About EPM Cloud User and Role Management
Oracle Fusion Cloud EPM implements several security layers. Infrastructure security components, which are implemented and managed by Oracle, create highly secure Oracle Enterprise Performance Management Cloud environments. EPM Cloud ensures security using the following mechanisms that permit only authorized users to access the service.
- Single Sign-On (SSO)
- Role-based access to environments
SSO and role-based security are controlled by Oracle Identity Management, which defines a security domain for each environment. After a successful signin, access to the service is determined by the role assigned to the user.
Identity Domain
In Classic environments, identity domain is a slice of the shared identity management infrastructure where Identity Domain Administrators create and manage EPM Cloud users and security.
Identity Domain Administrator uses My Services application (Classic) to manage the users who need access to these environments. By default, each customer is allocated two environments (test and production environments) of a service. Many EPM Cloud services may be activated under one identity domain.
Cloud Account Name
Cloud Account Name is the name of the account that manages your EPM Cloud subscription. In OCI (Gen 2), the Cloud Account Name is used as the name of the identity domain that secures your EPM Cloud environments. Identity Domain Administrators use My Services, Oracle Cloud Identity Console, and Oracle Cloud Console (IAM) to set up and manage EPM Cloud users and security. By default, each customer is allocated two environments (test and production environments) of a service.
The Account Administrator grants the Identity Domain Administrator role to one or more users to delegate the process of setting up security. Many EPM Cloud services may be activated under cloud account name.
Users
Each user who needs to access an environment must have an account in the identity domain associated with the environment. The EPM Cloud predefined roles assigned to the user determine what the user can do within an environment.
Predefined EPM Cloud Roles
Roles link users to the business activities that they are permitted to perform within an environment and the data that they can access. Users must be assigned to predefined roles that grant them access to business functions and associated data. Predefined roles are described in Understanding Predefined Roles. Identity Domain Administrator is not a predefined role.
Groups
EPM Cloud recognizes three types of groups:- PREDEFINED: These groups are automatically created for each predefined role. All users are assigned to a PREDEFINED group based on their predefined role (for example, Power User). You can view them in EPM Cloud Access Control.
- EPM: These are the groups that you create in EPM Cloud Access Control. They cannot be created in the Identity Console. They also do not show up in the Identity Console.
- IDCS: In OCI (Gen 2), multiple EPM Cloud users can be assigned to groups, and then these groups can be assigned to predefined roles. This removes the need to assign predefined roles to individual users, thus simplify the administration of predefined role assignment. Since Oracle Identity groups can be synced with identity provider (IdP) groups (such as Azure AD groups), you can even add individual users to IdP groups and assign the predefined roles to these groups in Oracle Cloud Identity Console or Oracle Cloud Console (IAM) They may be synchronized with an identity provider (for example, Okta or Azure AD). They show up in Access Control, but you cannot create them through EPM Cloud.
Use of SYSTEM as a Username
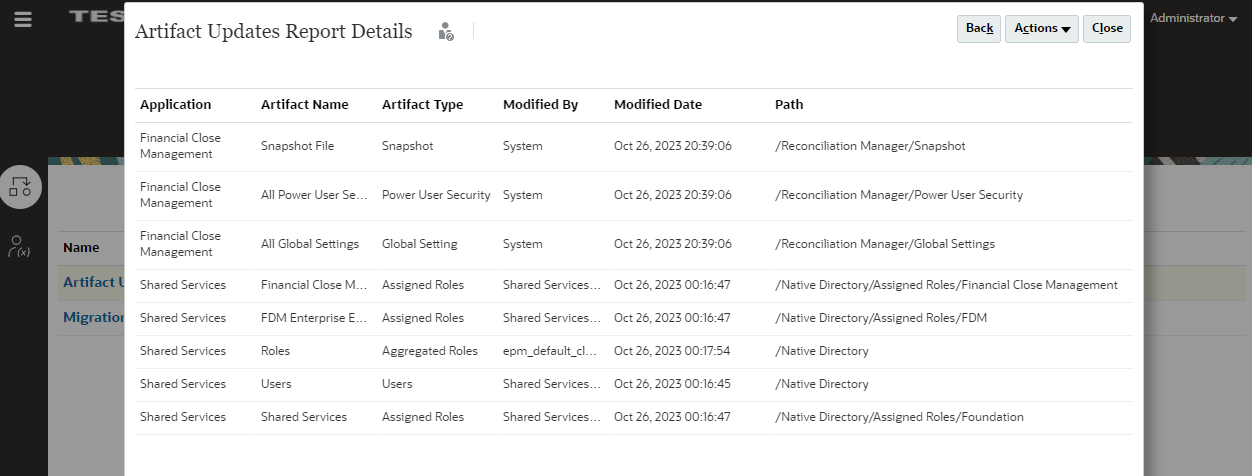
EPM Cloud shows the user name as SYSTEM if there are changes done internally or it is not recorded who made the change. There is no real user on the environment with this name. For example, for the following Account Reconciliation artifacts, there may be many Modified By users or the Modified By user is not always recorded. In such cases, SYSTEM is identified as the Modified By user:
- All Global Settings
- All Power User Security
- Snapshot File
Related Tutorial
This tutorial describes the layers of security in Cloud EPM business processes and shows you how to manage security using Access Control and access permissions. The sections build on each other and should be completed sequentially. See Setting Up Security in Cloud EPM Business Processes.