Content Security Policy Customer Enablement in Cloud Implementations
In this release, you are expected to run tests to understand the external URLs you use in the application. You should fill in the Content Security Policy (CSP) Modification Request form with details and raise a service request to the Oracle Utilities Cloud Operations team to get them included in the CSP. Note that CSP will be enabled by default in the next release so if the external URLs are not added to the CSP, it will result in functionality loss.
CSP is a feature that helps to prevent or minimize the risk of certain types of security threats. The primary use case for CSP is to control which resources, in particular JavaScript resources, a document is allowed to load. By enabling this response header, customer gets the security benefits related to this.
Steps to Enable and Configure
To test this feature, complete these steps:
- Users must have F1-DEBUG privileges will be able to enable the csp reporting.
- Login into the application (user/password).
- Modify the URL add the request parameter (?cspReportOnly=true) Eg: http://servername:portno/spl/cis.jsp?cspReportOnly=true.
- In the browser refresh option choose the > 'Empty cache hard refresh' (This will ensure that the cache is deleted and all the contents are freshly loaded).
- Open the Settings and more (Alt + F) > More Tools > Developer Tools >. Ensure you see Content-Security-Policy-Report-Only response header for all different requests.
- Navigate through CM modules and modules where there is a possibility to use or access other URLs. For example, in the below screenshot, we can see that the error is related to a URL missing in the script-src direct.
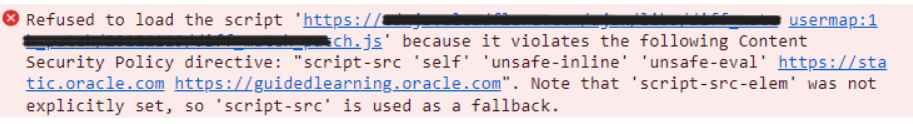
- Go back to Developer Tools > Console Tab. Look for possible errors starting with [Report Only] similar to the screenshot ([Report Only] Refused to execute inline event handler because it violates the following Content Security Policy directive: …..).
- Customers can look for the directive name(s) listed in the CSP Modification Request form. Examples include img-src, script-src, and so on. Collect these and document like the Sample Filled CSP Modification Request Form below.
- Logout of the application.
- In the browser refresh option, choose the > 'Empty cache hard refresh' (This will ensure that the cache is deleted and all the contents are freshly loaded). This will ensure to fresh download of the static files without the Content-Security-Policy-Report-Only response header.
CSP Modification Request Form
Here is the form customers should fill out. Note that the "Cloud Operations Key" will provide the name of the substitution variable.
Environments names: (example: DEV, TEST, PROD)
| Directive Name | Cloud Operations Key | URL That is Causing the Violation (For example, if the URL is https://customer-domain1.com/abc/abc.js, then specify https://customer-domain1.com without the path. Multiple URLs should be delimited by spaces.) |
|---|---|---|
| img-src | CSP_URL_IMG_SRC | |
| script-src | CSP_URL_SCRIPT_SRC | |
| frame-src | CSP_URL_FRAME_SRC | |
| style-src | CSP_STYLE_SRC | |
| connect-src | CSP_CONNECT_SRC | |
| font-src | CSP_FONT_SRC |
Sample Filled CSP Modification Request Form
Here is an example of a completed form:
ENVIRONMENT: DEV01, TEST
Environments names: (example: DEV, TEST, PROD)
| Directive Name | Cloud Operations Key | URL That is Causing the Violation (For example, if the URL is https://customer-domain1.com/abc/abc.js, then specify https://customer-domain1.com without the path. Multiple URLs should be delimited by spaces.) |
|---|---|---|
| img-src | CSP_URL_IMG_SRC | https://customer-domain1.com |
| script-src | CSP_URL_SCRIPT_SRC | https://customer-domain1.com |
| frame-src | CSP_URL_FRAME_SRC | |
| style-src | CSP_STYLE_SRC | https://customer-domain1.com https://customer-domain2.com |
| connect-src | CSP_CONNECT_SRC | |
| font-src | CSP_FONT_SRC |