Access Examples: Intrarole Risk
To begin an intrarole-risk investigation, review the Intrarole Access Risks summary worksheet. It may contain records of analysis by two types of algorithm.
The first type detects sensitive access: A role may include individual privileges whose assignments are worthy of review because each provides broad access. These algorithms include the word "sensitive" in their names. For each of these algorithms that a role has violated, open the algorithm-result spreadsheet. In it, each record identifies a sensitive access point, the role that contains it, and a user assigned the role. You may remove the role from a user who doesn't need its sensitive access. More commonly, the user requires the sensitive access, but should be monitored.
The second intrarole-algorithm type detects occasions when a role on its own grants privileges that conflict with one another. The name of each of these algorithms consists of the names of two entitlements containing access points that would enable users to perform conflicting actions. For each algorithm that a role has violated, open the algorithm-result worksheet and create a pivot table based on these three values:
-
Role: This identifies the role in which a conflict exits.
-
Access Entitlement Name: Any role associated with two entitlements necessarily has an intrarole conflict. (The pivot table is likely to include records in which a role is associated with one entitlement. They apply to user-access-risk conflicts, so you can ignore them as you investigate intrarole conflicts.)
-
Incident Information: These records identify paths to access points that conflict within the role. Each path belonging to one entitlement conflicts with every path belonging to the other entitlement.
For example, suppose the Intrarole Access Risks summary worksheet contains four rows that identify job roles with intrarole conflicts. One of them, Human Resource Manager, violates an algorithm called Manage Employee and Manage Payroll. The role is assigned to 25 people. This role is listed first in the following illustration.
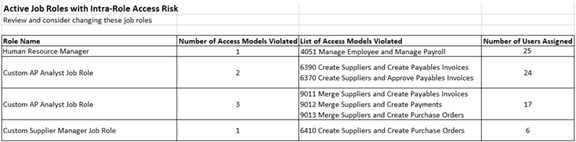
Open the result worksheet for that algorithm (click on the tab labeled with its name), create the pivot table, and search on the role name. You'll find a set of records that looks like this:
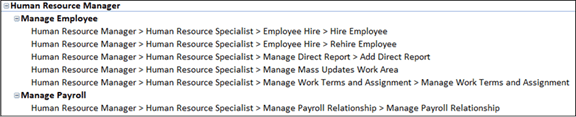
In this example, the one path belonging to the Manage Payroll entitlement conflicts with each of the five paths belonging to the Manage Employee entitlement.
You might decide that the number of affected users is large enough that you should redesign the role to eliminate its conflicts. In this example, you might use the Security Console to remove the one access point that conflicts with all the others: Manage Payroll Relationship.
Or, suppose that the number of users had been smaller and that, having identified those users, you realize they require the conflicting access to do their jobs. You might choose to leave the role as it is, monitor those users regularly, and prevent the role from being assigned to users who don't need its conflicting access.
Then follow the same process to resolve conflicts in any remaining roles. (There are three in this example.) Use the Intrarole Access Risks summary worksheet to identify a suspect role and the algorithms it's violated. Open the worksheet for each algorithm, create the pivot table, and search for the role. Note, though, that if you've already created a pivot table for an algorithm as you cleaned up conflicts in another role, you can reuse that pivot table.