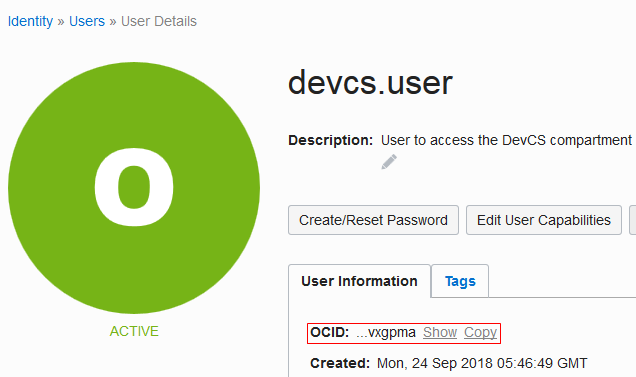
| User OCID and Fingerprint | On the OCI console, from the left navigation bar, under Governance and Administration, select Identity > Users.
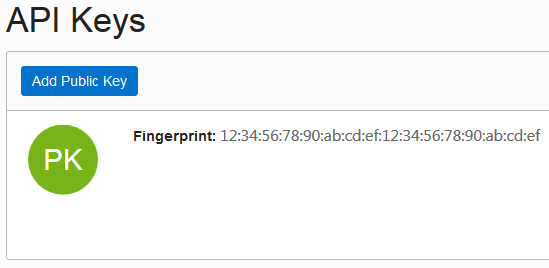
The User Information tab displays the user OCID in OCID. Click the Copy link to copy it to the clipboard. Here's an example of To get the fingerprint of the public key associated with your OCI account, scroll down to the API Keys section and copy the fingerprint value. |
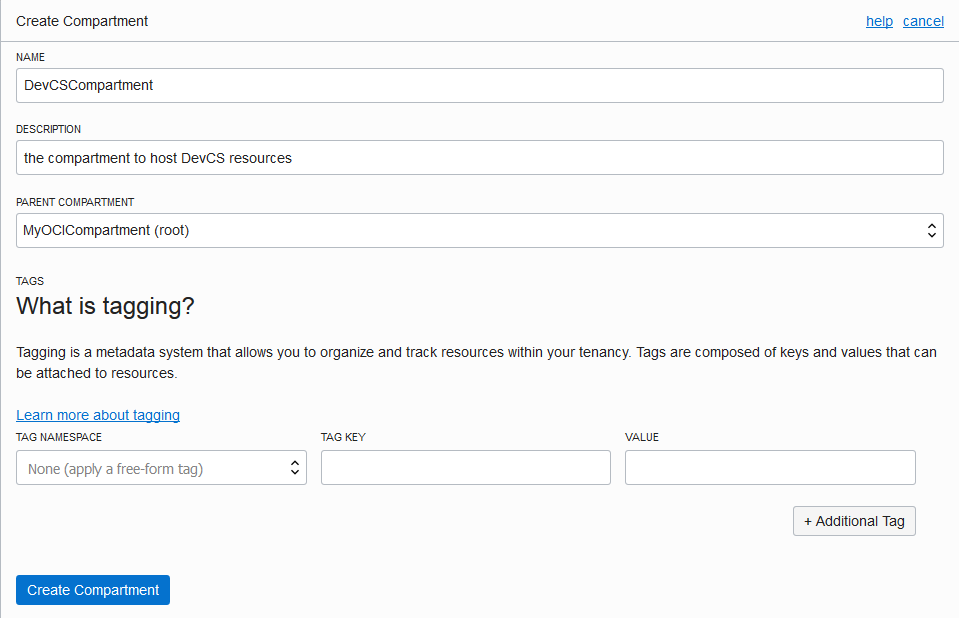
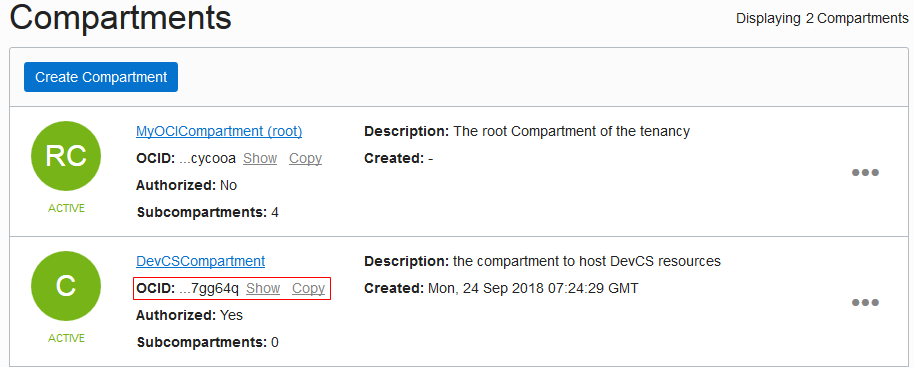
| Compartment OCID | On the OCI console, from the left navigation bar, select Identity > Compartments.
The Compartments list displays the compartments with the compartment OCID in the OCID field. Click the Copy link to copy it to the clipboard. Here's an example: |
Set Up the OCI Connection in the Target DevCS Instance
To connect to OCI, get the DevCS compartment, user details, and the required OCID values. Then, create an OCI connection from DevCS. If you're not the OCI administrator, get the details from the OCI administrator.
![]() You must be the Organization Administrator to create the connection.
You must be the Organization Administrator to create the connection.