17 Monitoring and Auditing Oracle Key Vault
Oracle Key Vault administrators can monitor and audit the Oracle Key Vault system, configure alerts and use reports.
- Managing System Monitoring
System monitoring refers to tasks such as configuring SNMP connections, email notifications, the syslog destination, and system diagnostics. - Configuring Oracle Key Vault Alerts
You can select the type of alerts that you want to see in the Oracle Key Vault dashboard. - Managing System Auditing
Auditing entails tasks such as capturing audit records in a syslog file or downloading the audit records to a local file. - Using Oracle Key Vault Reports
Oracle Key Vault collects statistical information on a range of activities that impact Key Vault operations.
17.1 Managing System Monitoring
System monitoring refers to tasks such as configuring SNMP connections, email notifications, the syslog destination, and system diagnostics.
- Configuring Remote Monitoring to Use SNMP
With Simple Network Management Protocol (SNMP) enabled, system administrators can remotely monitor the Oracle Key Vault appliance and its services. - Configuring Email Notification
You can use email notifications to directly notify administrators of Key Vault status changes without logging into the Oracle Key Vault management console. - Configuring the Syslog Destination for Individual Multi-Master Cluster Nodes
On each node, you can forward syslog entries to a remote service such as Splunk or SIEM. - Capturing System Diagnostics
To troubleshoot problems that may arise, you can generate a system diagnostics file. - Configuring Oracle Audit Vault Integration for the Node
You can configure the integration of Oracle Audit Vault (but not the Database Firewall component) for a node.
Parent topic: Monitoring and Auditing Oracle Key Vault
17.1.1 Configuring Remote Monitoring to Use SNMP
With Simple Network Management Protocol (SNMP) enabled, system administrators can remotely monitor the Oracle Key Vault appliance and its services.
The collected data can be further processed and presented for the needs of the enterprise.
- About Using SNMP for Oracle Key Vault
You can use the Simple Network Management Protocol (SNMP) to monitor devices on a network for resource usage. - Granting SNMP Access to Users
You can grant any user, including users who are not Oracle Key Vault administrators, access to SNMP data. - Changing the SNMP User Name and Password
You can change the SNMP user name and password for a node at any time. - Changing SNMP Settings on the Standby Server
You change the SNMP settings from the command line on the standby server. - Remotely Monitoring Oracle Key Vault Using SNMP
SNMP enables you to monitor the vital components of Oracle Key Vault remotely without having to install new software in Oracle Key Vault. - SNMP Management Information Base Variables for Oracle Key Vault
Oracle Key Vault provides a set of SNMP Management Information Base (MIB) variables that you can track. - Example: Simplified Remote Monitoring of Oracle Key Vault Using SNMP
In Linux, you can simplify the SNMP commands you manually enter to find Oracle Key Vault information, yet still have useful and detailed output.
Parent topic: Managing System Monitoring
17.1.1.1 About Using SNMP for Oracle Key Vault
You can use the Simple Network Management Protocol (SNMP) to monitor devices on a network for resource usage.
Monitoring Oracle Key Vault is an important aspect how critical Oracle Key Vault's availability is when hundreds or thousands of Oracle and MySQL databases store their TDE master encryption keys in an Oracle Key Vault multi-master cluster. The types of resource usage that you should monitor include memory, CPU utilization, and processes. Even though Oracle Key Vault provides continuous key availability by allowing up to 16 (geographically distributed) instances to be connected to a single cluster, the health of each individual node contributes to the performance and availability of the entire cluster.
You can use Simple Network Management Protocol (SNMP) third-party tool to monitor remote systems that access Oracle Key Vault. The benefits of using SNMP to monitor Oracle Key Vault are as follows:
- There is no need to allow SSH access to Oracle Key Vault. (SSH access should only be enabled for the window of time in which it is being used.)
- You do not need to install additional tools to perform an SNMP monitoring operation.
Oracle Key Vault uses SNMP version 3 for user authentication and data encryption features. Unlike SNMP versions 1 and 2 that communicate in readable, insecure plaintext, SNMP 3 authenticates users and encrypts data on the communication channel between the monitoring server and the target. The information from Oracle Key Vault is unreadable to an intruder, even if the communication channel is intercepted.
In addition, with SNMP enabled on Oracle Key Vault, you can determine whether the key management server (KMIP daemon) is running. To track this information, you must use a third-party SNMP client to poll the Oracle Key Vault instance, because Oracle Key Vault does not provide SNMP client software.
Oracle Key Vault audits the creation and modification of SNMP credentials.
You must be a user with the System Administrator role to configure the SNMP account with a user name and password. These SNMP credentials are needed to access SNMP data.
In a multi-master cluster, the SNMP account with a user name and password can be set for all nodes of the cluster at once. It can also be set for each individual node.
Note:
You must ensure that the SNMP username and password is not the same username and password as any of the Oracle Key Vault administrative user accounts with the System Administrator, Key Administrator, or Audit Manager role.
Parent topic: Configuring Remote Monitoring to Use SNMP
17.1.1.2 Granting SNMP Access to Users
You can grant any user, including users who are not Oracle Key Vault administrators, access to SNMP data.
Parent topic: Configuring Remote Monitoring to Use SNMP
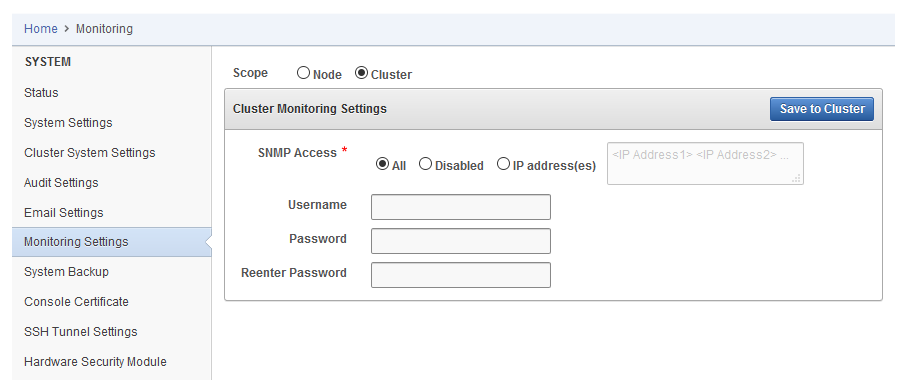
17.1.1.3 Changing the SNMP User Name and Password
You can change the SNMP user name and password for a node at any time.
- Log in to the Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then select Monitoring Settings.
- In the Username, Password, and Reenter Password fields, enter the user name and password information.
- Click Save.
Parent topic: Configuring Remote Monitoring to Use SNMP
17.1.1.4 Changing SNMP Settings on the Standby Server
You change the SNMP settings from the command line on the standby server.
To add SNMP support in a primary-standby environment, you should configure SNMP on both the primary and standby servers before pairing them. This is because the standby server is no longer accessible from the Oracle Key Vault management console because all requests are forwarded to the primary server. However, you can change SNMP settings on the standby server in a primary-standby environment.
The following examples show how to change SNMP settings on a standby server:
snmpuser and password password:./stdby_snmp_enable -a "all" -u "snmpuser" -p "password"./stdby_snmp_enable -a "disabled"snmpuser and password password:./stdby_snmp_enable -a "192.0.2.1 192.0.2.3 192.0.2.3" -u "snmpuser" -p "password"Parent topic: Configuring Remote Monitoring to Use SNMP
17.1.1.5 Remotely Monitoring Oracle Key Vault Using SNMP
SNMP enables you to monitor the vital components of Oracle Key Vault remotely without having to install new software in Oracle Key Vault.
snmpwalk and snmpget from the command line on a remote computer that has a network connection into the SNMP account in Oracle Key Vault.
Parent topic: Configuring Remote Monitoring to Use SNMP
17.1.1.6 SNMP Management Information Base Variables for Oracle Key Vault
Oracle Key Vault provides a set of SNMP Management Information Base (MIB) variables that you can track.
The following table lists the MIB variables that are supported.
Table 17-1 MIBs That SNMP Tracks for Oracle Key Vault
| MIB Variable | Object ID | Description |
|---|---|---|
|
|
1.3.6.1.2.1.25.1.1 |
Tracks the amount of time that an Oracle Key Vault instance has been running |
|
|
1.3.6.1.2.1.2.2.1.7 |
Tracks if the Oracle Key Vault network interface (
|
|
|
1.3.6.1.4.1.2021.4.6 |
Tracks the available RAM |
|
|
1.3.6.1.4.1.2021.4.5 |
Tracks the total amount of RAM being used |
|
|
1.3.6.1.4.1.2021.11.53 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent idle |
|
|
1.3.6.1.4.1.2021.11.56 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing hardware interrupts |
|
|
1.3.6.1.4.1.2021.11.55 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing kernel-level code |
|
|
1.3.6.1.4.1.2021.11.51 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing reduced-priority code |
|
|
1.3.6.1.4.1.2021.11.52 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing system-level code |
|
|
1.3.6.1.4.1.2021.11.50 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent processing user-level code |
|
|
1.3.6.1.4.1.2021.11.54 |
For CPU monitoring; tracks the number of ticks (typically 1/100s) spent waiting for input-output (IO) |
|
|
1.3.6.1.4.1.2021.2 |
Tracks the number of processes running under a certain name. Names we monitor are |
See Also:
For more information refer to the Net-SNMP documentation at http://www.net-snmp.org
Parent topic: Configuring Remote Monitoring to Use SNMP
17.1.1.7 Example: Simplified Remote Monitoring of Oracle Key Vault Using SNMP
In Linux, you can simplify the SNMP commands you manually enter to find Oracle Key Vault information, yet still have useful and detailed output.
The configuration in this section assumes that you have granted SNMP access to a trusted user. It also assumes that the you have installed the SNMP Management Information Base (MIB) variables on the remote host that will monitor Oracle Key Vault.
For example, a lengthy version of the snmpwalk command for an SNMP user named snmp_admin is as follows:
snmpwalk -v3 OKV_IP_address -n "" -l authPriv -u snmp_admin -a SHA -A snmp_user_password -x AES -X snmp_user_password
This command lists the vital services that are running on Oracle Key Vault. However, you can modify the command (and other SNMP commands) to be not only shorter, but to show additional information, such as whether the services are running or not running.
To simplify this type of command, you can edit the /etc/snmp/snmp.conf configuration file so that the SNMP commands you enter will automatically include commonly used settings, such as the default user or the default security level. The example in this topic omits password parameters so that users can enter the password at the command line interactively.
- Log in to the remote host that will monitor Oracle Key Vault.
- Edit the
/etc/snmp/snmp.conf, which appears as follows:# As the snmp packages come without MIB files due to license reasons, # loading MIBs is disabled by default. If you added the MIBs you # can reenable loading them by commenting out the following line. mibs :
- Comment out the
# mibs :line and then add the following lines, as follows:# loading MIBs is disabled by default. If you added the MIBs you # can reenable loading them by commenting out the following line. # mibs : defSecurityName snmp_admin defSecurityLevel authPriv defAuthType SHA defPrivType AES
In this example:
defSecurityName: Enter the name of the user to whom you granted SNMP access. This example usessnmp_admin.defSecurityLevel: Enter the default security level to use. This example usesauthPriv, which enables communication with authentication and privacy.defAuthType: Enter the default authorization type. This example usesSHA.defPrivType: Enter the default privilege type. This example usesAES.
- Restart
snmpdto load the configuration file.For example, for Linux 7:
systemctl restart snmpd
For Linux 6:
service snmpd restart
- To run the simplified version of the
snmpwalkcommand that was shown earlier, enter the following command:snmpwalk okv_ip_address prNames -A snmp_user_pwd -X snmp_user_pwd
In this command,
prNamesrefers to "process names", which displays the names of processes instead of numbers. For example:$ snmpwalk 192.0.2.254 prNames -A snmp_user_pwd -X snmp_user_pwd UCD-SNMP-MIB::prNames.1 = STRING: mwecsvc UCD-SNMP-MIB::prNames.2 = STRING: httpd UCD-SNMP-MIB::prNames.3 = STRING: kmipd UCD-SNMP-MIB::prNames.4 = STRING: ora_pmon_dbfwdb UCD-SNMP-MIB::prNames.5 = STRING: ServiceManager UCD-SNMP-MIB::prNames.6 = STRING: adminsrvr UCD-SNMP-MIB::prNames.7 = STRING: distsrvr UCD-SNMP-MIB::prNames.8 = STRING: recvsrvr
snmptable command now becomes the following. snmptable okv_ip_address prTable -A snmp_user_pwd -X snmp_user_pwd
Output similar to the following appears.
SNMP table: UCD-SNMP-MIB::prTable
prIndex prNames prMin prMax prCount prErrorFlag prErrMessage prErrFix prErrFixCmd
1 mwecsvc 1 1 1 noError noError
2 httpd 1 20 9 noError noError
3 kmipd 1 2 2 noError noError
4 ora_pmon_dbfwdb 1 1 1 noError noError
5 ServiceManager 1 1 1 noError noError
6 adminsrvr 1 1 1 noError noError
7 distsrvr 1 1 1 noError noError
8 recvsrvr 1 1 1 noError noError
The next example shows how you would now run the snmpdf command:
snmpdf okv_ip_address -A snmp_user_pwd -X snmp_user_pwd
Output similar to the following appears.
Description Size (kB) Used Available Used% / 20027260 7247856 12779404 36% /usr/local/dbfw/tmp 6932408 15764 6916644 0% /var/log 5932616 19932 5912684 0% /tmp 1999184 3072 1996112 0% /var/lib/oracle 143592160 35023900 108568260 24%
Parent topic: Configuring Remote Monitoring to Use SNMP
17.1.2 Configuring Email Notification
You can use email notifications to directly notify administrators of Key Vault status changes without logging into the Oracle Key Vault management console.
- About Email Notification
Email notifications alert users of status changes and are used to complete the processes of endpoint enrollment and user password reset operations. - Configuring Email Settings
You can configure the Simple Mail Transfer Protocol (SMTP) server properties to receive email notifications from Oracle Key Vault. - Testing the Email Configuration
Oracle Key Vault management console enables you to send test emails to test the email configuration. - Disabling Email Notifications for a User
You can use the Oracle Key Vault management console to enable or disable email notifications.
Parent topic: Managing System Monitoring
17.1.2.1 About Email Notification
Email notifications alert users of status changes and are used to complete the processes of endpoint enrollment and user password reset operations.
To enable email notification you must set your email preferences in Oracle Key Vault. You can choose the events that you want updates to. The events include Oracle Key Vault system status like disk utilization, backup, and primary-standby, or user and endpoint status like expiration of user passwords, endpoint certificates, and keys, or cluster status like the heartbeat lag, naming conflicts, cluster-wide HSM status, and others.
Oracle Key Vault supports anonymous and insecure connections to the SMTP server. By default, Oracle Key Vault uses the default Java truststore packaged with Oracle Key Vault's Java library to validate the server certificate. Optionally, you can upload a custom truststore in order to use a specific certificate or certificate chain at the same time you configure SMTP settings.
You can modify the SMTP server configuration at any time. If a custom SMTP certificate was used initially, and you later decide to use the default, you can modify the trust store setting to default, instead of custom.
For example:
-
The enrollment token generated during endpoint enrollment can be mailed directly to the endpoint administrator from Oracle Key Vault.
-
An Oracle Key Vault system administrator can send the random temporary password directly to the user when the user password is reset.
To enable email notifications successfully, there must be a connection between Oracle Key Vault and the SMTP server.
You can disable email notifications at any time.
Parent topic: Configuring Email Notification
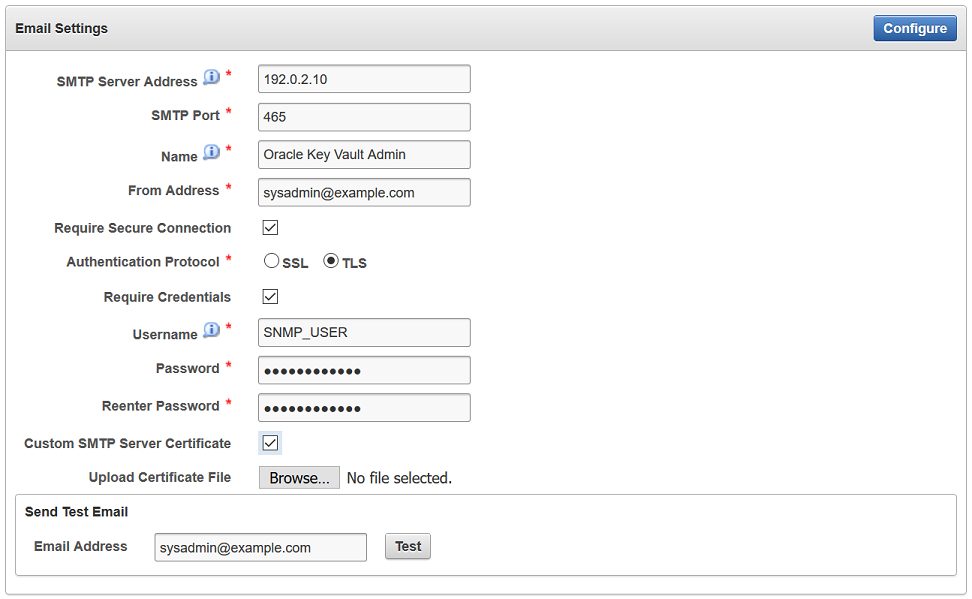
17.1.2.2 Configuring Email Settings
You can configure the Simple Mail Transfer Protocol (SMTP) server properties to receive email notifications from Oracle Key Vault.
Parent topic: Configuring Email Notification
17.1.2.3 Testing the Email Configuration
Oracle Key Vault management console enables you to send test emails to test the email configuration.
Related Topics
Parent topic: Configuring Email Notification
17.1.2.4 Disabling Email Notifications for a User
You can use the Oracle Key Vault management console to enable or disable email notifications.
Parent topic: Configuring Email Notification
17.1.3 Configuring the Syslog Destination for Individual Multi-Master Cluster Nodes
On each node, you can forward syslog entries to a remote service such as Splunk or SIEM.
- Setting the Syslog Destination Setting for the Node
You can set the syslog destination to use either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP). - Clearing the Syslog Destination Setting for the Node
You can clear the syslog destination setting for the node and then reset the node to the cluster setting.
Parent topic: Managing System Monitoring
17.1.3.1 Setting the Syslog Destination Setting for the Node
You can set the syslog destination to use either Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
17.1.4 Capturing System Diagnostics
To troubleshoot problems that may arise, you can generate a system diagnostics file.
- About Capturing System Diagnostics
The Oracle Key Vault diagnostics file provides advanced debug and troubleshooting information for problems that you may encounter while using Oracle Key Vault. - Installing the Diagnostics Generation Utility
You can use the Oracle Key Vault management console to download instructions for installing and using the diagnostics generation utility. - Generating a System Diagnostics File
The system diagnostics file that you download is in a.zipfile. - Removing the Diagnostic Generation Utility Temporary Files
Removing the diagnostic generation utility temporary files frees up space on your server. - Removing the Diagnostic Generation Utility
If you no longer need to generate system diagnostic reports, then you can remove the diagnostic generation utility.
Parent topic: Managing System Monitoring
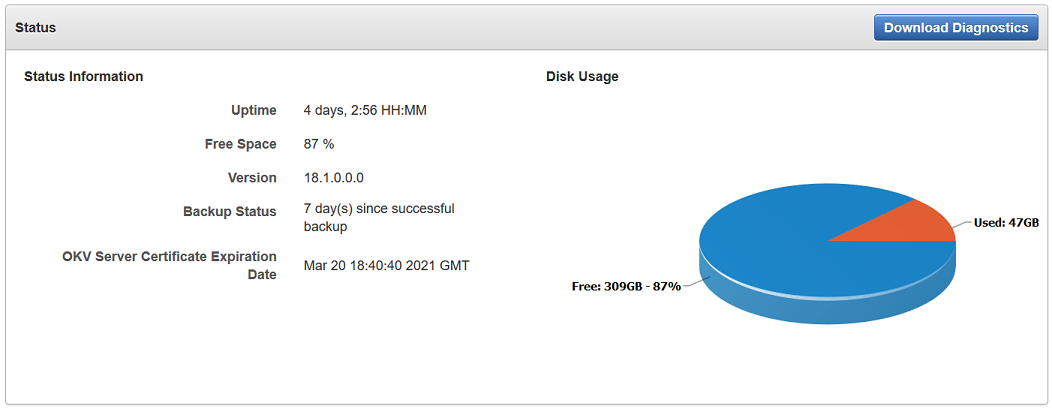
17.1.4.1 About Capturing System Diagnostics
The Oracle Key Vault diagnostics file provides advanced debug and troubleshooting information for problems that you may encounter while using Oracle Key Vault.
You can download this file and provide it to Oracle support for further analysis and debugging. The diagnostics file includes information about free space and disk usage reported is space available to Oracle Key Vault and not based on total disk size.
Diagnostics reporting is not enabled by default. You must enable the feature to generate diagnostics reports. After you have enabled diagnostics, you can configure the necessary information to be captured in diagnostics reports. You then can customize and package diagnostics reports with flexibility. Be aware that the first time you run the diagnostic utility or after the Oracle Key Vault system's internal database has been restarted, it can take longer that it will in future runs because it must gather all the diagnostic information in the system.
If you plan to perform an upgrade of Oracle Key Vault, then you must remove the diagnostic generation utility before performing the upgrade.
Parent topic: Capturing System Diagnostics
17.1.4.2 Installing the Diagnostics Generation Utility
You can use the Oracle Key Vault management console to download instructions for installing and using the diagnostics generation utility.
Parent topic: Capturing System Diagnostics
17.1.4.3 Generating a System Diagnostics File
The system diagnostics file that you download is in a .zip file.
Related Topics
Parent topic: Capturing System Diagnostics
17.1.4.4 Removing the Diagnostic Generation Utility Temporary Files
Removing the diagnostic generation utility temporary files frees up space on your server.
Parent topic: Capturing System Diagnostics
17.1.4.5 Removing the Diagnostic Generation Utility
If you no longer need to generate system diagnostic reports, then you can remove the diagnostic generation utility.
Parent topic: Capturing System Diagnostics
17.1.5 Configuring Oracle Audit Vault Integration for the Node
You can configure the integration of Oracle Audit Vault (but not the Database Firewall component) for a node.
- Log into any Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then System Settings from the left navigation bar.
- Select the Enable check box to Oracle Audit Vault Integration for the node.
- In the Password and Reenter password fields that appear after you click Enable, enter the password of the user in the database that Audit Vault and Database Firewall will use to extract the audit records.
- Click Save.
Parent topic: Managing System Monitoring
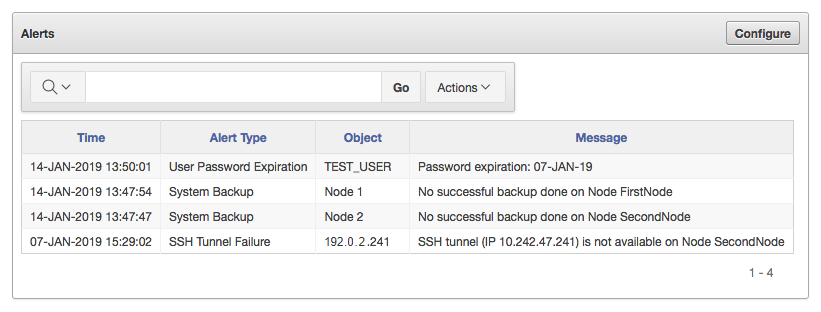
17.2 Configuring Oracle Key Vault Alerts
You can select the type of alerts that you want to see in the Oracle Key Vault dashboard.
- About Configuring Alerts
System administrators can configure alerts from the Oracle Key Vault dashboard, but all users can see alerts for their security objects. - Configuring Alerts
You can configure alerts in the Reports page of the Oracle Key Vault management console. - Viewing Open Alerts
Users can view alerts depending on their privileges.
Parent topic: Monitoring and Auditing Oracle Key Vault
17.2.1 About Configuring Alerts
System administrators can configure alerts from the Oracle Key Vault dashboard, but all users can see alerts for their security objects.
The Oracle Key Vault dashboard is the first page you see on logging into to the management console. You can navigate to this page by clicking the Home tab. All users can see the alerts on security objects they have access to, but only users with the System Administrator role can configure alerts.
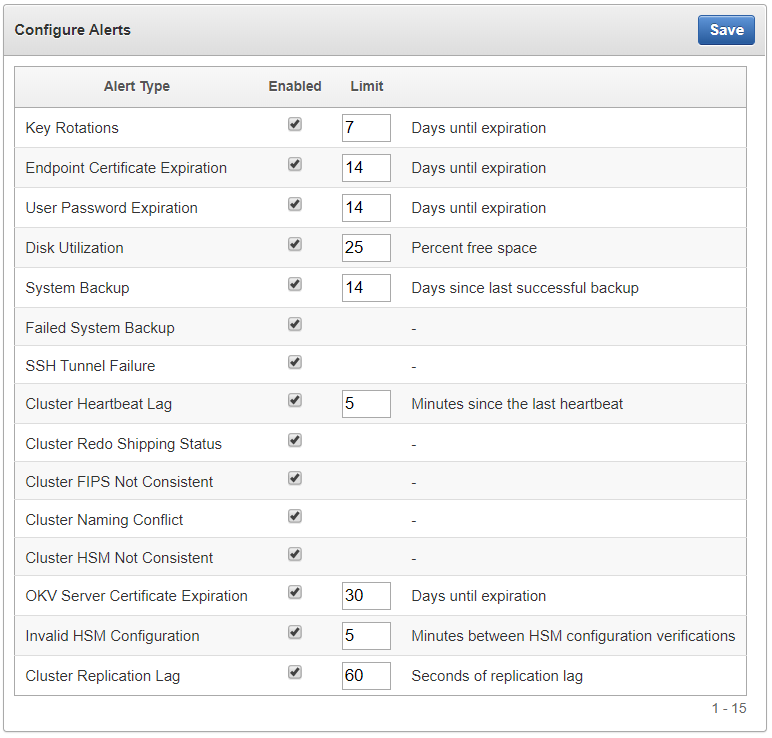
Oracle Key Vault has 17 alerts, including alerts for an HSM-enabled Oracle Key Vault server, that you can configure with appropriate thresholds according to your requirements.
You can configure the following alerts:
Table 17-2 Available Alerts
| Alert Type | Applicability | Purpose |
|---|---|---|
Cluster FIPS Not Consistent |
Cluster-wide | Raised when at least one, but not all, ACTIVE nodes in the cluster are in FIPS mode
|
Cluster Heartbeat Lag |
Node specific | Raised when a node has not received a heartbeat from another ACTIVE node in the cluster for over the threshold value (default 5 minutes)
|
Cluster HSM Not Consistent |
Cluster-wide | Raised when at least one, but not all, ACTIVE nodes in the cluster are HSM-enabled
|
Cluster Naming Conflict |
Cluster-wide | Raised when a naming conflict is resolved |
Cluster Redo Shipping Status |
Node specific | Raised when a read-write node is unable to ship redo to its read-write peer, and as a result, is in read-only restricted mode |
Disk Utilization |
Node specific | Raised when the free disk space percentage of the /var/lib/oracle partition is lower than the threshold value (default 25 percent)
|
Endpoint Certificate Expiration |
Cluster-wide | Raised when an endpoint's certificate is expiring within the threshold value (default 30 days) |
Failed System Backup |
Node specific | Raised when the last backup did not complete successfully |
Primary-Standby Data Guard Broker Status |
Primary-Standby Only | Raised when the Oracle Data Guard Broker status is not ENABLED |
Primary-Standby Data Guard Fast-Start Failover Status |
Primary-Standby Only | Raised when the fast-start failover status is not SYNCHRONIZED |
Primary-Standby Destination Failure |
Primary-Standby Only | Raised when the switchover status is FAILED DESTINATION |
Primary-Standby Restricted Mode |
Primary-Standby Only | Raised when in primary-standby environment and the primary is running in read-only restricted mode |
Primary-Standby Role Change |
Primary-Standby Only | Raised when there is a role change |
Key Rotations |
Cluster-wide | Raised when a key's deactivation date is within the threshold value (default 7 days) |
OKV Server Certificate Expiration |
Node specific | Raised when the Oracle Key Vault server certificate is expiring within the threshold value (default 30 days) |
SSH Tunnel Failure |
Node specific | Raised when an SSH tunnel is not available |
System Backup |
Node specific | Raised when the last successful backup is over the threshold value (default 14 days) |
User Password Expiration |
Cluster-wide | Raised when a user's password will expire within the threshold value (default 14 days) |
OKV Server Certificate Expiration |
Node specific | Raised when the Oracle Key Vault server certificate is expiring within the threshold value (default 30 days) |
Invalid HSM Configuration |
Node specific | Raised when there is an error in the HSM configuration (checked by default every 5 minutes) |
Cluster Replication Lag |
Node specific | Raised when incoming replication lag is greater than the threshold value (default 60 seconds) |
Related Topics
Parent topic: Configuring Oracle Key Vault Alerts
17.2.2 Configuring Alerts
You can configure alerts in the Reports page of the Oracle Key Vault management console.
Related Topics
Parent topic: Configuring Oracle Key Vault Alerts
17.2.3 Viewing Open Alerts
Users can view alerts depending on their privileges.
Parent topic: Configuring Oracle Key Vault Alerts
17.3 Managing System Auditing
Auditing entails tasks such as capturing audit records in a syslog file or downloading the audit records to a local file.
- About Auditing in Oracle Key Vault
Oracle Key Vault records and time-stamps all endpoint and user activity. - Configuring Syslog to Store Audit Records
You can configure the Oracle Key Vault syslog to store audit records if the System Administrator has enabled this functionality. - Configuring Audit Settings for a Multi-Master Cluster
You can enable or disable auditing for a multi-master cluster. - Viewing Audit Records
To view audit records, access the Oracle Key Vault management console Audit Trail page. - Exporting and Deleting Audit Records
Oracle Key Vault audit records are stored in a.csvfile. - Audit Consolidation with Audit Vault and Database Firewall
Oracle Key Vault audit data can be forwarded to Audit Vault and Database Firewall (AVDF) for audit consolidation.
Parent topic: Monitoring and Auditing Oracle Key Vault
17.3.1 About Auditing in Oracle Key Vault
Oracle Key Vault records and time-stamps all endpoint and user activity.
The audit records include endpoint groups and user groups, from endpoint enrollment and user password reset, to the management of keys and wallets, and changes to system settings and SNMP credentials. The audit trail captures details on who initiated which action, with what keys and tokens, and the result of the action. In addition, it records the success or failure of each action.
Only a user who has the Audit Manager role can manage the audit trail for Oracle Key Vault activity. Each user can see audit records of the objects that the user can access.
Auditing in Oracle Key Vault is enabled by default.
A user with the Audit Manager role can see and manage all the audit records. Other users can see only those audit records that pertain to security objects that they have created, or have been granted access to.
The audit manager can export audit records to view system activity off line. After exporting the records, the audit manager can delete them from the system to free up resources.
Related Topics
Parent topic: Managing System Auditing
17.3.2 Configuring Syslog to Store Audit Records
You can configure the Oracle Key Vault syslog to store audit records if the System Administrator has enabled this functionality.
Related Topics
Parent topic: Managing System Auditing
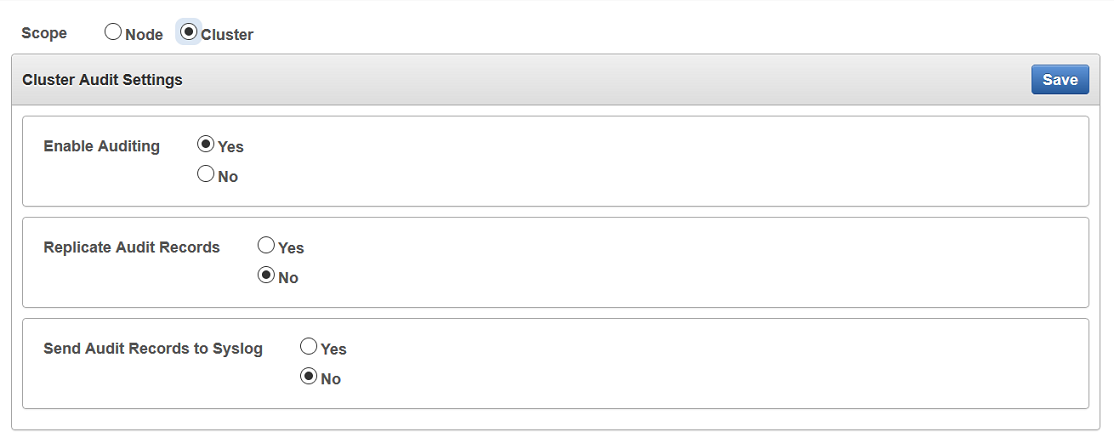
17.3.3 Configuring Audit Settings for a Multi-Master Cluster
You can enable or disable auditing for a multi-master cluster.
Parent topic: Managing System Auditing
17.3.4 Viewing Audit Records
To view audit records, access the Oracle Key Vault management console Audit Trail page.
Parent topic: Managing System Auditing
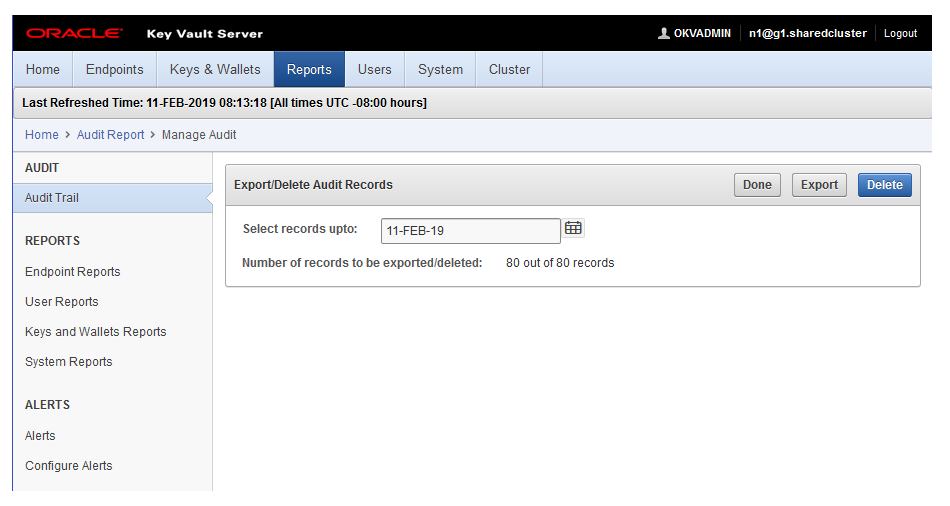
17.3.5 Exporting and Deleting Audit Records
Oracle Key Vault audit records are stored in a .csv file.
.csv file that can be downloaded to the user's local system. The .csv file contains the same details found in the audit trail on the Reports page. The timestamp in the .csv file reflects the time zone of the particular Oracle Key Vault server whose records were exported. After you export the records, you can delete them from the Oracle Key Vault server to free up space.
Parent topic: Managing System Auditing
17.3.6 Audit Consolidation with Audit Vault and Database Firewall
Oracle Key Vault audit data can be forwarded to Audit Vault and Database Firewall (AVDF) for audit consolidation.
Parent topic: Managing System Auditing
17.4 Using Oracle Key Vault Reports
Oracle Key Vault collects statistical information on a range of activities that impact Key Vault operations.
- About Oracle Key Vault Reports
The reports cover system activity, certificate expiration, keys, passwords, entitlement status, and metadata. - Viewing Endpoint Reports
You must have the Audit Manager role to view the four categories of endpoint reports. - Viewing User Reports
You must have the Audit Manager role to view the four categories of user reports. - Viewing Keys and Wallets Reports
You must have the Audit Management role to view the two categories of keys and wallets reports. - Viewing System Reports
You must have the Audit Manager role to view the three categories of system reports.
Parent topic: Monitoring and Auditing Oracle Key Vault
17.4.1 About Oracle Key Vault Reports
The reports cover system activity, certificate expiration, keys, passwords, entitlement status, and metadata.
Oracle Key Vault provides four types of reports for endpoints, users, keys and wallets, and system. In a multi-master cluster, some reports contain additional information, such as the node ID, node name, and IP address.
The four report types are as follows:
-
Endpoint reports contain details of all endpoint and endpoint group activity, certificate and password expiration, and access privileges.
-
User reports contain details of all user and user group activity, their certificate and password expiration, and access privileges.
-
Keys and wallets reports list the access privileges granted to all keys and wallets, and the details of TDE master encryption keys managed by Oracle Key Vault.
-
System reports contain a history of system backups taken and scheduled, details of remote restoration points, and RESTful API usage.
A user who has the Audit Manager role can view all reports, including reports that are accessible from the Audit Trail pages in the Oracle Key Vault management console. A user with the Key Administrator role can view user reports and keys and wallets reports. Users with the System Administrator role can view endpoint, user, and system reports.
Related Topics
Parent topic: Using Oracle Key Vault Reports
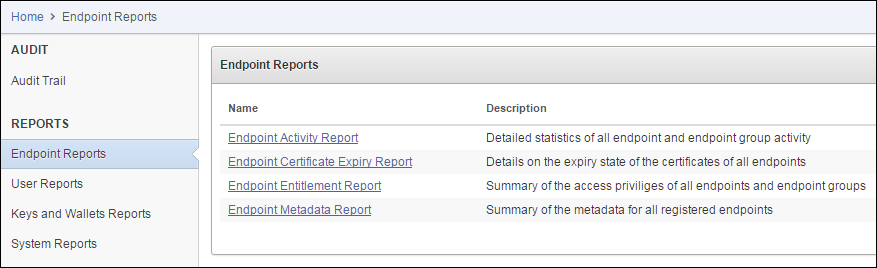
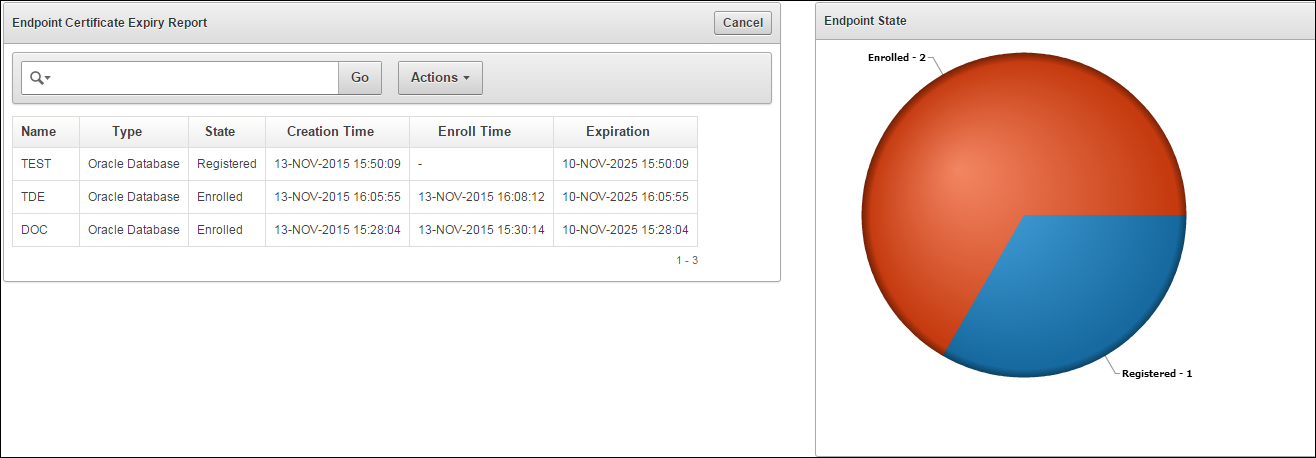
17.4.2 Viewing Endpoint Reports
You must have the Audit Manager role to view the four categories of endpoint reports.
Parent topic: Using Oracle Key Vault Reports
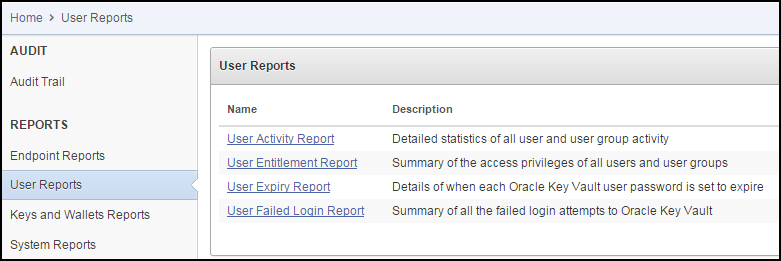
17.4.3 Viewing User Reports
You must have the Audit Manager role to view the four categories of user reports.
Parent topic: Using Oracle Key Vault Reports
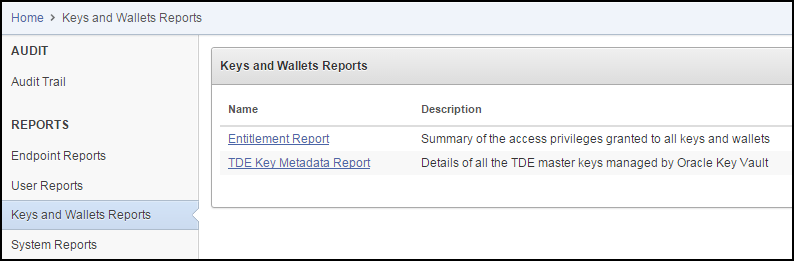
17.4.4 Viewing Keys and Wallets Reports
You must have the Audit Management role to view the two categories of keys and wallets reports.
Parent topic: Using Oracle Key Vault Reports
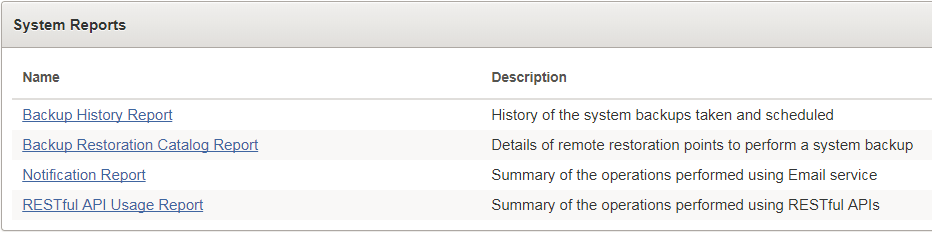
17.4.5 Viewing System Reports
You must have the Audit Manager role to view the three categories of system reports.
Parent topic: Using Oracle Key Vault Reports