- Using B2C Service
- Agent Login Using an IdP-initiated SSO
Agent Login Using an IdP-initiated SSO
IdP-initiated SSO for agents occurs when single sign-on is enabled for agents who log in to the agent desktop by first logging into an external identity provider.
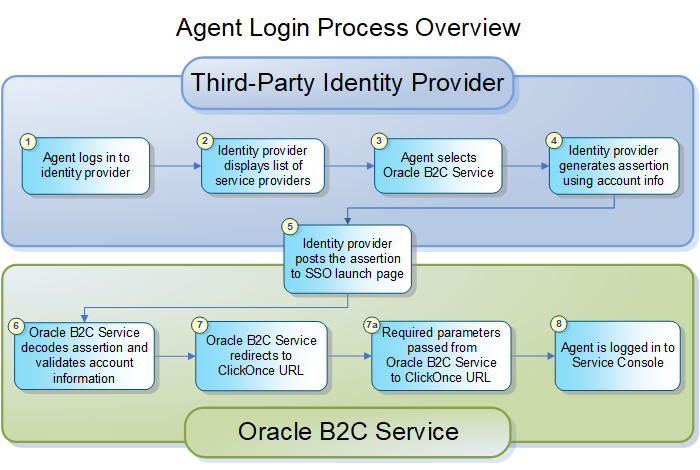
- An agent enters a user name and password to log in to the organization’s identity provider (such as a PingFederate Server-based application). When the information is verified, the agent is logged in to the identity provider.
- The identity provider displays a list of service providers, including B2C Service, that the agent can connect to.
- The agent selects B2C Service.
- The identity provider generates a signed SAML 2.0 assertion
using the account login, email address, account ID, or a staff account
custom field as the assertion subject. See How You Identify the SAML Subject for Agent Login.
Note: The assertion must be signed using XML Signature Syntax and Processing recommendations. If the certificate used to sign the assertion is self-signed, it must be uploaded to the Additional Root Certificates (certs/root) directory in the File Manager. See Certificate Validation Options. The certificate must also be listed in the SAML_20_SIGN_CERTS configuration setting or it will not be accepted for SAML signing. See Define Single Sign-on Configuration Settings. Additionally, the assertion cannot be encrypted.
- The identity provider then submits the assertion to the B2C Service SSO launch page using HTTP POST binding (since that's the only binding method supported). The SSO launch page is similar to the standard launch page except that it automatically starts the ClickOnce URL, which logs the agent in after validation.
- B2C Service decodes and verifies the assertion
and validates the account by confirming that the assertion matches
an account in the Oracle database.
- Staff members logging in through an identity provider must have the SSO Login (SAML 2.0) permission enabled in their profile. See Considerations When Using Single Sign-on.
- Because accounts cannot be created through the single sign-on process, only existing accounts can be logged in. (The public API can be used to create or update accounts if necessary.)
- B2C Service redirects the agent to the ClickOnce URL, which signals the installer to use the SSO login instead of the standard login, and passes the necessary parameters for automatic login.
- B2C Service verifies the account using the parameters
of the ClickOnce URL for authentication. If necessary, the B2C Service client is downloaded and installed. The application
is then launched, and the agent is logged in.
See Server and client configuration issues in ClickOnce deployments for information about browser scripting and compatibility with ClickOnce applications.