5 Creating an Oracle Label Security Policy
An Oracle Label Security policy is a named set of commands that implements Oracle Label Security.
- About Creating Oracle Label Security Policies
An Oracle Label Security policy enforces user access to data based on labels. - Privileges for Managing Oracle Label Security Policies
When a user creates an Oracle Label Security policy container, Oracle Label Security creates and grants this user an administrative role that is specific to the policy, named in the format ofpolicy_DBA. - Step 1: Create the Label Security Policy Container
The Oracle Label Security policy container is a storage place for the policy settings. - Step 2: Create Labels for the Label Security Policy
After you create a policy container, you are ready to create data labels to be used by each row in the protected table(s).. - Step 3: Authorize Users for the Label Security Policy
Before users can have access to data that is protected by an Oracle Label Security policy, they must be authorized. - Step 4: Grant Privileges to Users and Trusted Stored Program Units
Oracle Label Security supports special privileges that allow authorized users to bypass certainparts of the policy - Step 5: Apply the Policy to a Database Table or Schema
After you create grant authorizations and privileges to an Oracle Label Security policy, you can apply it to a database table or schema. - Step 6: Add Policy Data Labels to Table Rows
You must add policy data labels to table rows. - Step 7: Optionally, Configure Auditing
For Oracle Label Security policies, if you want to enable auditing, then you must create a unified audit policy. - Using Oracle Label Security Policies and Oracle Flashback Data Archive
Oracle Label Security policies do not automatically work with Oracle Flashback Data Archive (FDA). - Using Enterprise Manager Cloud Control to Create an OLS Policy
You can create Oracle Label Security policies in Oracle Enterprise Manager Cloud Control. However, you cannot create audit policies using Cloud Control; you must use SQL*Plus to create unified audit policies.
Parent topic: Using Oracle Label Security Functionality
5.1 About Creating Oracle Label Security Policies
An Oracle Label Security policy enforces user access to data based on labels.
-
Create a policy container that defines the policy name, the name of a column that Oracle Label Security will add to the tables to be protected, whether to hide this column, whether to enable the policy, and default enforcement options for the policy.
See Step 1: Create the Label Security Policy Container for more information.
-
Define the following components for the label: level of sensitivity, and optionally, compartments and groups to further filter the label sensitivity. Once you have the components defined, create the label itself and then associate these components with the label.
-
Authorize users for the policy.
See Step 3: Authorize Users for the Label Security Policy for more information.
-
Grant privileges to these users or to trusted program units.
See Step 4: Grant Privileges to Users and Trusted Stored Program Units for more information.
-
Apply the policy to a database table. Alternatively, you can apply the policy to an entire schema.
See Step 5: Apply the Policy to a Database Table or Schema for more information.
-
Add the policy labels to the table rows. You must update the table that is being used for the policy.
See Step 6: Add Policy Data Labels to Table Rows for more information.
-
Optionally, configure audit settings for users.
See Step 7: Optionally, Configure Auditing for more information.
Parent topic: Creating an Oracle Label Security Policy
5.2 Privileges for Managing Oracle Label Security Policies
When a user creates an Oracle Label Security policy container, Oracle Label
Security creates and grants this user an administrative role that is specific to the policy,
named in the format of policy_DBA.
For example, for a policy named emp_ols_pol, the role name is EMP_OLS_POL_DBA. This role becomes effective only after a new user session begins.
To enable the user to manage the policy, Oracle Label Security performs these checks in the following order:
- Checks if the user is granted the
policy_DBArole. - Checks if the
policy_DBAis enabled for this user. - In the event of a nested call stack, checks if the top definer's rights procedure owner has been granted the
policy_DBArole. - Checks if the
policy_DBArole is granted to theLBACSYSuser, which is the current user.
Parent topic: Creating an Oracle Label Security Policy
5.3 Step 1: Create the Label Security Policy Container
The Oracle Label Security policy container is a storage place for the policy settings.
- About the Label Security Policy Container
The Oracle Label Security policy container stores metadata that describes how the policy behaves. - Creating a Label Policy Container
You can use theSA_SYSDBA.CREATE_POLICYprocedure to create an Oracle Label Security policy container.
Parent topic: Creating an Oracle Label Security Policy
5.3.1 About the Label Security Policy Container
The Oracle Label Security policy container stores metadata that describes how the policy behaves.
This container defines the policy name, the name of a column that Oracle Label Security will add to the tables to be protected, whether to hide this column, and default enforcement options for the policy.
The column that you add to the tables that you want to protect will include data labels (which you create later on) that are assigned to specific rows in a the table, based on values in a specific column or other attributes.
You can create the policy container in Oracle Enterprise Manager Cloud Control, or use the SA_SYSDBA.CREATE_POLICY procedure.
Parent topic: Step 1: Create the Label Security Policy Container
5.3.2 Creating a Label Policy Container
You can use the SA_SYSDBA.CREATE_POLICY procedure to create an Oracle Label Security policy container.
-
To create the policy, run
SA_SYSDBA.CREATE_POLICY, specifying the policy name, column name, and default options.
For example:
BEGIN SA_SYSDBA.CREATE_POLICY ( policy_name => 'emp_ols_pol', column_name => 'ols_col', default_options => 'read_control, update_control'); END; /
Related Topics
Parent topic: Step 1: Create the Label Security Policy Container
5.4 Step 2: Create Labels for the Label Security Policy
After you create a policy container, you are ready to create data labels to be used by each row in the protected table(s)..
- About Labels
A label indicates the sensitivity associated with a data record or user. - About Policy Level Sensitivity Components
A level is a ranking that denotes the sensitivity of the information it labels. - Creating a Policy Level Component
TheSA_COMPONENTS.CREATE_LEVELprocedure creates a policy level component. - About Policy Compartment Components
Compartments identify areas that describe the sensitivity of the labeled data, providing a finer level of granularity within a level. - Creating a Policy Compartment Component
TheSA_COMPONENTS.CREATE_COMPARTMENTprocedure creates an Oracle Label Security compartment. - About Policy Group Components
Groups can identify organizations, regions, or other organizing structures that are allowed to access the data, such asEASTERN_REGION,WESTERN_REGION,WR_SALES. - Creating a Policy Label Group
TheSA_COMPONENTS.CREATE_GROUPprocedure creates a label group. - About Associating the Policy Components with a Named Data Label
After defining the label components, you can create a data label itself by associating it with an existing policy. - Associating the Policy Components with a Named Data Label
TheSA_LABEL_ADMIN.CREATE_LABELprocedure creates a data label.
Parent topic: Creating an Oracle Label Security Policy
5.4.1 About Labels
A label indicates the sensitivity associated with a data record or user.
Each label is a single attribute with multiple components that control the types of filtering to be used for user access.
Table 5-1 describes the different components of a label.
Table 5-1 Label Components
| Component | Description | Examples |
|---|---|---|
|
Level |
Required - at least one level must be defined An ordered rank of names indicating sensitivity. |
|
|
Compartments |
Used to provide a finer level of granularity to the sensitivity level and can represent projects or other sensitive topics. Zero or more compartments can be associated with a label. |
|
|
Groups |
Represent organizations, regions, or other attributes. Zero or more groups can be associated with a label. |
|
All labels must contain a level component, but the compartment and group components are optional. Compartments and groups are a way of fine tuning access that users will have to the data. Valid characters for specifying all label components include alphanumeric characters, underscores, and spaces. (Leading and trailing spaces are ignored.) You must define the label components before you can create data labels.
You can use Enterprise Manager Cloud Control to create the label and its components
for an existing policy. Alternatively, you can use the SA_COMPONENTS
PL/SQL package to create the components, and the SA_LABEL_ADMIN package
to create the data label.
Related Topics
Parent topic: Step 2: Create Labels for the Label Security Policy
5.4.2 About Policy Level Sensitivity Components
A level is a ranking that denotes the sensitivity of the information it labels.
The more sensitive the information, the higher its level. The less sensitive the information, the lower its level.
Every label must include one level. Oracle Label Security permits up to 10,000 levels in a policy. For each level, you must define a numeric form, a long character form, and the required short character form.
Table 5-2 shows examples of levels.
Table 5-2 Policy Level Example
| Numeric Form | Long Form | Short Form |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 5-2 explains the numeric form, long form, and short form for levels.
Table 5-3 Forms of Specifying Levels
| Form | Explanation |
|---|---|
|
Numeric form, also called "tag" |
The numeric form of the level can range from 0 to 9999. Sensitivity is ranked by this numeric value, so you must assign higher numbers to levels that are more sensitive, and lower numbers to levels that are less sensitive. In Table 5-2, 40 ( Administrators should avoid using sequential numbers for the numeric form of levels. A good strategy is to space out the numbers between levels (such as 10, 20, 30... or 100, 200, 300...). You can then insert additional levels between two preexisting levels, at a later date. |
|
Long form |
The long form of the level name can contain up to 80 characters. |
|
Short form |
The short form can contain up to 30 characters. |
Although you define both long and short names for the level (and for each of the other label components), only the short form of the name is displayed upon retrieval. When users manipulate the labels, they use only the short form of the component names.
Examples of levels can be names such as TOP_SECRET, SECRET, CONFIDENTIAL, and UNCLASSIFIED or TRADE_SECRET, PROPRIETARY, COMPANY_CONFIDENTIAL, PUBLIC_DOMAIN.
If you use only levels, a level 40 user (in this example) can access or alter any data row whose level is 40 or less.
Parent topic: Step 2: Create Labels for the Label Security Policy
5.4.3 Creating a Policy Level Component
The SA_COMPONENTS.CREATE_LEVEL procedure creates a policy level component.
Related Topics
Parent topic: Step 2: Create Labels for the Label Security Policy
5.4.4 About Policy Compartment Components
Compartments identify areas that describe the sensitivity of the labeled data, providing a finer level of granularity within a level.
All data related to a particular project can be labeled with the same compartment.
For example, a user with level HS that has access to compartments
FINCL and CHEM would not be allowed access to any
data that includes the OP compartment.
Table 5-4 shows an example set of compartments.
Table 5-4 Policy Compartment Example
| Numeric Form | Long Form | Short Form |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
Table 5-5 shows different ways to specify compartments.
Table 5-5 Forms of Specifying Compartments
| Form | Explanation |
|---|---|
|
Numeric form |
The numeric form can range from 0 to 9999. It is unrelated to the numbers used for the levels. The numeric form of the compartment does not indicate greater or less sensitivity. Instead, it controls the display order of the short form compartment name in the label character string. For example, assume a label is created that has all three compartments listed in Table 5-4, and a level of S:OP,CHEM,FINCL meaning The display order follows the order of the numbers assigned to the compartments: 45 is lower than 65, and 65 is lower than 85. By contrast, if the number assigned to the S:FINCL,OP,CHEM |
|
Long form |
The long form of the compartment name scan have up to 80 characters. |
|
Short form |
The short form can contain up to 30 characters. |
Compartments are optional. You can include up to 10,000 compartments for a label.
Not all labels must have compartments. For example, you can specify HIGHLY_SENSITIVE and CONFIDENTIAL levels with no compartments, and a SENSITIVE level that does contain compartments.
When you analyze the sensitivity of data, you may find that some compartments are only useful at specific levels.
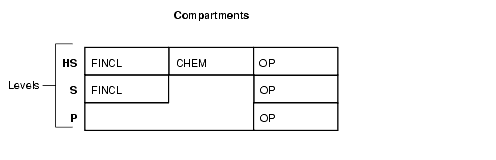
The following figure shows how compartments can be used to categorize data.
Here, compartments FINCL, CHEM, and OP are used with the level HIGHLY_SENSITIVE (HS). The label HIGHLY_SENSITIVE:FINCL, CHEM indicates a level of 40 with the two named compartments. Compartment FINCL is not more sensitive than CHEM, nor is CHEM more sensitive than FINCL. Note also that some data in the protected table may not belong to any compartment.
If you specify compartments, then a user whose level would normally permit access to a row's data will nevertheless be prevented from such access unless the user's label also contains all the compartments appearing in that row's label. For example, user hpreston, who is granted access to the HS level, could be granted access only to FINCL and CHEM but not to OP.
Parent topic: Step 2: Create Labels for the Label Security Policy
5.4.5 Creating a Policy Compartment Component
The SA_COMPONENTS.CREATE_COMPARTMENT procedure creates an Oracle Label Security compartment.
Related Topics
Parent topic: Step 2: Create Labels for the Label Security Policy
5.4.6 About Policy Group Components
Groups can identify organizations, regions, or other organizing structures
that are allowed to access the data, such as EASTERN_REGION,
WESTERN_REGION, WR_SALES.
All data pertaining to a certain department can have that department's group name in the label. Groups are useful for the controlled dissemination of data and for timely reaction to organizational change. When a company reorganizes, data access can change right along with the reorganization.
Groups can be hierarchical. You can label data based upon your organizational infrastructure. A group can thus be associated with a parent group.
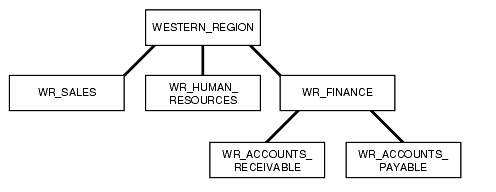
Figure 5-2 shows how you can define a set of groups corresponding to the following organizational hierarchy.
The WESTERN_REGION group includes three subgroups: WR_SALES, WR_HUMAN_RESOURCES, and WR_FINANCE. The WR_FINANCE subgroup is subdivided into WR_ACCOUNTS_RECEIVABLE and WR_ACCOUNTS_PAYABLE.
Table 5-6 shows how the organizational structure in this example can be expressed in the form of Oracle Label Security groups. The numeric form assigned to the groups affects display order only. You specify the hierarchy (that is, the parent and child relationships) separately. The first group listed, WESTERN_REGION, is the parent group of the remaining groups in the table.
Table 5-6 Group Example
| Numeric Form | Long Form | Short Form | Parent Group |
|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 5-7 shows the forms that you must use when you specify groups.
Table 5-7 Forms of Specifying Groups
| Form | Explanation |
|---|---|
|
Numeric form |
The numeric form of the group can range from 0 to 9999, and it must be unique for each policy. The numeric form does not indicate any kind of ranking. It does not indicate a parent-child relationship, or greater or less sensitivity. It only controls the display order of the short form group name in the label character string. For example, assume that a label is created that has the level S:CHEM:WR,WR_HR
|
|
Long form |
The long form of the group name can contain up to 80 characters. |
|
Short form |
The short form can contain up to 30 characters. |
Groups are optional. A label can contain up to 10,000 groups.
All labels do not need to have groups. When you analyze the sensitivity of data, you may find that some groups are only used at specific levels. For example, you can specify HIGHLY_SENSITIVE and CONFIDENTIAL labels with no groups, and a SENSITIVE label that does contain groups.
Parent topic: Step 2: Create Labels for the Label Security Policy
5.4.7 Creating a Policy Label Group
The SA_COMPONENTS.CREATE_GROUP procedure creates a label
group.
Related Topics
Parent topic: Step 2: Create Labels for the Label Security Policy
5.4.8 About Associating the Policy Components with a Named Data Label
After defining the label components, you can create a data label itself by associating it with an existing policy.
Optionally, you can include compartments and groups in this association.
You can use Oracle Enterprise Manager Cloud Control or the SA_LABEL_ADMIN.CREATE_LABEL procedure. Character string representations of labels use the following syntax:
level:compartment1,...,compartmentn:group1,...,groupn
The text string that specifies the label can have a maximum of 4,000 characters, including alphanumeric characters, spaces, and underscores. The label names are case-insensitive. You can enter them in uppercase, lowercase, or mixed case, but the string is stored in the data dictionary and displayed in uppercase. Separate each set of components with a colon. You do not need to enter trailing delimiters in this syntax.
For example, you can create valid labels such as these:
SENSITIVE:FINANCIAL,CHEMICAL:EASTERN_REGION,WESTERN_REGION CONFIDENTIAL:FINANCIAL:VP_GRP SENSITIVE HIGHLY_SENSITIVE:FINANCIAL SENSITIVE::WESTERN_REGION
Parent topic: Step 2: Create Labels for the Label Security Policy
5.4.9 Associating the Policy Components with a Named Data Label
The SA_LABEL_ADMIN.CREATE_LABEL procedure creates a data label.
Related Topics
Parent topic: Step 2: Create Labels for the Label Security Policy
5.5 Step 3: Authorize Users for the Label Security Policy
Before users can have access to data that is protected by an Oracle Label Security policy, they must be authorized.
- About Authorizing Users for Label Security Policies
When you authorize users, you enable them to have access to row data based on the row data label. - About Authorizing Levels
You can explicitly set default, minimum, and maximum authorization levels. - Authorizing a Level
TheSA_USER_ADMIN.SET_LEVELSprocedure authorizes users for policy levels components. - About Authorizing Compartments
After you authorize the user for a specific level, you can optionally specify compartments authorized for the user. - Authorizing a Compartment
TheSA_USER_ADMIN.SET_COMPARTMENTSprocedure authorizes a user for the compartments component. - About Authorizing Groups
You can specify the list of groups that the user is authorized to be associated with. - Authorizing a Group
TheSA_USER_ADMIN.SET_GROUPSprocedure authorizes users for a policy group.
Parent topic: Creating an Oracle Label Security Policy
5.5.1 About Authorizing Users for Label Security Policies
When you authorize users, you enable them to have access to row data based on the row data label.
You set the user's authorization by setting their level, zero or more compartments,
and zero or more groups as their user label. You can find the currently granted
privileges for a user by querying the DBA_SA_USER_PRIVS data dictionary
view.
Parent topic: Step 3: Authorize Users for the Label Security Policy
5.5.2 About Authorizing Levels
You can explicitly set default, minimum, and maximum authorization levels.
Table 5-8 Authorized Levels Set by the Administrator
| Authorization | Meaning |
|---|---|
|
User Max Level |
The maximum ranking of sensitivity that a user can access during read and write operations |
|
User Min Level |
The minimum ranking of sensitivity that a user can access during write operations. The User Max Level must be equal to or greater than the User Min Level. |
|
User Default Level |
The level that is assumed by default when connecting to Oracle Database |
|
User Default Row Level |
The level that is used by default when inserting data into Oracle Database |
For example, you might set the following level authorizations for user hpreston:
| Type | Short Name | Long Name | Description |
|---|---|---|---|
|
Maximum |
|
|
User's highest level |
|
Minimum |
|
|
User's lowest level |
|
Default |
|
|
User's default level |
|
Row |
|
|
Row level on |
Parent topic: Step 3: Authorize Users for the Label Security Policy
5.5.3 Authorizing a Level
The SA_USER_ADMIN.SET_LEVELS procedure authorizes users for policy levels components.
Related Topics
Parent topic: Step 3: Authorize Users for the Label Security Policy
5.5.4 About Authorizing Compartments
After you authorize the user for a specific level, you can optionally specify compartments authorized for the user.
Write access must be explicitly given for each compartment. A user cannot directly insert, update, or delete a row that contains a compartment that the user does not have authorization to write.
For example, you could set the following compartment authorizations for user hpreston:
| Short Name | Long Name | WRITE | DEFAULT | ROW |
|---|---|---|---|---|
|
|
|
YES |
YES |
NO |
|
|
|
YES |
YES |
NO |
|
|
|
YES |
YES |
YES |
Parent topic: Step 3: Authorize Users for the Label Security Policy
5.5.5 Authorizing a Compartment
The SA_USER_ADMIN.SET_COMPARTMENTS procedure authorizes a user for the compartments component.
SA_USER_ADMIN.ADD_COMPARTMENTS procedure.
Related Topics
Parent topic: Step 3: Authorize Users for the Label Security Policy
5.5.6 About Authorizing Groups
You can specify the list of groups that the user is authorized to be associated with.
Write access must be explicitly given for each group listed.
For example, you could set the following group authorizations:
| Short Name | Long Name | WRITE | DEFAULT | ROW | Parent |
|---|---|---|---|---|---|
|
|
|
YES |
YES |
YES |
|
|
|
|
YES |
YES |
NO |
|
|
|
|
YES |
YES |
NO |
|
Defining group parent associations is done as part of the group definition.
Parent topic: Step 3: Authorize Users for the Label Security Policy
5.5.7 Authorizing a Group
The SA_USER_ADMIN.SET_GROUPS procedure authorizes users for a policy group.
SA_USER_ADMIN.ADD_GROUPS procedure.
Related Topics
Parent topic: Step 3: Authorize Users for the Label Security Policy
5.6 Step 4: Grant Privileges to Users and Trusted Stored Program Units
Oracle Label Security supports special privileges that allow authorized users to bypass certainparts of the policy
- About Granting Privileges to Users and Trusted Program Units for the Policy
Certain authorized users and trusted program units may need special privileges to bypass parts of the OLS policy. - Granting Privileges to a User
TheSA_USER_ADMIN.SET_USER_PRIVSprocedure grants users privileges. - Granting Privileges to a Trusted Program Unit
TheSA_USER_ADMIN.SET_PROG_PRIVSprocedure grants privileges to trusted program units.
Parent topic: Creating an Oracle Label Security Policy
5.6.1 About Granting Privileges to Users and Trusted Program Units for the Policy
Certain authorized users and trusted program units may need special privileges to bypass parts of the OLS policy.
Trusted program units are functions, procedures, or packages that are granted Oracle Label Security privileges. You create a trusted stored program unit in the same way that you create a standard procedure, function, or package, that is by using the CREATE PROCEDURE, CREATE FUNCTION, or CREATE PACKAGE and CREATE PACKAGE BODY statements. The program unit becomes trusted when you grant Oracle Label Security privileges to it.
Table 5-9 summarizes the special privileges that can be granted to users or trusted stored program units.
Table 5-9 Oracle Label Security Privileges
| Security Privilege | Explanation |
|---|---|
|
|
Allows read access to all data protected by the policy |
|
|
Allows full read and write access to all data protected by the policy |
|
|
Bypasses the group component check if the session label level and compartment(s) dominate the data level and compartments |
|
|
Allows a session to change its labels and privileges to those of a different user |
|
|
Allows users to set or raise only the level, within a row label, up to the maximum level authorized for the user. (Active only if |
|
|
Allows users to set or lower the level, within a row label, to any level equal to or greater than the minimum level authorized for the user. (Active only if |
|
|
Allows a user to set or change groups and compartments of a row label, but does not allow changes to the level. (Active only if |
5.6.2 Granting Privileges to a User
The SA_USER_ADMIN.SET_USER_PRIVS procedure grants users privileges.
Related Topics
5.7 Step 5: Apply the Policy to a Database Table or Schema
After you create grant authorizations and privileges to an Oracle Label Security policy, you can apply it to a database table or schema.
- About Applying the Policy to a Database Table or Schema
When you apply a policy to a table, the policy is automatically enabled. - Applying a Policy to a Schema
TheSA_POLICY_ADMIN.APPLY_TABLE_POLICYapplies a policy to a table within a schema and theSA_POLICY_ADMIN.APPLY_SCHEMA_POLICYprocedure applies a policy to an entire schema.
Parent topic: Creating an Oracle Label Security Policy
5.7.1 About Applying the Policy to a Database Table or Schema
When you apply a policy to a table, the policy is automatically enabled.
To disable a policy is to turn off its protections, although it is still applied to the table. To enable a policy is to turn on and enforce its protections for a particular table or schema.
To remove a policy is to take it entirely away from the table or schema. Note, however, that the policy label column and the labels remain in the table unless you explicitly drop them.
You can alter the default policy enforcement options for future tables that may be created in a schema. This does not, however, affect policy enforcement options on existing tables in the schema.
To change the enforcement options on an existing table, you must first remove the policy from the table, make the desired changes, and then reapply the policy to the table.
In cases where a master-detail table relationship exists with primary and foreign keys, only one of the tables needs to be protected by an OLS policy. The other table will also be protected based on the key relationship.
Be aware that you cannot enforce Oracle Label Security policies on external tables.
After you have created the policy components and configured user authorizations, privileges, and auditing for them, you can apply the policy to a database table or to an entire schema.
When you apply the policy to a database table, in addition to the policy name and target schema table, you must specify the following information:
-
table_options: A comma-delimited list of policy enforcement options to be used for the table. IfNULL, then the policy's default options are used. -
label_function: A string calling a function to return a label value to use as the default. For example,my_label(:new.dept,:new.status)computes the label based on the new values of theDEPTandSTATUScolumns in the row. -
predicate: An additional predicate to combine (usingANDorOR) with the label-based predicate forREAD_CONTROL
Note the following aspects of using Oracle Label Security policies with schemas:
-
If you apply a policy to an empty schema, then every time you create a table within that schema, the policy is applied. Once the policy is applied to the schema, the default options you choose are applied to every table added.
-
If you remove the policy from a table so that it is unprotected, and then run
SA_POLICY_ADMIN.ENABLE_SCHEMA_POLICY, then the table will remain unprotected. If you wish to protect the table once again, then you must apply the policy to the table, or re-apply the policy to the schema.
If you apply a policy to a schema that already contains tables protected by the policy, then all future tables will have the new options that were specified when you applied the policy. The existing tables will retain the options they already had.
Parent topic: Step 5: Apply the Policy to a Database Table or Schema
5.7.2 Applying a Policy to a Schema
The SA_POLICY_ADMIN.APPLY_TABLE_POLICY applies a policy to a table within a schema and the SA_POLICY_ADMIN.APPLY_SCHEMA_POLICY procedure applies a policy to an entire schema.
Parent topic: Step 5: Apply the Policy to a Database Table or Schema
5.8 Step 6: Add Policy Data Labels to Table Rows
You must add policy data labels to table rows.
- About Adding Policy Data Labels to Table Rows
After you have applied a policy to a table, you must add data labels to the rows in the table. - Adding a Policy Data Label to a Table Row
You must update the table to which you are adding a policy label.
Parent topic: Creating an Oracle Label Security Policy
5.8.1 About Adding Policy Data Labels to Table Rows
After you have applied a policy to a table, you must add data labels to the rows in the table.
These labels are stored in the policy label column that you created earlier in the table. The user updating the table must have the FULL security privilege for the policy. This user is normally the owner of the table.
Parent topic: Step 6: Add Policy Data Labels to Table Rows
5.8.2 Adding a Policy Data Label to a Table Row
You must update the table to which you are adding a policy label.
Parent topic: Step 6: Add Policy Data Labels to Table Rows
5.9 Step 7: Optionally, Configure Auditing
For Oracle Label Security policies, if you want to enable auditing, then you must create a unified audit policy.
UNIFIED_AUDIT_TRAIL data dictionary view. For example:SELECT OLS_PRIVILEGES_USED FROM UNIFIED_AUDIT_TRAIL
WHERE OLS_POLICY_NAME = 'OLS_ADMIN_POL' AND DBUSERNAME = 'PSMITH';Related Topics
Parent topic: Creating an Oracle Label Security Policy
5.10 Using Oracle Label Security Policies and Oracle Flashback Data Archive
Oracle Label Security policies do not automatically work with Oracle Flashback Data Archive (FDA).
Parent topic: Creating an Oracle Label Security Policy
5.11 Using Enterprise Manager Cloud Control to Create an OLS Policy
You can create Oracle Label Security policies in Oracle Enterprise Manager Cloud Control. However, you cannot create audit policies using Cloud Control; you must use SQL*Plus to create unified audit policies.
- Creating the Label Security Policy Container Using Cloud Control
You can create the Oracle Label Security policy container in Cloud Control. - Creating Policy Components Using Cloud Control
After you create a container for the policy and set enforcement options for it, you can create components for the policy. - Creating Data Labels for the Policy Using Cloud Control
You can create data labels for an Oracle Label Security policy in Cloud Control. - Authorizing and Granting Privileges for a Policy Using Cloud Control
You can authorize and grant privileges to users for a policy during the user creation process. - Granting Privileges to Trusted Program Units Using Cloud Control
You can grant privileges to trusted program units in Cloud Control. - Applying a Policy to a Database Table with Cloud Control
You can apply an Oracle Label Security policy to a database table in Cloud Control. - Applying Policy Data Labels to Table Rows Using Cloud Control
You can apply Oracle Label Security policy data labels to table rows in Cloud Control.
Parent topic: Creating an Oracle Label Security Policy
5.11.1 Creating the Label Security Policy Container Using Cloud Control
You can create the Oracle Label Security policy container in Cloud Control.
5.11.2 Creating Policy Components Using Cloud Control
After you create a container for the policy and set enforcement options for it, you can create components for the policy.
5.11.3 Creating Data Labels for the Policy Using Cloud Control
You can create data labels for an Oracle Label Security policy in Cloud Control.
Alternatively, you can use the SA_LABEL_ADMIN package to define label components for a policy.
Related Topics
5.11.4 Authorizing and Granting Privileges for a Policy Using Cloud Control
You can authorize and grant privileges to users for a policy during the user creation process.
Alternatively, you can use the SA_USER_ADMIN package to authorize users.
5.11.5 Granting Privileges to Trusted Program Units Using Cloud Control
You can grant privileges to trusted program units in Cloud Control.
Alternatively, you can use the SA_USER_ADMIN package to authorize trusted program units.
Related Topics
5.11.6 Applying a Policy to a Database Table with Cloud Control
You can apply an Oracle Label Security policy to a database table in Cloud Control.
Related Topics