PeopleSoft User Management
Before You Begin
Introduction
The PeopleSoft Tools integration helps you to manage PeopleSoft Tools-based user profiles, records in PeopleSoft applications including Role and Permission, with the help of Oracle Identity Cloud Service.
About the Oracle PeopleSoft Tool
Managing your workforce globally often requires region- or country-specific features and functions in Human Resources (HR) and Payroll. Oracle’s PeopleSoft Enterprise Human Resources and Global Payroll applications help to make this possible. Being compliant with HR regulations is essential. Making timely payments to your workforce while lowering your total cost of ownership is a business goal your organization can achieve. With PeopleSoft Enterprise country extensions, you have complete control over all aspects of your local HR and payroll operations, including statutory payroll and reporting requirements.
After integrating Oracle PeopleSoft and Oracle Identity Cloud Service, administrators can use the Identity Cloud Service console to:
- Assign and revoke user access to the Oracle PeopleSoft Tool.
- Manage users, user roles, and permission lists.
What Do You Need?
- An Oracle Identity Cloud Service Identity Domain Administrator, Security Administrator, or Application Administrator account so that you can manage apps and user accounts.
- An Oracle PeopleSoft account with authorization rights to manage users, roles, and permission list.
Supported Operations
The following operations are supported:
| Operation | Supported? |
|---|---|
| Authoritative Sync | Not supported. |
| Sync | Supported. Note: The user details should be exported XML files and the folder location accessible to the Bridge. |
| Create User | Supported. |
| Update User | Supported. |
| Disable User | Supported. |
| Enable User | Supported. |
| Delete User | Supported. |
Prerequisite Steps
Before you can synchronize users and roles between Oracle PeopleSoft and Oracle Identity Cloud Service, you must:
Install and Configure a Provisioning Bridge
Install and configure a Provisioning Bridge in Oracle Identity Cloud Service. This bridge provides a link between Oracle PeopleSoft and Oracle Identity Cloud Service. Oracle Identity Cloud Service can synchronize with Oracle PeopleSoft so that any new, updated, or deleted user are synced with Oracle Identity Cloud Service. See the Manage Provisioning Bridges for Oracle Identity Cloud Service chapter in Administering Oracle Identity Cloud Service.
Add the Oracle PeopleSoft User Management App
Use the App Catalog to add the Oracle PeopleSoft User management app to Oracle Identity Cloud Service. The Provisioning Bridge uses this app to synchronize, import, and provision users and roles between Oracle PeopleSoft and Oracle Identity Cloud Service. See Add an App Catalog Application in Administering Oracle Identity Cloud Service.
Access to the Dependency .jar files
Ensure that you have access to the psjoa and psmanagement jars (dependency jars).
Update the Connector Bundle with the PeopleSoft Third-Party Jars
- Stop the Provisioning Bridge.
- Back up the
org.identityconnectors.peoplesoftum-<latest_version>.jarfile atBRIDGE_HOME/bundle_home. - Under
BRIDGE_HOME/thirdparty-lib, create the folderpeoplesoft/lib. - Copy the
psjoa.jarfile from the Peoplesoft instance atPEOPLESOFT_HOME/web/psjoato thepeoplesoft/libfolder in the Bridge. - Copy the
psmanagement.jarfile from the Peoplesoft instance atPEOPLESOFT_HOME/client-tools/classto thepeoplesoft/libfolder in the Bridge. - Run below command from
BRIDGE_HOME:- For Linux:
updateBundleJarWithThirdPartyLib.sh org.identityconnectors.peoplesoftum-<latest_version>.jar ./thirdparty-lib/peoplesoft - For Windows:
updateBundleJarWithThirdPartyLib.bat org.identityconnectors.peoplesoftum-<latest_version>.jar D:\devBridge\thirdparty-lib\peoplesoft
- For Linux:
- Start the Provisioning Bridge.
Export Currency Codes, Languages, Permission Lists and Roles
Export currency codes, languages, permission lists and roles using the PeopleSoft Application Designer. See the PeopleSoft Application Designer documentation for instructions.
Create a User in Oracle PeopleSoft
Create a user in Oracle PeopleSoft so that the Provisioning Bridge can use it to synchronize, import, and provision users between Oracle PeopleSoft and Oracle Identity Cloud Service.
Note: Permission lists, roles, and user profiles are the building blocks of PeopleSoft security. Each user of the system has an individual user profile, which in turn is linked to one or more roles. To each role, you can add one or more permission lists, which define what a user can access. So, a user inherits permissions through the role that is attached to a user profile. You must create limited rights users who have restricted rights to access resources in the production environment to perform PeopleSoft-specific installation or maintenance operations. A limited rights user has the privilege to invoke PeopleSoft User Profile Component Interface Java APIs for provisioning.
Oracle Identity Cloud Service requires this user to access Oracle PeopleSoft Applications. You provide the credentials of this user while performing the procedure described in Enable and Associate Provisioning Bridge to the Oracle PeopleSoft App.
Create a Target System User Account for Operations
You must create a target system account with privileges required for application integration operations. The user account created on the target system has the permission to perform all the configurations required for application integration operations. This includes configuring the PeopleSoft Integration Broker for full sync. This account doesn't have access to pages or components that are not required by the integration.
Important: The following steps describe the procedures to create an account. These steps might not match your PeopleSoft version. Consult the PeopleSoft documentation if required.
Note: For creating the target system account, you must log in to PeopleSoft Internet Architecture with administrator credentials.
Create a Permission List
Open a Web browser and enter the URL for PeopleSoft Internet Architecture. The URL is in the following format:
http://IPADDRESS:PORT/psp/ps/?cmd=login. For example:http://172.21.109.69:9080/psp/ps/?cmd=login.In the PeopleSoft Internet Architecture window:
- For PeopleTools 8.54 and earlier releases, expand PeopleTools, Security, Permissions & Roles, and then click Permission Lists.
- For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Security, Permissions & Roles, and then click Permission Lists.
- Click Add a new Value. On the Add a New Value tab, enter the permission list name, for example,
OIMER, and then click Add. On the General tab, enter a description for the permission list in the Description field.
On the Component Interfaces tab, click the search icon for the Name field and perform the following:
a. In the Name lookup, enter
USER_PROFILEand then click Lookup. From the list, selectUSER_PROFILE. The application returns to the Component Interfaces tab. Click Edit.b. On the Component Interface Permissions page, click Full Access(All).
c. Click OK and then click Save.
d. Click the plus sign (+) to add a row for the Name field and repeat Steps a through c for the
DELETE_USER_PROFILEcomponent interface.On the Pages tab, click the search icon for Menu Name and perform the following:
a. Click the plus sign (+) to add a row for Menu Name. Click the search icon for Menu Name. In the Menu Name lookup, enter
APPLICATION_ENGINEand then click Lookup. From the list, selectAPPLICATION_ENGINE. The application returns to the Pages tab. Click Edit Components.b. On the Component Permissions page, click Edit Pages for the
AE_REQUESTcomponent name.c. Click Select All, and then click OK. Click OK on the Components Permissions page.
d. On the Pages tab, click the plus sign (+) to add a row for Menu Name. Click the search icon for Menu Name. In the Menu Name lookup, enter
IB_PROFILEand then click Lookup. From the list, selectIB_PROFILE. The application returns to the Pages tab. Click Edit Components.e. On the Component Permissions page, click Edit Pages for each of the following component names:
IB_GATEWAYIB_MESSAGE_BUILDERIB_MONITOR_QUEUESIB_NODEIB_OPERATIONIB_QUEUEDEFNIB_ROUTINGDEFNIB_SERVICEIB_SERVICEDEFNIB_MONITOR
f. Click Select All, and then click OK for each of the components. Click OK on the Components Permissions page.
g. On the Pages tab, click the plus sign (+) to add another row for Menu Name.
h. In the Menu Name lookup, enter PROCESSMONITOR and then click Lookup. From the list, select PROCESSMONITOR. The application returns to the Pages tab. Click Edit Components.
i. On the Component Permissions page, click Edit Pages for the PROCESSMONITOR component name.
j. Click Select All, and then click OK. Click OK on the Components Permissions page.
k. On the Pages tab, click the plus sign (+) to add another row for Menu Name.
l. In the Menu Name lookup, enter PROCESS_SCHEDULER and then click Lookup. From the list, select PROCESS_SCHEDULER. The application returns to the Pages tab. Click Edit Components.
m. On the Component Permissions page, click Edit Pages for the PRCSDEFN component name.
n. Click Select All, and then click OK. Click OK on the Components Permissions page.
On the People Tools, select the Application Designer Access check box and click the Definition Permissions link. The Definition Permissions page is displayed.
On this page, grant full access to the following object types by selecting Full Access from the Access list:
- App Engine Program
- Message
- Component
- Project
- Application Package
Click OK.
Click the Tools Permissions link. The Tools Permissions page is displayed. On this page, grant full access to the SQL Editor tool by selecting Full Access from the Access list.
Click OK. The application returns to the People Tools tab.
On the Web Libraries tab, click the search icon for the Web Library Name field and perform the following:
a. In the Web Library Name lookup, enter
WEBLIB_PORTALand then click Lookup. From the list, select WEBLIB_PORTAL. The application returns to the Web Libraries tab. Click the Edit link.b. On the WebLib Permissions page, click Full Access(All).
c. Click OK and then click Save.
d. Click the plus sign (+) to add a row for the Web Library Name field and repeat Steps a through c for the WEBLIB_PT_NAV library.
e. Click Save to save all the settings specified for the permission list.
On the Process tab, click the Process Group Permissions link. The Process Group Permission page is displayed.
In the Process Group lookup, click the search icon. From the list, select TLSALL. The application returns to the Process Group Permission page.
Click the plus sign(+) to add another row for Process Group.
In the Process Group lookup, click the search icon. From the list, select STALL. The application returns to the Process Group Permission page.
Click OK.
Click Save.
Create a Role for a Limited Rights User
Open a Web browser and enter the URL for PeopleSoft Internet Architecture. The URL is in the following format:
http://IPADDRESS:PORT/psp/ps/?cmd=loginFor example:http://172.21.109.69:9080/psp/ps/?cmd=login.- In the PeopleSoft Internet Architecture window:
- For PeopleTools 8.54 and earlier releases, click PeopleTools, Security, Permissions & Roles, and then click Roles.
- For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Security, Permissions & Roles, and then click Roles.
Click Add a new Value. On the Add a New Value tab, enter the role name, for example,
IAMUM, and then click Add.On the General tab, enter a description for the role in the Description field.
On the Permission Lists tab, click the search icon and perform the following:
a. In the Permission Lists lookup, enter
IAMUMand then click Lookup. From the list, select IAMUM.b. Click the plus sign (+) to add another row.
c. In the Permission Lists lookup, enter
EOEI9000and then click Lookup. From the list, select EOEI9000.d. Click the plus sign (+) to add another row.
e. In the Permission Lists lookup, enter
EOCO9000and then click Lookup. From the list, select EOCO9000.f. Click Save.
Assign the Required Privileges to the Target System Account
Open a Web browser and enter the URL for PeopleSoft Internet Architecture. The URL is in the following format:
http://IPADDRESS:PORT/psp/ps/?cmd=login. For example:http://172.21.109.69:9080/psp/ps/?cmd=login.In the PeopleSoft Internet Architecture window:
- For PeopleTools 8.54 and earlier releases, click PeopleTools, Security, User Profiles, and then click User Profiles.
- For PeopleTools 8.55, 8.56, and 8.57, click NavBar, Navigator, PeopleTools, Security, User Profiles, and then click User Profiles.
Click Add a new Value.
On the Add a New Value tab, enter the user profile name, for example,
IAMUM, and then click Add.On the General tab, perform the following:
a. From the Symbolic ID list, select the value that is displayed, for example, SYSADM1.
b. Enter valid values for the Password and Confirm Password fields.
c. Click the search icon for the Process Profile permission list.
d. In the Process Profile lookup, enter
IAMUMand then click Lookup. From the list, select IAMUM. The application returns to the General tab.On the ID tab, select none as the value of the ID type.
On the Roles tab, click the search icon and perform the following:
a. In the Roles lookup, enter
IAMUMand then click Lookup. From the list, select IAMUM.b. Click the plus sign (+) to add another row.
c. In the Roles lookup, enter
ProcessSchedulerAdminand then click Lookup. From the list, select ProcessSchedulerAdmin.d. Click the plus sign (+) to add another row.
e. In the Roles lookup, enter
EIR Administratorand then click Lookup. From the list, select EIR Administrator.f. Click Save to save this user profile.
Oracle Identity Cloud Service uses this profile for integration-related operations that is, synching of users and provisioning.
Generating XML Files
The steps for Full Reconciliation on PeopleSoft Target 8.58.
Configuring the Target System for Full Reconciliation
Configuring the target system for full reconciliation involves configuring the USER_PROFILE message by performing the following procedures:
Activating the Full Data Publish Rule
You must define and activate this rule, because it acts as a catalyst for the Full Reconciliation process. This rule provides the Full Reconciliation process the desired information to initiate reconciliation.
In the PeopleSoft Internet Architecture window, expand Enterprise Components, Integration Definitions, and then click Full Data Publish Rules.
Search for and open the USER_PROFILE message.
In the Publish Rule Definition region:
a. In the Publish Rule ID field, enter
IAM_USER_PROFILE.b. In the Description field, enter
IAM_USER_PROFILE.c. From the Status list, select Active.
Click Save.
Configure the PeopleSoft Integration Broker
The following sections explain the procedures to configure the PeopleSoft Integration Broker.
Configure the PeopleSoft Integration Broker Gateway
PeopleSoft Integration Broker is installed as part of the PeopleTools installation process.
The Integration Broker Gateway is a component of PeopleSoft Integration Broker, which runs on the PeopleSoft Web Server. It is the physical hub between PeopleSoft and the third-party system. The integration gateway manages the receipt and delivery of messages passed among systems through PeopleSoft Integration Broker.
Open a Web browser and enter the URL for PeopleSoft Internet Architecture. The URL for PeopleSoft Internet Architecture is in the following format:
http://IPADDRESS:PORT/psp/ps/?cmd=login. For example:http://172.21.109.69:9080/psp/ps/?cmd=login.- To display the Gateway component details, expand PeopleTools, Integration Broker, Configuration, and then click Gateways.
- In the Integration Gateway ID field, enter
LOCALand then click Search. The LOCAL gateway is a default gateway that is created when you install PeopleSoft Internet Architecture. - Ensure that the IP address and host name specified in the URL of the PeopleSoft listener are those on which the target system is installed. The URL of the PeopleSoft listener is in one of the following formats:
http://HOSTNAME_of_the_PeopleSoft_Web_ServerorIP_address:port/PSIGW/PeopleSoftListeningConnector. For example:http://10.121.16.42:80/PSIGW/PeopleSoftListeningConnector. - To load all target connectors that are registered with the LOCAL gateway, click Load Gateway Connectors. A window is displayed mentioning that the loading process is successful. Click OK.
- Click Save.
Click Ping Gateway to check whether the gateway component is active. The PeopleTools version and the status of the PeopleSoft listener are displayed. The status should be ACTIVE.
Configure PeopleSoft Integration Broker
PeopleSoft Integration Broker provides a mechanism for communicating with the outside world using XML files. Communication can take place between different PeopleSoft applications or between PeopleSoft and third-party systems. To subscribe to data, third-party applications can accept and process XML messages posted by PeopleSoft by using the available PeopleSoft connectors. The Integration Broker routes messages to and from PeopleSoft.
A remote node that you create within the Integration Broker acts as the receiver for XML messages from PeopleSoft. This remote node accepts XML messages and posts them as XML files to a folder that you specify. During a reconciliation run, a scheduled task running on Oracle Identity Manager uses the data in these XML files to Oracle Identity Manager.
While creating the remote node, you use the value of the
ig.fileconnector.passwordproperty in theintegrationGateway.propertiesfile. Determine the value of this property as follows:a. In the PeopleSoft Internet Architecture window, expand PeopleTools, Integration Broker, Configuration, and then click Gateways.
b. In the Integration Gateway ID field, enter LOCAL and then click Search.
c. Click the Gateway Setup Properties link.
d. Enter the user ID and password for accessing the
integrationGateway.propertiesfile, and then click OK.e. On the PeopleSoft Node Configuration page, click Advanced Properties Page. The contents of the
integrationGateway.propertiesfile are displayed.f. Search for
electroencephalographicin the file contents. The line displayed in the file may be similar to the following sample line:ig.fileconnector.password={V1.1}%5GhbfJ89bvNT1HzF98==.g. Copy the text after (that is, to the right of) the equal sign of the property. For example, copy
{V1.1}%5GhbfJ89bvNT1HzF98==from the line given in the preceding sample.Note: This is the password that you specify while creating the remote node. The sample password given here is encrypted. If the password displayed on your PeopleSoft installation isn't encrypted, then you can encrypt it by following the steps given later in this section.
In the PeopleSoft Internet Architecture window, expand PeopleTools, Integration Broker, Integration Setup, and then click Nodes.
On the Add a New Value tab, enter the node name, for example,
IAM_FILE_NODE, and then click Add.- On the Node Definition tab, provide the following values:
- In the Description field, enter a description for the node.
- In the Default User ID field, enter
PS.
Make this node a remote node by deselecting the Local Node check box and selecting the Active Node check box.
Make the Node Type as PIA.
- On the Connectors tab, search for the following information by clicking the Lookup icon:
- Gateway ID: LOCAL
- Connector ID: FTPTARGET
Once the Properties page is displayed after entering above information. On the Properties page in the Connectors tab, enter the following information:
- Property ID: HEADER
- Property Name: sendUncompressed
- Required value: Y
- Property ID: FTPTARGET
- Property Name: HOSTNAME
- Required value: Enter the hostname of the computer on which you want to generate the files. You can also give Identity Cloud Service hostname if ftp port is open.
- Property ID: FTPTARGET
- Property Name: USERNAME
- Required value: Enter the hostname of the computer on which you want to generate the files.
- Property ID: FTPTARGET
- Property Name: PASSWORD
- Required value: Enter the password of the computer on which you want to generate the files. Password should be in encrypted form. If the password isn't already encrypted, then you can encrypt it as follows:
- In the Password Encrypting Utility region, enter the value of the ig.fileconnector.password property in the Password and Confirm Password fields.
- Click Encrypt.
- From the Encrypted Password field, copy the encrypted password to the Value field for the Password property.
- Property ID: FTPTARGET
- Property Name: TYPE
- Required value: ASCII
- Property ID: FTPTARGET
- Property Name: METHOD
- Required value: PUT
- Property ID: FTPTARGET
- Property Name: FTPS
- Required value: N
- Property ID: FTPTARGET
- Property Name: FTPMODE
- Required value: ACTIVE
- Property ID: FTPTARGET
- Property Name: DIRECTORY
- Required value: Enter the location where you want to generate xmls.
- Property ID: HEADER
- Click Save.
Click Ping Node to check whether a connection is established with the specified IP address.
Configure the USER_PROFILE Service Operation
To configure the USER_PROFILE service operation, perform the following procedures.
Activate the USER_PROFILE Service Operation
The service operation is a mechanism to trigger, receive, transform, and route messages that provide information about updates in the PeopleSoft or an external application. You must activate the service operation for successful transmission and receipt of messages.
Note: If the message version isn’t the same as specified, then you can change the message version.
In PeopleSoft Internet Architecture, expand PeopleTools, Integration Broker, Integration Setup, and then click Service Operations.
On the Find Service Operation tab, enter
USER_PROFILEin the Service field, and then click Search.Click the USER_PROFILE link.
In the Default Service Operation Version region, click Active. The following screenshot displays the default version of the USER_PROFILE service operation:
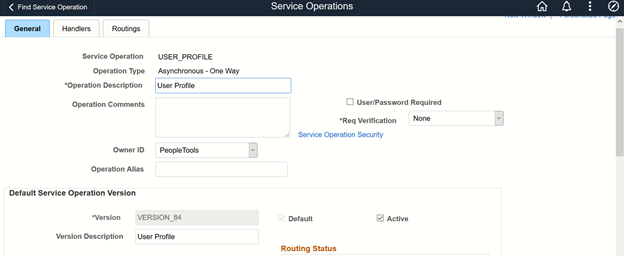
Click Save.
Verify the Queue Status for the USER_PROFILE Service Operation
All messages in PeopleSoft are sent through a queue. Queues ensure that the messages are delivered in the correct sequence. Therefore, you must ensure that the queue is in a Run status.
To ensure that the USER_PROFILE status of the queue for the service operation is Run:
In the PeopleSoft Internet Architecture window, expand PeopleTools, Integration Broker, Integration Setup, and then click Queues.
Search for the USER_PROFILE queue.
In the Queue Status list, ensure that Run is selected. If it is not, from the Queue Status list, select Run and click Save.
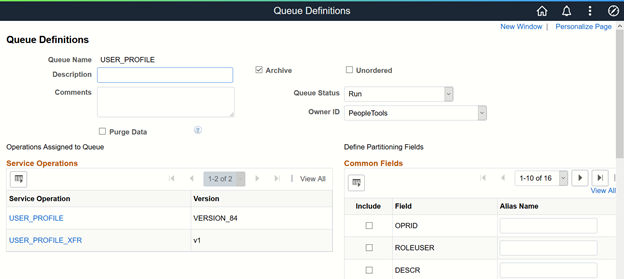
Click Return to Search.
Set Up the Security for the USER_PROFILE Service Operation
The target system user who has the permission to modify, add, or delete personal or job information of an employee might not have access to send messages regarding these updates. Therefore, it is imperative to explicitly grant security to enable operations.
In the PeopleSoft Internet Architecture window, expand NavBar, Navigator, PeopleTools, Integration Broker, Integration Setup, and then click Service Operations.
Search for and open the USER_PROFILE service operation.
On the General tab, click the Service Operation Security link. The link is shown in the following screenshot:
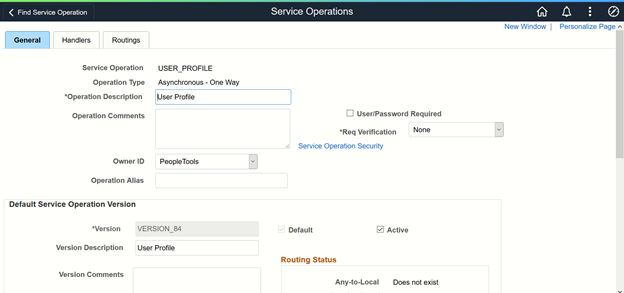
Attach the permission list IAMUM to the USER_PROFILE service operation.
To attach the permission list:
Note: This procedure describes how to grant access to the IAMUM permission list. The IAMUM permission list is used as an example. However, to implement this procedure you must use the permission list (attached through a role) to the user profile of the actual user who maintains the user profile information or the user who performs full reconciliation.
a. Click the plus sign (+) to add a row to the Permission List field.
b. In the Permission List field, enter
IDCSand then click the Look up Permission List icon. The IAMUM permission list appears.c. From the Access list, select Full Access.
d. Click Save.
e. Click Return to Search.
Define the Routing for the USER_PROFILE Service Operation
Routing is defined to inform PeopleSoft about the origin and the intended recipient of the message. You might have to transform the message being sent or received according to the business rules.
On the Routing tab, enter
USER_PROFILE_HR_TO_UMFILEas the routing name and then click Add.On the Routing Definition tab, enter the following: Sender Node:
PSFT_HRNote: The Sender Node is the default active local node. To locate the sender node:
a. Click the Lookup icon.
b. Click Default to sort the results in descending order.
The default active local node should meet the following criteria:
- Local Node: 1
- Default Local Node: Y
Node Type: PIA
Only one node can meet all the above conditions at a time.
c. Select the node. For Receiver Node, enter
IAM_FILE_NODE.d. Click Save.
- Click Save.
Click Return to go back to the Routings tab of the Service Operation and verify whether your routing is active.
Generate XML Files
If you’re using PeopleTools 8.50 and HCM 9.0, then before running Full Data Publish, you must apply the patch that addresses issue 824529. This patch can be downloaded from My Oracle Support.
You must run the Application Engine program if you’re performing the full reconciliation for the first time.
- In PeopleSoft Internet Architecture, expand Enterprise Components, Integration Definitions, Initiate Processes, and then click Full Data Publish.
- Click the Add a New Value tab.
- In the Run Control ID field, enter a value and then click ADD.
- In the Process Request region, provide the following values:
- Request ID: Enter a request ID.
- Description: Enter a description for the process request.
- Process Frequency: Select Always.
- Message Name: Enter
USER_PROFILEas the message name.
Click Save to save the configuration.
Click Run. The following screenshot displays the preceding steps:
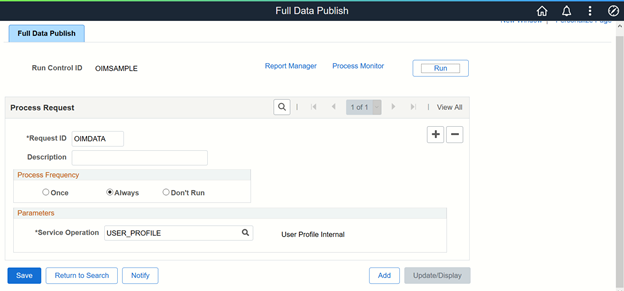
The Process Scheduler Request page appears.
From the Server Name list, select the appropriate server.
Select Full Table Data Publish process list and click OK. The following screenshot displays the Process Scheduler Request page:
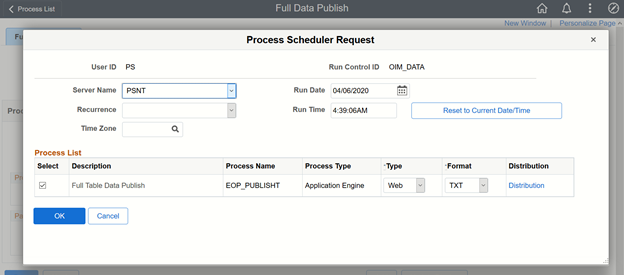
Click Process Monitor to verify the status of
EOP_PUBLISHTApplication Engine. The Run Status is Success if the transaction is successfully completed. On successful completion of the transaction, XML files for the USER_PROFILE message are generated at a location that you specified in the FilePath property while creating the IAM_FILE_NODE node for PeopleSoft Web Server. See Configure PeopleSoft Integration Broker for more information.Copy these XML files to a directory on the Oracle Identity Cloud Service host computer. Ensure that the permissions for these XML files are sufficiently restrictive. By default, the permissions are set to 644. You can set them to 640.
After you’ve performed this procedure:- Remove the permission list created in Set Up the Security for the USER_PROFILE Service Operation section. This is for security purposes.
- Disable the
USER_PROFILE_HR_TO_UMFILErouting created in Define the Routing for the USER_PROFILE Service Operation. To do so, clear the Active check box in Step 2 of the procedure.
Run the Application Engine Program
You can run the Application Engine program by using PeopleSoft Internet Architecture to perform Lookup Reconciliation.
Note: You must run the Application Engine program periodically.
Open a Web browser and enter the URL for PeopleSoft Internet Architecture. The URL is in the following format:
http://IPADDRESS:PORT/psp/ps/?cmd=login. For example:http://172.21.109.69:9080/psp/ps/?cmd=login.Click People Tools, Process Scheduler, Processes, and then Add a new Value.
Select Application Engine as the process type and enter
LOOKUP_RECONas the process name.Click Add.
- In the Process Definition Options tab, enter the following values for Component and Process Groups, and click Save.
- Component: AE_REQUEST
- Process Groups: TLSALL, STALL
To make the Application Engine program run in PeopleSoft Internet Architecture, click People Tools, Application Engine, Request AE, and then click Add a new Value.
- Enter values for the following and then click Add:
- User ID: Enter your User ID.
- Run Control ID: Enter a unique run control value.
- Program Name: Enter LOOKUP_RECON.
- Click Run.
- From the list that is displayed, select the LOOKUP_RECON process, which you created in Step 3.
Click OK.
To determine the progress status of the Application Engine program, click People Tools, Process Scheduler, and then Process Monitor. Click Refresh until Success message is displayed as the status.
Note: If Status is displayed as Queued, then you must check the status of the process scheduler. To do so, click People Tools, Process Scheduler, and then Process Monitor. Click the Server List tab and check the status of the server. If the status isn’t displayed, then start the process scheduler.
Enable and Associate Provisioning Bridge to the Oracle PeopleSoft App
Assign the Provisioning Bridge that you installed and configured to the on-premises Oracle PeopleSoft app in Oracle Identity Cloud Service. This bridge serves as a provisioning and synchronizing agent between Oracle Identity Cloud Service and the app.
Note: You installed and configured a Provisioning Bridge in Oracle Identity Cloud Service, and you added the Oracle E-Business Suite app to Oracle Identity Cloud Service.
In the Identity Cloud Service console, expand the Navigation Drawer, and then click Applications.
Click the Oracle E-Business Suite app that you added in Prerequisite Steps.
Click Provisioning.
Turn on the Enable Provisioning switch.
In the Confirmation window, click OK.
From the Associate with Provisioning Bridge list, select the Provisioning Bridge that you installed and configured in Prerequisite Steps. Note: If the Provisioning Bridge has an inactive status, then activate it. See Activate Provisioning Bridges.
In the Configure Connectivity section, use the following table to configure connectivity for establishing a connection with the Oracle E-Business Suite app:
Parameter Value Username Username of the target system account to be used for connector operations. User Password Password of the target system account specified by the User parameter. URL PeopleSoft domain URL. URL example: <IP_ADDRESS>:<Port> or <Hostname>:<Port>Domain Password Enter the PeopleTools Domain Connection Password. DelCompIntfcKey Name of the component interface used for delete operations. Generally, it is DELETE_USER_PROFILE.RwCompIntfcKey Name of the component interface used for create and update operations. Generally, it is USER_PROFILE_8_4X.XML Mapping This file contains the definitions used by the connector for various operations. This file is part of the Bridge. Check BRIDGE_HOME/dependencies/peoplesoftum_<latest-version>/xmlfolder for the file. Provide the complete path of this file in the configuration. If you don’t see the file, download the latest version of the Bridge.Path to read Files Folder path to the location of the property files mentioned in the ObjectClassesconfiguration. Path example:/scratch/psft/lookup_filesObject Classes Different object classes mapping for the dynamic data obtained by files. Sample values: __CURRENCYCODE__=currencycodes.properties,__LANGUAGECODE__=language.properties,__PERMISSIONLIST__=permission.properties,__ROLES__=roles.properties,__ACCOUNT__=/<path_to_user_xml_files_folder>. IMPORTANT: 1. Don't change this mapping unless a new configuration is added. 2. Update the folder path to the user xml files in configuration for__ACCOUNT__object class.Data Node Names Name of the node in the XML files to run a transaction Default value: Transaction You must not change the default value. Ignore root audit action Don't use. Reserved for use by Oracle. Use this value if the Root PSCAMA audit action is required to be considered while parsing the XML message. Use Yes if PSCAMA Audit Action isn’t considered. Here, the Root Audit Action is considered as a Change event. Use No if PSCAMA Audit Action is considered. If Root PSCAMA Audit Action is NULL or Empty, then the Root Audit Action is considered as an ADD event. Target Date Format Data format of the Date type data in the XML file and messages Don’t modify this entry. Default: yyyy-MM-dd. Click Test Connectivity to verify the connection with the Oracle PeopleSoft app. Oracle Identity Cloud Service displays a confirmation message.
To view predefined attribute mappings between the users in Oracle Identity Cloud Service and users in Oracle PeopleSoft, click Attribute Mapping, and then click OK.
Use the following table to see the default attribute mappings when users are provisioned from Oracle Identity Cloud Service to Oracle PeopleSoft.
Oracle Identity Cloud Service User Oracle PeopleSoft User $(user.userName) Name $(user.emails[primary=true].value) emailAddress $(user.active) active To add a new attribute mapping, click Add Row, specify the attributes in the User and Oracle PeopleSoft - User Management Account columns, and then click OK. For example, if you want to add the External ID user attribute, then enter
$(user.externalId)in the User column, and then select the corresponding field from the drop-down list in the Oracle PeopleSoft - User Management Account column.- Specify the provisioning operations that you want to enable for Oracle PeopleSoft Suite:
- Create Account: Automatically creates an Oracle PeopleSoft account when Oracle PeopleSoft access is granted to the corresponding user in Oracle Identity Cloud Service.
- Update Account: Automatically updates an Oracle PeopleSoft account when the corresponding user is updated in Oracle Identity Cloud Service.
- De-activate Account: Automatically activates or deactivates the Oracle PeopleSoft account when the corresponding user is activated or deactivated in Oracle Identity Cloud Service.
- Delete Account: Automatically revokes an account from Oracle PeopleSoft when Oracle PeopleSoft access is revoked from the corresponding user in Oracle Identity Cloud Service.
Turn on the Enable Synchronization switch.
- From the User Identifier drop-down list, select the Oracle Identity Cloud Service user attribute that you want to match with the corresponding record fetched from Oracle PeopleSoft Suite:
- Primary Email Address: Primary email address of the Oracle Identity Cloud Service user.
- User Name: User name of the Oracle Identity Cloud Service user. Note: By default, the Primary Email Address option is selected from the drop-down list. Leave this default attribute for accurate synchronization of user records.
To match an Oracle PeopleSoft account attribute with the existing Oracle Identity Cloud Service user, select an attribute from the Application Identifier drop-down list. Note: By default, the name option is selected. This option represents the Email attribute of the Oracle PeopleSoft account. Don't change this default option.
- From the When exact match is found drop-down list, select one of the following actions to be performed when a matching Oracle Identity Cloud Service user is found for an account:
- Link and confirm: Automatically links and confirms the matched account to the corresponding Oracle Identity Cloud Service user based on the defined User Identifier and Application Identifier fields.
- Link but do not confirm: Automatically links all matched accounts to the corresponding Oracle Identity Cloud Service users based on the defined User Identifier and Application Identifier fields. You need to confirm the linked accounts manually.
In the Max. number of creates field, enter a number that's greater than or equal to 10. This value limits the number of accounts to be created during the synchronization run.
In the Max. number of deletes field, enter a number that's greater than or equal to 10. This value limits the number of accounts to be deleted during the synchronization run.
Click Save, Activate, and then, in the Confirmation window, click OK. Oracle Identity Cloud Service displays a confirmation message.
Synchronize Data from Oracle PeopleSoft to Oracle Identity Cloud Service
In this section, you synchronize user accounts from Oracle PeopleSoft and link them to the corresponding Oracle Identity Cloud Service users. You also synchronize roles and permission lists for the accounts from Oracle PeopleSoft to Oracle Identity Cloud Service.
In the Oracle PeopleSoft app that you added in Prerequisite Steps, click the Import tab.
Click the Import button. If this button is grayed out, then click the Provisioning tab and verify that both Enable Provisioning and Enable Synchronization are turned on, and that the Oracle PeopleSoft Suite app is activated.
Verify that you see a status of Running for the job that Oracle Identity Cloud Service uses to synchronize users and roles from Oracle PeopleSoft Suite. After all users and roles are synchronized, the Import tab lists the Oracle PeopleSoft user accounts and the job status changes to Success.
If you don't see the status change after a few minutes, then click Refresh. Also, if the status of the job is Failed, then an error occurred while the Provisioning Bridge was transferring users and roles from Oracle PeopleSoft Suite to Oracle Identity Cloud Service.
- Oracle Identity Cloud Service tries to match each Oracle PeopleSoft Suite user account with an existing user in Oracle Identity Cloud Service. If a user exists, then the user is assigned to the Oracle PeopleSoft Suite app. If the user doesn't exist, then from the Actions column of the Import tab, you can perform one of the following actions:
- Assign Existing User: Assign the Oracle PeopleSoft user account to any user in Oracle Identity Cloud Service.
- Create New User and Link: Add a new user to Oracle Identity Cloud Service, and then assign the Oracle PeopleSoft user account to this newly created user.
Provision and Synchronize a User's Roles and Permission Lists
Use Oracle Identity Cloud Service to provision Oracle PeopleSoft roles and Permission list for a user that you synchronized from Oracle PeopleSoft. Then, you assign additional roles and permission list for the user in Oracle PeopleSoft, and synchronize these roles and permission list into Oracle Identity Cloud Service. The state of the user's roles and permission list is synchronized between Oracle PeopleSoft and Oracle Identity Cloud Service.
In the Oracle PeopleSoft app that you added, click the Users tab.
Click the Action menu to the right of the user to which you want to provision roles and permission list, and then select Edit from the menu that appears.
In the Assign Application window:
a. Click the Roles field, and then select a role that you want to provision to the user.
b. Click the Permission List field, and then select a responsibility for the user.
c. Click Save.
Note: By clicking Save, Oracle Identity Cloud Service provisions the user with the role and responsibility you selected.
Access the Oracle PeopleSoft console as an administrator and verify whether the user was created.
Revoke a User's Roles and Permission List
Use both Oracle Identity Cloud Service and Oracle PeopleSoft to revoke the roles and permission list of an Oracle PeopleSoft user.
In the Oracle PeopleSoft app that you added, click the Action menu to the right of the user to which you want to revoke roles and permission list, and then select Edit from the menu that appears.
In the Assign Application window, click the X button for the role and responsibility that you want to revoke from the user, and then click Save.
By clicking Save, Oracle Identity Cloud Service revokes the role and responsibility from the user.
Access the Oracle PeopleSoft console as an administrator and verify whether the role and responsibility was updated.
Revoke a User
Use Oracle Identity Cloud Service to revoke a user's access to Oracle PeopleSoft, and then verify in Oracle PeopleSoft that the user's access is revoked.
In the Oracle PeopleSoft app that you added, select the check box to the right of the user that you want to revoke from Oracle PeopleSoft, and then click Revoke.
In the Confirmation window, click OK.
In the Users page of the Oracle PeopleSoft console, use the User Name field to enter the user name of the Oracle PeopleSoft user to which you revoked access, and then click Go.
After the task is completed, the User will be deleted successfully in PeopleSoft.
Troubleshooting
Use this section to locate solutions to common integration issues.
For any issues, contact Oracle Support:
Go to https://support.oracle.com.
Select Cloud Support, and then sign in with your support credentials.
In the Cloud Dashboard, confirm that there are no planned outages in Oracle Identity Cloud Service, and then click Create Service Request.
Select Oracle Identity Cloud Service as the service type.
Complete your service request.