Prerequisites for a Private Endpoint
To provision an Oracle Fusion Data Intelligence instance with a private endpoint, you must have the following resources already created:
- A virtual cloud network (VCN) within the region where you plan to deploy Oracle Fusion Data Intelligence and a private subnet in your VCN with availability of /28 (14 IP addresses)
IP address or more. You can change this after provisioning.To avoid instance creation failures, ensure the following toggles are enabled:
- The Use DNS hostnames in this VCN toggle, while creating the VCN.
- The Use DNS hostnames in this Subnet toggle, while creating the subnet.
- Ensure that you (or whoever plans to create the Oracle Fusion Data Intelligence instance) have the required policies to access the VCN.
Choose the most appropriate level for you from these options:
Limited Resource Access Policy
-
Allow any-user to use vnics in tenancy where request.principal.type = 'fawservice' -
Allow any-user to read vcns in tenancy where request.principal.type = 'fawservice' -
Allow any-user to use network-security-groups in tenancy where request.principal.type = 'fawservice' -
Allow any-user to use private-ips in tenancy where request.principal.type = 'fawservice' -
Allow any-user to use subnets in tenancy where request.principal.type = 'fawservice'
If you want to view and manage your virtual network family from the Oracle Cloud Infrastructure Console, then you may want to create these policies:
-
Allow group FAWAdmin.grp to read virtual-network-family <in compartment your-compartment or in tenancy> -
Allow group FAWAdmin.grp to manage vnics <in compartment your-compartment or in tenancy> -
Allow group FAWAdmin.grp to use subnets <in compartment your-compartment or in tenancy> -
Allow group FAWAdmin.grp to use private-ips <in compartment your-compartment or in tenancy>
Broad Resource Access Policy
Allow any-user to manage virtual-network-family in tenancy where request.principal.type = 'fawservice'If you want to view and manage your virtual network family from the Oracle Cloud Infrastructure Console, then you may want to create this policy:Allow group FAWAdmin.grp to manage virtual-network-family <in compartment compartment-name or in tenancy>Apart from these, you must create the following general service policies:
-
Allow group FAWAdmin.grp to manage analytics-warehouse <in compartment your-compartment or in tenancy> -
Allow group FAWAdmin.grp to read analytics-warehouse-work-requests <in compartment your-compartment or in tenancy> -
Allow group FAWAdmin.grp to manage autonomous-database-family <in compartment your-compartment or in tenancy> -
Allow group FAWAdmin.grp to manage analytics-instances <in compartment your-compartment or in tenancy> -
Allow group FAWAdmin.grp to read analytics-instance-work-requests <in compartment your-compartment or in tenancy>
-
- Optional: If you plan to restrict traffic (ingress and egress) using network security
group rules, then you must do so when you create your Oracle Fusion Data Intelligence instance. You can specify up to 5 network security groups to meet your
business requirements. Ensure that the network security groups exist in the same
VCN as your Oracle Fusion Data Intelligence and you have this required policy to use network security groups:
Allow group FAWAdmin.grp to use network-security-groups <in compartment your-compartment or in tenancy>See “To create an NSG” in Network Security Groups.
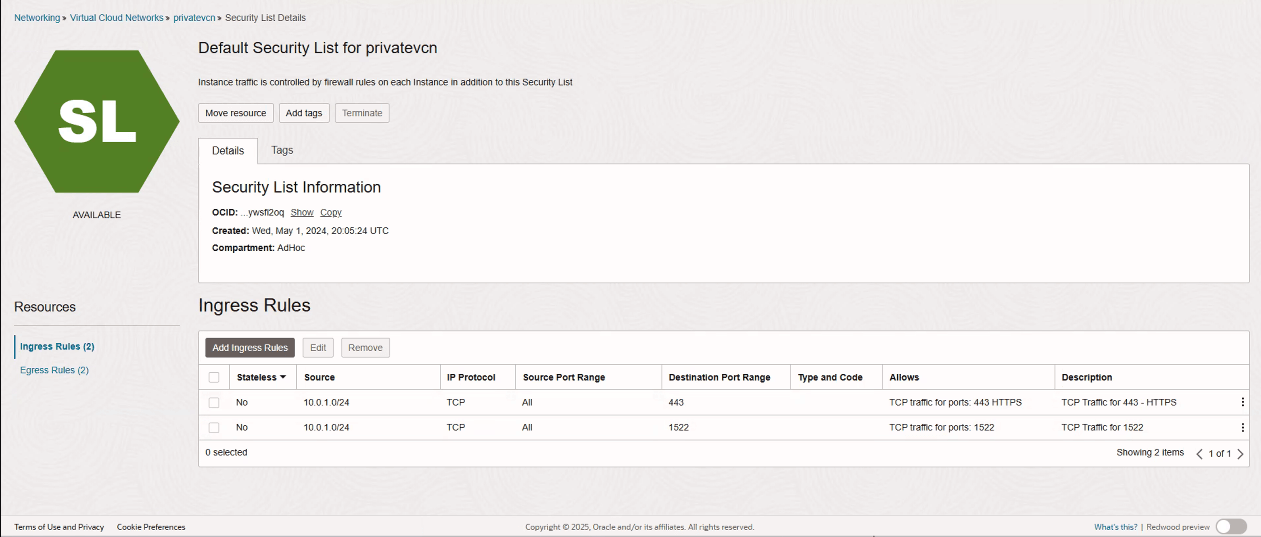
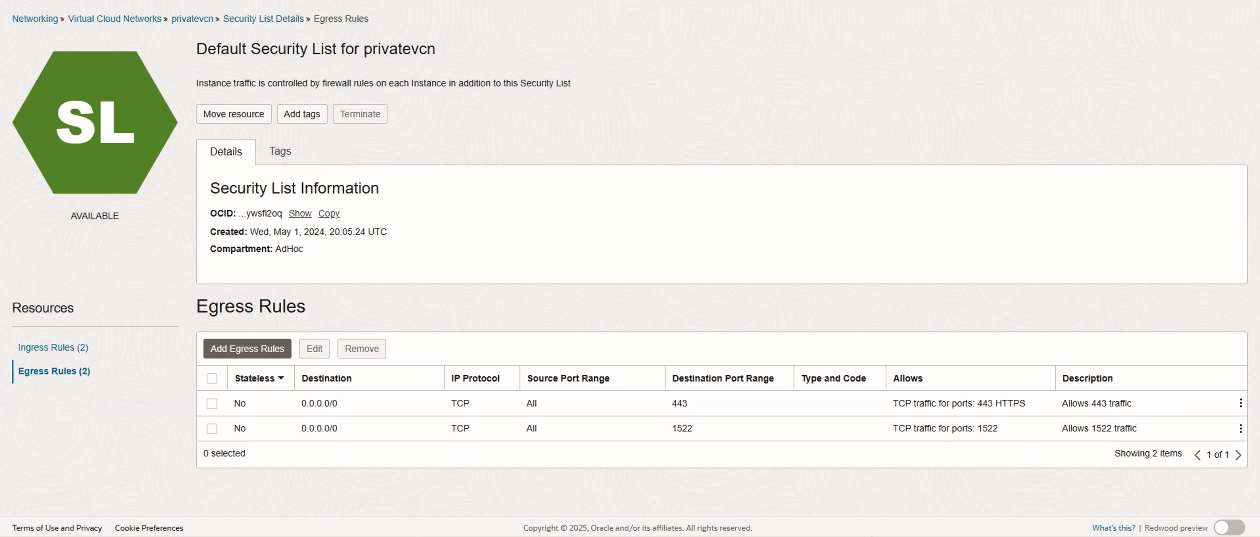
- Inbound traffic specified on Port 1522 for Oracle Autonomous Data Warehouse and Port 443 for Oracle
Analytics Cloud while entering the security rule information for the network security group
or VCN. Ensure that the VCN/SUBNET CIDR block allows ingress and egress in the
rules to ports 443 and 1522.
Note:
Both of these ports are required for the functioning of Oracle Fusion Data Intelligence instance with a private endpoint.