Setting Up Authentication with OAuth 2
Oracle Fusion Cloud Enterprise Performance Management environments on an Oracle Cloud Infrastructure (OCI) / Gen 2 architecture enable you to use an OAuth 2 access token to issue REST APIs on Cloud EPM to satisfy the requirement of avoiding the use of passwords in your environment.
Setting Up Authentication with OAuth 2
In order for the EPM Integration Agent to access OCI (Gen 2) Oracle Enterprise Performance Management Cloud environments, a Cloud EPM Service Administrator has to request the Domain Administrator to set up an OAuth 2 client and provide the Identity Domain Cloud Service (IDCS) URL, application scope, and Client ID.
Register the Client
The first step is to update the service provider configuration to authorize requests from the client application. As a security measure, any client application that accesses Oracle Cloud resources must be authorized to do so. A domain administrator provides this authorization by registering a client and providing the appropriate registration information to the client's users.
Clients can be public (outside a data center) or confidential. Public clients are assigned a client_id. Confidential clients also have a client secret in addition to a client_id. Clients are also authorized to access particular scopes. The type of application you select determines the allowed grant types available to request access tokens.
Client applications require an access token in order to access server resources. To obtain an access token, the client implements one of the IDCS supported access grant types, see Refresh Token Grant Type.
The Identity Cloud Service domain administrator follows the steps in this topic to create a public client in the Identity Cloud Service Administrator console for the requested client. The domain administrator then shares the Identity Cloud Service application URL, and client identification with the Cloud EPM Service Administrator.
Identity Cloud Service Administrator tasks to register a client:
-
Log in to the Identity Cloud Service Administrator console as a Domain Administrator.
-
Configure the token properties for protected OAuth 2 APIs:
-
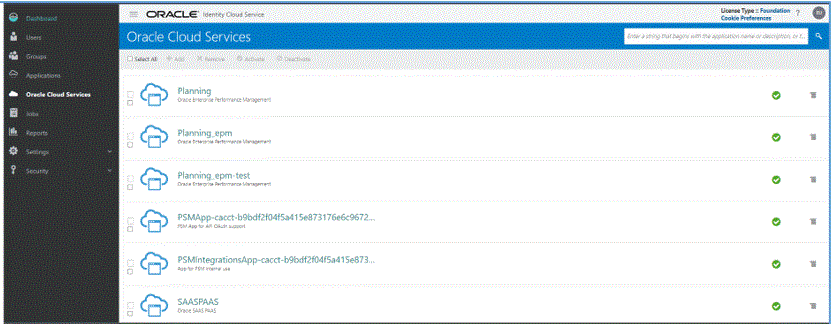
From the Dashboard drawer, click Oracle Cloud Services, and then select the Cloud Service.
-
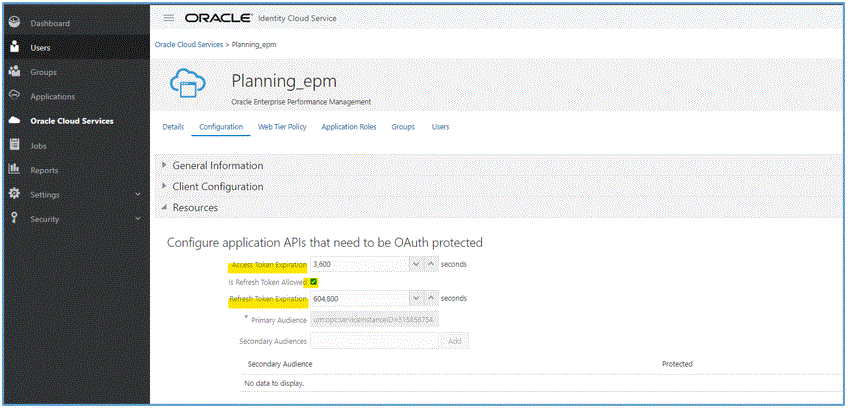
On the Configuration tab, under Resources, select the Is Refresh Token Allowed check box.
-
Optional: Change the Access Token Expiration and Refresh Token Expiration. Oracle recommends 3600 (1 hour) as the value of Access Token Expiration and 604,800 (7 days) as the value of Refresh Token Expiration.
-
Click Save.
-
-
From the Applications drawer, click Add .
-
From the Add Application page, select Mobile Application.
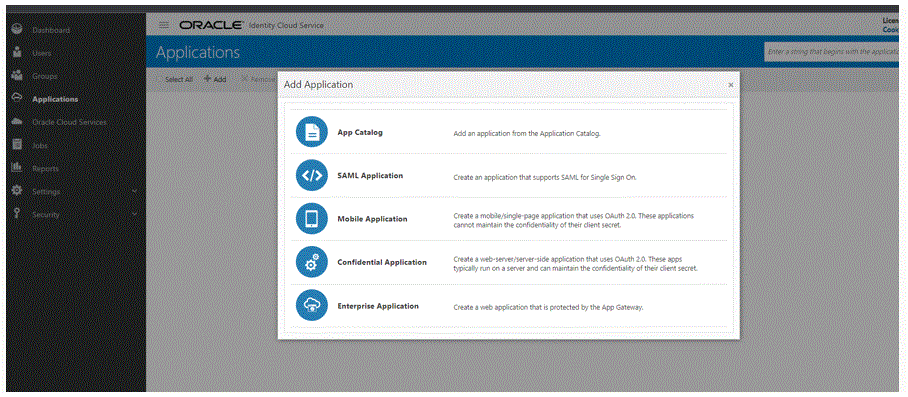
For detailed information about adding a mobile application, see Add a Mobile Application.
-
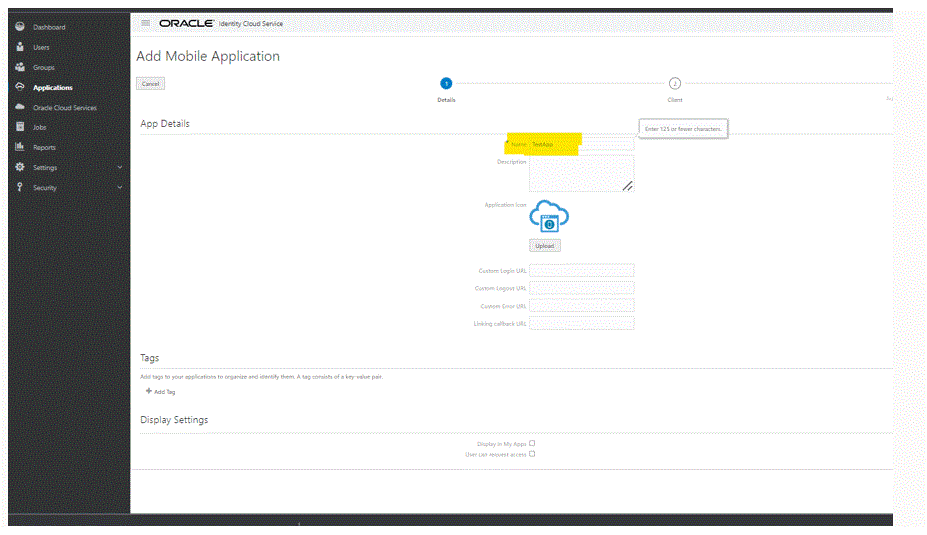
In the App Details section, then Name, enter the name for the REST client.
-
Optional: Add other details as needed.
-
Click Next.
-
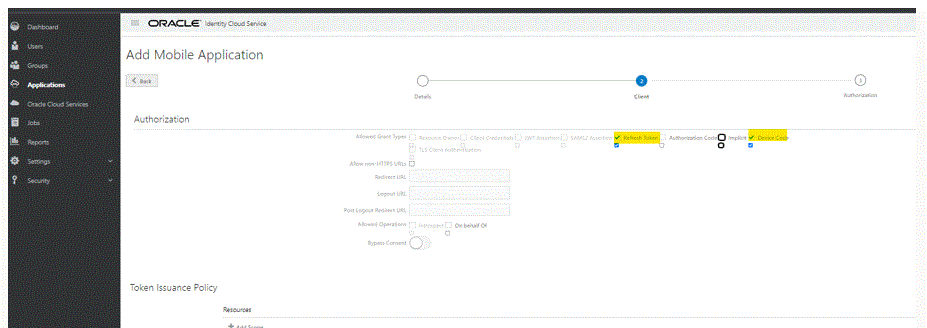
In the Authorization section, under Allowed Grant Types, select the Refresh Token and Device Code check boxes.
-
Click Next and then click Finish.
The Application Added page shows the generated Client ID.
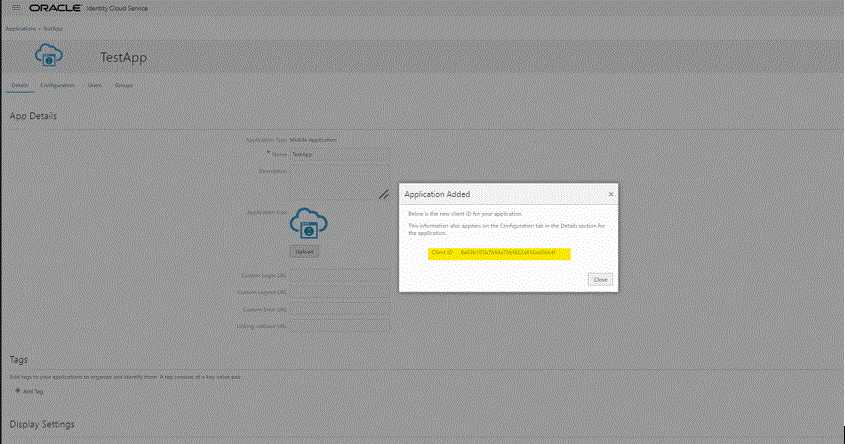
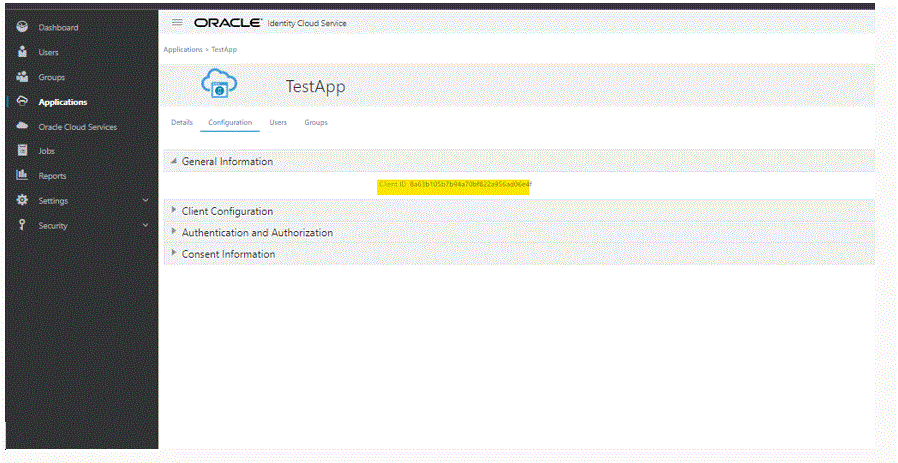
This Client ID also appears on the Configuration tab under the Details section for the application.
-
Copy the ID to the Client_ID field in the
agentparams.inifor the agent. See Enabling the OAUTH Option in the EPM Integration Agent. - On the Application Added page, click Close.
-
Click Activate to activate the client, and then click OK.

The message: "application name has been activated" is displayed.
