Use Redwood Pages for HCM Security Profiles and Exclusion Rules
Enrich the user experience with several new Security Profiles pages developed using the Redwood toolset. These pages are built entirely using Visual Builder Studio (VBS) to give you a unique experience of Oracle applications. The following pages are new:
- Country Security Profiles
- Document Type Security Profiles
- HCM Exclusion Rules
- Legislative Data Group Security Profiles
- Organization Security Profiles
- Person Security Profiles
- Position Security Profiles
IT Security Manager users can navigate to these pages from the Quick Actions pane under the My Client Groups section, Workforce Structures subsection. As long as you enable the corresponding profiles, you can also access the respective Redwood pages from the Setup and Maintenance navigation.
Overall streamlining of the security profile task flows includes elimination of the initial view page before editing the content. You will now go directly into edit mode, if you have functional access to the respective page.
NOTE: Predefined security profile values are delivered as read-only and you won’t be able to edit these rows.
Other enhancements included with these task flows enable you to:
-
View enabled security profiles and exclusion rules by default.
-
Expose audit details for each row, such as when the security profile was created and updated.
-
View focused search results with less-frequently used columns hidden by default.
-
Use the Columns icon to hide or show columns and modify the column order.
-
Click the ascending or descending icon to sort results.
-
-
Export search results.
-
Edit a role with a single click of the role name.
-
Quickly define security criteria using a simplified page.
Exposing Creation and Update Details
You’ll now see an organized search page where the most common securing methods are visible. You can enable other options under the column selector. New columns options have been added that let you expose, sort, and search security profiles based on who created or updated that security object. You can view the date it was created on or who last updated it when you enable these hidden column options:
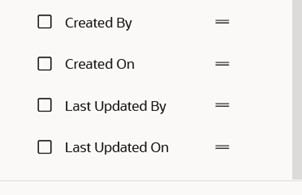
Optional Audit Search Fields
Country Security Profile
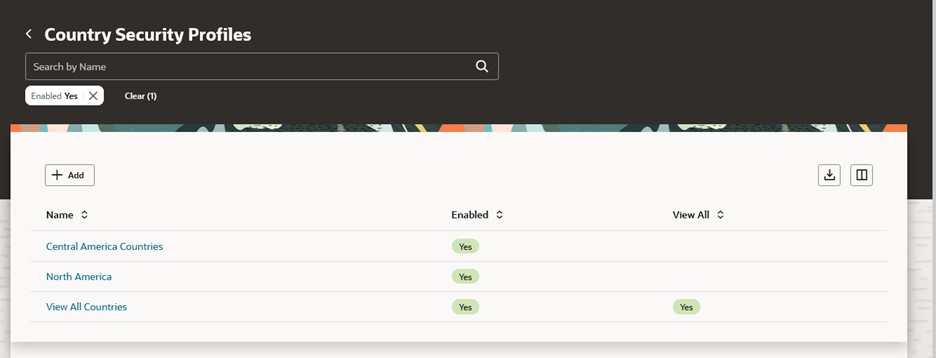
Country Security Profiles Search
When the delivered View All Countries security profile doesn’t support your business requirements, creating a new country security profile is easy.
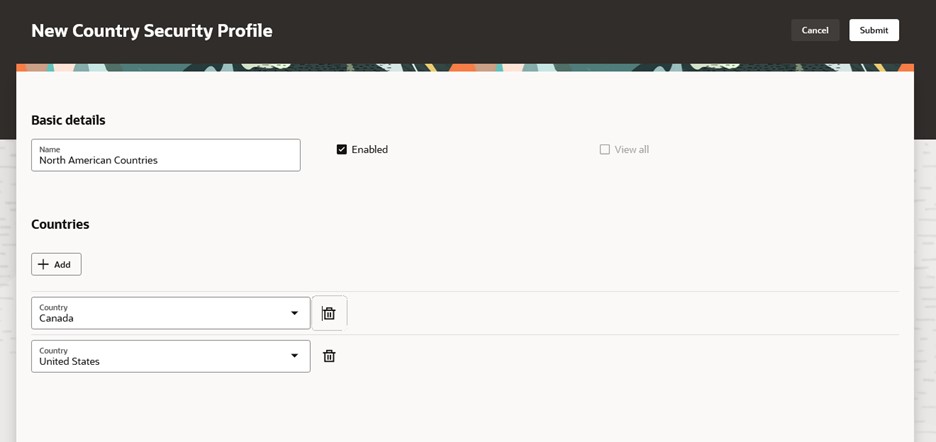
Creating a Country Security Profile
Document Type Security Profile
Document type security profiles are used to limit a user’s access to relevant document records and document types.
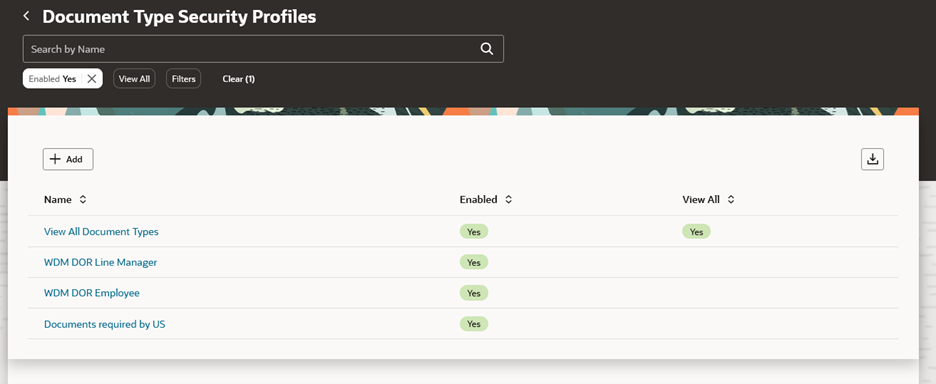
Document Type Security Profiles Search
When adding a new record, you will choose the relevant document type. By default, the applicable country name will appear to which the document type is associated, unless it is applicable to all countries. Choose the checkmark to save the row, or the “x” to cancel and delete your selection.
Save and Cancel Options When Adding a Document Type
Legislative Data Group Security Profile
Restrict data access by defining legislative data group security profiles. If you don’t have restriction requirements, use the delivered View All Legislative Data Group security profile with your data role.
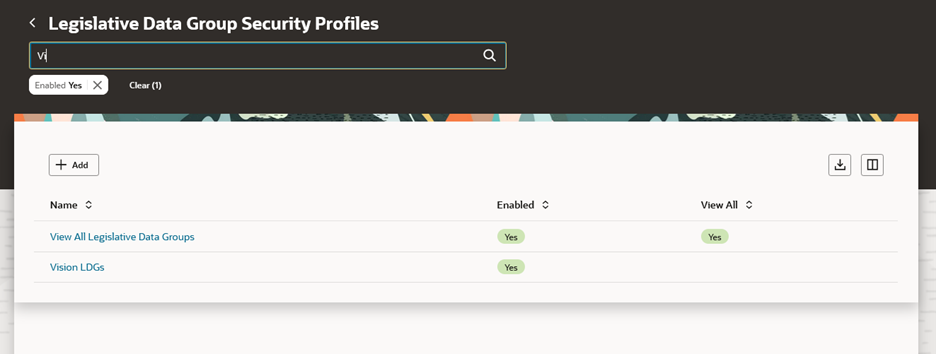
Legislative Data Group Security Profiles Search
You can create a legislative data group security profile by clicking the Add button.
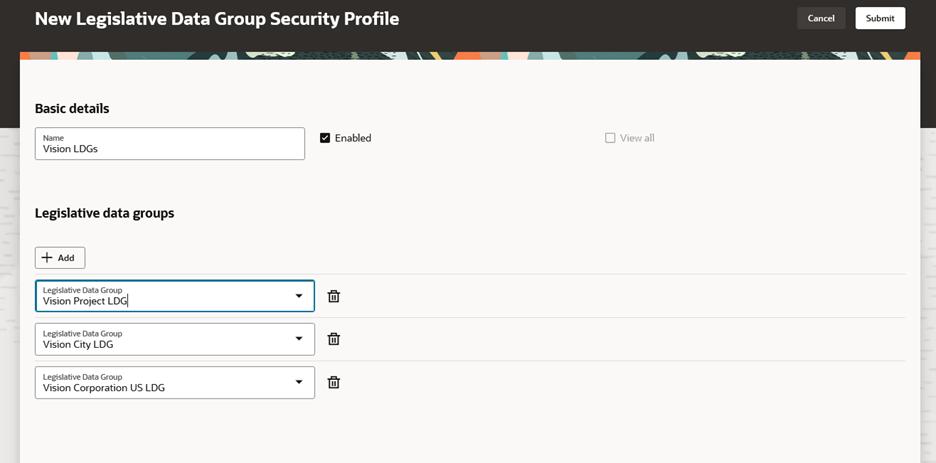
Creating a Legislative Data Group Security Profile
Organization Security Profile
Define an organization security profile when you want to limit a user’s access based on certain organizational structures. If your users don’t have any organizational restrictions, use the predefined View All Organizations security profile.
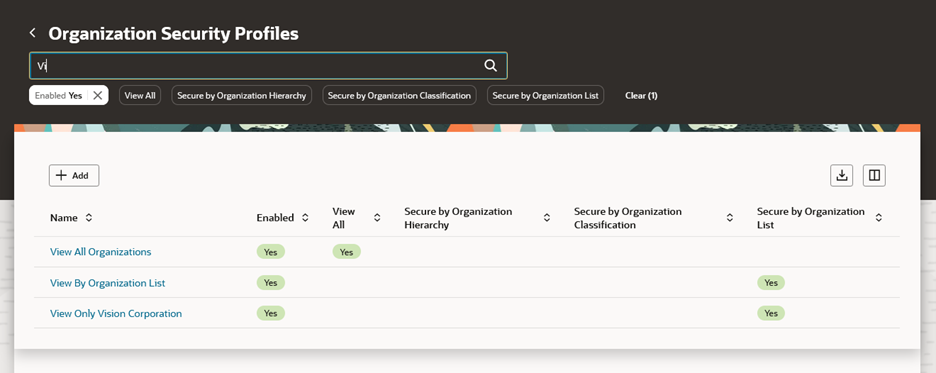
Organization Security Profiles Search
You can create an organization security profile by clicking the Add button.
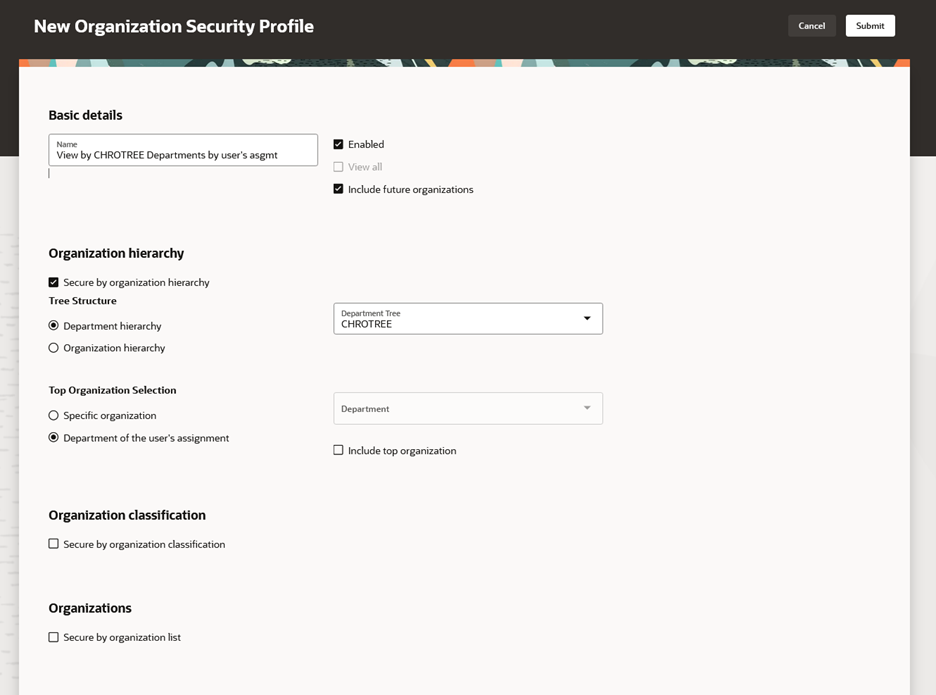
Creating an Organization Security Profile
Person Security Profile (also applies to Public Person security profile)
As the person security profile is more complex, this is redesigned to present information in a compact guided process flow.
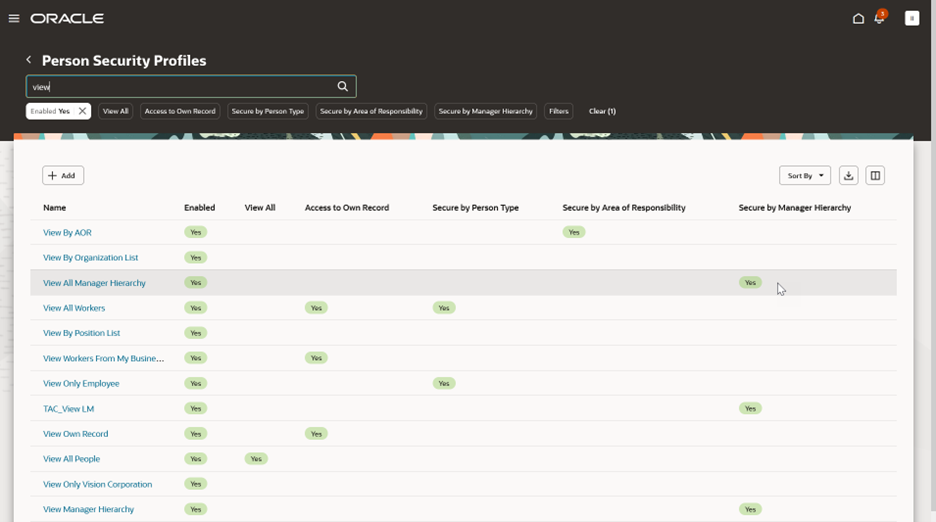
Person Security Profiles Search
NOTE: When assignment-level security is enabled, you will see this message on the search page above the add button.

Assignment Level Security Enabled
While creating a person security profile, you'll need to know in advance, which method you’ll want to use in order to secure access to people. You’ll notice that we have simplified the process and removed fields that aren't applicable to the chosen securing method criterion.
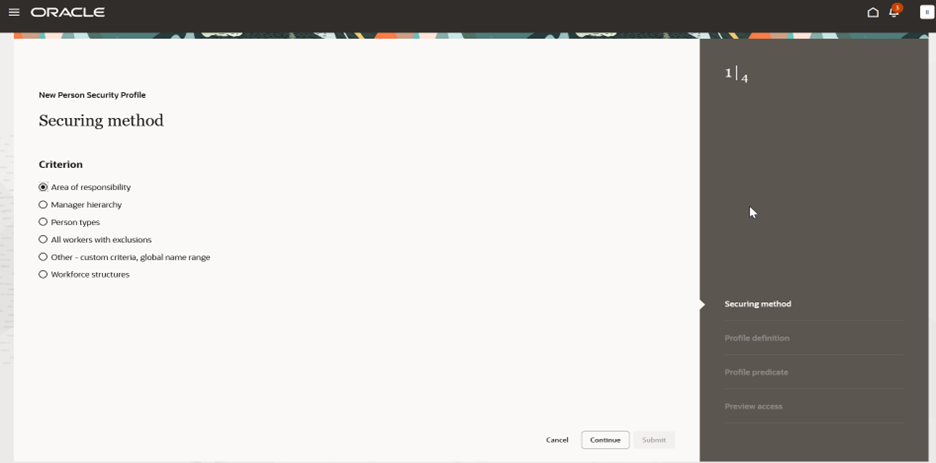
Criterion Selection for Person Security Profile Securing Methods
With this streamlined flow, you're only required to choose entries on the securing method and profile definition steps. Profile predicate and preview access are optional steps. This means the submit button will be enabled after the required steps are completed and that you’re allowed to submit the person security profile at this point. In this example, only the fields that are relevant to profiles that are secured by areas of responsibility are displayed.
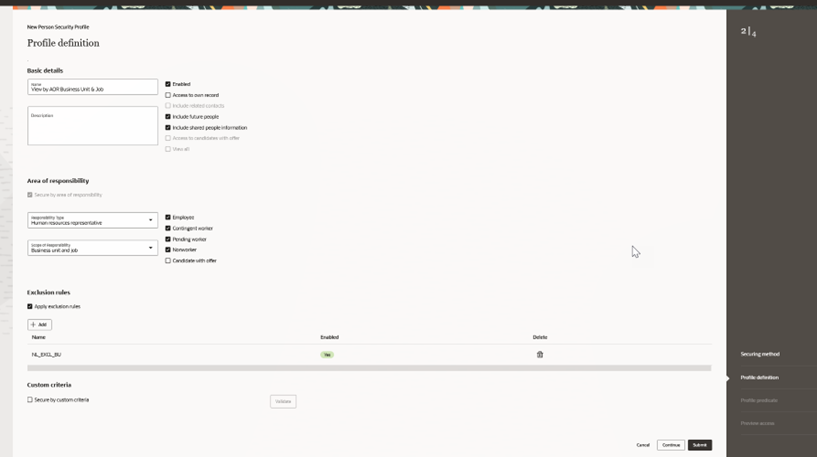
Profile Definition for Person Security Profile for Area of Responsibility Criterion
The profile predicate contains the person access SQL predicate that’s generated based on your profile definition entries. If assignment-level security is enabled, then an additional tabbed region for Assignment Access appears containing the relevant assignment-based SQL predicate. When your security profile has a purpose that includes imported candidates, you will see another tabbed region for Imported Candidate Access. A new copy button is available so you can easily copy this predicate to your clipboard for testing or debugging purposes.
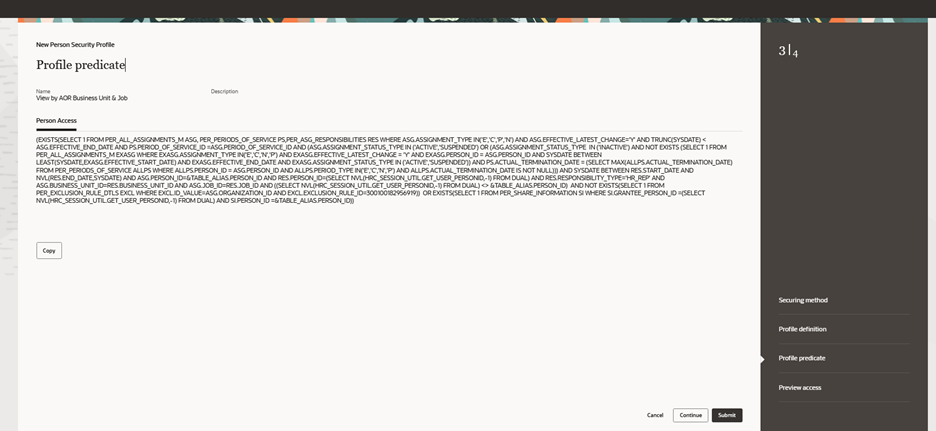
Profile Predicate for Person Security Profile.
The new Preview access page allows you to simulate a user’s data access once assigned this person security profile. It does not take the user's current security data access into consideration.
There are two sections on this page available to help you evaluate the user’s data access:
User Summary
This section shows the user details, number of available person records, and lists the responsibilities (i.e., AORs) the selected user already has been assigned.
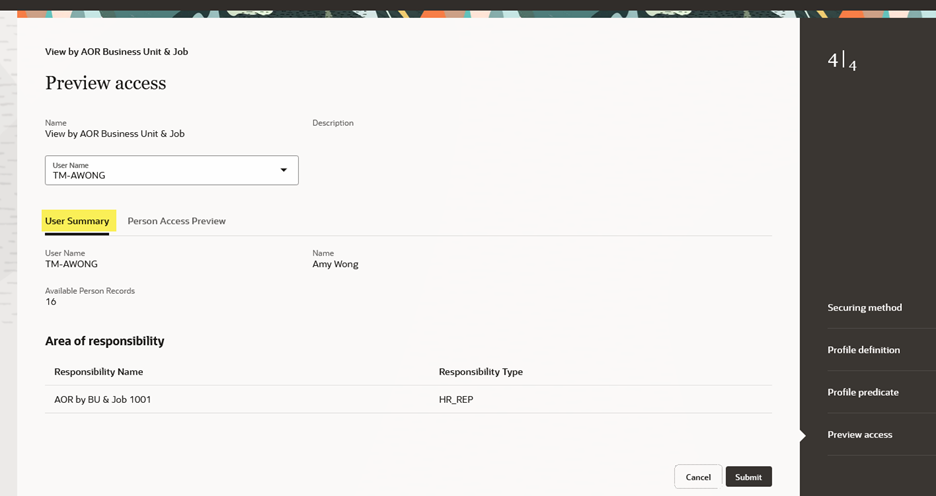
Preview Access for Person Security Profile – User Summary Section
Person Access Preview
This section is available for preliminary testing or debugging purposes. A person search is available that allows you to filter the user’s search results by legal employer, department, business unit, or country.
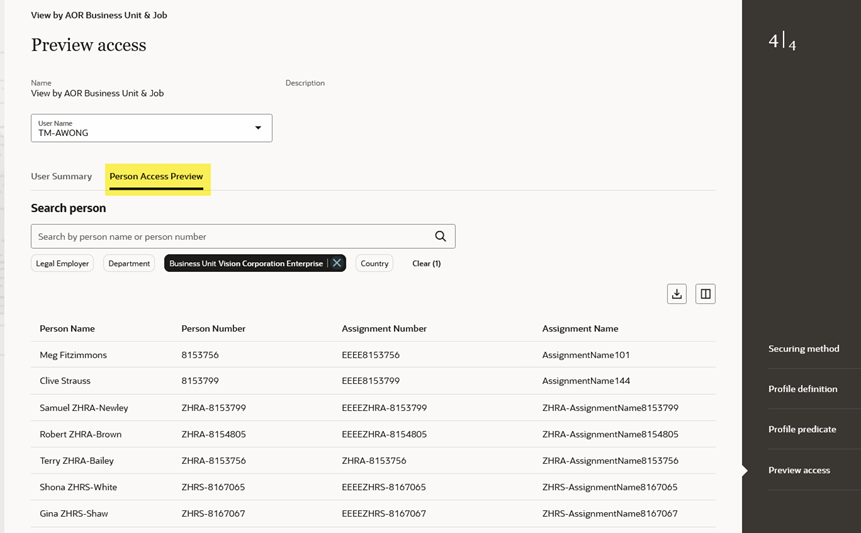
Preview Access for Person Security Profile – Person Access Preview Section
Position Security Profile
Similar to a person security profile in that it is more complex than other security profiles, position security profile is also presented as a compact guided process flow.
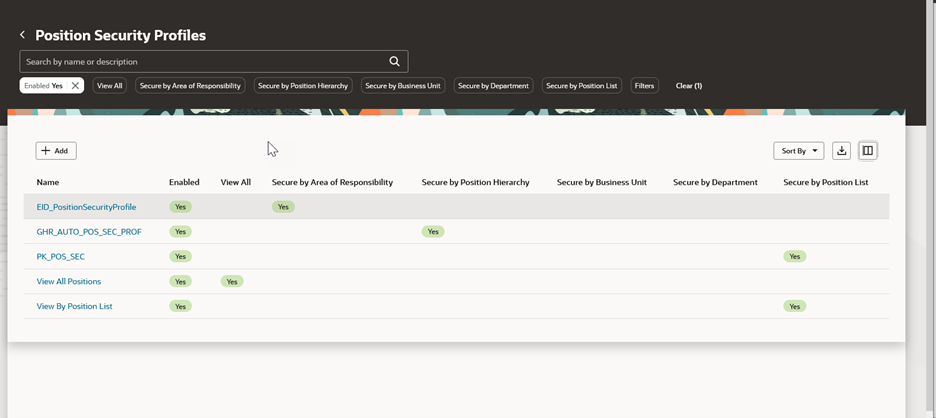
Position Security Profile Search Results
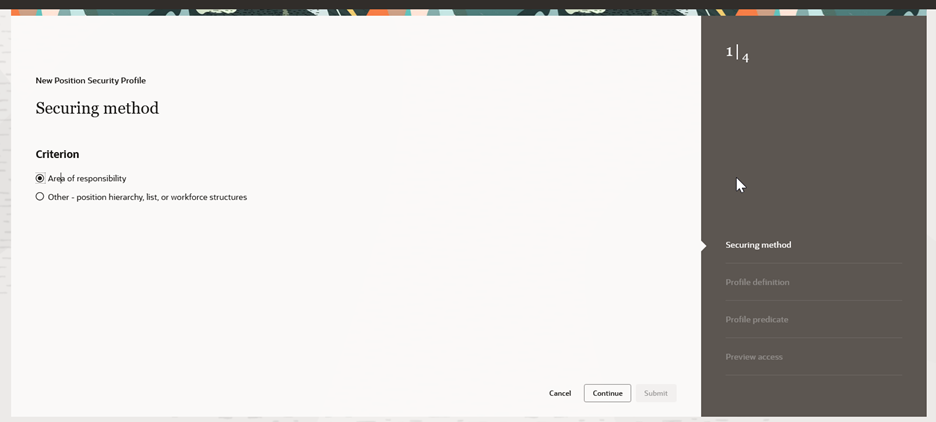
Criterion Selection for Position Security Profile Securing Methods.
When adding a new position security profile as part of a compact guide process flow, once you complete the required Securing method and Profile definition steps, the submit button will be enabled after the required steps are completed. You’re allowed to submit the position security profile at this point, if you choose to do so.
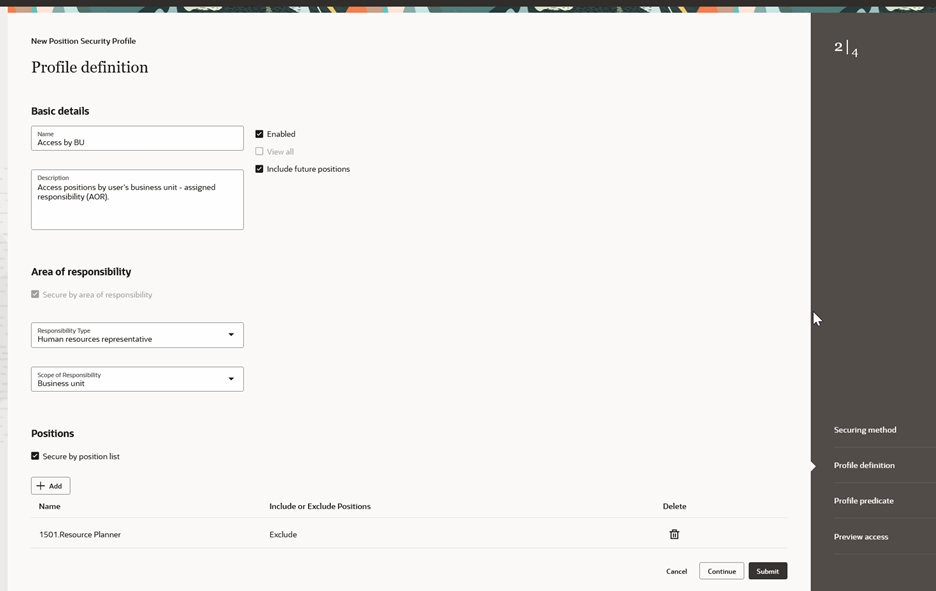
Profile Definition for Position Security Profile for Area of Responsibility Criterion
The profile predicate contains the SQL predicate that’s generated based on your profile definition entries. A new copy button is available so you can easily copy this predicate to your clipboard for testing or debugging purposes.
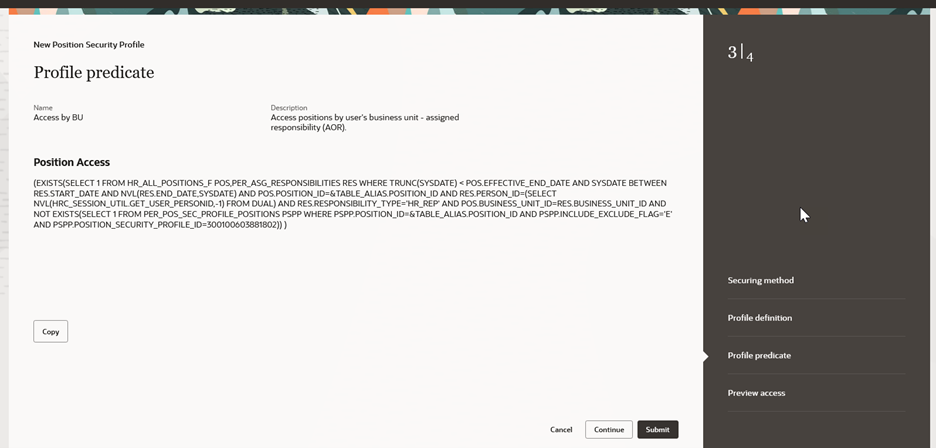
Profile Predicate for Position Security Profile
The new Preview access page lets you simulate a user’s data access once assigned this position security profile. It does not take the user's current security data access into consideration.
There are two sections on this page available to help you evaluate the user’s data access.
User Summary
This section contains the user details, number of available position records, plus lists the responsibilities (i.e., AORs) the selected user already has assigned.
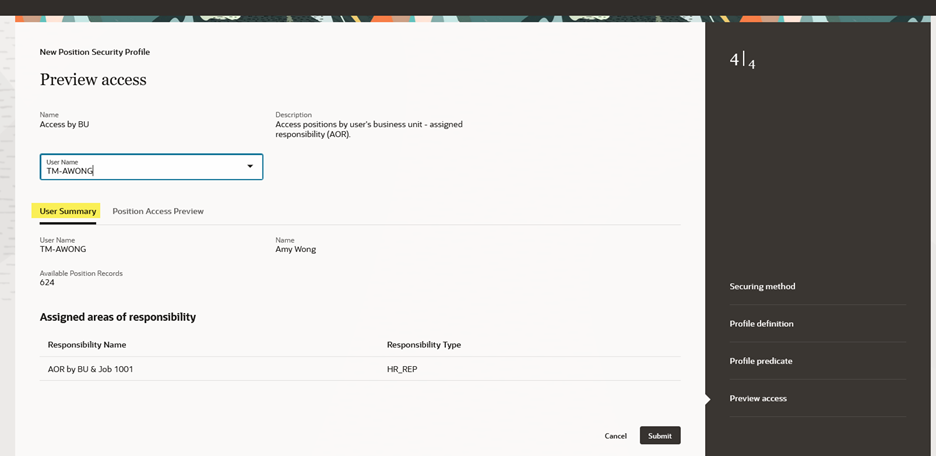
Preview Access for Position Security Profile – User Summary Section
Position Access Preview
This section is available for preliminary testing or debugging purposes. A position search is available that allows you to filter the user’s search results by business unit and department.
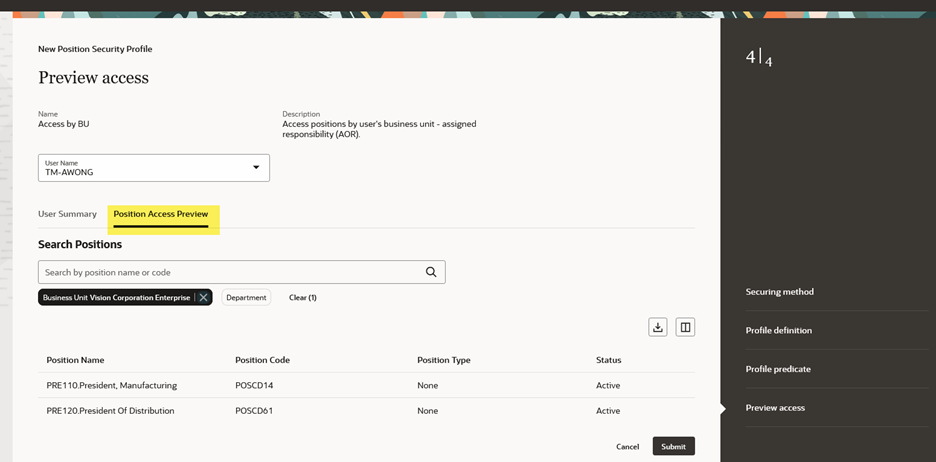
Preview Access for Position Security Profile – Position Access Preview Section
HCM Exclusion Rules
HCM exclusion rules has a new, simplified user interface.
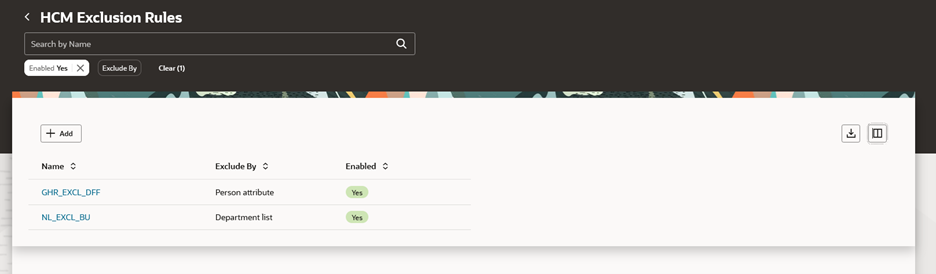
HCM Exclusion Rules Search Results
You can create an exclusion rule using this new user interface. Validations are built in to support required fields and to prevent entering duplicate entries. In this example of excluding certain departments in a list, you can't enter the same department twice. You also can’t create an exclusion rule with the same name.
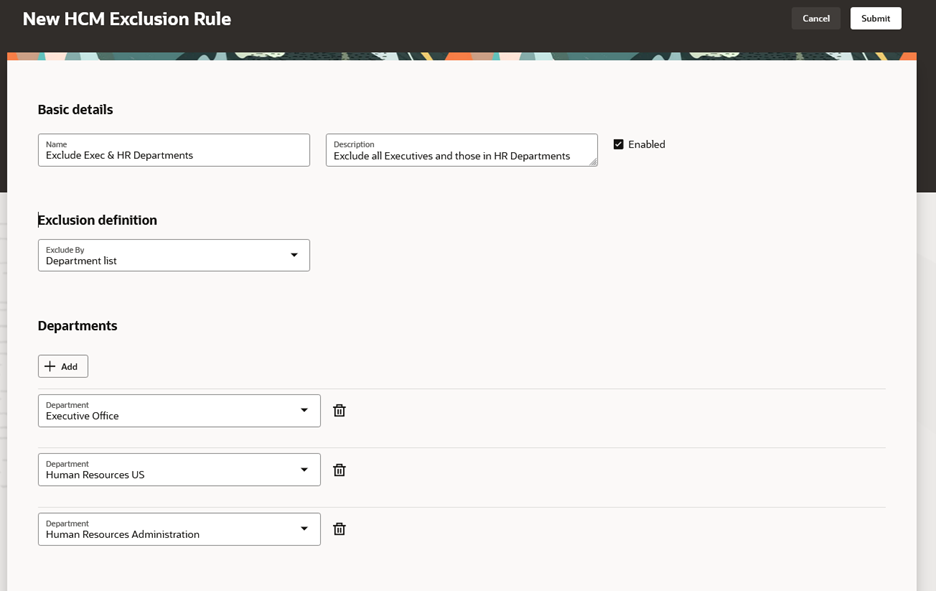
Create an HCM Exclusion Rule
Once you've submitted the exclusion rule, you won’t be able to edit the Exclude By selection exclusion definition. You will need to disable the exclusion rule, and then create a new one.
By using the new Redwood pages, you can take advantage of the cohesiveness through the application.
Steps to Enable
In order to work with the new Redwood security profile pages, you must first enable the ORA_HCM_VBCS_PWA_ENABLED profile option.
In addition, the following profile options must also be enabled, so you’ll need to set the profile option value to Yes for these:
-
ORA_PER_COUNTRY_SECURITY_PROFILE_REDWOOD_ENABLED (Redwood Country Security Profile Enabled)
-
ORA_PER_LDG_SECURITY_PROFILE_REDWOOD_ENABLED (Redwood Legislative Data Group Security Profile Enabled)
-
ORA_PER_PERSON_SECURITY_PROFILE_REDWOOD_ENABLED (Redwood Person Security Profile Enabled)
-
ORA_PER_POSITION_SECURITY_PROFILE_REDWOOD_ENABLED (Redwood Position Security Profile Enabled)
-
ORA_PER_ORGANIZATION_SECURITY_PROFILE_REDWOOD_ENABLED (Redwood Organization Security Profile Enabled)
-
ORA_PER_EXCLUSION_RULE_REDWOOD_ENABLED (Redwood Exclusion Rule Enabled)
-
ORA_PER_DOCUMENT_TYPE_SECURITY_PROFILE_REDWOOD_ENABLED (Redwood Document Type Security Profile Enabled)
To enable the profile option, navigate to the Setup and Maintenance work area:
-
Search for and click the Manage Administrator Profile Values task.
- Search for and select the profile option.
- Select the Level as Site.
- Enter Yes in the Profile Value field.
- Click Save and Close.
Tips And Considerations
- Define the necessary security profiles ahead of time. You can no longer create new security profiles from within the Data Roles and Security Profiles task flow.
- The Review page has been removed from this task flow.
- LOVs used within the security profiles are case-sensitive in Update 24C. This will be fixed in Update 24D.
- When exporting search results, you’ll only get the results that have loaded to your page. You might need to add columns or scroll to the end of the page, in order to get the complete content list before exporting.
- For Person and Position security profiles, you might not have the option for “workforce structures” as this is an option previously available to early adopter customers, and has been superseded by the Area of responsibility criterion.
- Future releases will include additional new Redwood security profiles to create and manage HCM transactions, candidates, job requisitions, talent pools, elements, payroll, and payroll flows.
Key Resources
For more information, refer to these resources on the Oracle Help Center:
- HCM Security Profiles
- What's New documentation for the feature Use Redwood Pages for HCM Data Roles and Security Profiles
Access Requirements
To use this feature, you need this job role name and code:
-
IT Security Manager (ORA_FND_IT_SECURITY_MANAGER_JOB)
No role changes are necessary to access this feature.