Restricting access using an IP allowlist
You can restrict access to Oracle Eloqua by setting up an allowlist of IP addresses. Any user who tries to log in from a computer with an IP address not included in the allowlist will not be able to log in.
The IP allowlist lets you:
- Prevent unauthorized users from using Oracle Eloqua credentials.
- Ensure that former employees can no longer access Oracle Eloqua. Most organizations disable internal and VPN network access when an employee exits.
Before you begin:
- Identify the IP address that you need to allow. This can be a range of IP address or a specific list. If your network uses subnets, you can use the slash notation for your network masks. A tool like the online subnet mask calculator is helpful in finding the slash notation (called “mask bits” in the calculator).
- If you are using Oracle Eloqua AppCloud apps, you must allow the IP addresses used to host the apps. You can allow all IP addresses used by the apps using the Add Internal Eloqua IPs option described below.
- In order for the Oracle Eloqua support team to troubleshoot issues with your environment, you must allow support's various IP addresses.
- Work with your IT department to determine how Eloqua will get the IP address for comparison to the allowlist. By default, Oracle Eloqua will compare the first IP address in the X-Forwarded-For request header to the allowlist. But you can use other methods that determine how the IP address is gathered. Step 4 below discusses these options.
To restrict access using an IP allowlist:
- Click Settings
 .
. - Click Security in the Users and Security area.
- Click IP.
-
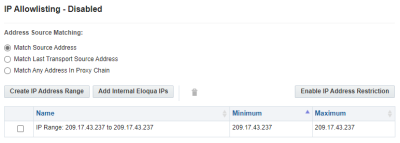
Choose the Address Source Matching.
-
Match Source Address: Compares the first IP address in the X-Forwarded-For header to the allowlist values. This is the default option.
-
Match Last Transport Source Address: Compares the IP address from the network transport layer to the allowlist. You can use this option when all traffic to Oracle Eloqua is routed through a single IP address or dedicated range of IP addresses, such as a trusted proxy.
-
Match Any Address In Proxy Chain: Compares all IP addresses in the X-Forwarded-For header to the allowlist. If any address matches, access is allowed. You can use this option when multiple internal or cloud proxies are in use at your organization.
-
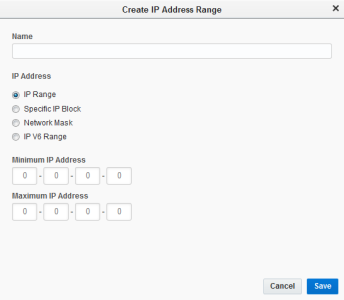
- Click Create IP Address Range.
- Enter the name of the IP address.
- Choose an option:
- To restrict access to a range of IP addresses, select IP Range or IP V6 Range and enter the IP range.
- To restrict access to a specific IP address, select Specific IP Block and enter the IP address.
- To restrict access to a range of IP addresses using a subnet mask, select Network Mask and enter the beginning IP address of the IP range followed by the network mask using slash notation. For example, the /24 subnet mask is equal to a 255.255.255.0 subnet mask and includes the addresses 1.1.1.0 to 1.1.1.254. The online subnet mask calculator can help you find the mask (called “mask bits” in the calculator).
- Click Save.
- Repeat the steps for all IP addresses required.
Important: After you have created your full IP address allowlist, confirm the list before continuing. This can help prevent locking users out.
- If you are using Oracle Marketing Apps, click Add Internal Eloqua IPs on the IP Allowlist - Disabled window. This allows appropriate IP address required to continue using the apps.
- Click Enable IP Address Restriction to restrict access using the IP allowlist you created.
Restricting access using an IP allowlist
Oracle Marketing apps IP addresses