Role Assignment Audit Report
Users with a Service Administrator role can use this API to generate a Role Assignment Audit Report. The report shows all the changes made to the predefined role and application role assignments within the provided time frame. This report can be generated for up to the previous 90 days from the current date. You can download the report using the Download REST API. The report shows the timestamp (UTC) in the Date and Time column in 24-hour format.
This is an asynchronous job and uses the job status URI to determine if the operation is complete.
The presence of status -1 in the response indicates that the generation of the report is in progress. Use the job status URI to determine whether the generation of the report is complete. Any non-zero status except -1 indicates failure of generating the report.
The default retention period for audit data is 30 days; however, you can extend the retention period up to a maximum of 90 days from the Identity Console. If you want a longer duration of audit data, download a Role Assignment Audit Report and archive it.
This API is version v1.
Note:
Oracle Fusion Cloud EPM ensures that only valid date range is used during report generation. Thesevalidations are performed for the start and end dates:
- The start date cannot be earlier than the allowed maximum retention period (90 days) from the current date.
-
The end date cannot be later than the maximum retention period from the start date.
-
The end datecannot be earlier than the start date.
Required Roles
-
Service Administrator
-
Any predefined role and the Identity Domain Administrator role
-
Any predefined role and the Access Control - Manage application role
-
Any predefined role and the Access Control - View application role
REST Resource
POST
/interop/rest/security/{api_version}/roleassignmentauditreport
Note:
Before using the REST resources, you must understand how to access the REST resources and other important concepts. See Implementation Best Practices for Cloud EPM REST APIs. Using this REST API requires prerequisites. See Prerequisites.
Table 12-106 Tasks for Role Assignment Audit Report
| Task | Request | REST Resource |
|---|---|---|
| Role Assignment Audit Report | POST |
|
| Role Assignment Audit Report Status | GET |
|
Request
Supported Media Types:application/x-www-form-urlencoded
Table 12-107 Parameters
| Name | Description | Type | Required | Default |
|---|---|---|---|---|
api_version |
Specific API version | Path | Yes | None |
from_date |
The start date for the report (in YYYY-MM-DD format) | Form | Yes | None |
to_date |
The end date for the report (in YYYY-MM-DD format) | Form | Yes | None |
filename |
CSV file where the report is to be populated, such as roleAssignmentAuditReport.csv | Form | Yes | None |
Response
Supported Media Types: application/json
Table 12-108 Parameters
| Parameters | Description |
|---|---|
details |
In case of errors, details are published with the error string |
status |
See Migration Status Codes |
links |
Detailed information about the link |
href |
Links to API call |
action |
The HTTP call type |
rel |
Can be self and/or Job Status.
If set to Job Status, you can use the
href to get the status
|
data |
Parameters as key value pairs passed in the request |
Sample Role Assignment Audit Report
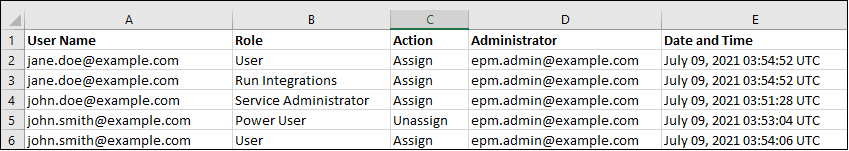
The Role Assignment Audit Report lists the User Login Name, IDCs Group Name, or EPM Group Name for which a role change (in Action column) was made. It also includes the predefined or application role that was assigned or unassigned, the user who performed the role change (Performed By column), and the timestamp (UTC) in 24-hour format when the action was completed. The Type column indicates what Name column represents. It can have one of these three values: User (if the Name column identifies a login name of a user), IDCS Group (if the Name column displays an IDCS group name), or EPM Group (if the Name column lists an EPM group name).
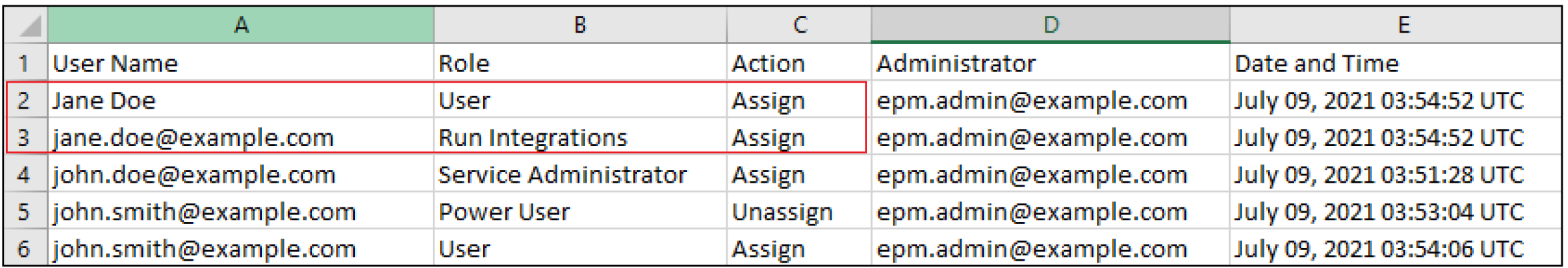
Information on deleted users who were previously assigned to predefined roles in the environment is listed with the display name (first and last name) of the user in the User Name column. In such cases, the Role column indicates the predefined role that the user had before the user's account was deleted. This change does not apply to application roles, if any, that were assigned to the deleted user; such assignments are shown with the User Login Name of the user. For an example, see the information in the red box in the following illustration.
Examples of Response Body
The following show examples of the response body in JSON format.
Response 1: Job is in Progress
{
"links": [
{
"rel": "self",
"href": "https://<BASE-URL>/interop/rest/security/<api_version>/roleassignmentauditreport",
"data": {
"jobType": "GENERATE_ROLE_ASSIGNMENT_AUDIT_REPORT",
"to_date": "<toDate>",
"filename": "<filename>",
"from_date": "<fromDate>"
},
"action": "POST"
},
{
"rel": "Job Status",
"href": "https://<BASE-URL>/interop/rest/security/<api_version>/jobs/3023387588778806",
"data": null,
"action": "GET"
}
],
"details": null,
"status": -1,
"items": null
}Response 2: Job Completes with Errors
{
"links": [
{
"data": {
"jobType": "GENERATE_ROLE_ASSIGNMENT_AUDIT_REPORT",
"from_date": " ",
"to_date": " ",
"filename": " "
},
"action": "POST",
"href": "https://<BASE-URL>/interop/rest/security/{api_version}/roleassignmentauditreport",
"rel": "self"
}
],
"status": 1,
"details": "EPMCSS-20678: Failed to generate Role Assignment Audit Report. Invalid or insufficient parameters specified. Provide all required parameters for the REST API. ",
"items": null
}
Response 3: Job Completes without Errors
{
"links": [
{
"data": null,
"action": "GET",
"href": "https://<BASE-URL>/interop/rest/security/<api_version>/jobs/<jobID>",
"rel": "self"
}
],
"status": 0,
"details": null,
"items": null
}Java Sample Code
Prerequisites: json.jar
Common Functions: See CSS Common Helper Functions for Java
public void generateRoleAssignmentAuditReport(String fromDate, String toDate,String fileName) {
try {
String url = this.serverUrl + "/interop/rest/security/" + apiVersion + "/roleassignmentauditreport";
Map<String, String> reqHeaders = new HashMap<String, String>();
reqHeaders.put("Authorization", "Basic " + DatatypeConverter
.printBase64Binary((this.userName + ":" + this.password).getBytes(Charset.defaultCharset())));
Map<String, String> reqParams = new HashMap<String, String>();
reqParams.put("from_date", fromDate);
reqParams.put("to_date", toDate);
reqParams.put("filename", fileName);
Map<String, String> restResult = CSSRESTHelper.callRestApi(new HashMap(), url, reqHeaders, reqParams,
"POST");
String jobStatus = CSSRESTHelper.getCSSRESTJobCompletionStatus(restResult, reqHeaders);
System.out.println(jobStatus);
} catch (Exception e) {
e.printStackTrace();
}
}Shell Script Sample Code
Prerequisites: jq (http://stedolan.github.io/jq/download/linux64/jq)
Common Functions: See CSS Common Helper Functions for cURL
funcGenerateRoleAssignmentAuditReport() {
url="$SERVER_URL/interop/rest/security/$API_VERSION/roleassignmentauditreport"
params="from_date=$1&to_date=$2&filename=$3"
header="Content-Type: application/x-www-form-urlencoded;charset=UTF-8"
cssRESTAPI="generateRoleAssignmentAuditReport"
statusMessage=$(funcCSSRESTHelper "POST" "$url" "$header" "$USERNAME" "$PASSWORD" "$params" "$cssRESTAPI")
echo $statusMessage
}Groovy Sample Code
Common Functions: See CSS Common Helper Functions for Groovy
def generateRoleAssignmentAuditReport(from_date,to_date,fileName) {
String scenario = "Generating Role assignment audit report in " + fileName;
String params = "jobtype=GENERATE_ROLE_ASSIGNMENT_AUDIT_REPORT&from_date="+from_date+"&to_date="+to_date+"&filename="+ fileName;
def url = null;
def response = null;
try {
url = new URL(serverUrl + "/interop/rest/security/" + apiVersion + "/roleassignmentauditreport");
} catch (MalformedURLException e) {
println "Please enter a valid URL"
System.exit(0);
}
response = executeRequest(url, "POST", params, "application/x-www-form-urlencoded");
if (response != null) {
getJobStatus(getUrlFromResponse(scenario, response, "Job Status"), "GET");
}
}Sample cURL Command Basic Auth
curl -X POST -s -u '<USERNAME>:<PASSWORD>' -H 'Content-Type: application/x-www-form-urlencoded' -d 'from_date=2025-03-10&to_date=2025-03-31&filename=roleAssignmentAuditReport.csv' 'https://<BASE-URL>/interop/rest/security/v1/roleassignmentauditreport'Sample cURL Command OAuth 2.0
curl -X POST --header "Authorization: Bearer <OAUTH_ACCESS_TOKEN>" -H 'Content-Type: application/x-www-form-urlencoded' -d 'from_date=2025-03-10&to_date=2025-03-31&filename=roleAssignmentAuditReport.csv' 'https://<BASE-URL>/interop/rest/security/v1/roleassignmentauditreport'