Topics:
Get Started with Oracle WebCenter Content 12c (12.2.1.4) on Marketplace
Provision Oracle WebCenter Content 12c (12.2.1.4) on Marketplace Instances
Get Started with Oracle WebCenter Content 12c (12.2.1.4) on Marketplace
Here’s information about Oracle WebCenter Content on Marketplace that will help you get started:
About Oracle WebCenter Content on Marketplace
Oracle WebCenter Content on Marketplace is provided as a VM-based solution on Oracle Cloud Infrastructure.
Oracle WebCenter Content on Marketplace is available in two types of Marketplace offerings: Paid and BYOL. See WebCenter Content Marketplace Licensing.
Oracle WebCenter Content on Marketplace helps customers to provision/set up the environment in few clicks and enables to deliver Content solutions on cloud.
About Roles and User Accounts
Oracle WebCenter Content on Marketplace uses roles to control access to tasks and resources. A role assigned to a user gives certain privileges to the user.
Access to Oracle WebCenter Content on Marketplace is based on the roles and users set up for the Oracle Cloud Infrastructure console. You need OCI Administrator role to provision WebCenter Content.
For information about how to add user accounts in Oracle Cloud, see:
Add Users to a Cloud Account with Identity Cloud Service in Getting Started with Oracle Cloud.
Managing Oracle Identity Cloud Service Users and Groups in the Oracle Cloud Infrastructure Console in the Oracle Cloud Infrastructure documentation.
Provision Oracle WebCenter Content 12c (12.2.1.4) on Marketplace Instances
The information in this chapter will help you create and view Oracle WebCenter Content on Marketplace instances.
Before You Begin
Before you begin, you would need to complete the following tasks and prerequisites.
Sign in to Oracle Cloud Infrastructure Console
Complete the following steps to sign in to the Oracle Cloud Infrastructure console.
Go to http://cloud.oracle.com.
Enter your cloud account name and click Next.
Sign in to the Oracle Cloud Infrastructure console:
If your cloud account uses identity domains, sign in to the Oracle Cloud Infrastructure console as a user configured in Oracle Cloud Infrastructure Identity and Access Management (IAM).
Select the domain you normally use to log in to the OCI console.
If your cloud account does not use identity domains, sign in to the Oracle Cloud Infrastructure console as a user federated through Oracle Identity Cloud Service.
Under Single Sign-On (SSO) options, note the identity provider selected in the Identity Provider field and click Continue.
Enter the user name and password provided in the welcome email, and click Sign In. The Oracle Cloud Infrastructure console is shown.
Prerequisites
You'll need to complete the following prerequisites before provisioning the WebCenter Content stack.
Configure Dynamic Groups and Policies for Non-Admin Delegated Users - This is required only when non-admin users need to provision the stack.
Setup DNS resolver to resolve Database domain - This is required only when VCNs used for Database and WebCenter Stack pre-exist and are different.
After completing the above prerequisites, you can proceed to provision the WebCenter Content stack.
System Requirements
You require access to the following services to use Oracle WebCenter Content on OCI.
Identity and Access Management (IAM)
Compute, Network, Block Storage, Block Volume
Vault, Key, Secret
Resource Manager
Database
Load Balancer
Tagging
Make sure you have the following minimum limits for the services in your Oracle Cloud Infrastructure tenancy, and if necessary, request for an increase of a service limit.
| Service | Minimum Limit |
|---|---|
| Identity and Access Management (IAM) Policy | 1 |
| Compute Shape VM.Standard.E4.Flex or VM.Standard.E5.Flex | 1 |
| Virtual Cloud Network | 1 |
| Block Storage | 1 TB |
| Block Volume | 50 GB |
| Vault & Key | 1 |
| Secrets | 1 |
| Load Balancer | Flexible Load Balancer |
In Oracle Cloud Infrastructure Vault (formerly known as Key Management), a standard vault is hosted on a hardware security module (HSM) partition with multiple tenants, and it uses a more cost-efficient, key-based metric for billing purposes. A virtual private vault provides greater isolation and performance by allocating a dedicated partition on HSM. Each type of vault has a separate service limit in your Oracle Cloud Infrastructure tenancy. The limit for secrets spans all the vaults.
See Service Limits in the Oracle Cloud Infrastructure documentation.
Generate SSH key pair
See Generate an SSH Key Pair for WebCenter for generating an SSH key pair.
This SSH key pair will be used for connecting to Bastion and Compute instances after stack execution.
Note: This will be used to create DB and WebCenter Content nodes.
Create a Compartment
If your tenancy does not already include a compartment for your Oracle WebCenter Content on Marketplace instances, you can create a new one.
Note: To create a compartment, your administrator must first add the following policy for your group: allow group groupName to manage compartments in tenancy
To create a compartment in Oracle Cloud Infrastructure:
Open the navigation menu and click Identity & Security. Under Identity, click Compartments. A list of the existing compartments in your tenancy is displayed.
Click Create Compartment.
Enter the following:
Name: Specify a name. For example, wcc-compartment. Restrictions for compartment names are: Maximum 100 characters, including letters, numbers, periods, hyphens, and underscores. The name must be unique across all the compartments in your tenancy.
Description: A friendly description.
Parent Compartment: Select the parent compartment where you want the new compartment to be created. When the parent compartment is not selected, the new compartment is created under the root compartment.
Click Create Compartment.
Once the compartment is created, if you are not an administrator, ask your administrator to complete the following steps to grant you the permissions needed to perform the required tasks in the compartment:
Note: You can use any name (wcc-admins, wcc-compartment, and wcc-policy are examples).
Create an IAM group with the user that will do the Marketplace install.
Navigate to Identity & Security, and then Domains.
If not already selected, select the compartment where you’ll install the Marketplace product.
Click the domain where you’ll create the group.
Click Groups.
On the Create group page, provide the following information:
- Name: wcc-admins
- Description: Webcenter Content Administrators
- Users: Add the user that will do the Marketplace installation.
Click Create.
Create a policy with the permissions to perform the required tasks in the compartment.
Navigate to Identity & Security, and then Policies.
Click Create Policy and provide a name (for example, wcc-policy).
Create a policy with the following statements.
allow group wcc-admins to manage instance-family in compartment wcc-compartment
allow group wcc-admins to manage virtual-network-family in compartment wcc-compartment
allow group wcc-admins to manage volume-family in compartment wcc-compartment
allow group wcc-admins to manage load-balancers in compartment wcc-compartment
allow group wcc-admins to manage orm-family in compartment wcc-compartment
where
wcc-adminsis the group name andwcc-compartmentis the compartment name.
Create a Master Key
You'll need to create a master key for the vault.
Open the navigation menu and click Identity & Security and then Vault.
Change the necessary compartment.
Click the already created vault name.
On the left side, click Master Encryption keys and then click Create Key.
Complete the following:
Create In Compartment : Name of the selected compartment
Protection Mode: Software
Name: Specify a name.
For remaining fields, retain the default values.
Click Create Key.
Wait for the status to show green.
Create Database
You can follow the below steps to create a new Oracle Database instance (or you can use an existing database too).
Note: Currently, Autonomous Database Serverless - Transaction Processing, Autonomous Database on Dedicated Exadata Infrastructure, Exadata Database Service on Dedicated Infrastructure, and Base Database are supported. For any additional questions, contact the Oracle Support team.
Complete the following to create a new DB service instance:
Create VCN
Note: If you plan to create Autonomous Database Serverless, you can skip the VCN creation and move to the next step.
Log in to OCI Console, navigate to Networking, then to Virtual Cloud Networks.
Click Create VCN via Wizard.
Click Start VCN Wizard.
VCN name: Provide a name.
Compartment: Specify the compartment in which the VCN needs to be created.
VCN IPv4 CIDR block: Specify IPv4 CIDR block (for example, 10.0.0.0/16).
Select the Use DNS hostnames in this VCN check box.
In the Configure public subnet and Configure private subnet sections, specify the correct CIDR blocks and click Next.
Make sure to create the necessary gateways such as Internet gateway, NAT gateway, and Service gateway.
Click Create. The VCN is created.
Create a New Database
Follow the below OCI documentation links for creating OCI Database resources based on the preferred service.
Base Database (Single Node or RAC) : See Provision a Base Database Service for more information.
Note: The base database should be created with minimum 2 cores/OCPUs.
Autonomous Database Serverless (Transaction Processing) : See Provision an Autonomous Database Service for more information.
Autonomous Database on Dedicated Exadata Infrastructure : See Provision an Autonomous Database on Dedicated Exadata Infrastructure for more information.
Exadata Database Service on Dedicated Infrastructure: See Provision an Exadata Database Service on Dedicated Infrastructure for more information.
Create IDCS Application
An IDCS confidential application is needed to configure the IDCS security provider in Weblogic domain during provisioning.
If you are creating the stack as a private service (Checking Enable Private Service option), then the Identity Domain needs to be homed in the same region where the stack is going to be provisioned. Please ensure this before creating the application.
| Note |
|---|
| There is an alternate option to auto-create the application along with stack creation. If you prefer to choose that, then the provisioning user needs to be granted Identity Domain Administrator role in the domain’s security settings (see Adding Identity Domain Administrators) and the same user needs to create the stack. If you prefer that option, you can skip this requirement and choose Auto-Create Domain App option during stack provisioning. |
Follow the below instructions based on whether OCI Tenancy IAM is with Identity Domains or not.
For OCI accounts where IAM is with Identity Domains (tenancy with IAM domains), complete the following:
Log in to OCI console.
Navigate to Identity and then Domains.
Select the domain which needs to be used for SSO log-in.
Go to Integrated Applications and click Add application.
Choose Confidential Application and launch the workflow.
On the Add Application Details page, fill the Name and Description fields, and then click Next.
On the Configure OAuth page, select the Configure this application as a client now option under Client configuration section.
In the Authorization section, select the Client credentials check box for the Allowed Grant Types field.
Scroll down and select the Add app roles check box. In the App roles section, add the Identity Domain Administrator role.
Click Next. Leave the default settings for the next page as is and click Finish.
Make a note of the client ID and client secret. These values will be needed when you run the script.
Activate the application.
For OCI accounts where IDCS is not yet migrated to IAM Domains (tenancy without IAM domains), complete the following:
Log in to the IDCS administration console of the federated IDCS.
For example,
https://idcs-abcde.identity.oraclecloud.com/ui/v1/adminconsole.Navigate to Applications. Click + to add an application. Choose Confidential Application in the wizard:
Add a name and a description on the App details page.
Click Next. Select the Configure this application as a client now option.
In the Authorization section, select the Client credentials check box for the Allowed Grant Types field.
In the Grant the client access to Identity Cloud Service Admin APIs section, click Add to add the application roles. You need to add the Identity Domain Administrator role.
Click Next. Leave the default settings for the next pages as is and click Finish.
Make a note of the client ID and client secret. These values will be needed when you run the script.
Activate the application.
Create the Object Storage Bucket in OCI
Click the navigation menu in the upper left corner of the page and click Storage.
Click Buckets.
Confirm that you're in the correct compartment and the correct region.
Click Create Bucket on the "Buckets in <compartment name> Compartment" page.
Provide a value for Bucket Name.
Leave the Default Storage Tier set to Standard.
Leave the Encryption set to Encrypt using Oracle managed keys.
Click Create.
See Object Storage Buckets for more information.
Create a New User API Key
Click on your avatar in the upper-right corner of the page.
Click My profile.
In the Resources menu on the left side of the page, click API Keys.
Click Add API Key.
Download the private key by clicking Download private key. The private key will be added to the vault's secret later.
Click Add.
Click Copy to copy the content of the configuration file which has user OCID and fingerprint as this will be required later. Close the dialog.
Create Vault Secrets
Log in to the OCI console and search for Vault, and then create a vault app.
Click Create Vault.
Provide a name and click Create Vault.
Click the vault app you created earlier. Create a master encryption key by specifying the compartment, protection mode, name, algorithm, length, and so on in the Create Key section.
Click Secrets on the left side and start adding secrets by specifying the compartment, name, key, secret type template, secret contents, and so on in the Create Secret section.
| Secret Name | Secret Description | Comment |
|---|---|---|
| wcc-admin-password | Secret for WebCenter Content Admin Password | The Secret Contents field should be populated with the Weblogic password value. The password needs to meet the following password policy: The password must be at least 8 alphanumeric characters with at least one number or a special character. |
| db-system-sys-password | Secret for DB System SYS Password | SYS user password of DB created in the Create a New Database section should be used in the Secret Contents field. Required only if chosen database service is Base Database. |
| db-system-ssh-private-key | Secret for DB System SSH private key | The Secret Contents field should be populated with the passphrase of private key value that was used to create DB in the Create a New Database section. Required only if chosen database service is Base Database. |
| db-system-ssh-private-key-passphrase | Secret for DB System SSH private key’s passphrase | The Secret Contents field should be populated with the private key’s passphrase value that was used to create DB in the Create a New Database section. Required only if chosen database service is Base Database and Key is passphrase protected. |
| exadata-db-sys-password | Secret for Exadata Database SYS Password | SYS user password of Exadata database created in the Create a New Database section should be used in the Secret Contents field. Required only if chosen database service is Exadata Database Service on Dedicated Infrastructure. |
| exadata-db-ssh-private-key | Secret for Exadata Database SSH private key | The Secret Contents field should be populated with the private key value that was used to create DB in the Create a New Database section. Required only if chosen database service is Exadata Database Service on Dedicated Infrastructure. |
| exadata-db-ssh-private-key-passphrase | Secret for Exadata Database SSH private key’s passphrase | The Secret Contents field should be populated with the private key’s passphrase value that was used to create DB in the Create a New Database section. Required only if chosen database service is Exadata Database Service on Dedicated Infrastructure and Key is passphrase protected. |
| atp-db-password | Secret for Autonomous Database Admin Password | Admin user password of Autonomous database created in the Create a New Database section should be used in the Secret Contents field. Required only if chosen database service is Autonomous Database Serverless or Autonomous Database on Dedicated Exadata Infrastructure. |
| idcs-client-secret | Secret for IDCS Client secret | The Secret Contents field should be populated with the Client Secret value that was noted when the IDCS Confidential App was created in the IDCS section. |
| wcc-schema-password | Secret for WCC schema password. | The password needs to meet the following password policy: •The password must start with a letter. •The password must contain at least two digits. •The password must contain at least two uppercase letters. •The password must contain at least two lowercase letters. •The password must contain at least two special characters from the set [$#_]. •The password must be of at least 15 characters and maximum 30 characters in length. Example: OCI#db#456789123 |
| oci-user-private-key | Secret for user API private key | The Secret Contents field should be populated with the private key value downloaded earlier in the Create a New User API Key section. |
Provision WebCenter Content Stack
You can provision Oracle WebCenter Content on a Marketplace instance in a selected compartment in Oracle Cloud Infrastructure.
| Note |
|---|
| In the Stack Configuration section, you can select the Quick Start check box to quickly provision a WebCenter environment using default values. See Quick Start for WebCenter for more information. |
To provision Oracle WebCenter Content on a Marketplace instance:
Navigate to the WebCenter Content listing on Marketplace by direct URL or by browsing in Oracle Cloud Infrastructure.
Using direct URL:
In your browser, enter https://cloudmarketplace.oracle.com/marketplace/en_US/homePage.jspx?tag=WebCenter+Content.
The Marketplace listings for WebCenter Content are displayed.
Click the title of the listing you want to use. The landing page of that listing is displayed.
Click Get App.
Select your Oracle Cloud Infrastructure region and click Sign In.
By browsing:
Open the navigation menu and click Marketplace. Under Marketplace, click All Applications.
In the Marketplace search field, enter WebCenter Content.
The Marketplace listings for WebCenter Content are displayed.
Click the title of the listing you want to use and review the information on the Overview page.
Accept the terms and restrictions, and then click Launch Stack. The Create Stack wizard is displayed.
Provide information about the stack for the instance.
Stack information:
Enter name and description.
Create in Compartment: Select the compartment.
Terraform version: Specify the Terraform version and click Next.
Configure variables:
Stack Configuration
Resource Name Prefix: Enter a prefix (for example, WCC). The name of all compute and network resources will begin with this prefix. It must begin with a letter and it can contain only letters or numbers.
SSH Public key: Provide the SSH public key (created in Generate SSH key pair).
Quick Start: Select this check box to quickly provision a WebCenter Content environment using default values. See Quick Start for WebCenter for more information.
OCI Policies: Select this check box if you need the stack to create policies to provision WebCenter Content resources, configure Database Network, and read Vault Secrets. Deselecting this option is for Advanced users only. See Configure Dynamic Groups and Policies for Non-Admin Delegated Users for more information.
Enable Authentication Using Identity Cloud Service: Select this check box if you need to use Identity Cloud Service (IDCS) as the security provider in WebCenter Content. If not selected, the local Weblogic identity store will be used.
Enable Private Service: Select this check box if you need to provision service in private subnet for Fast Connect usage. Service Gateway is required for private service provisioning. Please create service gateway and add route for all services in webcenter subnet route table. If you plan to remove service gateway from VCN then please configure DRG
Enable All Traffic via 443 Port: Select this check box if you need to enable all external traffic via 443 load balancer listener port only.
Secrets Key Management
OCI Vault compartment: Select the compartment for OCI vault.
Use pre-created OCI Vault Secrets: Select this check box if you need to use pre-created KMS Secrets. If not selected, a new KMS secret and KMS encryption key will be created in the given OCI vault. If selected, you need to pre-create vault secrets as mentioned in Create Vault Secrets.
OCI Vault to store secrets: Select the OCI vault to store new KMS secret. This option is visible when the Use pre-created OCI Vault Secrets check box is not selected.
OCI Vault to fetch secrets: Select the OCI vault to fetch pre-created KMS secrets. This option is visible when the Use pre-created OCI Vault Secrets check box is selected.
Virtual Cloud Network
If you're using an existing VCN, complete the following:
Network Compartment: Select the compartment you created earlier.
Existing WebCenter Content Virtual Cloud Network: Select the VCN provisioned for WebCenter Content.
Ensure the existing VCN has the required subnets and route tables as mentioned in Create VCN.
If you need to use a new VCN, then select the Create the Virtual Cloud Network check box and complete the following:
Network Compartment: Select the compartment you created earlier.
Virtual Cloud Network Name: Specify a name for the new VCN to be created for this service.
Virtual Cloud Network CIDR: Specify a CIDR to assign to the new VCN.
Content Storage
Content Storage Strategy: Select a content storage strategy from the drop-down list. The available options are Database, File System, and Object Storage.
If you selected Object Storage as the content storage strategy, complete the following:
Object Storage Compartment: Select the compartment where the bucket was created.
Bucket Name: Specify the bucket name which you created earlier. It should be between 1 and 16 characters long and must start with a letter, followed by alphanumeric characters, hyphens, or underscores.
User OCID: This will be pre-populated with the current user's OCID. If you are using a different user for creating the API key, specify the user OCID of that user.
Public Key Fingerprint: Specify the fingerprint from the configuration file (that you copied when you created the user API key as part of the prerequisites).
OCI User Private Key: Upload the user API private key. This is applicable only if the Use pre-created OCI Vault Secrets check box is not selected.
Secret for OCI User Private Key: Select the secret for the user API private key. This is applicable only if the Use pre-created OCI Vault Secrets check box is selected.
Database
Database Strategy: Select the type of database to use for provisioning. The supported databases are: Database System, Autonomous Transaction Processing Database, and Exadata Database.
If you selected Autonomous Transaction Processing Database as the Database Strategy, then complete the following that are displayed:
Select the value for Autonomous Database compartment.
Select the value for Autonomous Database.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
- **Autonomous Database Admin Password**: Provide the value of Autonomous Database Admin Password.
- If you selected **Use pre-created OCI Vault Secrets**, then complete the following that are displayed. - **Secret for Autonomous Database Admin Password**: Select the secret for Autonomous Database Admin Password.If you selected Database System as the Database Strategy, then complete the following that are displayed:
Select the value for DB System compartment.
Select the value for DB System Instance Name.
PDB name: Provide the PDB name of the DB system.
DB System PDB User: Leave the value 'sys' as is. Do not change this user name.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
DB System Password: Provide the value of DB System password.
DB System SSH Private key: Upload the DB System SSH Private key which is created.
Passphrase needed for DB System SSH Private key: Check if the private key is passphrase protected.
Passphrase for DB System SSH Private key: Provide the value for DB System SSH key passphrase.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for DB System Password: Select the secret for DB system password. When defining the secret key, you must have specified a user-friendly name for each secret. Use the same name here so that it is easy.
Secret for DB System SSH Private key: Select the secret for DB System SSH private key.
Passphrase needed for DB System SSH Private key: Check if the private key is passphrase protected.
Secret for DB System SSH Private key passphrase: Select the secret for DB System SSH private key’s passphrase.
If you selected Exadata Database as the Database Strategy, then complete the following that are displayed:
Select the value for Exadata Database compartment.
Exadata DB Home OCID: Provide the OCID of Exadata DB Home.
Select the value for Exadata Database.
Exadata Database PDB name: Provide the PDB name of the Exadata database.
Exadata Database PDB User: Leave the value 'sys' as is. Do not change this user name.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Exadata Database Password: Provide the value of the PDB user password for the Exadata database.
Exadata Database SSH Private key: Upload the Exadata database SSH Private key created without passphrase.
Passphrase needed for Exadata Database SSH Private key: Check if the private key is passphrase protected.
Passphrase for Exadata Database SSH Private key: Provide the value for Exadata Database SSH key passphrase.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for Exadata Database Password: Select the secret for Exadata database password. When defining the secret key, you must have specified a user-friendly name for each secret. Use the same name here so that it is easy.
Secret for Exadata Database SSH Private key: Select the secret for Exadata Database SSH private key.
Passphrase needed for Exadata Database SSH Private key: Check if the private key is passphrase protected.
Secret for Exadata Database SSH Private key passphrase: Select the secret for Exadata Database SSH private key’s passphrase.
Database Schema Strategy: Select the database schema strategy to use for provisioning. The supported schema strategies are: Create New Database Schemas and Use existing Database Schemas. The option Create New Database Schemas will create new database schemas with the given schema prefix. The option Use existing Database Schemas will try to find and use existing database schemas with the given schema prefix and provisioning will fail if database schemas matching the given schema prefix don’t pre-exist.
Database Schema Prefix: Provide a value for database schema prefix. It should not be longer than 12 characters and should start with a letter followed by uppercase alphabets and numeric characters.
Bastion Instance:
If you're using an existing VCN, complete the following:
Bastion Strategy: Select a bastion strategy from the drop-down list. The available options are Create New Bastion Instance, and Use Existing Bastion Instance.
If you selected Create New Bastion Instance as the Bastion Strategy, then complete the following that are displayed:
Existing Subnet for Bastion Host: Select an existing public subnet to use for a Bastion compute instance.
Bastion Host Shape: Select the appropriate Bastion host shape (keep the default value).
If you selected Use Existing Bastion Instance as the Bastion Strategy, then complete the following that are displayed:
Public IP of Bastion Instance: Provide the public IP of existing Bastion and make sure it is reachable for new WebCenter compute instances.
SSH Private Key Bastion Instance: Select the appropriate SSH Private key to access the bastion instance. This private key should not contain passphrase.
WebCenter Content Compute Instance:
Compute Shape: Select the appropriate compute shape.
OCPU count: Select the OCPU count. The default value is 2.
If you're using an existing VCN, complete the following:
Existing Subnet for WebCenter Content Compute Instances: Select an existing subnet to use for WebCenter Content compute instances.
Node Count: Specify the node count. The default value is 2.
File System:
Use Existing File System: Select this check box to use an existing File System and Mount Target.
If selected, you will need to select the compartment and availability domain of the existing File System and provide the File System OCID. The Mount Target must have security rules configured to allow traffic to the chosen VCN CIDR. See Configuring VCN Security Rules for File Storage.
File System Compartment: Choose the compartment where the WebCenter Content stack will be created.
File System Availability Domain: Select the Availability Domain.
Mount Target Subnet CIDR: Provide the value for Mount Subnet CIDR. For example, 10.0.5.0/24.
Load Balancer:
If you're using an existing VCN, complete the following:
Existing Subnet for Load Balancer: Select an existing subnet to use for the load balancer.
Provide the value for Minimum Bandwidth for Flexible Load Balancer.
Provide the value for Maximum Bandwidth for Flexible Load Balancer.
Identity Domain:
Auto-Create Identity Domain App: If this option is selected, then a new IDCS App will be created during stack provisioning. It requires the provisioning user to be granted Identity Domain Administrator role in the selected Domain. If this is not feasible and IDCS application is already created as part of pre-requisites, this option can be deselected.
If you are creating the stack as a private service (Checking Enable Private Service option), then the Identity Domain needs to be homed in the same region where the stack is going to be provisioned.
If you selected Auto-Create Identity Domain App option, then complete the following that are displayed:
Identity Domain Compartment: Select the compartment of identity domain.
Identity Domain Name: Provide the name of identity domain.
Identity Domain Username: Provide the value for IDCS username who will be configured as the product administrator.
If you deselected Auto-Create Identity Domain App option, then complete the following that are displayed:
Identity Domain URL: Provide the value for IDCS domain URL.
Identity Domain Username: Provide the value for IDCS username who will be configured as the product administrator.
Identity Client ID: Provide the value for IDCS Client ID created in Prerequisites.
Identity Client Secret: Provide the value for IDCS Client Secret. This is applicable only if the Use pre-created OCI Vault Secrets check box is not selected.
Secret for the Identity Client Secret: Select the secret for the IDCS client secret. This is applicable only if the Use pre-created OCI Vault Secrets check box is selected.
WebCenter Content WebLogic Domain Configuration:
- WebCenter Content Admin User Name: Leave the value 'weblogic' as is.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
WebCenter Content Admin Password: Provide the value for WebCenter Content Admin password.
WebCenter Content Schema Password: Provide the value for WebCenter Content Schema password.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for WebCenter Content Admin Password: Select the secret for WebCenter Content administrator password.
Secret for the WebCenter Content Schema Password: Select the secret for the WebCenter Content schema password.
Click Next. Review all the configuration variables and then select the Run apply check box under Run apply on the created stack section. Click Create.
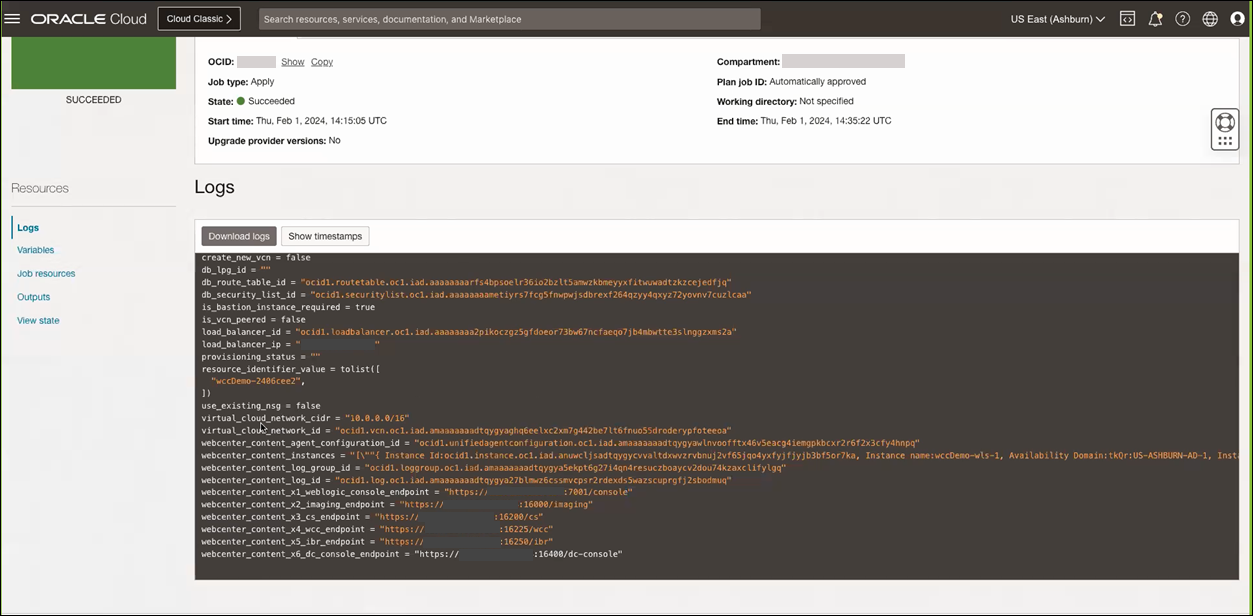
If everything goes as expected, then navigate to the WebCenter Content stack and click the Application Information tab. You'll see all the provisioned end points for the services under section WebCenter Content Endpoints:
webcenter_content_x1_weblogic_console_endpoint =
"https://<host-IP>:7001/console"webcenter_content_x2_imaging_endpoint =
"https://<host-IP>:16000/imaging"webcenter_content_x3_cs_endpoint =
"https://<host-IP>:16200/cs"webcenter_content_x4_wcc_endpoint =
"https://<host-IP>:16225/wcc"webcenter_content_x5_ibr_endpoint =
"https://<host-IP>:16250/ibr"webcenter_content_x6_dc_console_endpoint =
"https://<host-IP>:16400/dc-console"
After provisioning the stack, to create a connection from Imaging to WebCenter Content:
Note: You should not use the public IP of load balancer when making the RIDC connection. To get the private IP of WebCenter Content Load Balancer for RIDC connection, log in to OCI console and navigate to the load balancer details page for WebCenter Content load balancer. Click Backends sets. From the list of backend sets, click the backend set having a name like %-intradocsvr-bset. Hover the mouse over the green tick (next to OK) to get the private IP of the load balancer.
Note:
If you see a stale web location when opening content in the Content Server application (when content is created via Imaging application), then do the following to resolve this issue:
Update the following file in all the WebCenter Content node VMs when you create an application in the Imaging application:
/u01/data/domains/wcc_domain/ucm/cs/data/ipmsys/apps/app<app-no>.hdaIn the
app<app-no>.hdafile, update the value forViewerUrlFormatwith correct host name and port of Imaging application:ViewerUrlFormat=https://<hostname>:<port>/imaging/faces/Pages/UrlTools.jspx?ToolName=AWVWR&DocumentId=%sAfter making this change, you need to bounce all the WebCenter Content servers from the Weblogic console.
To navigate to the WebCenter Content stack:
In the side menu, select Developer Services, Resource Manager, and then Stacks.
Select your compartment and click the name of the WebCenter Content stack you created.
If something goes wrong or if for any reason you want to do a clean-up of all the resources that were provisioned as part of the WebCenter Content deployment, use Destroy Job to do the clean-up.
Troubleshoot
This chapter describes common problems that you might encounter and also provides information that can be helpful with the troubleshooting process.
Issue: Provisioning failed
Description
If you encountered a failure when trying to provision WebCenter Content, do the following to see the logs which might help in troubleshooting:
Log in to bastion host.
From bastion host perform ssh to wls-1 VM. For example:
ssh -I <private key> opc@<IP Address of wls-1 VM>sudo su – oraclecd /u01/data/domains/logsvi provisioning.log
Issue: Stale web location when opening content in the Content Server application
Description
If you see a stale web location when opening content in the Content Server application (when content is created via Imaging application), then do the following to resolve this issue:
Update the following file in all the WebCenter Content node VMs when you create an application in the Imaging application:
/u01/data/domains/wcc_domain/ucm/cs/data/ipmsys/apps/app<app-no>.hdaIn the
app<app-no>.hdafile, update the value forViewerUrlFormatwith the correct host name and port of Imaging application:ViewerUrlFormat=https://<hostname>:<port>/imaging/faces/Pages/UrlTools.jspx?ToolName=AWVWR&DocumentId=%sAfter making this change, you need to bounce all the WebCenter Content servers from the Weblogic console.
| Note |
|---|
| If you have further issues, raise a support ticket in My Oracle Support and attach logs. You can collect logs using the package logs tool described in Package Logs for Troubleshooting. |
Appendix
This appendix provides supporting information related to WebCenter Content stack-provisioning, OpenSearch, and also includes information about known issues.
How to Access WebCenter Content IBR Endpoint accessible via a Private Loadbalancer IP?
WebCenter Content IBR endpoint is accessible via a private loadbalancer IP. Complete the following steps to access this endpoint using SSH tunnelling:
Obtain the Load Balancer private IP from the Stacks UI.
Go to Stacks and then <created_stack>
Click the Application Information tab.
In the Networking section, Load Balancer Private IP will be available.
Execute the following from your local machine:
ssh -i <ssh_private_key_for_bastion> -L 16250:<lb_private_ip>:16250 opc@<bastion_ip>
Access the IBR endpoint using: https://localhost:16250/ibr
About OpenSearch 2.x
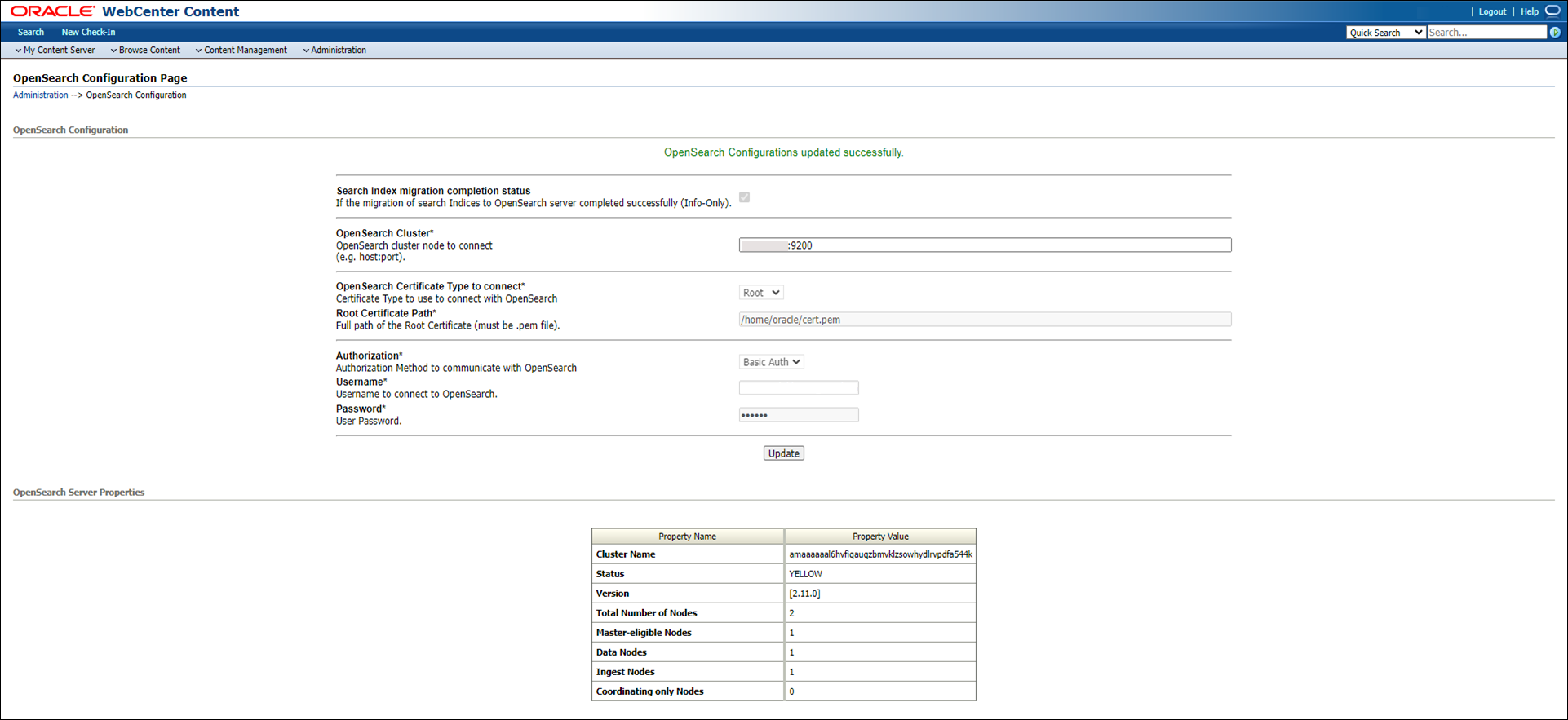
Note: You need to use Basic Auth as the authorization method if you are using OpenSearch 2.11.
When configuring OpenSearch 2.11 for WebCenter Content with OCI, use the following steps to get the OpenSearch certificate and test the connection from WebCenter Content instance to the OpenSearch cluster.
To get the OpenSearch certificate, in a shell of WebCenter Content instance, run the following command:
openssl s_client -showcerts -connect <OpenSearch private IP>:9200 </dev/null | sed -n -e '/-.BEGIN/,/-.END/ p' > cert.pemTo test the connection from WebCenter Content instance to the OpenSearch cluster:
/usr/bin/curl -u <username>:<password> https:<OpenSearch private IP>:9200 –insecureThis is merely a simple test to see if WebCenter Content instance can reach the OS cluster. If successful, it will return the following:
[oracle@wcctestinstance ~]$ /usr/bin/curl -u <username>:<password> https://<OpenSearch private IP>:9200 { "name" : "opensearch-master-0", "cluster_name" : "amaaaaaal6hvfiqauqzbmvklzsowhydlrvpdfa544kitmgdymnugepq5nkwq", "cluster_uuid" : "EtrnIgjXQmmuK4gBdf02xg", "version" : { "distribution" : "opensearch", "number" : "2.11.0", "build_type" : "tar", "build_hash" : "unknown", "build_date" : "2024-05-28T05:20:26.940869407Z", "build_snapshot" : false, "lucene_version" : "9.7.0", "minimum_wire_compatibility_version" : "7.10.0", "minimum_index_compatibility_version" : "7.0.0" }, "tagline" : "The OpenSearch Project: https://opensearch.org/" }
The following image shows the OpenSearch Configuration Page when Basic Auth is used as the authorization.
Configure FA Adapter Integration with WebCenter Content
Learn to install and configure FA integration (using AdapterFA component) with WebCenter Content on marketplace. See Extending Oracle Fusion Applications with Managed Attachments.
Configure SAML2 IDCS Single Sign-On in WebCenter Content
Learn to configure SAML2 IDCS Single Sign-On in WebCenter Content.
Prerequisites
Complete the following before running the configuration script.
Create a WebCenter Content Stack
A WebCenter Content stack should have been created from OCI Marketplace on which SAML2 IDCS SSO configuration needs to be configured.
Create an OAuth Client for IDCS
Follow the below instructions based on whether OCI Tenancy IAM is with Identity Domains or not.
For OCI accounts where IAM is with Identity Domains (tenancy with IAM domains), complete the following:
Log in to OCI console.
Navigate to Identity and then Domains.
Select the domain which needs to be used for SSO log-in.
Go to Integrated Applications and click Add application.
Choose Confidential Application and launch the workflow.
On the Add Application Details page, fill the Name and Description fields, and then click Next.
On the Configure OAuth page, select the Configure this application as a client now option under Client configuration section.
In the Authorization section, select the Client credentials check box for the Allowed Grant Types field.
Scroll down and select the Add app roles check box. In the App roles section, add the Identity Domain Administrator role.
Click Next. Leave the default settings for the next page as is and click Finish.
Make a note of the client ID and client secret. These values will be needed when you run the script.
Activate the application.
For OCI accounts where IDCS is not yet migrated to IAM Domains (tenancy without IAM domains), complete the following:
Log in to the IDCS administration console of the federated IDCS.
For example,
https://idcs-abcde.identity.oraclecloud.com/ui/v1/adminconsole.Navigate to Applications. Click + to add an application. Choose Confidential Application in the wizard:
Add a name and a description on the App details page.
Click Next. Select the Configure this application as a client now option.
In the Authorization section, select the Client credentials check box for the Allowed Grant Types field.
In the Grant the client access to Identity Cloud Service Admin APIs section, click Add to add the application roles. You need to add the Identity Domain Administrator role.
Click Next. Leave the default settings for the next pages as is and click Finish.
Make a note of the client ID and client secret. These values will be needed when you run the script.
Activate the application.
Configuration in WebCenter Content Stack
Run the Configuration Script
A configuration helper script will be available in WebCenter Content stack VM. It can be executed from Admin compute VM or VM-1 (*-wls-1).
The script expects the following inputs.
| Argument | Description |
|---|---|
| idcs_tenant | IDCS tenant name For example, if IDCS URL is idcs-abcde.identity.example.com, then IDCS tenant name would be idcs-abcde. |
| idcs_domain | IDCS domain For example, if IDCS URL is idcs-abcde.identity.example.com, then IDCS domain would be identity.example.com. |
| idcs_client | Client ID of the OAuth client created in prerequisites |
| idcs_client_secret | Client secret of the OAuth client created in prerequisites |
| service_host | WebCenter Content stack service host with DNS record mapped to load balancer IP. For example, wccstack1.xyz.com If service host is not available, WebCenter Content stack load-balancer IP can be provided here for testing. |
| idcs_user_name | IDCS user who is configured as WebCenter product administrator user |
Complete the following steps to execute the script:
ssh -o ProxyCommand="ssh -W %h:%p -i <key> opc@<bastion-ip>" -i <key> opc@<vm-ip>
sudo su - oracle
cd /u01/scripts/sh
nohup sh configure_sso.sh --idcs_tenant <idcs-tenant> --idcs_domain identity.oraclecloud.com --idcs_client <idcs_client> --idcs_client_secret <idcs_client> --idcs_username <idcs_username> --service_host <service_host> &
The script execution progress can be monitored from /u01/data/domains/logs/provisioning.log. Once the execution completes without any error, the configuration is completed in WebCenter Content stack environment.
This script covers the steps mentioned in Configuring SAML 2.0 (IDCS) Single Sign-On.
Note: If the configuration was done with load-balancer IP, then the above script needs to be executed again with the service host once the DNS mapping to load-balancer IP is created.
Configuration in your IDCS Tenant
Once the SAML configuration is completed on WebCenter Content, SAML applications will be created under Integrated Applications in the IDCS domain. The WebCenter Content role mapping groups (as described in the table below) are also created.
| WebCenter Content Groups | Description |
|---|---|
| admin | The admin role is assigned to the system administrator. By default, this role has Admin permission to all security groups and all accounts, and has rights to all the administration tools. |
| contributor | The contributor role has Read and Write permissions to the Public security group, which enables users to search for, view, check in, and check out content. |
| guest | The guest role has Read permission to the Public security group, which enables users to search for and view content. |
| sysmanager | The sysmanager role has privileges to access the Admin Server links from the Administration menu in the user interface. |
The Admin user is granted membership to the admin group and can be used to access the service.
The SAML applications will be prefixed with the stack service name. For example, wcc12_ucm_saml, wcc12_capture_saml, wcc12_wcc_saml, and wcc12_imaging_saml.
Add Users to Groups
To add a new user other than the administrator, you would need to add the user to the IDCS WebCenter Content groups based on the permissions required for their usage.
Verification
After the configuration of SAML, verify the WebCenter Content application URLs and validate that the IDCS SSO log-in is working.
Content Server: https://<service_host|lb_ip>:16200/cs
Web UI: https://<service_host|lb_ip>:16225/wcc
Capture: https://<service_host|lb_ip>:16400/dc-console
Imaging: https://<service_host|lb_ip>:16000/imaging
Multi-threaded Indexing
WebCenter Content’s legacy indexer is a single-threaded process and is specifically designed to run only on one of the servers configured in a cluster.
The MultiThreadIndexer component is designed to introduce some amount of parallelism to the existing legacy indexer, thus increasing the indexing throughput. The design of MultiThreadIndexer component now supports ORACLETEXTSEARCH (OTS), ELASTICSEARCH and OPENSEARCH search indexer engines and allows text extraction and search index building to be performed parallelly. This feature is seamless and transparent to the end-user and all the functionalities including UI remain the same.
To use the new MultiThreadIndexer feature:
Enable the MultiThreadIndexer component.
Configure one of the above supported search indexer engines and enable MultiThreadIndexer in the config.cfg file:
SearchIndexerEngineName=ORACLETEXTSEARCH EnableMultiThreadIndexer=trueRestart the WebCenter Content servers.
To manage search features in WebCenter Content, see Managing Search Features. To manage OracleTextSearch, see Managing OracleTextSearch.
Note:
You can set the ForceMetadataOnlyIndexing configuration variable to true to force the indexer to perform metadata-only indexing irrespective of the search engine configured. Thus, this improves the indexing performance for scenarios where you want to use a full-text based search engine like OracleTextSearch or OpenSearch but do not require full-text indexing capabilities.
You can set the ValidateMaxIndexableFileSizeEarly configuration variable to true to check and validate whether the uploaded document’s file size is higher than the MaxIndexableFileSize limit configured while indexing. The default value is 10 MB. A document with its file size higher than the MaxIndexableFileSize limit will not be downloaded to the filesystem as it would not go through the text extraction process and therefore improves indexing performance.
Conversational Search
Learn about the integration of Retrieval-Augmented Generation (RAG) in WebCenter Content (on Marketplace) using OCI Search with OpenSearch which provides support for creating an OCI Generative AI connector. You can do the following.
- Choose one of the LLM for creating RAG pipeline using OCI Search with OpenSearch.
- Perform conversational search on a single document or a group of documents by passing prompt along with the search query.
Prerequisites
WebCenter Content (on Marketplace) should be configured with OCI Search Service.
OCI Search Service with OpenSearch should be on version 2.11. By default, new clusters are configured to use version 2.11. For existing clusters configured for version 2.3, you can perform an inline upgrade to version 2.11.
To use OCI Generative AI, your tenancy must be subscribed to one of the regions with Generative AI.
The node configuration of the OCI Search Service should be of type Application Search.
Create a policy to grant access to Generative AI resources. The following policy example includes the required permissions:
ALLOW ANY-USER to manage generative-ai-family in tenancy WHERE ALL {request.principal.type='opensearchcluster', request.resource.compartment.id='<cluster_compartment_id>'}Use the settings operation of the Cluster APIs to configure the recommended cluster settings that allow you to create a connector. The following example includes the recommended settings:
PUT _cluster/settings { "persistent": { "plugins": { "ml_commons": { "only_run_on_ml_node": "false", "model_access_control_enabled": "true", "native_memory_threshold": "99", "rag_pipeline_feature_enabled": "true", "memory_feature_enabled": "true", "allow_registering_model_via_local_file": "true", "allow_registering_model_via_url": "true", "model_auto_redeploy.enable":"true", "model_auto_redeploy.lifetime_retry_times": 10 } } } }
Enabling Smart Content Component
- Log in to WebCenter Content as an administrator.
- Navigate to Administration, Admin Server, Component Manager, and then Advanced Component Manager.
- Select the SmartContent component and click Enable.
- Restart the server once the component is enabled.
Enabling Conversational Search
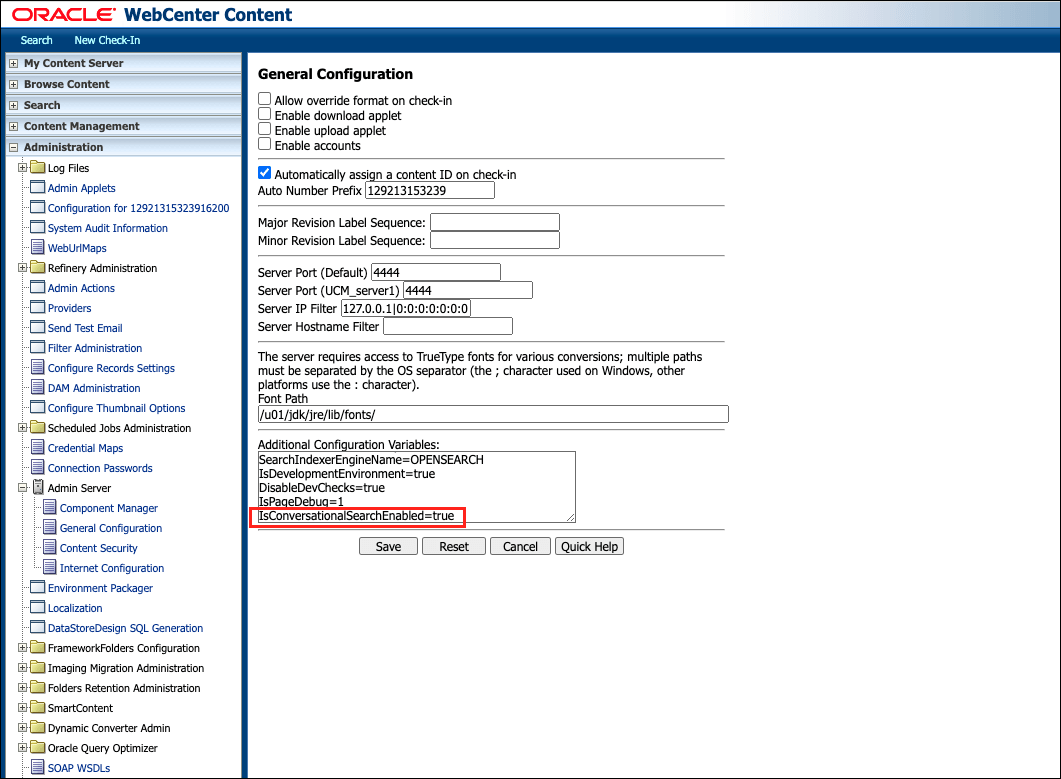
- Log in to WebCenter Content as an administrator.
- Navigate to Administration, Admin Server, and General Configuration.
- Add the following flag in the Additional Configuration Variables section.
IsConversationalSearchEnabled=true - Restart the server
Configuration
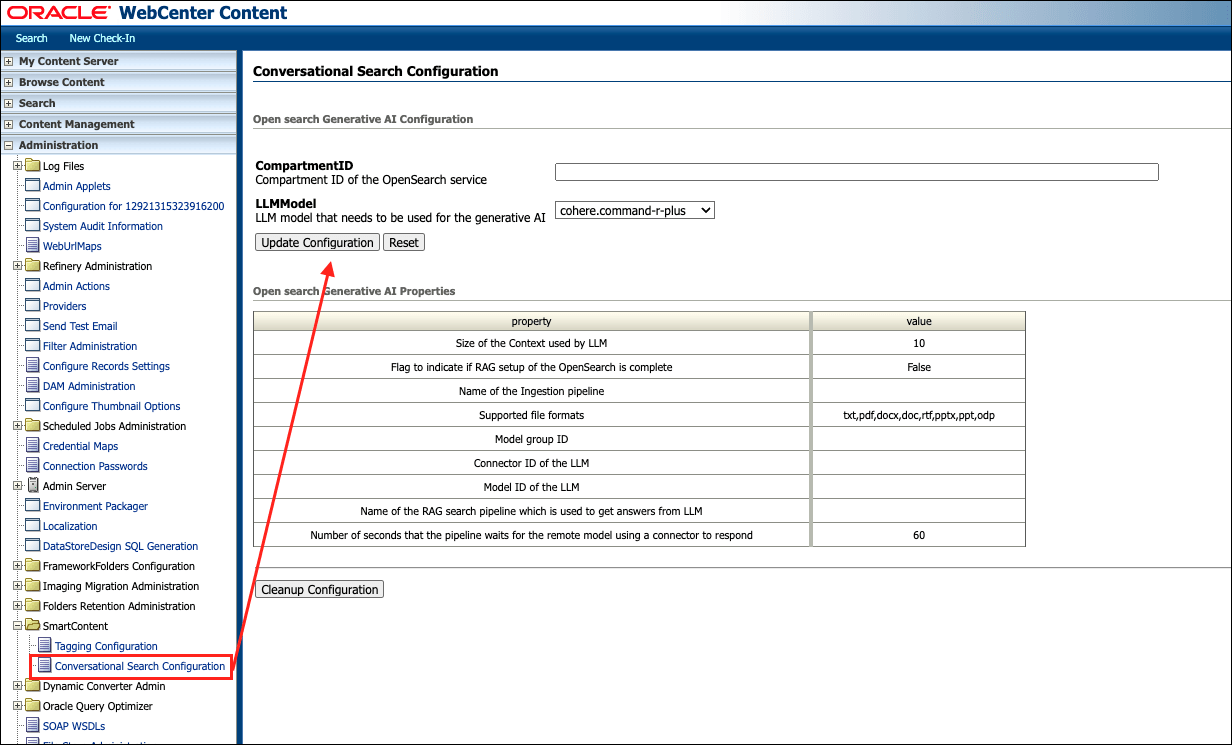
Log in to WebCenter Content as an administrator.
Navigate to Administration, SmartContent, and then Conversational Search Configuration.
Provide the following values in the configuration screen.
Name Description CompartmentID Compartment ID of the OpenSearch service.
Note: An invalid value for the compartmentID will not cause the configuration to fail. However, the API call to get the LLM response will fail with an appropriate error message.LLMModel LLM model that needs to be used for the generative AI Once configured, click UpdateConfiguration to save the configuration.
Note: Creating RAG pipeline involves multiple calls to the OpenSearch cluster. If you encounter gateway timeout issues, increase the timeout value of the cs-lsnr for your load balancer.
Setting Up RAG Pipeline
| Name | Description |
|---|---|
| Size of the Context used by LLM | Number of search results that are used as the context for the Large Language Model. 10 in case of cohere.command-r-plus and meta.llama-3.1-70b-instruct |
| Flag to indicate if RAG setup of OpenSearch is complete | Flag which denotes if the RAG pipeline is ready to use. In case of any failure during the setup, this is set to false. |
| Model Group ID | ID of the Model group. For access control, models are organized into model groups. |
| Name of the Ingestion pipeline | Ingestion pipeline which is used to truncate the data of the file to first 1000 words. |
| Name of the RAG search pipeline | Search pipeline which is used for Retrieval-Augmented Generation. |
| Number of seconds the pipeline waits for the response | LLM response timeout in seconds. Default value is 60 seconds. |
| Supported file formats | File formats on which conversational search can be done. |
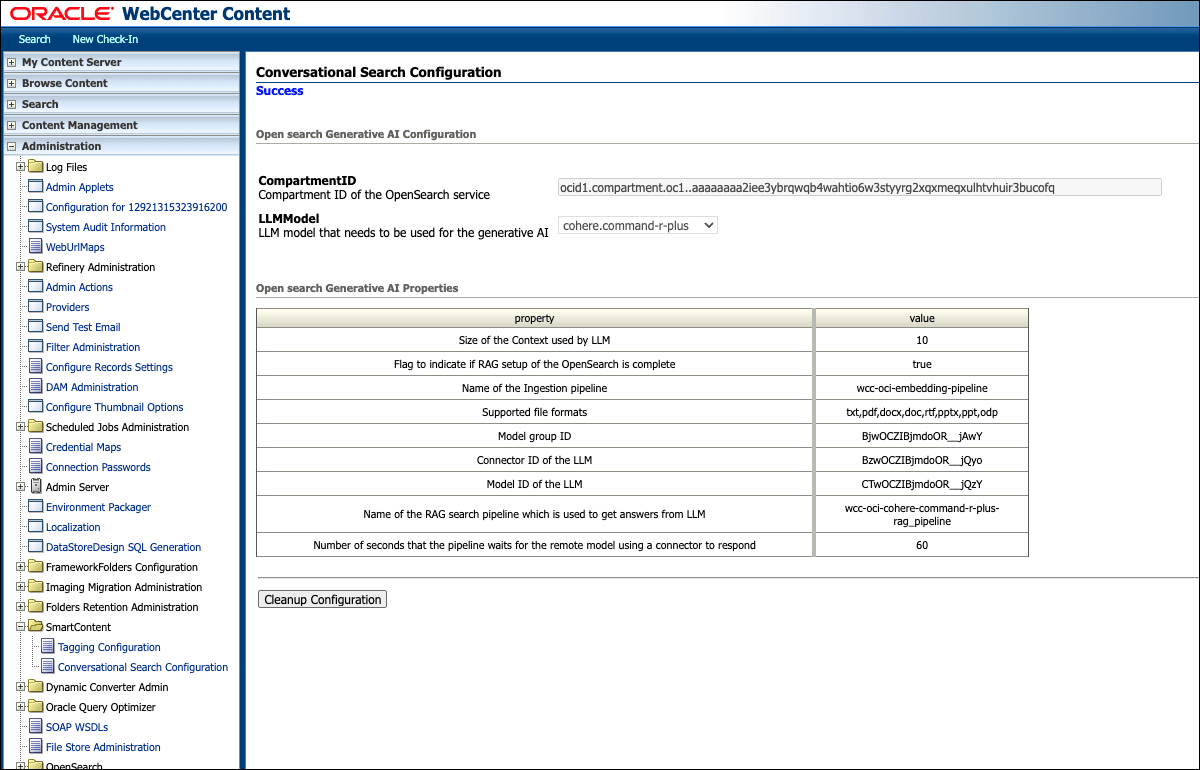
Cleanup
- Log in to WebCenter Content as an administrator.
- Navigate to Administration, SmartContent, and then Conversational Search Configuration.
- Click Cleanup Configuration.
Cleanup can be invoked any number of times irrespective of the flag which indicates the RAG set-up status. In case of error, user is expected to use OCI search service APIs to cleanup.
NOTE:
- Conversational search can be performed only on documents uploaded or edited after the configuration is completed.
- Support for existing documents will be introduced in future releases.
- After an index rebuild, it is necessary to clean up and recreate the configuration.
Configure Two-Legged or Three-Legged OAuth
Learn to configure two-legged or three-legged authorization for WebCenter Content.
Overview
To complete this configuration you will need to:
- Access the IDCS administration console to create a confidential client app (for two-legged authentication) or a mobile client app (for three-legged authentication)
- Configure the WebCenter Content Server
Configuring SAML 2.0 (IDCS) Single Sign-On
If the Stack is created without enabling IDCS Authentication or it’s created from a release older than 24.12.1, SAML 2.0 configuration needs to be executed again to apply the OAuth changes. if the Stack is created from a release older than 24.12.1, It’s required to patch the environment to latest release. Execute the script as mentioned in Configuration in WebCenter Content Stack.
This step can be skipped if the stack is created with release version from 24.12.1 onwards and IDCS Authentication is enabled during provisioning.
Create IDCS Applications
To support two-legged or three-legged authentication, an IDCS application needs to be created. A confidential client app is required for two-legged authentication; or a mobile client app is required for three-legged authentication.
Create a Confidential Client Application
To use two-legged authentication, complete the following steps:
Log in to the IDCS administration console.
Navigate to Identity, Domains, OracleIdentityCloudService Domain, and then Integrated Applications. Click Add Application to add a new application.
Select Confidential Application and click Launch Workflow.
Give the application a name and optionally, a description. Click Next.
Choose to configure this application as a client.
Under Authorization, Allowed Grant Types, select the following grants:
- Client Credentials
- Resource Owner
- Refresh Token grants
Scroll down to the Token Issuance Policy section. Under Resources, select Add Resources to show the Resources table and then click Add Scope to give the application access to the required WebCenter Content instance.
Select the correct instance. Click the right arrow to select the scope. The only scope required is the one ending with
/wcc:opc:all. Select the check box next to it and then click Add.Click Next until the end of the workflow.
Click Finish.
Select Activate and then click Save to enable the application.
Add the following groups one by one to the application from the Groups menu under Resources on the left panel.
admin
contributor
guest
sysmanger
WebcenterGroup
Note the
Client IDandClient Secretvalues for the client application.
Create a Mobile Client Application
To use three-legged authentication, complete the following steps:
Log in to the IDCS administration console.
Navigate to Identity, Domains, OracleIdentityCloudService Domain, and then Integrated Applications. Click Add Application to add a new application.
Select Mobile Application and click Launch Workflow.
Give the application a name and optionally, a description. Click Next.
Choose to configure this application as a client.
Under Authorization, Allowed Grant Types, select the Authorization grant.
Set the Redirect URL to the WebCenter Content URL. For example:
https://
wcc-host:wcc-port/csScroll down to the Token Issuance Policy section. Under Resources, select Add Resources to show the Resources table and then click Add Scope to give the application access to the required WebCenter Content instance.
Select the correct instance and then click the right arrow to select the scope. The only scope required is the one ending with
/wcc:opc:all. Select the check box next to this scope and click Add.Click Next until the end of the workflow.
Click Finish.
Select Activate and then click Save to enable the application.
Note the
Client IDvalue for the client application.
Generate Authorization Code
WebCenter Content supports the PKCE security model.
Create the code_verifier and code_challenge with the PKCE Code Generator tool.
Configure WebCenter Content
Enable the IDCSIntegration Component
- Log in to WebCenter Content as an administrator.
- Navigate to Administration, Admin Server, Component Manager, and then Advanced Component Manager.
- Select the IDCSIntegration component and click Enable.
Configure Two-Legged Authentication
The server needs to use clientID created in IDCS by the Confidential Client Application. A user with admin privileges needs to set this in config.cfg:
| Name | Default | Description | Example |
|---|---|---|---|
| IDCSRegisteredIntegrationClients | null | The comma separated Confidential Client application IDs. | IDCSRegisteredIntegrationClients=clientID1,clientID2,clientIDn |
The server must be restarted at this point.
A WebCenter admin user must log in and sync the server with the IDCS application by logging into WebCenter Content and going to this URL:
https://
wcc-host:wcc-port/cs/idcplg?IdcService=SYNC_IDCS_CLIENT_APPS&IsJson=1
Get an Access Token from IDCS
Use the clientID and secret created in IDCS by the Confidential Client application to get an AccessToken using a curl command:
curl -X POST https://
idcs-url-for-tenancy/oauth2/v1/token -H ‘Authorization: BasicBase64_encoded: clientID:clientSecret’ -d ‘grant_type=client_credentials&scope=https://wcc-host/wcc:opc:all’
IDCS will return a response similar to:
{“access_token”:“
access-token-value”}
This access-token-value can be used to access WebCenter Content.
Configure Three-Legged Authentication
The IDCSIntegration component must be enabled and the server must be restarted.
Get an Access Token from IDCS
Any user can get an authz-code with the following URL. If the user has not logged in, IDCS will prompt for login.
https://
idcs-url-for-tenancy/oauth2/v1/authorize?client_id=IDCSMobileClientID&response_type=code&redirect_uri=https://wcc-host:wcc-port/cs&scope=https://wcc-host/wcc:opc:all&code_challenge=fromTool&code_challenge_method=S256
Use the following POST request without an authorization header. It is recommended to use code challenge. The request token request must be made with the IDCS mobile client ID to get the bearer token for the user for whom we generated the authorization code.
curl https://
idcs-url-for-tenancy/oauth2/v1/token –header ‘Content-Type: application/x-www-form-urlencoded; charset=utf-8’
–data-urlencode ‘grant_type=authorization_code’
–data-urlencode ‘code=authz-code’
–data-urlencode ‘client_id=MobileClientID’
–data-urlencode ‘code_verifier=fromPKCETool’
Known Issues
24.8.1 — August 2024
| Feature | Description |
|---|---|
| New Redwood UI | The new Redwood UI supports English only as the UI language and does not offer any translation/localization to other languages. Accessibility guidelines pertaining to WCAG have not been tested for the new Redwood UI. There are alternative UIs, namely the Native UI and the ADF UI that meet the accessibility guidelines. You can use these alternative UI options in case you find any accessibility limitations with the new Redwood UI. |
25.6.1 — June 2025
| Feature | Description |
|---|---|
| MultiThreadIndexer | With the latest changes to the multi-thread indexer in an effort to decouple it completely from the core indexer to achieve full parallelism, the “Empty Quick Search” is not working with all the 3 full-text search engines (OTS, ES & OS) and will be addressed in the next monthly release. Here are few limitations in the current release and these will be fixed in the future monthly releases - • From the Administration -> Admin Actions page (also from Repository Manager Applet), triggering the Automatic Update Cycle will have no effect. • From the Administration -> Admin Actions page (also from Repository Manager Applet), triggering the **Index Rebuild (Fast or Full)“** will have no effect. • In case customer has requirement to add new searchable metadata field, then such customers should disable Multi-Thread Indexer component, because new searchable metadata fields are not yet supported with Multi-Thread Indexer feature. • In case customer has a requirement to switch from other search engines to OTS or ES or OS, then such customers should disable Multi-Thread Indexer component, because”Index Rebuild” is not yet supported with Multi-Thread Indexer feature. |
25.7.1 — July 2025
| Feature | Description |
|---|---|
| MultiThreadIndexer | As part of our ongoing efforts to enhance the performance of the MultiThreadIndexer, the latest updates focus on fully decoupling it from the UCM legacy indexer to enable complete parallelism. While these changes lay the groundwork for significant long-term improvements, the July 2025 release includes a few limitations that users should be aware of. Limitations: ============ 1) Automatic Update Cycle: Triggering the Automatic Update Cycle from Administration –> Admin Actions or via the Repository Manager Applet will not have any effect. 2) Index Rebuild (Fast or Full): Initiating an Index Rebuild (Fast or Full) from Administration –> Admin Actions or via the Repository Manager Applet will not function as expected. 3) New Searchable Metadata Fields: If your use-case involves adding new searchable metadata fields, please disable the MultiThreadIndexer component. This feature is not currently supported with the MultiThreadIndexer enabled. 4) Switching Search Engines: If you need to switch between search engines (OTS, Elasticsearch or OpenSearch), you must disable the MultiThreadIndexer component. The Index Rebuild process is not yet supported in this configuration. 5) Inbound Refinery (IBR): Inbound Refinery (IBR) conversions and workflow use cases are not supported. 6) OracleTextSearch (OTS): We are working on addressing a critical issue with OracleTextSearch search engine and we do not recommend using OTS with MultiThreadIndexer with July 2025 release. 7) Archiver and Replication: Archiver and Replication is not supported yet. 8) Indexing native vault file: UseNativeFormatInIndex configuration is not supported yet. These limitations are being actively addressed and will be resolved in upcoming releases. |
Using Oracle WebCenter Content 12c (12.2.1.4) on Marketplace in Oracle Cloud Infrastructure
F98077-13
Last updated: August 2025
Copyright © 2025, Oracle and/or its affiliates.
Primary Author: Oracle Corporation