10 Managing Oracle Key Vault Virtual Wallets and Security Objects
You can create a virtual wallet to store security objects, and then share this wallet with trusted peers at different access levels.
- Managing Virtual Wallets
A virtual wallet is a container for security objects that you can create and then grant access to users. - Managing Access to Virtual Wallets from Keys & Wallets Tab
You can grant virtual wallet access to and revoke virtual wallet access from endpoint by using the Keys & Wallets tab. - Managing Access to Virtual Wallets from User’s Menu
To manage access control on virtual wallets for users, endpoints, and their respective groups, you can use the Users menu or Endpoints menu. - Managing the State of a Key or a Security Object
You can set the date to activate or deactivate keys or security objects, and change the state of some virtual wallet security objects. - Managing the Extraction of Symmetric Keys from Oracle Key Vault
You can restrict symmetric keys from leaving Oracle Key Vault. - Managing Details of Security Objects
You can manage details about security objects, such as find details about these objects and modifying these details.
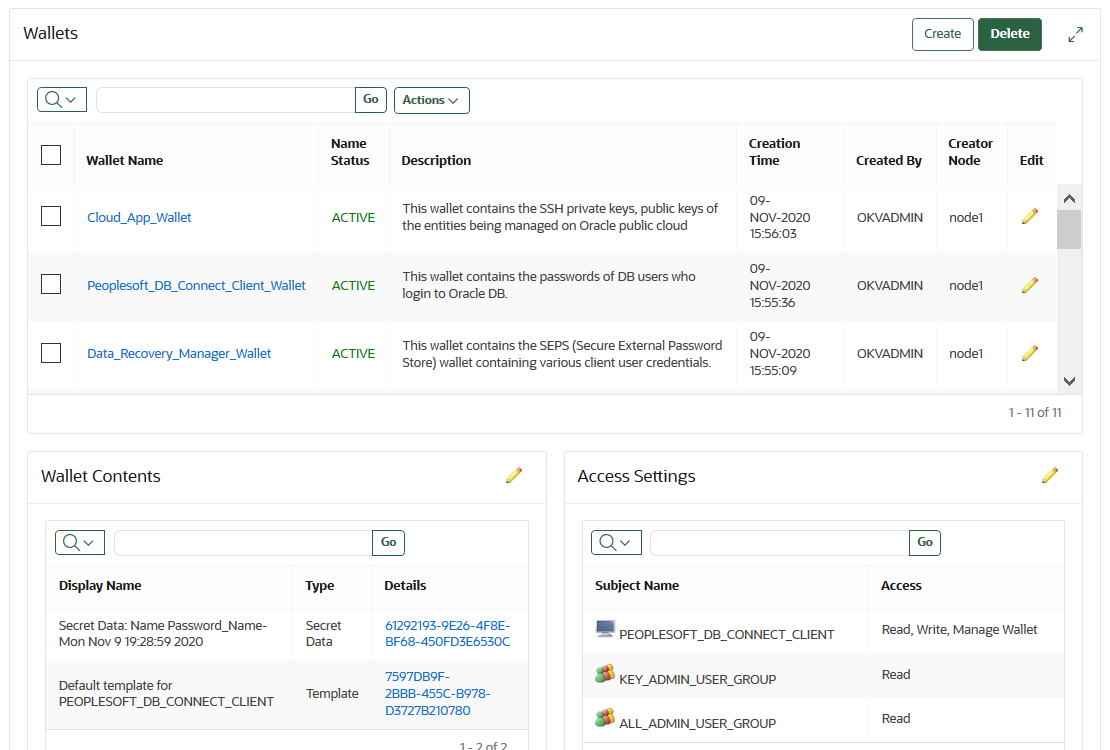
10.1 Managing Virtual Wallets
A virtual wallet is a container for security objects that you can create and then grant access to users.
- About Virtual Wallets
A virtual wallet is a container for security objects. - Creating a Virtual Wallet
You can create a virtual wallet and add security objects to it at the same time. - Modifying a Virtual Wallet
You can modify a virtual wallet and add security objects to it at the same time. - Adding Security Objects to a Virtual Wallet
You can add new security objects to a virtual wallet at any time as needed. - Removing Security Objects from a Virtual Wallet
You cannot remove security objects from virtual wallets at any time as needed. - Deleting a Virtual Wallet
Deleting a virtual wallet removes the wallet as a container, but does not delete the security objects that were contained in it.
10.1.1 About Virtual Wallets
A virtual wallet is a container for security objects.
These security objects can be public and private encryption keys, including Transparent Data Encryption (TDE) keystores, Oracle wallets, Java keystores, certificates, secret data, and credential files. You can use a virtual wallet to group security objects for sharing with multiple users who need them to access encrypted data.
Any user can create a virtual wallet. After you create a virtual wallet, you can add keys and other security objects to the wallet. You can then grant other users, endpoints, user groups, and endpoint groups access to the virtual wallet at various levels of access. You can modify a virtual wallet and its wallet contents at any time. You can also modify virtual wallet user lists and their respective access level.
Other than the Key Administrator, access to the virtual wallet must be granted explicitly to users. Read, modify, and manage wallet permissions are required to add and remove objects from the wallet, and to grant or modify wallet access to other users and groups.
Parent topic: Managing Virtual Wallets
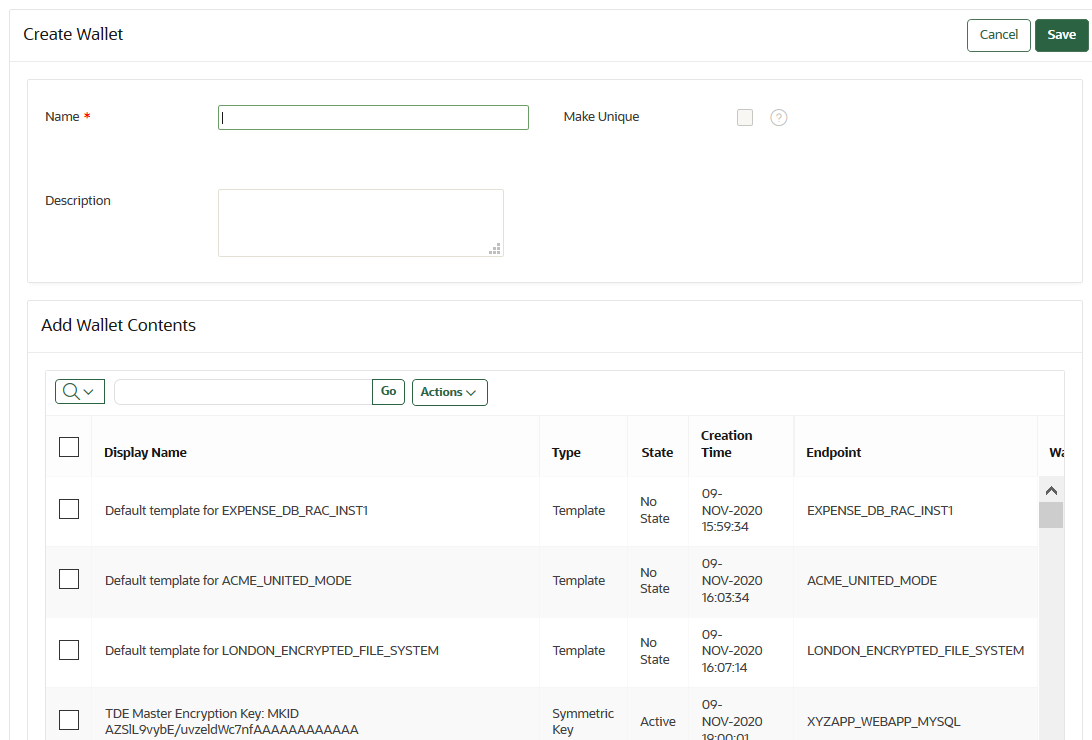
10.1.2 Creating a Virtual Wallet
You can create a virtual wallet and add security objects to it at the same time.
Related Topics
Parent topic: Managing Virtual Wallets
10.1.3 Modifying a Virtual Wallet
You can modify a virtual wallet and add security objects to it at the same time.
Related Topics
Parent topic: Managing Virtual Wallets
10.1.4 Adding Security Objects to a Virtual Wallet
You can add new security objects to a virtual wallet at any time as needed.
PENDING state.
Parent topic: Managing Virtual Wallets
10.1.5 Removing Security Objects from a Virtual Wallet
You cannot remove security objects from virtual wallets at any time as needed.
PENDING state.
Parent topic: Managing Virtual Wallets
10.1.6 Deleting a Virtual Wallet
Deleting a virtual wallet removes the wallet as a container, but does not delete the security objects that were contained in it.
PENDING state.
Parent topic: Managing Virtual Wallets
10.2 Managing Access to Virtual Wallets from Keys & Wallets Tab
You can grant virtual wallet access to and revoke virtual wallet access from endpoint by using the Keys & Wallets tab.
- About Managing Access to Virtual Wallets from the Keys & Wallets Tab
Access control is deciding which users and endpoints share virtual wallets and security objects, and what operations they can perform on those virtual wallets. - Granting Access to Users, User Groups, Endpoints, and Endpoint Groups
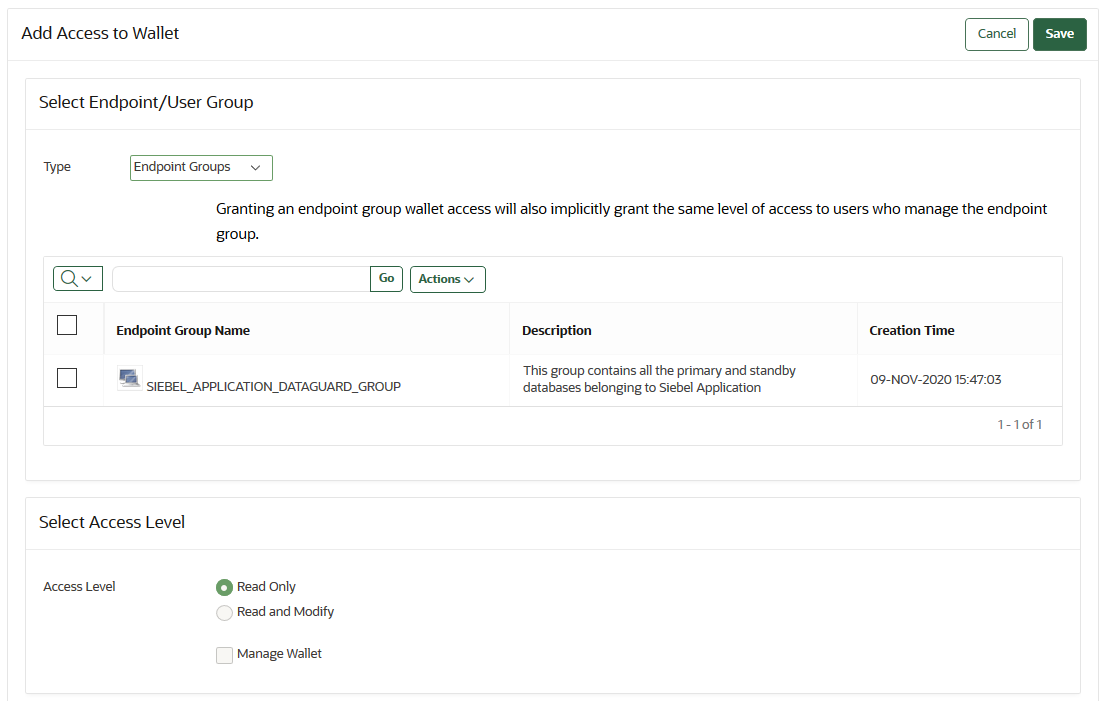
You can grant the Read Only, Read and Modify, and Manage Wallet access levels to users, user groups, endpoints, and endpoint groups. - Modifying Access to Users, User Groups, Endpoints, and Endpoint Groups
You can modify access settings on a virtual wallet for users, user groups, endpoints, and endpoint groups from the Keys & Wallets tab.
10.2.1 About Managing Access to Virtual Wallets from the Keys & Wallets Tab
Access control is deciding which users and endpoints share virtual wallets and security objects, and what operations they can perform on those virtual wallets.
You must have Manage Wallet access to a virtual wallet or be a Key Administrator to manage access control for users, endpoints, and their respective groups.
To manage access to virtual wallets, you can use the Keys & Wallets tab, where you select the wallet, you grant an endpoint, endpoint group, user, or user group access to the wallet.
Related Topics
10.2.2 Granting Access to Users, User Groups, Endpoints, and Endpoint Groups
You can grant the Read Only, Read and Modify, and Manage Wallet access levels to users, user groups, endpoints, and endpoint groups.
PENDING state.
10.2.3 Modifying Access to Users, User Groups, Endpoints, and Endpoint Groups
You can modify access settings on a virtual wallet for users, user groups, endpoints, and endpoint groups from the Keys & Wallets tab.
PENDING state.
10.3 Managing Access to Virtual Wallets from User’s Menu
To manage access control on virtual wallets for users, endpoints, and their respective groups, you can use the Users menu or Endpoints menu.
- Granting a User Access to a Virtual Wallet
You can grant access to a virtual wallet by using the Users tab. - Revoking User Access from a Virtual Wallet
You can revoke access to a virtual wallet for a user by using the Users tab. - Granting a User Group Access to a Virtual Wallet
You can grant user group access to a virtual wallet by using the Users tab. - Revoking User Group Access from a Virtual Wallet
You can remove user group access to a virtual wallet by using the Users tab.
Related Topics
10.3.1 Granting a User Access to a Virtual Wallet
You can grant access to a virtual wallet by using the Users tab.
PENDING state.
Related Topics
Parent topic: Managing Access to Virtual Wallets from User’s Menu
10.3.2 Revoking User Access from a Virtual Wallet
You can revoke access to a virtual wallet for a user by using the Users tab.
PENDING state.
Parent topic: Managing Access to Virtual Wallets from User’s Menu
10.3.3 Granting a User Group Access to a Virtual Wallet
You can grant user group access to a virtual wallet by using the Users tab.
PENDING state.
Parent topic: Managing Access to Virtual Wallets from User’s Menu
10.3.4 Revoking User Group Access from a Virtual Wallet
You can remove user group access to a virtual wallet by using the Users tab.
PENDING state.
Parent topic: Managing Access to Virtual Wallets from User’s Menu
10.4 Managing the State of a Key or a Security Object
You can set the date to activate or deactivate keys or security objects, and change the state of some virtual wallet security objects.
- About Managing the State of a Key or a Security Object
You can control the dates when a key or a security object is active, that is, when it can be used. - How a Multi-Master Cluster Affects Keys and Security Objects
Keys that you create on one node of a multi-master cluster will take some time to appear on other nodes in the cluster. - Activating a Key or Security Object
Keys can be in the Active or Pre-Active state. - Deactivating a Key or Security Object
A key deactivates or expires when it passes the date that has been set for deactivation. - Revoking a Key or Security Object
When you revoke a key, you can set its state to Deactivated or Compromised. - Destroying a Key or Security Object
When a key is no longer used or compromised in some way, then you can destroy it.
10.4.1 About Managing the State of a Key or a Security Object
You can control the dates when a key or a security object is active, that is, when it can be used.
You also can revoke and destroy keys and security objects. Be aware that a multi-master cluster affects the activation or de-activation times of keys and security objects on different nodes, and that naming conflicts can arise.
Related Topics
Parent topic: Managing the State of a Key or a Security Object
10.4.2 How a Multi-Master Cluster Affects Keys and Security Objects
Keys that you create on one node of a multi-master cluster will take some time to appear on other nodes in the cluster.
The time is defined by the replication lag between nodes. The replication lag value is displayed on the Cluster Link State pane of the Monitoring page, which can be accessed by choosing the Cluster tab.
If you add a Transparent Data Encryption (TDE) master encryption key to two different keystores on two different nodes, then it will be shown in both keystores.
Adjusting the activation date, deactivation date, process start date, and protect stop date has restrictions. For these dates, if changes are made to the security object very close to the current time, then state changes can happen because of replication lag.
As with the creation of any object in a multi-master cluster, a security object can have a name conflict with an object created on a different node. If there is a conflict, then Oracle Key Vault will suggest a unique name or allow you to rename it.
Related Topics
Parent topic: Managing the State of a Key or a Security Object
10.4.3 Activating a Key or Security Object
Keys can be in the Active or Pre-Active state.
- Log in to the Oracle Key Vault management console as a user who has read and modify access on this key.
- Select the Keys & Wallets tab, then Keys & Secrets in the left navigation bar.
- In the Keys & Secrets page, click the edit pencil icon under Edit corresponding to the item for which you want to set.
- On the Object Details page for the item, click Activate.
- Click OK to confirm.
Parent topic: Managing the State of a Key or a Security Object
10.4.4 Deactivating a Key or Security Object
A key deactivates or expires when it passes the date that has been set for deactivation.
- Log in to the Oracle Key Vault management console as a user who has read and modify access on this key.
- Select the Keys & Wallets tab, then Keys & Secrets in the left navigation bar.
- In the Keys & Secrets page, click the edit pencil icon under Edit corresponding to the item to be deactivated.
- In the Object Details page for the item, set the Date of Deactivation to the date by which you want the key to be deactivated.
- Click Save.
Parent topic: Managing the State of a Key or a Security Object
10.4.5 Revoking a Key or Security Object
When you revoke a key, you can set its state to Deactivated or Compromised.
- Log in to the Oracle Key Vault management console as a user who has read and modify access on this key.
- Select the Keys & Wallets tab, then Keys & Secrets in the left navigation bar.
- In the Keys & Secrets page, click the edit pencil icon under Edit corresponding to the item that you want to revoke.
- In the Object Details page, click Revoke.
- In the Revoke Object page, from the Revocation Reason drop-down list, select a reason for the revocation.
- Optionally, add more details in Revocation Message
- Click Save.
Parent topic: Managing the State of a Key or a Security Object
10.4.6 Destroying a Key or Security Object
When a key is no longer used or compromised in some way, then you can destroy it.
- Log in to the Oracle Key Vault management console as a user who has read and modify access on this key.
- Select the Keys & Wallets tab, then Keys & Secrets in the left navigation bar.
- In the Keys & Secrets page, click the edit pencil icon under Edit corresponding to the item that you want to destroy.
- On the Object Details page, click Destroy.
- In the confirmation window, click OK.
Parent topic: Managing the State of a Key or a Security Object
10.5 Managing the Extraction of Symmetric Keys from Oracle Key Vault
You can restrict symmetric keys from leaving Oracle Key Vault.
- About Managing the Extraction of Symmetric Keys from Oracle Key Vault
The ability to restrict symmetric keys (extraction) from leaving Oracle Key Vault ensures a higher level of security for these objects. - Configuring the Extractable Attribute Value of Existing Symmetric Keys
You can configure the extractable attribute value of existing symmetric keys.
10.5.1 About Managing the Extraction of Symmetric Keys from Oracle Key Vault
The ability to restrict symmetric keys (extraction) from leaving Oracle Key Vault ensures a higher level of security for these objects.
Many operations that use symmetric keys perform these operations outside of Oracle Key Vault and by default, symmetric keys within Oracle Key Vault can be extracted for this purpose. Consider the example with Transparent Database Encryption (TDE) master encryption keys that are stored in Oracle Key Vault. When an Oracle Database endpoint needs to decrypt the data encryption key, the PKCS#11 library fetches the TDE master encryption key from Oracle Key Vault to perform the decryption. If your site requires that symmetric keys never leave Oracle Key Vault, then you can configure the symmetric keys to remain within Oracle Key Vault by setting their extractable attribute value to false. Setting the extractable attribute value to false prevents the key material of the symmetric key from being extracted from Oracle Key Vault, but still allows other object metadata (including object attributes, state, and so on) to be retrieved from Oracle Key Vault. If the TDS master encryption key is restricted from leaving Oracle Key Vault, the PKCS#11 library sends a request to Oracle Key Vault to decrypt the encrypted data encryption key. Decryption is then performed within Oracle Key Vault and afterward, the plaintext data encryption key is returned to the PKCS#11 library. To allow a symmetric key to leave Oracle Key Vault, you would set its extractable attribute value to true.
You can set the extractable attribute of symmetric keys in the following ways:
- Setting the extractable attribute value for an existing symmetric key: A user who has the Key Administrator role can modify the extractable attribute value of an existing symmetric key to be either true or false. A user or an endpoint with read-write access on an existing symmetric key can also modify its extractable attribute setting. However, this is allowed only to apply the stricter setting (that is, to set the value to false to make the symmetric key non-extractable). Such users or endpoints cannot modify the extractable attribute setting to make a symmetric key extractable if it is currently non-extractable.
- Setting the default value of the extractable attribute globally for all
endpoints: You can set the default value of the extractable attribute in the
global endpoint settings. This setting applies to all endpoints. This setting is
used when an endpoint creates or registers a new symmetric key unless either of the
following conditions occur:
- The extractable attribute is set for the symmetric key at the time of its creation or registration.
- The default extractable attribute value has been set for that endpoint specifically (that is, the endpoint does not inherit this setting from the global endpoint).
This global endpoint setting does not apply to existing symmetric keys; it only applies to new symmetric keys that are created or registered after this setting has been configured.
- Setting the default value of the extractable attribute for an individual
endpoint: You can set the default value of the extractable attribute for an
individual endpoint. The endpoint specific setting takes precedence over the global
endpoint setting. This endpoint specific extractable attribute setting applies when
the endpoint creates or registers a new symmetric key unless the extractable
attribute is set for the symmetric key at the time of its creation or registration
itself.
This individual endpoint setting does not apply to existing symmetric keys; it only applies to new symmetric keys that are created or registered by the endpoint after this setting has been configured.
- Setting the extractable attribute value when you create or register a symmetric key: You can set the extractable attribute value for a new symmetric key at the time of its creation or registration using the C SDK, the Java SDK, or the RESTful services utility. The extractable attribute value specified at the time of key creation takes precedence over the endpoint’s effective setting for the extractable attribute. However, this is subject to an additional restriction: You cannot set the extractable attribute of a new symmetric key to true, that is, create the new key as extractable, if the endpoint’s effective setting for the extractable attribute is set to false (that is, the new symmetric keys are not extractable).
Be aware that setting the extractable attribute value to false may affect the performance of Oracle Key Vault. The performance impact may not be limited to Oracle Key Vault. The endpoint performance may be impacted as well.
Related Topics
10.6 Managing Details of Security Objects
You can manage details about security objects, such as find details about these objects and modifying these details.
- About Managing the Details of Security Objects
You can search for security objects within a virtual wallet, and add, modify, or remove these security objects. - Searching for Security Object Items
You can search for individual security objects if you have privileges to view these objects. - Viewing the Details of a Security Object
An administrative user with the Key Administrator role can view, add, and modify the details of a security object. - Adding or Modifying Details of a Security Object
Only users who have the appropriate privileges can add or modify the details of a security object.
10.6.1 About Managing the Details of Security Objects
You can search for security objects within a virtual wallet, and add, modify, or remove these security objects.
Security objects are managed by Oracle Key Vault administrative users with a clear separation of duties. You must be an administrative user with the Key Administrator role to manage wallet privilege on the virtual wallet containing the security objects. A user with the Audit Manager role can view security objects, but cannot modify them, whereas individual security objects are not even viewable to a user with the System Administrator role.
You can set the deactivation date for security objects and have an alert notify you when the security object will expire. For example, if you configure an alert for an object expiration with a threshold of 7 days, its expiration alert will be raised when object’s deactivation date is within the 7 days of its deactivation date. An email notification will be sent every 24 hours during this threshold period. The alert is raised only when the security object is in the PRE-ACTIVE or ACTIVE state. Oracle Key Vault deletes the expiration alerts for the security objects when the security object is revoked or destroyed.
Related Topics
Parent topic: Managing Details of Security Objects
10.6.2 Searching for Security Object Items
You can search for individual security objects if you have privileges to view these objects.
Parent topic: Managing Details of Security Objects
10.6.3 Viewing the Details of a Security Object
An administrative user with the Key Administrator role can view, add, and modify the details of a security object.
The administrative user can perform these actions on the security object from its corresponding Object Details page. Object details are attributes of a specific security object and depend on the type of security object.
-
Log in to the Oracle Key Vault management console as a user with the Key Administrator role or as a user with access to the virtual wallet.
-
Select the Keys & Wallets tab, then Keys & Secrets in the left navigation bar.
-
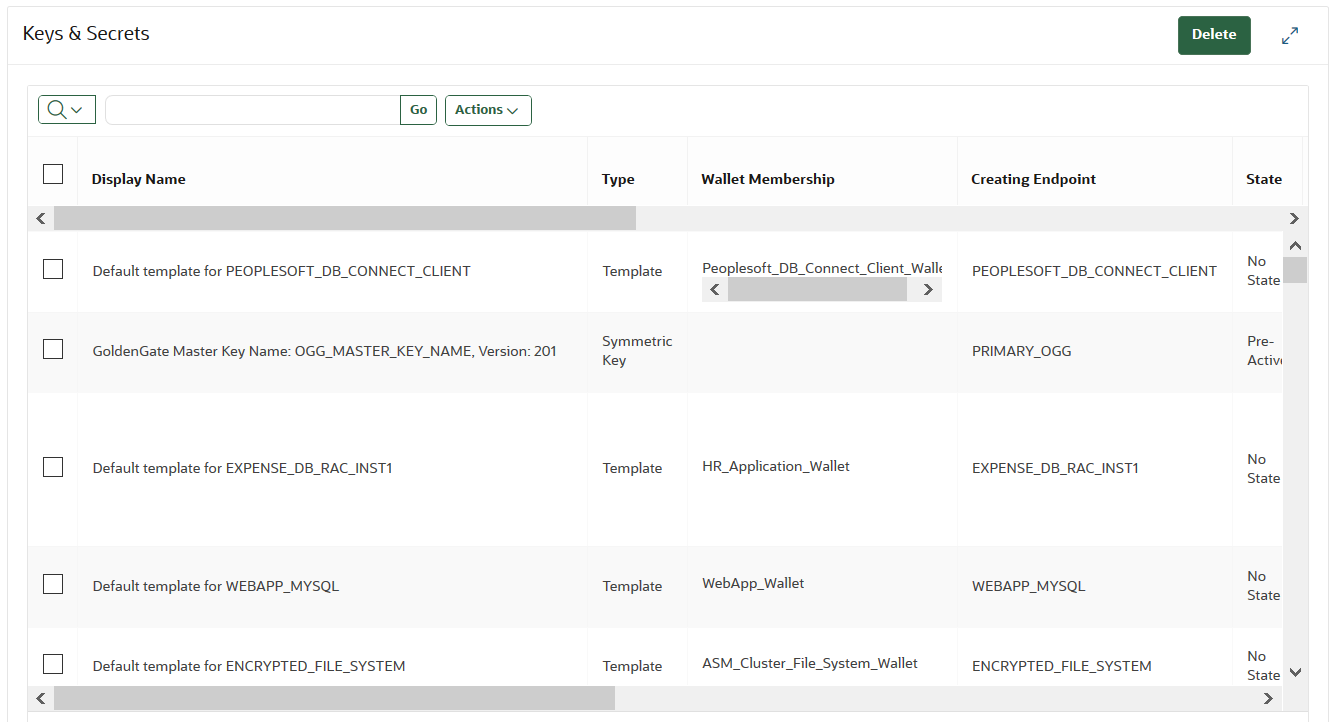
In the Keys & Secrets page, search for the security object that you want.
The Keys & Secrets page shows a table that displays the security objects in Key Vault.
You can modify the columns in this table to show more information. From the Actions menu, select Select Columns. In the Select Columns dialog box, move the columns that you want to see to the Display in Report list, and then click Apply.
-
Click the pencil icon in the Edit column corresponding to the security object.
The Object Details page appears displaying the attributes of the security object. The following screen shows a partial view of all the activities that you can perform on this object.
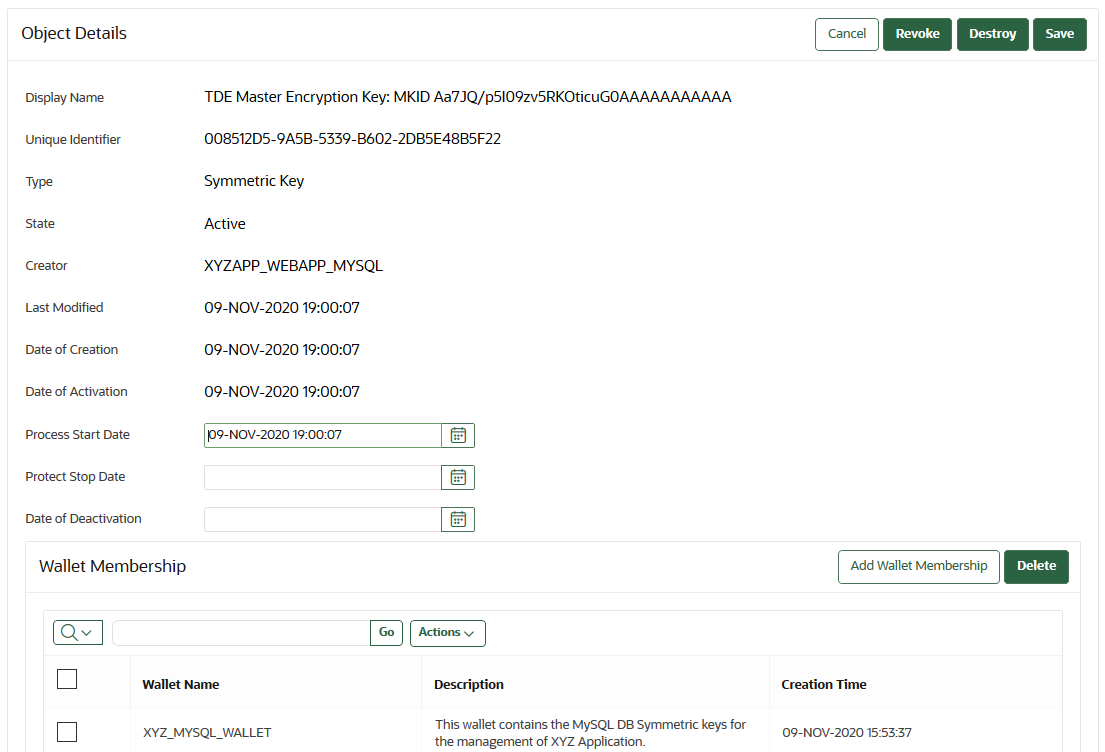
Description of the illustration 21_object_details.pngYou can set the dates when the security object should be deactivated or not used on the Object Details page. The attributes shown in Object Details depend on the type of security object. The attributes for a Symmetric Key are different from those of Private Key or Opaque Object.
You can revoke or destroy a security object, and add or remove it to and from a wallet from the Object Details page.
The Wallet Membership pane in the Object Details page enables you to add the security object to a wallet or delete the security object from a wallet.
The Object Details page contains the following attributes:
-
Display Name: A summary description to help identify the item to the user. For example, if the item is a TDE master encryption key, then the Identifier shows the prefix TDE master encryption key followed by the identifier used by the database to identify the key.
-
Unique Identifier: This is a globally unique ID that identifies an item.
-
Type: Indicates the object type of the item. Valid values are Symmetric Key, Public Key, Private Key, Template, Opaque Object, Certificate, and Secret Data.
-
State: Indicates the status of the security objects. Values are as follows:
-
Pre-active: The object exists but is not yet usable for any cryptographic purpose.
-
Active: The object is available for use. Endpoints should examine the Cryptographic Usage Mask attribute to determine which uses are appropriate for this object.
-
Deactivated: The object is no longer active and should not be used to apply cryptographic protection (for example, encryption or signing). It may still be appropriate to use for decrypting or verifying previously protected data.
-
Compromised: The object is believed to be compromised and should not be used.
-
Destroyed: The object is no longer usable for any purpose.
-
Destroyed Compromised: The object was compromised and destroyed. It is no longer usable for any purpose.
-
-
Creator: The endpoint that created the security object.
-
Last Modified: The date last modified.
-
Date of Creation: The date created.
-
Date of Activation: The date of activation.
-
Process Start Date: The date when the key may start to be used to encrypt data. It can be equal or later than the Date of Activation setting but cannot precede it.
-
Protect Stop Date: When this date is passed, the key should not be used to encrypt any more data. It cannot be later than the Date of Deactivation setting.
-
Date of Deactivation: The date of deactivation.
-
-
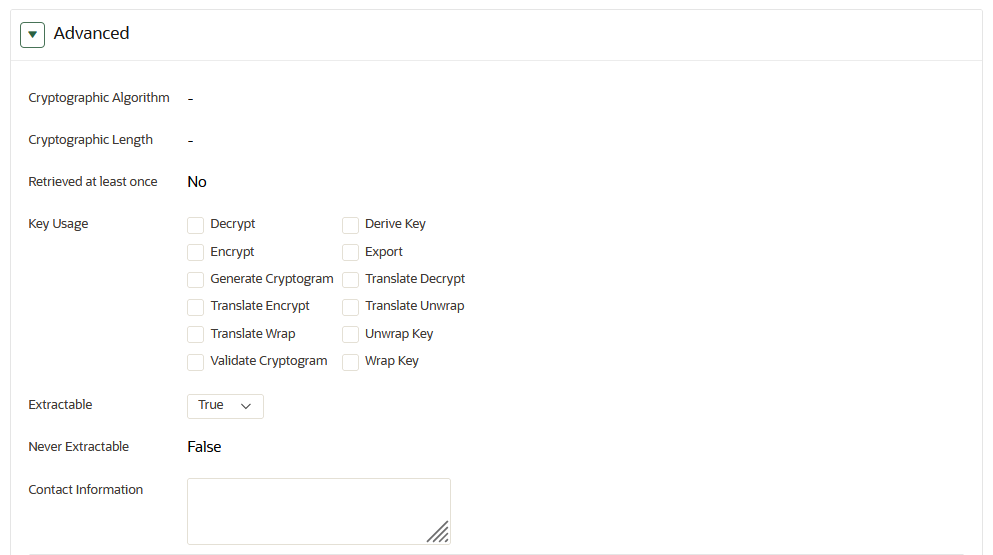
Click Advanced to view the attributes of the security object.
Attribute information and queries will vary depending on the item type. Examples of attributes are as follows:
-
Cryptographic Algorithms: The encryption algorithm used by the item
-
Key Usage: Operations that the key can be used for. Clients may or may not use these attributes. For example, Transparent Data Encryption does not consult the key usage attributes.
-
Extractable: Indicates if the symmetric key security object can be extracted. TRUE means that it can be extracted; FALSE means that it cannot be extracted.
-
Never Extractable: Indicates if a security object (in this case, symmetric keys only) was never allowed to be extracted from Oracle Key Vault. TRUE means that the extractable attribute of the symmetric key has always been set to FALSE. If the Extractable attribute was ever (even once) set to TRUE, then the Never Extractable attribute becomes (and remains set to) FALSE.
-
Names: Labels attached by a user or endpoint to identify the key
-
Custom Attributes: Additional attributes defined by the endpoint and not interpreted by Oracle Key Vault
-
Cryptographic Parameters: Optional parameters for the encryption algorithm used by the item, such as block cipher mode and padding method
-
Cryptographic Length: The length in bits of the key
-
Retrieved at Least Once: Indicates if the object has been served to the client
-
Contact Information: Used for contact purposes only
-
Digests: Digest values of the security object
-
Link Details: Links to related objects
-
Parent topic: Managing Details of Security Objects
10.6.4 Adding or Modifying Details of a Security Object
Only users who have the appropriate privileges can add or modify the details of a security object.
Parent topic: Managing Details of Security Objects