2 Configuring an HSM for Oracle Key Vault
The HSM can be configured to protect keys, or work in a classic primary-standby configuration or in a multi-master cluster.
- Protecting the Oracle Key Vault TDE Master Key with the HSM
You can use the Oracle Key Vault management console to configure protection for the TDE master encryption key. - Enabling HSM in a High Availability Key Vault Installation
In a primary-standby Oracle Key Vault installation, you must enable the HSM separately on the primary and standby servers. - HSMs in a Multi-Master Cluster
You can configure HSMs in a multi-master cluster with a single node or multiple nodes. - Backup and Restore Operations in an HSM-Enabled Oracle Key Vault Instance
You can back up and restore an HSM-enabled Oracle Key Vault instance. - Reverse Migration Operations to a Local Wallet
Reverse migrating an HSM-enabled Oracle Key Vault server reverts the Key Vault server to using the recovery passphrase to protect the TDE wallet.
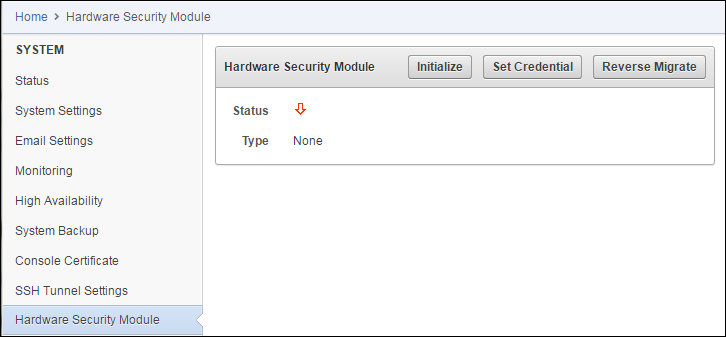
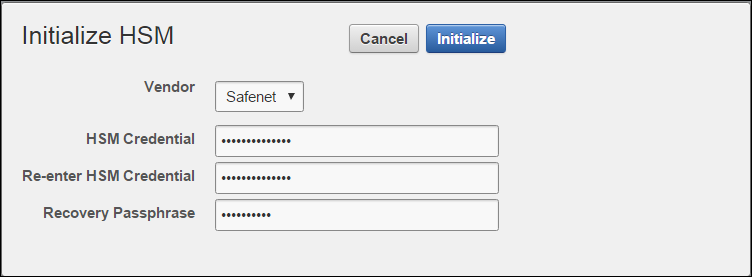
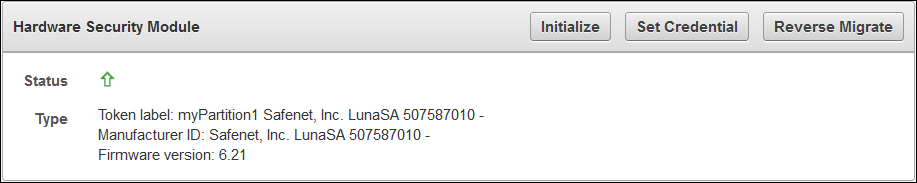
2.1 Protecting the Oracle Key Vault TDE Master Key with the HSM
You can use the Oracle Key Vault management console to configure protection for the TDE master encryption key.
Note:
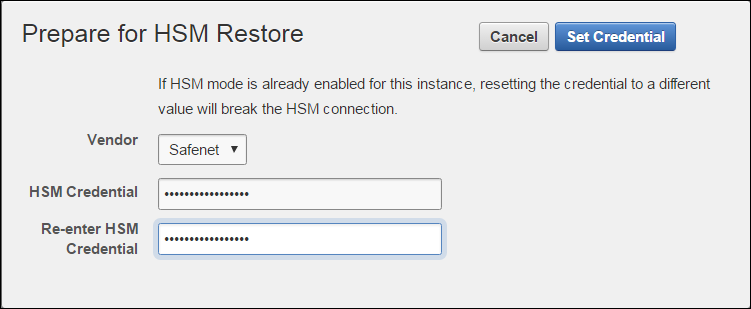
If you change the HSM credential on the HSM after initialization, then you must also update the HSM credential on the Oracle Key Vault server using the Set Credential command.Parent topic: Configuring an HSM for Oracle Key Vault
2.2 Enabling HSM in a High Availability Key Vault Installation
In a primary-standby Oracle Key Vault installation, you must enable the HSM separately on the primary and standby servers.
You must perform this task before pairing these two servers in a primary-standby configuration. If you have already HSM-enabled either the primary or the standby server, or both, but do not follow these steps and then do a primary-standby pairing, then the configuration will fail. If the servers are already paired but neither are HSM-enabled, then you must unpair them, reinstall the standby server, and the follow these steps.
Related Topics
Parent topic: Configuring an HSM for Oracle Key Vault
2.3 HSMs in a Multi-Master Cluster
You can configure HSMs in a multi-master cluster with a single node or multiple nodes.
- About HSMs in a Multi-Master Cluster
An HSM in Oracle Key Vault stores a top level master encryption key that acts as a Root of Trust (RoT). - Configuring an HSM for a Multi-Master Cluster with a Single Node
To use an HSM with a multi-master cluster, you should start with a single HSM-enabled node and add additional HSM-enabled nodes. - Configuring an HSM for a Multi-Master Cluster with Multiple Nodes
You can configure HSM for multiple nodes by copying information from an HSM-enabled node to the non-enabled nodes.
Parent topic: Configuring an HSM for Oracle Key Vault
2.3.1 About HSMs in a Multi-Master Cluster
An HSM in Oracle Key Vault stores a top level master encryption key that acts as a Root of Trust (RoT).
This RoT protects master encryption keys that Oracle Key Vault uses. HSMs are built with specialized tamper-resistant hardware which is harder to access than normal servers. This protects the RoT and makes it difficult to extract encrypted data, lowering the risk of compromise. In addition, you can use HSMs in FIPS 140-2 level 3 mode, which enables you to meet certain compliance requirements.
Note:
An existing Oracle Key Vault deployment cannot be migrated to use an HSM as a RoT.In a multi-master Oracle Key Vault installation, any Key Vault node in the cluster can use any HSM. The nodes in the multi-master cluster can use different TDE wallet passwords, RoT keys, and HSM credentials.
Note:
To ensure complete security, you must HSM-enable all Oracle Key Vault nodes in the cluster.Parent topic: HSMs in a Multi-Master Cluster
2.3.2 Configuring an HSM for a Multi-Master Cluster with a Single Node
To use an HSM with a multi-master cluster, you should start with a single HSM-enabled node and add additional HSM-enabled nodes.
Oracle recommends the following steps to configure an HSM for a multi-master cluster with a single node:
- Configure the first node of the cluster.
- Configure HSM on the first node before adding any new nodes. If there is already more than one node in the cluster, then configure the HSM for a multi-master cluster with multiple nodes.
- HSM-enable the candidate node before adding it to the cluster.
- Add the HSM-enabled candidate node to the cluster using a controller node that is also HSM-enabled. If any node in the cluster is already HSM-enabled, you cannot add a new node that is not HSM-enabled.
Parent topic: HSMs in a Multi-Master Cluster
2.3.3 Configuring an HSM for a Multi-Master Cluster with Multiple Nodes
You can configure HSM for multiple nodes by copying information from an HSM-enabled node to the non-enabled nodes.
Configuring an HSM for a Multi-Master Cluster with a Single Node explains how to configure an HSM for a multi-master cluster. If the first node to be HSM-enabled is in a cluster that already has multiple nodes, then you must manually copy information from that HSM-enabled Oracle Key Vault to the other Oracle Key Vault installations in the cluster before you can enable HSM in any other nodes. If the first node to be HSM-enabled has a read-write peer, then the read-write peer will not be able to decrypt the information from the HSM-enabled node until the bundle is copied and applied successfully to the read-write peer.
- Log in to the Oracle Key Vault management console as a user who has the System Administrator role.
- Click the System tab.
- On the left side of the System page, click Hardware Secure Module.
-
On the HSM-enabled node, click Create Bundle on the HSM page.
-
Log in to the HSM-enabled node through SSH as user
support.ssh support@hsm_enabled_node - Switch to the
rootuser.su root -
To copy the bundle to the
/usr/local/okv/hsmlocation on each of the other nodes using the IP address:scp /usr/local/okv/hsm/hsmbundle support@ip_address:/tmp -
Log in to each node in the cluster using the IP address (except the original HSM-enabled node):
ssh support@ip_address - Switch to the
rootuser.su root -
Perform the following steps on each node:
cp /tmp/hsmbundle /usr/local/okv/hsm/ chown oracle:oinstall /usr/local/okv/hsm/hsmbundle -
On each node except the original HSM-enabled node, click Apply Bundle on the HSM page.
You must apply the bundle immediately on all nodes before you reverse-migrate the original HSM-enabled node.
- Proceed to HSM-enable each of these nodes in the same way that you HSM-enabled the first node.
- After you have HSM-enabled all nodes and verified the replication between all nodes, remove the
hsmbundlefile from all of the nodes.
Parent topic: HSMs in a Multi-Master Cluster
2.4 Backup and Restore Operations in an HSM-Enabled Oracle Key Vault Instance
You can back up and restore an HSM-enabled Oracle Key Vault instance.
- Backup Operations in an HSM-Enabled Oracle Key Vault Instance
Backing up Oracle Key Vault data in an HSM-enabled instance is the same as backing up an instance that has not been HSM enabled. - Restore Operations in an HSM-Enabled Oracle Key Vault Instance
Only backups made to an HSM-enabled Oracle Key Vault instance can be restored onto an HSM-enabled Oracle Key Vault instance.
Parent topic: Configuring an HSM for Oracle Key Vault
2.4.1 Backup Operations in an HSM-Enabled Oracle Key Vault Instance
Backing up Oracle Key Vault data in an HSM-enabled instance is the same as backing up an instance that has not been HSM enabled.
Related Topics
2.4.2 Restore Operations in an HSM-Enabled Oracle Key Vault Instance
Only backups made to an HSM-enabled Oracle Key Vault instance can be restored onto an HSM-enabled Oracle Key Vault instance.
Related Topics
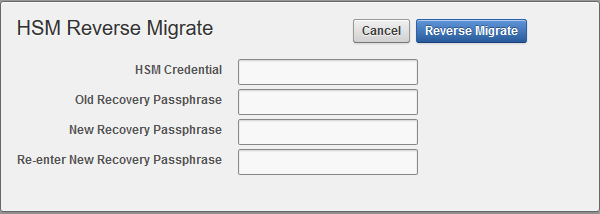
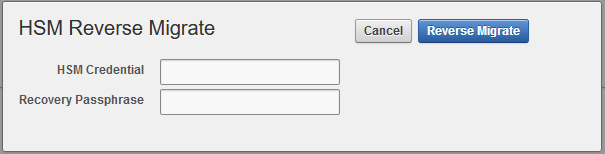
2.5 Reverse Migration Operations to a Local Wallet
Reverse migrating an HSM-enabled Oracle Key Vault server reverts the Key Vault server to using the recovery passphrase to protect the TDE wallet.
This operation is necessary if the HSM that protects Oracle Key Vault must be decommissioned.
- Reverse Migrating a Standalone Deployment
You can reverse migrate a standalone deployment by using the Oracle Key Vault management console. - Reverse Migrating a Primary-Standby Deployment
To reverse migrate a primary-standby deployment, use both the Oracle Key Vault management console and the command line. - Reverse Migrating a Multi-Master Cluster
You can reverse migrate a multi-master cluster by using the Oracle Key Vault management console.
Parent topic: Configuring an HSM for Oracle Key Vault
2.5.1 Reverse Migrating a Standalone Deployment
You can reverse migrate a standalone deployment by using the Oracle Key Vault management console.
Parent topic: Reverse Migration Operations to a Local Wallet
2.5.2 Reverse Migrating a Primary-Standby Deployment
To reverse migrate a primary-standby deployment, use both the Oracle Key Vault management console and the command line.
Parent topic: Reverse Migration Operations to a Local Wallet
2.5.3 Reverse Migrating a Multi-Master Cluster
You can reverse migrate a multi-master cluster by using the Oracle Key Vault management console.
Parent topic: Reverse Migration Operations to a Local Wallet