Send Notifications to External Software Using Webhooks
Using Webhooks, you can send notifications to remote services and applications about Oracle Developer Cloud Service (DevCS) events such as a Git push, an issue update, a merge request update, or a build completion.
When you create a webhook, you specify a webhook provider. When an event occurs and the webhook triggers, the webhook provider processes the event, sets the properties used to generate the HTTP request, and dispatches the HTTP request to the target service.
![]() You must be assigned the project Owner role to create and configure a webhook.
You must be assigned the project Owner role to create and configure a webhook.
Slack
Slack is a cloud based team collaboration software. Using a Slack Webhook, you can configure DevCS to send events and activities notifications to a Slack channel. To find more about Slack, see https://slack.com/.
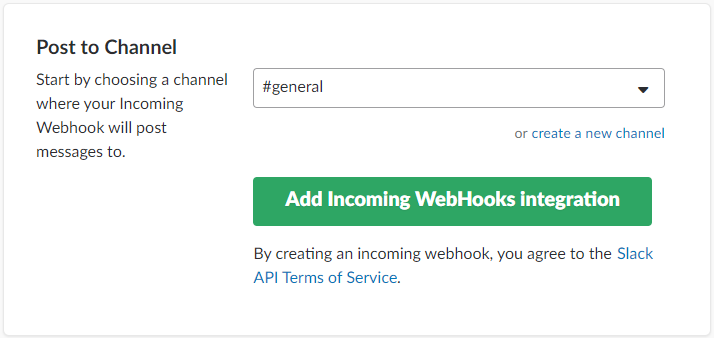
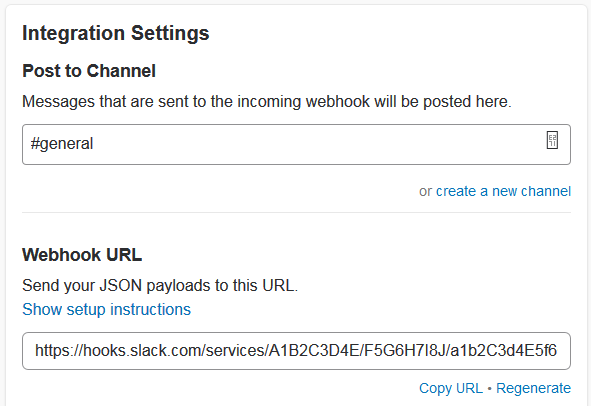
Get the Slack Channel’s Incoming Webhook URL
Configure a Slack Webhook in DevCS to Send Event Notifications
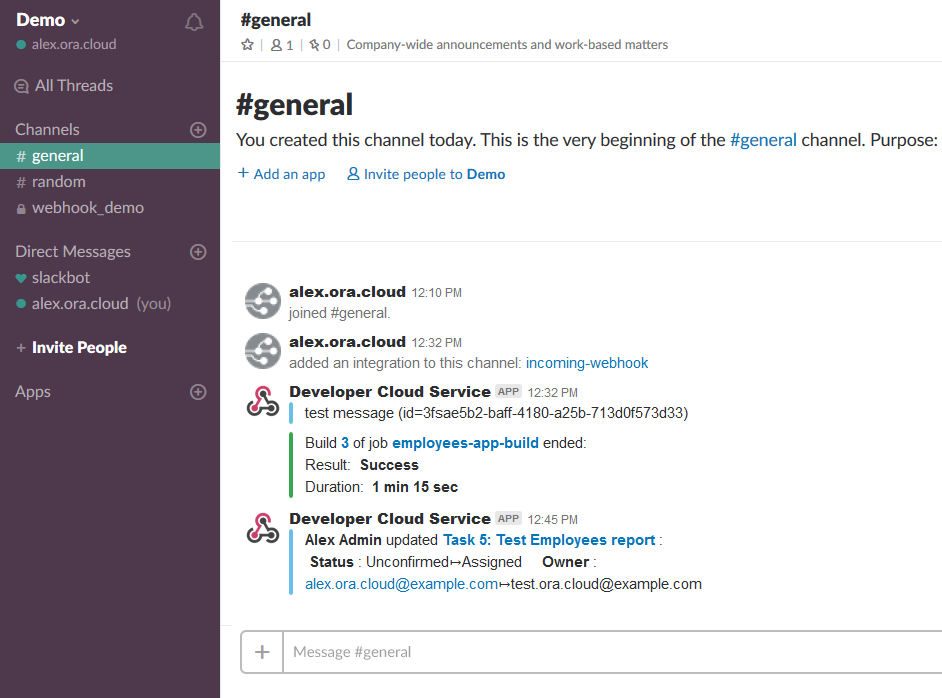
The Slack webhook is a outgoing webhook used to send DevCS event notifications to a Slack channel.
![]() You must be assigned the project Owner role to create and configure a webhook.
You must be assigned the project Owner role to create and configure a webhook.
Oracle Social Network
Oracle Social Network (OSN) is a secure enterprise collaboration and social networking solution for business. Using the Oracle Social Network webhook, you can send the DevCS events and activities to OSN conversations.
To send notification to a an OSN conversation, set up an DevCS Incoming Webhook in OSN and associate it with an OSN Conversation. When set up, the Incoming Webhook provides a URL with an authentication token to use in the OSN Webhook of your project. For more information, see https://cloud.oracle.com/social-cloud.
You can also set up the OSN functionality for Oracle Public Cloud from Oracle Content and Experience Cloud. The Oracle Content and Experience Cloud Administrator can create an incoming Webhook integration, associate it with an OSN conversation, and get the URL with an authentication token to use in the OSN Webhook of your project. See Configuring Webhooks in Administering Oracle Content and Experience Cloud.
Get OSN Conversation's Incoming Webhook URL
- Sign in to Oracle Social Network as an administrator.
- Click Webhooks.
- To the right of Generic Incoming Webhook, click New Instance.
- In Webhook Name, enter a name.
- In Target Conversation or Wall, specify the OSN conversation.
- In Message Template, specify the wording of the text to be included in the webhook-based message.
- Fill in the details in other fields of the webhook and click Save.
- In Webhook URL, click Copy to Clipboard.
PagerDuty
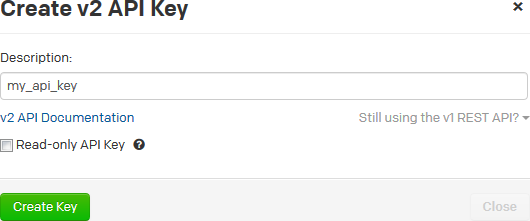
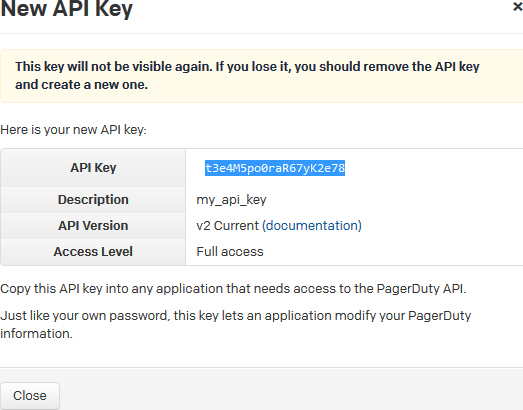
PagerDuty is an incident management platform that enables you to send notifications via email, push, SMS, and phone. Using the PagerDuty webhook, you can send notifications to your PagerDuty service about events in DevCS. When the PagerDuty service receives notifications from DevCS, it can redirect those notifications via email, push, SMS, and phone. To find more about PagerDuty, see https://www.pagerduty.com/.
To send notifications to PagerDuty, set up your PagerDuty account to receive notifications and create a DevCS webhook.
Jenkins
Jenkins is an open-source continuous integration software used to build and test your software applications. Using the various Jenkins webhooks, you can integrate your Jenkins with DevCS to run builds. Jenkins must be available on the public Internet to accept webhook notifications.
You can use these webhooks to integrate Jenkins with DevCS:
| To do this ... | Use this webhook |
|---|---|
| Trigger a Jenkins job on SCM polling of the job's Git repository | Hudson/Jenkins Git Plugin |
| Trigger a Jenkins job on a project's Git repository update | Hudson/Jenkins Build Trigger |
| Link a Jenkins job with a merge request | Jenkins Merge Requests |
| Receive notifications in DevCS project's activity feed from Jenkins when a job's build runs or completes | Jenkins Notification Plugin |
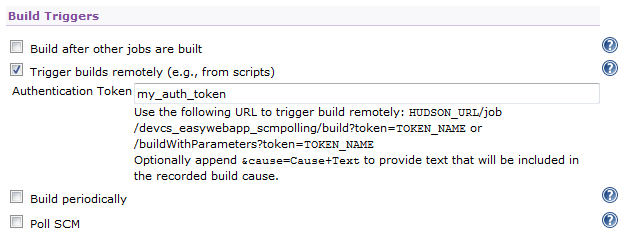
Trigger a Jenkins Job on SCM Polling
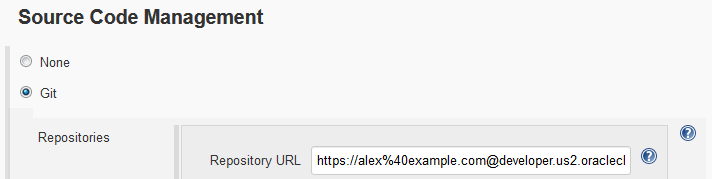
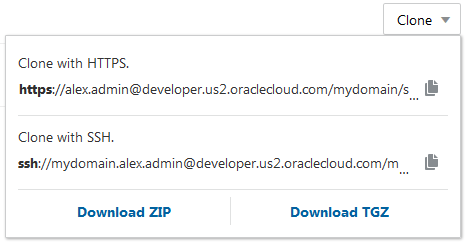
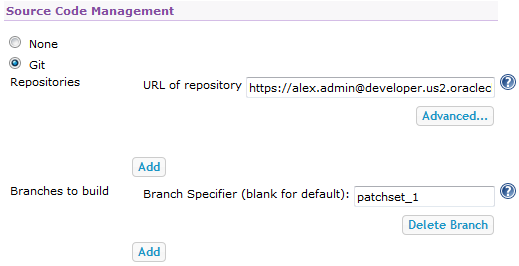
Using the Hudson/Jenkins - Git Plugin Webhook, you can trigger a Jenkins job that uses a DevCS Git repository as source on SCM polling.
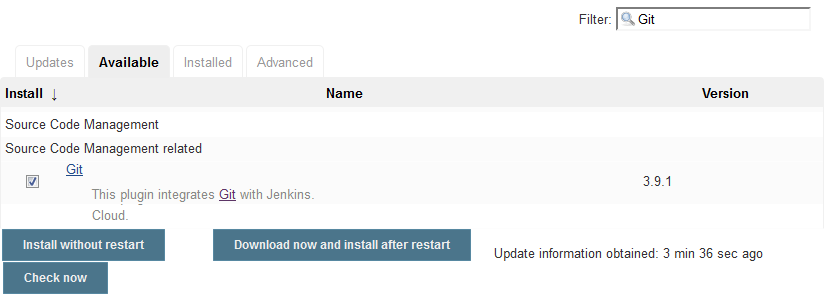
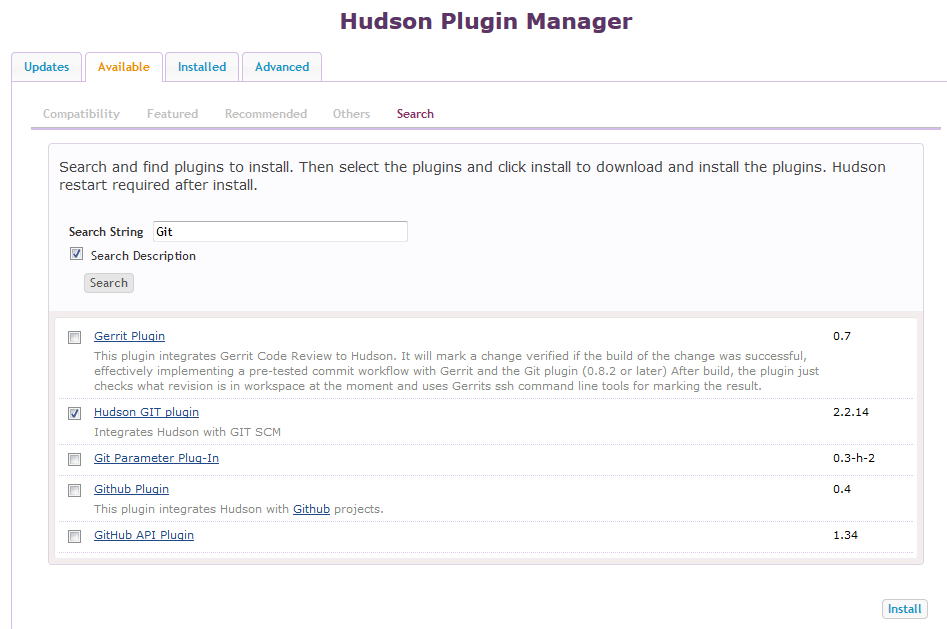
- If not installed, install the Git plugin.
- Create or configure the Jenkins job to use the DevCS project Git repository as source.
- Enable SCM polling in the Jenkins job.
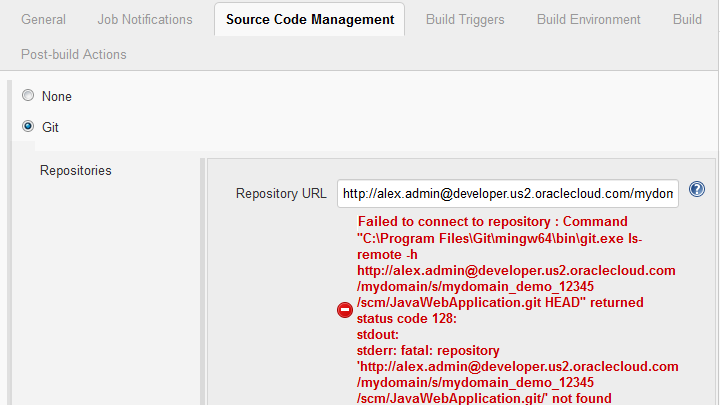
- Create or configure a webhook to send a notification to Jenkins when the job's Git repository (or any project Git repository) is updated.
When the Git plugin of Jenkins receives a notification, it goes through all Jenkins jobs that have SCM polling enabled and match the provided notification parameters (such as Git repositories and branches). For all matching jobs, it starts a build. The build won't run if no changes are found by polling.
For more information about the Jenkins Git plugin, see https://wiki.jenkins-ci.org/display/JENKINS/Git+Plugin#GitPlugin-Pushnotificationfromrepository.
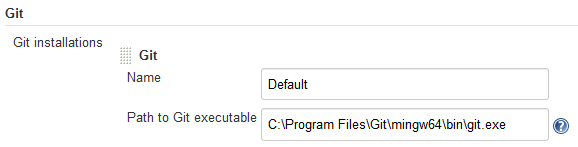
Set Up Git on Jenkins
Trigger a Jenkins Job on a Git Repository Update
Using the Hudson/Jenkins - Build Trigger webhook, you can trigger a Jenkins job when a project Git repository updates. It's not necessary that the Jenkins job uses a DevCS project Git repository as source.
To allow the webhook to connect to Jenkins, you'd need to specify the security settings of Jenkins.
| If ... | Do this: |
|---|---|
| Jenkins allows anonymous user to trigger a build |
|
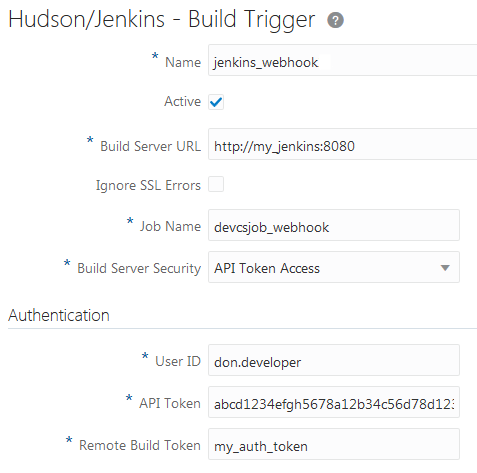
| Jenkins allows only authenticated users to trigger a build |
|
|
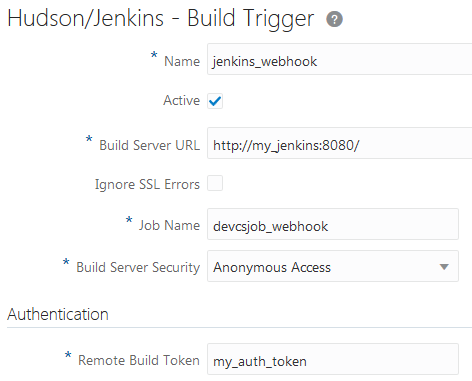
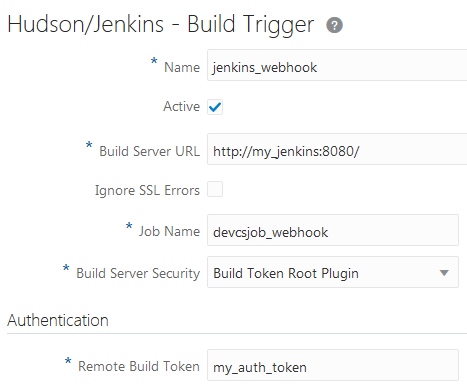
Anonymous access is disabled or lacks read permissions on Jenkins and you want to trigger the job without an authenticated user's credentials Or Jenkins uses a build token root to trigger builds |
|
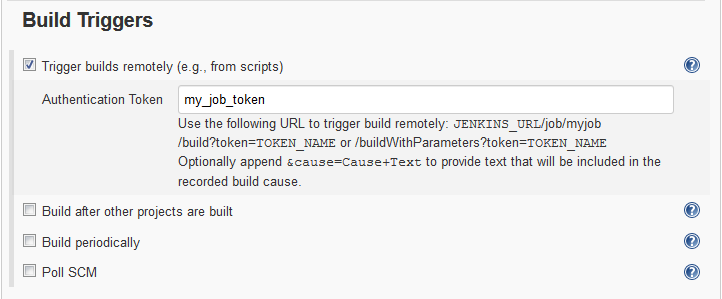
| Security is completely disabled on Jenkins. | Configure the webhook to connect to Jenkins job. No Jenkins configuration required. |
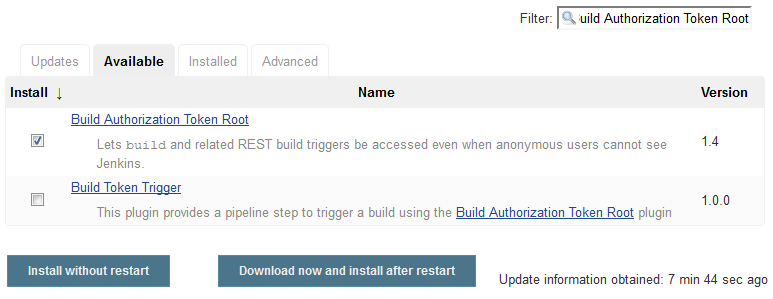
Install the Build Authorization Token Root Plugin on Jenkins
If anonymous access is disabled on Jenkins and you want to trigger Jenkins jobs without an authenticated user's credentials, install the Build Authorization Token Root plugin on Jenkins. You must be assigned the Admin role of Jenkins to install the plugin. The plugin is required To find out more about the plugin, see https://wiki.jenkins-ci.org/display/JENKINS/Build+Token+Root+Plugin.
Get the Jenkins API Access Token
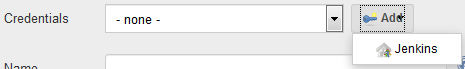
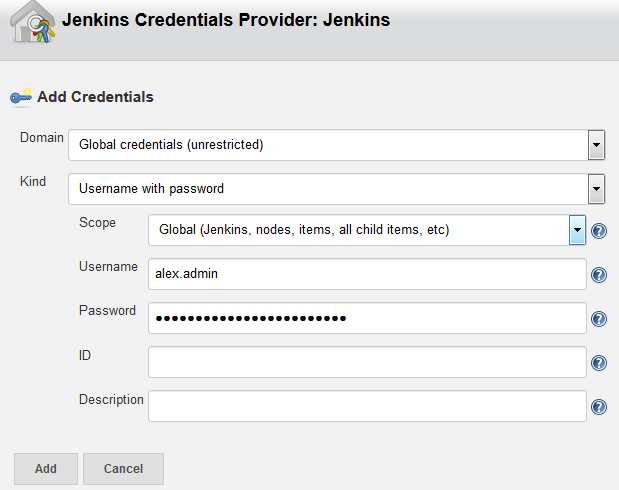
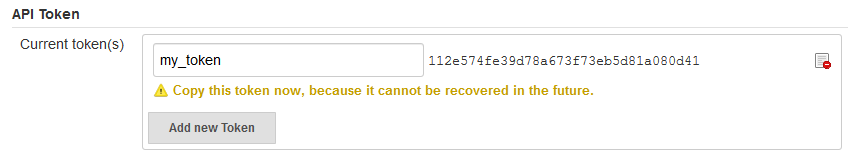
If Jenkins allows only authenticated users to trigger builds, use the API Access token of an authenticated user as the user's credentials in the DevCS webhook.
To use the API Access token in a DevCS webhook, provide the username and the token of an authenticated user. If you don't want to provide a user's details, create a separate username to trigger builds and assign the user the Overall/Read, Job/Read and Job/Build permissions. Then, use this user's details in the webhook.
Trigger a Jenkins Job from a Merge Request
Using the Jenkins - Merge Requests webhook, you can link a Jenkins job to a merge request. When a commit is pushed to the review branch of the merge request, the webhook sends a notification to Jenkins and triggers a build of the linked job. When the build completes, it sends a notification back to DevCS. Based on the build’s status, the linked build approves or rejects the merge request.
To allow the webhook to connect to Jenkins, you'd need to specify the security settings of Jenkins.
| If ... | Do this: |
|---|---|
| Jenkins allows anonymous user to trigger a build on Jenkins |
|
| Jenkins allows only authenticated users to trigger a build |
|
|
Anonymous access is disabled or lacks read permissions on Jenkins and you want to trigger the job without an authenticated user's credentials Or Jenkins uses a build token root to trigger builds |
|
| Security is completely disabled on Jenkins. | Configure the webhook to connect to Jenkins job. No Jenkins configuration required. |
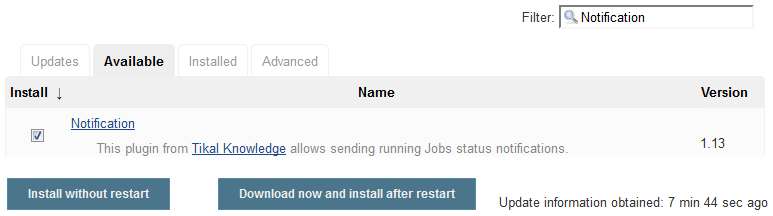
Install the Notification Plugin on Jenkins
To send notifications from Jenkins, install the Notification plugin.
Install the Build Authorization Token Root Plugin on Jenkins
If anonymous access is disabled on Jenkins and you want to trigger Jenkins jobs without an authenticated user's credentials, install the Build Authorization Token Root plugin on Jenkins. You must be assigned the Admin role of Jenkins to install the plugin. The plugin is required To find out more about the plugin, see https://wiki.jenkins-ci.org/display/JENKINS/Build+Token+Root+Plugin.
Get the Jenkins API Access Token
If Jenkins allows only authenticated users to trigger builds, use the API Access token of an authenticated user as the user's credentials in the DevCS webhook.
To use the API Access token in a DevCS webhook, provide the username and the token of an authenticated user. If you don't want to provide a user's details, create a separate username to trigger builds and assign the user the Overall/Read, Job/Read and Job/Build permissions. Then, use this user's details in the webhook.
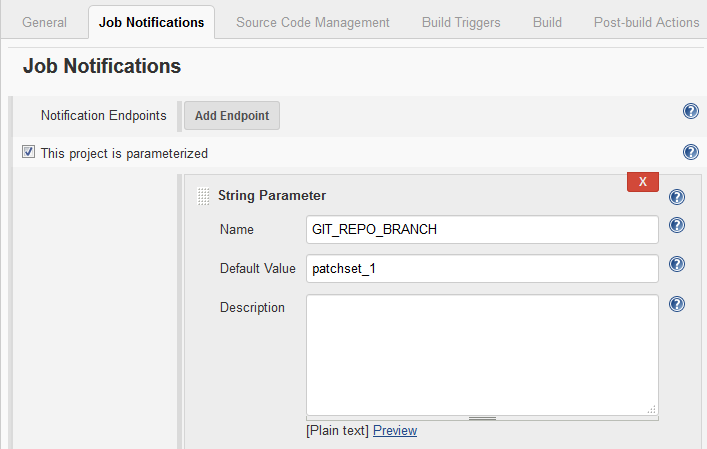
Configure the Jenkins Job to Set an Authentication Token and Accept Build Parameters
To trigger the Jenkins job when it receives a notification from DevCS, configure it to accept the Git repository’s branch name as a parameter and set an authentication token.
Configure a Webhook in DevCS to Trigger a Jenkins Job on a Merge Request Update
After installing the required plugins and configuring the Jenkins job, create the webhook.
Link the Jenkins Job with the Merge Request
When a commit is pushed to the review branch of the merge request, the webhook triggers a build of the specified job on the remote Jenkins server and notification is posted on the Recent Activity Feed of the project. If the build succeeds, it’s added to the Approve section of the Review Status list in the Merge Request page. If the build fails, it’s added to the Reject section of the Review Status list.
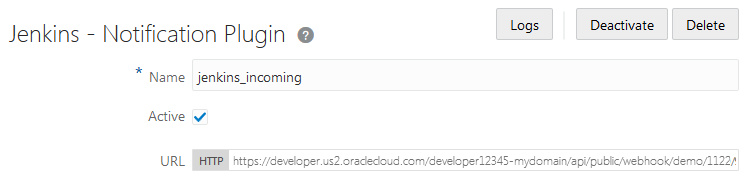
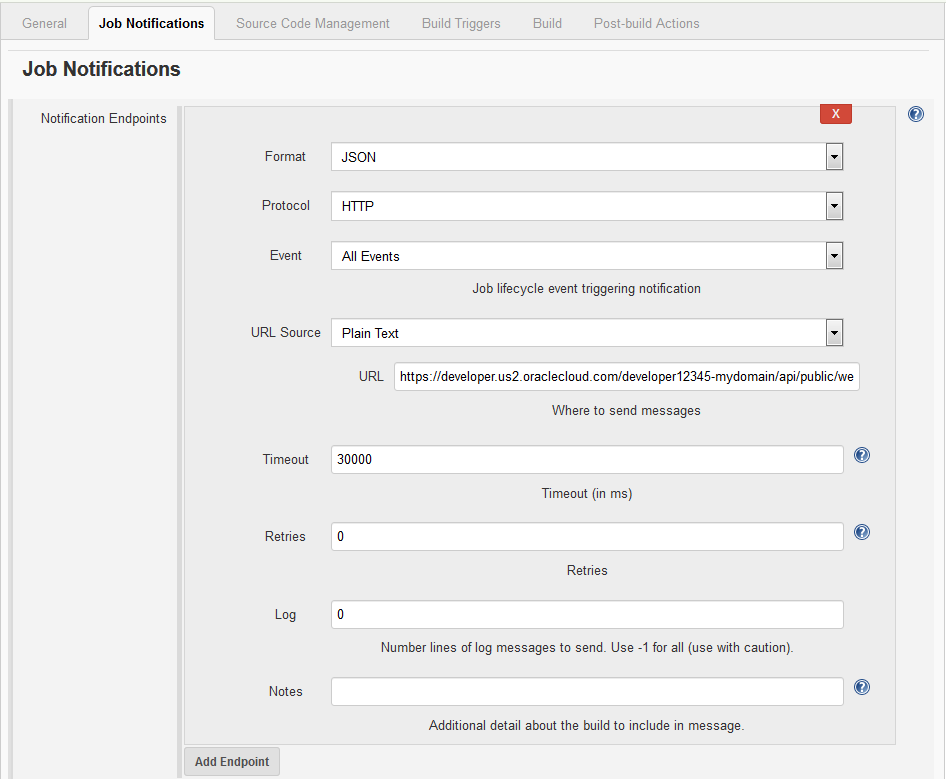
Receive Build Notifications from a Jenkins Job
Using the Jenkins - Notification Plugin Webhook, you can configure DevCS to accept build notifications from Jenkins and shows the build notification in the recent activities feed of the Project Home page.
Jenkins - Notification Plugin Webhook is an incoming Webhook and accepts build notifications only. Don’t use this webhook to pass information to any external server or accept information of any other type. To use the webhook, install the Notifications plugin on Jenkins, configure the DevCS webhook to connect to Jenkins, and then configure the Jenkins job to send build notifications.
Hudson
Hudson is an open-source extensible continuous integration software used to build and test your software applications. Using webhooks, you can integrate your Hudson server with DevCS to run builds. Hudson must be available on the public Internet to accept webhook notifications.
You can use these webhooks to integrate Hudson with DevCS:
| To do this ... | Use this webhook |
|---|---|
| Trigger a Hudson job on SCM polling of the job's Git repository | Hudson/Jenkins Git Plugin |
| Trigger a Hudson job on a project's Git repository update | Hudson/Jenkins Build Trigger |
Trigger a Hudson Job on SCM Polling
Using the Hudson/Jenkins - Git Plugin Webhook, you can trigger a Hudson job that uses a DevCS Git repository as source on SCM polling.
To trigger the job:
- If not installed, install the Git plugin
- Create or configure the Hudson job to use the DevCS project Git repository as source
- Enable SCM polling in the Hudson job
- Create or configure a webhook to send a notification to Hudson when the job's Git repository (or any project Git repository) is updated
When the Git plugin of Hudson receives a notification, it goes through all Hudson jobs that have SCM polling enabled and match the provided notification parameters (such as Git repositories and branches). For all matching jobs, it starts a build. The build won't run if no changes are found by polling.
For more information about the Hudson Git plugin, see http://wiki.hudson-ci.org/display/HUDSON/Git+Plugin#GitPlugin-PostCommitHook.
Set Up Git on Hudson
You must be assigned the Admin role of Hudson to set up Git on it. Git must also be installed on the computer running Jenkins. If the plugin is already installed and configured, ignore this section.
Trigger a Hudson Job on a Git Repository Update
Using the Hudson/Jenkins - Build Trigger webhook, you can trigger a Hudson job when a project Git repository updates. It's not necessary that the Hudson job uses a DevCS project Git repository as source.
To allow the webhook to connect to Hudson, you'd need to specify the security settings of Hudson.
| If ... | Do this: |
|---|---|
| Hudson allows anonymous user to trigger a build |
|
| Hudson allows only authenticated users to trigger a build |
|
| Security is completely disabled on Hudson | Configure the webhook to connect to Hudson job. No Hudson configuration required. |
GitHub Apps
If you're using apps that accept incoming webhook connections from GitHub, use the GitHub Compatible webhook to send DevCS event notifications to those apps. The payload is sent in the similar format as the GitHub, so you don't need to make changes to your GitHub apps.
To find more about GitHub webhooks, see https://developer.github.com/webhooks/.
When you’re finished, use the project navigation bar to switch to another page.
Send Event Notifications to Any Application
Using the DevCS Generic Webhook, you can sends event notifications to any application that accepts webhook requests and can parse payload specific content. The webhook payload format depends on the type of the event.
The generic webhook supports all possible events of DevCS, including Git pushes, issue updates, merge request updates, and project builds. It sends a POST request to the remote service in the JSON format with details of the subscribed events.
When you’re finished, use the project navigation bar to switch to another page.
Data Structure of a Generic Webhook
The information sent by a generic webhook is delivered using a POST request with the application/json content-type, with the UTF-8 character set, in a Message object.
This table describes the fields of the Message object.
| Field | Description |
|---|---|
|
|
Version of the API. It changes when the payload format of the request changes. |
|
|
Unique identifier of the message |
|
|
Timestamp of the message when it was generated |
|
|
Set to |
|
|
Unique identifier of the project |
|
|
List of events delivered by the message |
Each event delivered by the message follows a common structure. There are three types of events (ISSUE/PUSH/BUILD/REVIEW/ACTIVITY).
| Field | Description |
|---|---|
|
|
Type of the event ( |
|
|
Unique identifier of the project |
|
|
Timestamp of the event |
|
|
Data specific to the type of the event |
The structure of data of each event type is described in the following sections.
ISSUE Event
The ISSUE event contains the fields described in this table.
| Field | Description |
|---|---|
|
|
Type of the activity ( |
|
|
Timestamp of the activity |
|
|
Description of the change |
|
|
Description of the issue after the change |
|
|
Issue ID |
|
|
Change version |
|
|
URL of the issue |
|
|
Title of the issue |
|
|
Type of the issue ( |
|
|
Resolution of the issue. The value is |
|
|
User who reported the issue |
|
|
User to whom the issue is assigned |
|
|
Content of the added comment, available if the activity type is |
|
|
List of changed fields, available if the activity type is |
|
|
Field name |
|
|
Value before the change |
|
|
Value after the change |
Here is a JSON payload example of an issue create event.
{
"apiVersion": "1.0",
"messageId": "04abc282-a44e-4c23-ba53-15b519d30066",
"projectId": "qa-dev_example-project",
"testEvent": false,
"timestamp": 1417810876408,
"events": [
{
"eventId": "ISSUE",
"projectId": "example-project",
"timestamp": 1417810876,
"data": {
"activities": [
{
"type": "CREATED",
"date": 1417810875820,
"description": "",
"author": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Admin"
},
"issue": {
"id": 2,
"resolution": null,
"title": "Test Issue",
"type": "Feature",
"url": "http://test-server/#projects/example-project/task/2",
"version": "1417810875834",
"reporter": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Admin"
}
}
}
]
}
}
]
}Here is a JSON payload example of an issue update event.
{
"apiVersion": "1.0",
"messageId": "ccce183e-097d-4668-a07b-cf762108716e",
"projectId": "qa-dev_example-project",
"testEvent": false,
"timestamp": 1417811058243,
"events": [
{
"eventId": "ISSUE",
"projectId": "example-project",
"timestamp": 1417811058
"data": {
"activities": [
{
"type": "UPDATED"
"date": 1417811057698,
"description": "Assign to alex.admin\nset Resolution to FIXED\nset Status to RESOLVED\n",
"author": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Admin"
},
"issue": {
"id": 2,
"resolution": "FIXED",
"title": "Test Issue",
"type": "Feature",
"url": "http://test-server/#projects/example-project/task/2",
"version": "1417811057698",
"asignee": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Admin"
},
"reporter": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Admin"
}
},
"fieldUpdates": [
{
"name": "assigned_to",
"newValue": "alex.admin",
"oldValue": ""
},
{
"name": "resolution",
"newValue": "FIXED",
"oldValue": ""
},
{
"name": "bug_status",
"newValue": "RESOLVED",
"oldValue": "UNCONFIRMED"
}
]
},
{
"type": "COMMENTED"
"date": 1417811057929,
"description": "Feature is implemented",
"author": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Admin"
},
"comment": {
"author": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Admin"
},
"date": 1417811057929,
"text": "Feature is implemented",
"type": "UNKNOWN"
},
"task": {
"id": 2,
"resolution": "FIXED",
"title": "Test Issue",
"type": "Feature",
"url": "http://test-server/#projects/qa-dev_example-project/task/2",
"version": "1417811057698",
"asignee": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Alex Admin"
},
"reporter": {
"gravatarHash": "8940829abebbc5d8d84e37af7161fd31",
"loginName": "alex.admin",
"realName": "Alex Admin"
}
}
}
]
}
}
]
}PUSH Event
The PUSH event contains the fields described in this table.
| Field | Description |
|---|---|
|
|
Updated references |
|
|
Commits of the Push event |
|
|
Commit identifier |
|
|
Comment in the commit |
|
|
Author of the commit |
|
|
Timestamp of the commit |
|
|
List of commit parent identifiers |
|
|
Name of the repository to which the commit was pushed |
Here is a JSON payload example of a Git Push event.
{
"apiVersion": "1.0",
"messageId": "c3378be6-6be5-4191-9b20-1fb5d429bfce",
"projectId": "example-project",
"testEvent": false,
"timestamp": 1417810424512,
"events": [
{
"eventId": "GIT_PUSH",
"projectId": "example-project",
"timestamp": 1417810424,
"data": {
"refName": "refs/heads/master",
"commits": [
{
"sha": "32e03bc46a3a42eeab5dd25144a90c5b4f0b2e11",
"repository": "example-project.git",
"date": 1417810387000,
"comment": "file1.txt deleted, file3.txt created\n",
"author": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Admin",
"username": "alex.admin"
},
"parents": [
"1106e8c81cb49e71024e9017235f89dc3983d4ee"
]
},
{
"sha": "1106e8c81cb49e71024e9017235f89dc3983d4ee",
"repository": "example-project.git",
"date": 1417810290000,
"comment": "file2.txt updated\n",
"author": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Admin",
"username": "alex.admin"
},
"parents": [
"8dab56fb6ba6dd0fc0d0aa8c7ce4f01d77fa0835"
]
}
]
}
}
]
}
BUILD Event
The BUILD event contains the fields described in this table.
| Field | Description |
|---|---|
|
|
Name of the job |
|
|
Build timestamp |
|
|
Build number |
|
|
Build URL |
|
|
Build result ( |
|
|
Build duration |
|
|
Name of the artifact |
|
|
Path relative to the job workspace |
|
|
URL of the artifact |
Here is a JSON payload example of a Build event.
{
"apiVersion":"1.0",
"messageId":"4a253425-4598-4838-a4b5-aac30d0b9710",
"timestamp":1417795613257,
"testEvent":true,
"projectId":"test-project",
"events":[
{
"eventId":"BUILD",
"projectId":"test-project",
"timestamp":1417795613256,
"data":{
"jobName":"example-job",
"details":{
"timestamp":1417795590256,
"number":16,
"url":"http://server/test-dev/s2/test-project/hudson/job/test-project.example-job/16/",
"result":"SUCCESS",
"duration":36905,
"artifacts":[
{
"fileName":"sample-1.0-SNAPSHOT.jar",
"relativePath":"sample-project/target/sample-1.0-SNAPSHOT.jar",
"url":"http://server/test-dev/s2/test-project/hudson/job/test-project.example-job/16/artifact/sample-project/target/sample-1.0-SNAPSHOT.jar"
}
]
}
}
}
]
}
REVIEW Event
The REVIEW event represents changes in merge requests and contains the fields described in this table.
| Field | Description |
|---|---|
|
|
Description of the merge request |
|
|
Unique ID of the merge request |
|
|
Title of the merge request |
|
|
Timestamp of the merge request creation |
|
|
Timestamp of the merge request last modification |
|
|
Profile of the user who created the merge request |
|
|
Name of the Git repository |
|
|
Name of the review branch |
|
|
Name of the target branch |
|
|
Profile of the user who performed the action |
|
|
Merge request action Here is the list of merge request actions:
|
|
|
List of commits added to the merge request The
|
|
|
Text of the comment The |
|
|
Comment of the rejected or approved review action The |
|
|
Result of the merge ( The |
|
|
Status of the merge request ( The |
Here is a JSON payload example of a REVIEW event.
{
"apiVersion": "1.0",
"events": [
{
"data": {
"action": "CREATED",
"review": {
"created": 1431944319181,
"id": 6,
"modified": 1431944319635,
"reporter": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
},
"repository": "example-project.git",
"reviewBranch": "bug_branch",
"targetBranch": "master",
"title": "Bug Fix"
},
"user": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
}
},
"eventId": "REVIEW",
"projectId": "example-project",
"timestamp": 1431944327
}
],
"messageId": "08758261-e4e7-4c8f-b9fe-7b74f715803f",
"projectId": "example-project",
"testEvent": false,
"timestamp": 1431944329923
}
{
"apiVersion": "1.0",
"events": [
{
"data": {
"action": "COMMIT",
"commits": [
{
"author": "alex.admin",
"message": "fix version #3\n",
"sha": "8fd1d2a53a181aa7015e7535b6f64295c432eca7"
},
{
"author": "alex.admin",
"message": "fix version #2\n",
"sha": "ff2bdf91d0fb6fb664315879ec38acc0931beeb6"
}
],
"review": {
"created": 1431944319181,
"id": 6,
"modified": 1431944340209,
"reporter": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
},
"repository": "example-project.git",
"reviewBranch": "bug_branch",
"targetBranch": "master",
"title": "Bug Fix"
},
"user": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
}
},
"eventId": "REVIEW",
"projectId": "example-project",
"timestamp": 1431944353
}
],
"messageId": "5de98d08-49cd-4a19-86b5-d89757f75a1d",
"projectId": "example-project",
"testEvent": false,
"timestamp": 1431944355646
}
{
"apiVersion": "1.0",
"events": [
{
"data": {
"user": {
"email": "clara.coder@example.com",
"firstName": "Clara",
"lastName": "Coder",
"username": "clara"
},
"review": {
"created": 1436521285722,
"id": 23,
"modified": 1438246154916,
"reporter": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Admin",
"username": "alex"
},
"repository": "example-project.git",
"reviewBranch": "bug_branch",
"targetBranch": "master",
"title": "Some Review"
},
"action": "REVIEWED",
"status": "REJECTED",
"comment": "rejected the request because ...",
},
"eventId": "REVIEW",
"projectId": "example-project",
"timestamp": 1438246163
}
],
"messageId": "f0a75815-3470-4dc4-be82-975935152ed3",
"projectId": "example-project",
"testEvent": false,
"timestamp": 1438246165924
}
{
"apiVersion": "1.0",
"events": [
{
"data": {
"action": "COMMENTED",
"review": {
"created": 1431944319181,
"id": 6,
"modified": 1431944478701,
"reporter": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
},
"repository": "example-project.git",
"reviewBranch": "bug_branch",
"targetBranch": "master",
"title": "Bug Fix"
},
"text": "General comment",
"user": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
}
},
"eventId": "REVIEW",
"projectId": "example-project",
"timestamp": 1431945965
}
],
"messageId": "d2a36692-dae6-44d4-a112-7a615b524cc3",
"projectId": "example-project",
"testEvent": false,
"timestamp": 1431945967166
}
{
"apiVersion": "1.0",
"events": [
{
"data": {
"action": "MERGED",
"result": "FAST_FORWARD",
"review": {
"created": 1431944319181,
"id": 6,
"modified": 1431944478701,
"reporter": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
},
"repository": "example-project.git",
"reviewBranch": "bug_branch",
"targetBranch": "master",
"title": "Bug Fix"
},
"user": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
}
},
"eventId": "REVIEW",
"projectId": "example-project",
"timestamp": 1431945438
}
],
"messageId": "b06d5581-d38a-4972-9c80-dc1455547776",
"projectId": "example-project",
"testEvent": false,
"timestamp": 1431945440287
}
{
"apiVersion": "1.0",
"events": [
{
"data": {
"action": "CLOSED",
"review": {
"created": 1431944319181,
"id": 6,
"modified": 1431945453967,
"reporter": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
},
"repository": "example-project.git",
"reviewBranch": "bug_branch",
"targetBranch": "master",
"title": "Bug Fix"
},
"status": "COMPLETED",
"user": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
}
},
"eventId": "REVIEW",
"projectId": "example-project",
"timestamp": 1431945459
}
],
"messageId": "b434f6d2-b5c7-4c0a-bab2-3e6614025865",
"projectId": "example-project",
"testEvent": false,
"timestamp": 1431945453967
}
ACTIVITY Event
The ACTIVITY event contains the fields described in this table.
| Field | Description |
|---|---|
|
|
Profile of the user whose action produced the activity The value is |
|
|
Name of the activity |
|
|
Description of the activity, or the object whose fields depends on the Here is the list of supported activities:
|
Here is a JSON payload example of an Activity event.
{
"apiVersion": "1.0",
"events": [
{
"data": {
"author": {
"email": "alex.admin@example.com",
"firstName": "Alex",
"lastName": "Alex Admin",
"username": "alex.admin"
},
"name": "WIKI",
"properties": {
"page": "New Page Title",
"type": "CREATED"
}
},
"eventId": "ACTIVITY",
"projectId": "example-project",
"timestamp": 1432035029
}
],
"messageId": "45066d85-5a5c-4647-9a6c-43fc8e99481a",
"projectId": "qa-dev_test-rss",
"testEvent": false,
"timestamp": 1432035031418
}