Access Example: User-Access Risk
To begin investigating user-access risk, review the User Access Risks summary worksheet. For each user with role-assignment conflicts, identify the algorithms that define those conflicts. Open the worksheet for each algorithm, and create a pivot table based on these three values:
-
User Name: This identifies a user assigned roles that combine to violate access algorithms.
-
Role: This identifies the roles that potentially conflict.
-
Access Entitlement Name: This names entitlements containing access points that in combination may violate access algorithms. Sometimes, a role may be associated with two entitlements, which indicates an intrarole conflict. To remove that "noise," it's recommended that you clean up intrarole conflicts before you investigate user-access conflicts. Then, each role in the pivot table for user-access risk typically lists a single entitlement. Conflicts exist between roles associated with one entitlement and roles associated with any other entitlements.
For example, suppose the User Access Risk summary worksheet contains a row stating that a user named Luisa Miller is assigned roles that violate the Manage Employee and Manage Payroll algorithm. (Once again, the algorithm name identifies two entitlements whose access points conflict.)
Open the result worksheet for that algorithm, create the pivot table, and search for the user name. You'll find a set of records that looks like this:
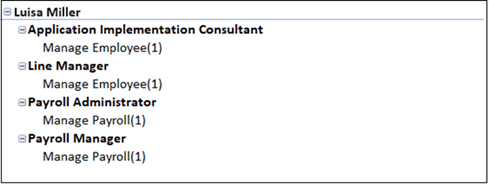
Each role associated with one entitlement conflicts with every role associated with the other entitlement. In this example, there are four conflicts: Application Implementation Consultant with Payroll Administrator, Application Implementation Consultant with Payroll Manager, Line Manager with Payroll Administrator, and Line Manager with Payroll Manager.
Your typical recourse is to rescind the user's access to one of the roles in each conflict. In this example, you would use the Security Console to remove either Application Implementation Consultant and Line Manager, or Payroll Administrator and Payroll Manager. Another option is to create customized versions of the two roles you would otherwise take away. Each custom role would remove a conflicting access point, but retain other access rights.