2.8 Enabling IDCS as Identity Provider in Spatial Studio
Starting from Oracle Spatial Studio Release 22.1.0, you can log into your Spatial Studio instance using users already managed by your own Oracle Cloud tenancy's IDCS identity domain.
The workflow to setup IDCS as the identity provider for Spatial Studio involves the following three steps:
- Adding Spatial Studio roles as Groups in IDCS.
- Creating an Application in IDCS.
- Copying IDCS settings into Spatial Studio's configuration file.
Before you begin, see Prerequisite Requirements for Setting Up IDCS with Spatial Studio to ensure that you meet all the prerequisite requirements.
- Prerequisite Requirements for Setting Up IDCS with Spatial Studio
- Adding Spatial Studio Role as a Group in IDCS
You must add the system administrator role supported in Spatial Studio as a group in IDCS. - Creating an Application in IDCS
This section describes the steps to add the Spatial Studio application in IDCS. - Copying IDCS Settings into Spatial Studio's Configuration File
To integrate Spatial Studio with IDCS, you must add the IDCS settings into thesgtech_config.jsonconfiguration file. - Testing IDCS Login
After all the setup steps are completed, you can test and verify the IDCS login.
Parent topic: Administering Oracle Spatial Studio
2.8.1 Prerequisite Requirements for Setting Up IDCS with Spatial Studio
To integrate IDCS with Spatial Studio, you must obtain the following details:
- Identify your IDCS tenant: See Retrieving IDCS Instance details.
- Identify your IDCS host: See Retrieving IDCS Instance details.
- Identify the Spatial Studio URL: https://localhost:4040/spatialstudio/ is the default.
- Setup an IDCS admin account: See About Oracle Identity Cloud Service User Accounts and Groups for details.
- Identify IDCS console URL: See Determining the IDCS Console URL for more information.
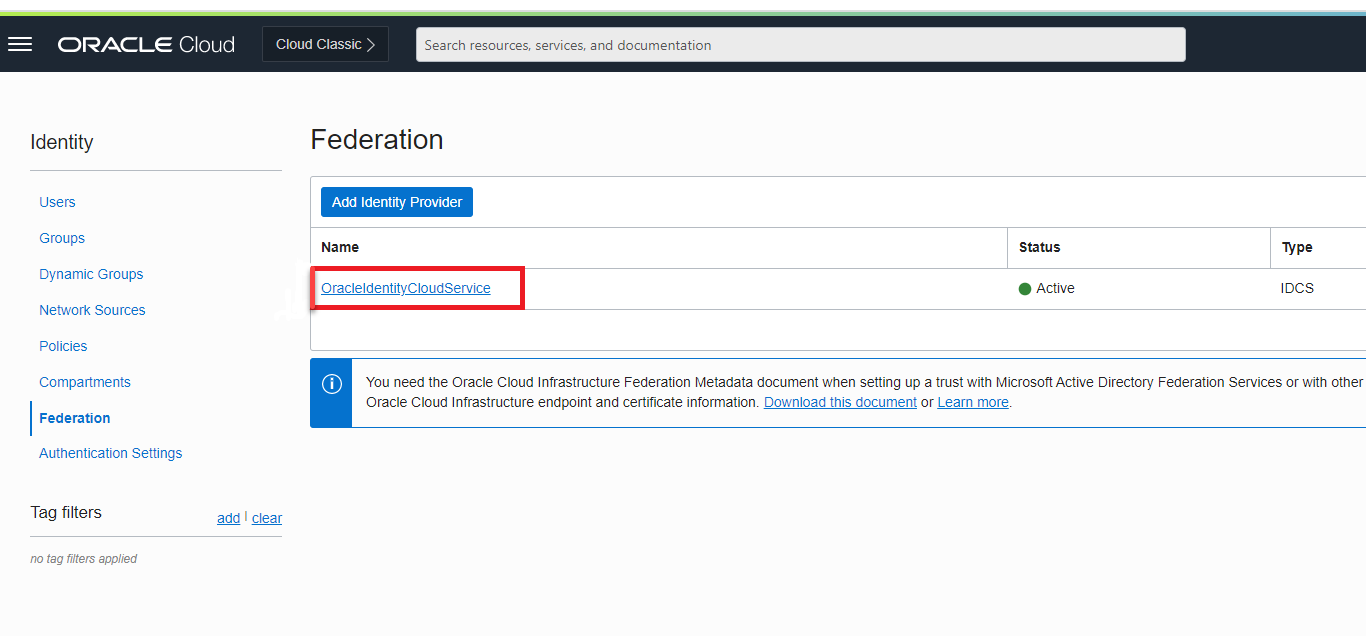
Retrieving IDCS Instance details
You can obtain the IDCS instance details by inspecting any of the IDCS URLs. For instance, you can inspect the IDCS login URL which you receive in the email when you are added as a user in IDCS. For example, consider the following sample IDCS cloud account login URL:
https://idcs-54656e616e742d4578616d706c652121.identity.oraclecloud.com/ui/v1/signin
- IDCS tenant: idcs-54656e616e742d4578616d706c652121
- IDCS host: identity.oraclecloud.com
- Determining the IDCS Console URL
OCI tenancies include a default IDCS instance and you can obtain the IDCS console URL using the OCI console.
Parent topic: Enabling IDCS as Identity Provider in Spatial Studio
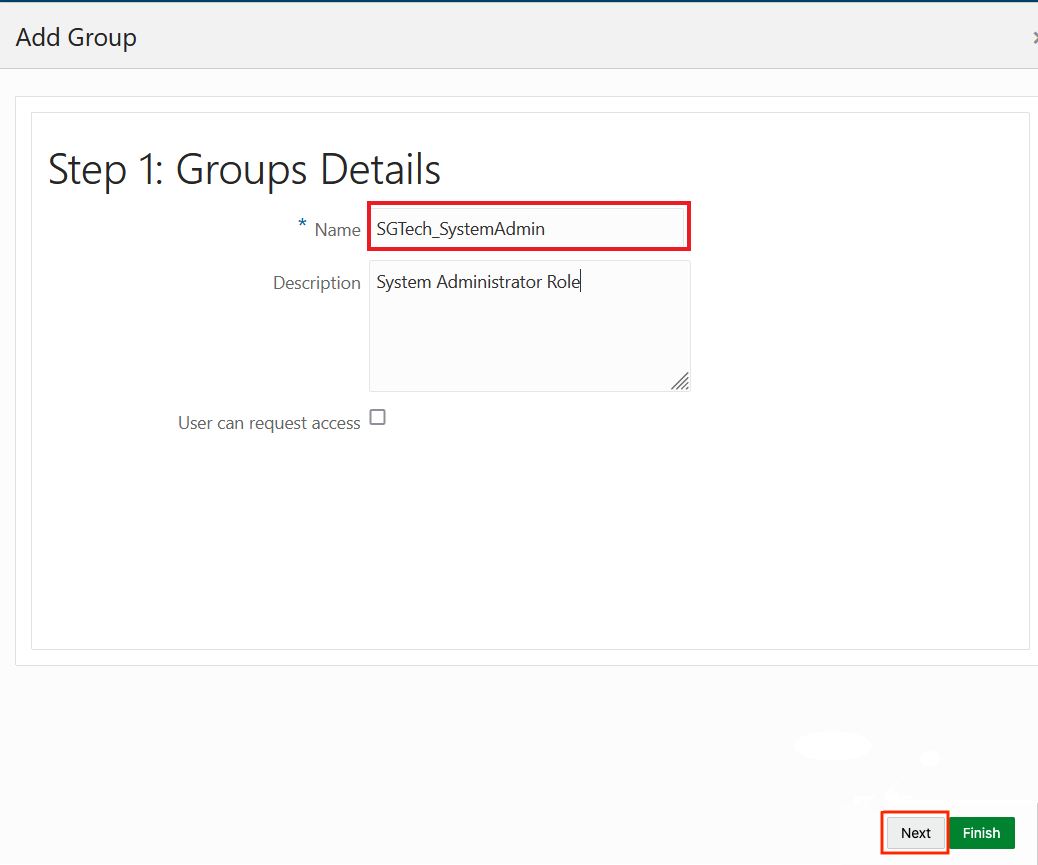
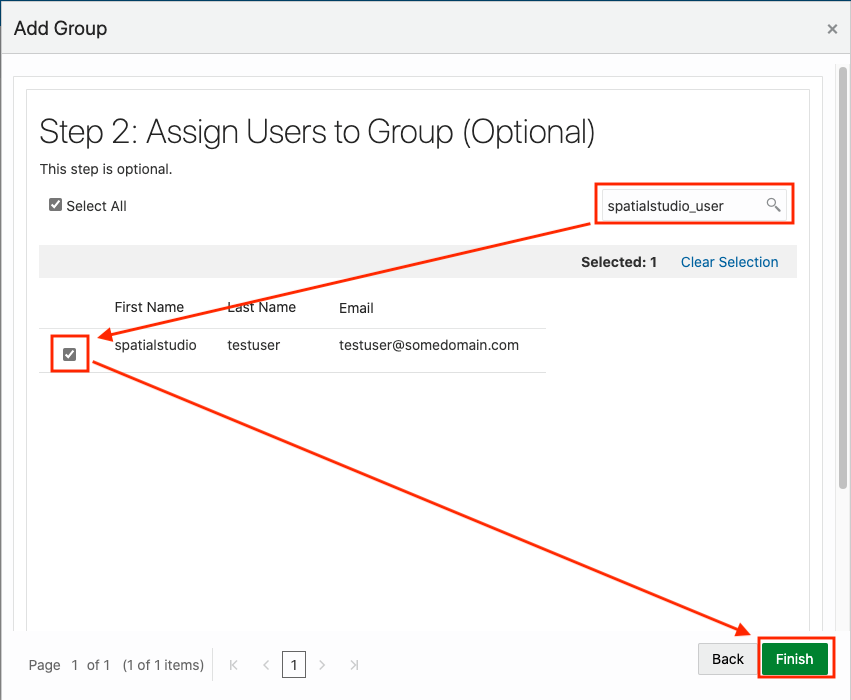
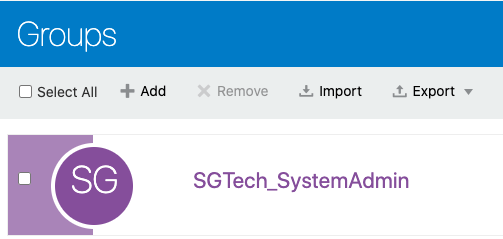
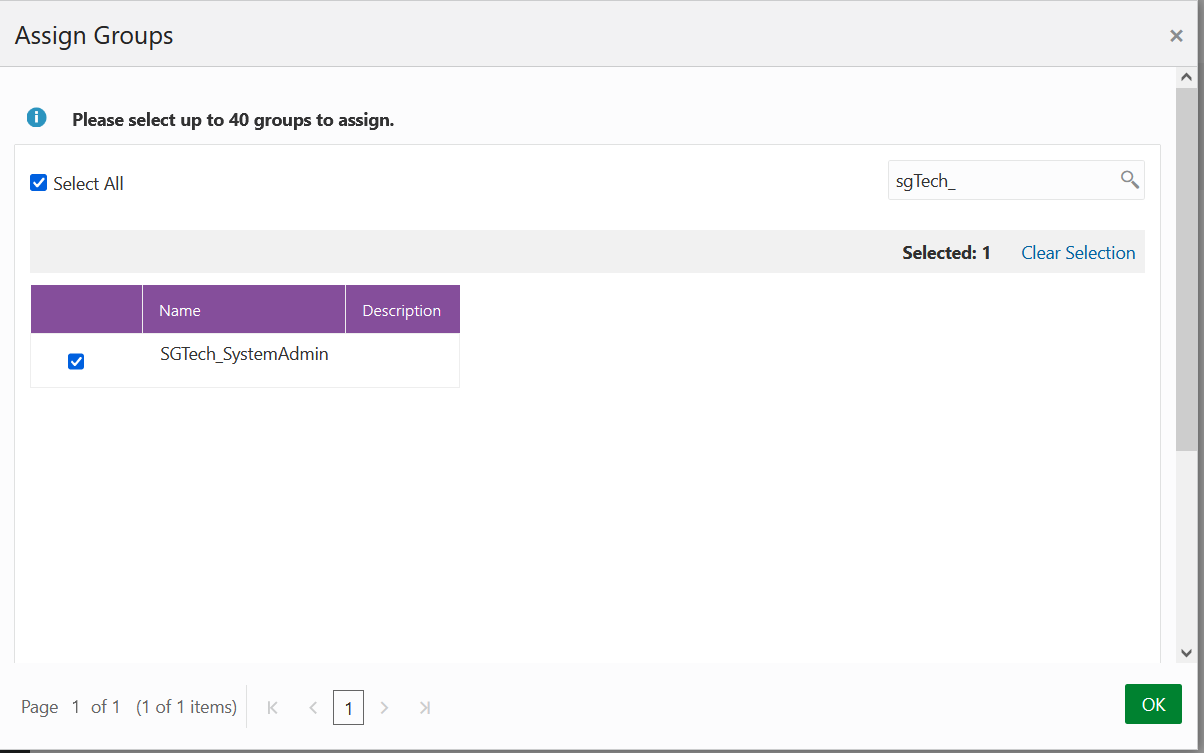
2.8.2 Adding Spatial Studio Role as a Group in IDCS
You must add the system administrator role supported in Spatial Studio as a group in IDCS.
You need to add this role as an IDCS group. However, the following applies:
- Users assigned to this group will have admin rights in the Spatial Studio instance that is being set up.
- Users who do not belong to this group will have regular access to the Spatial Studio instance when added to the IDCS application.
Perform the following steps to create the groups in IDCS:
Parent topic: Enabling IDCS as Identity Provider in Spatial Studio
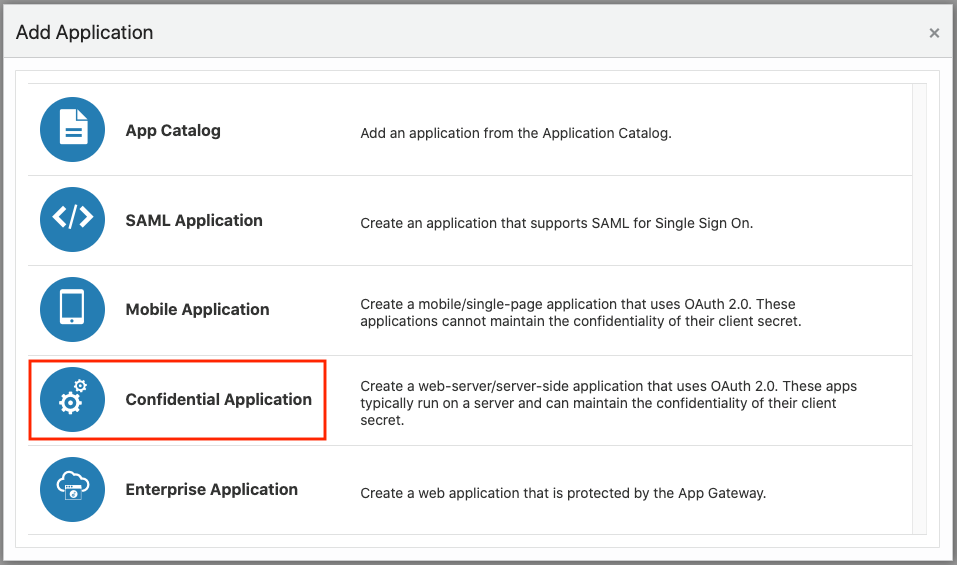
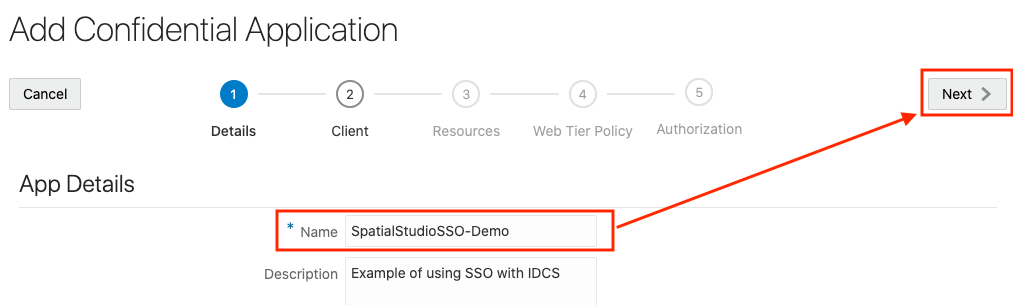
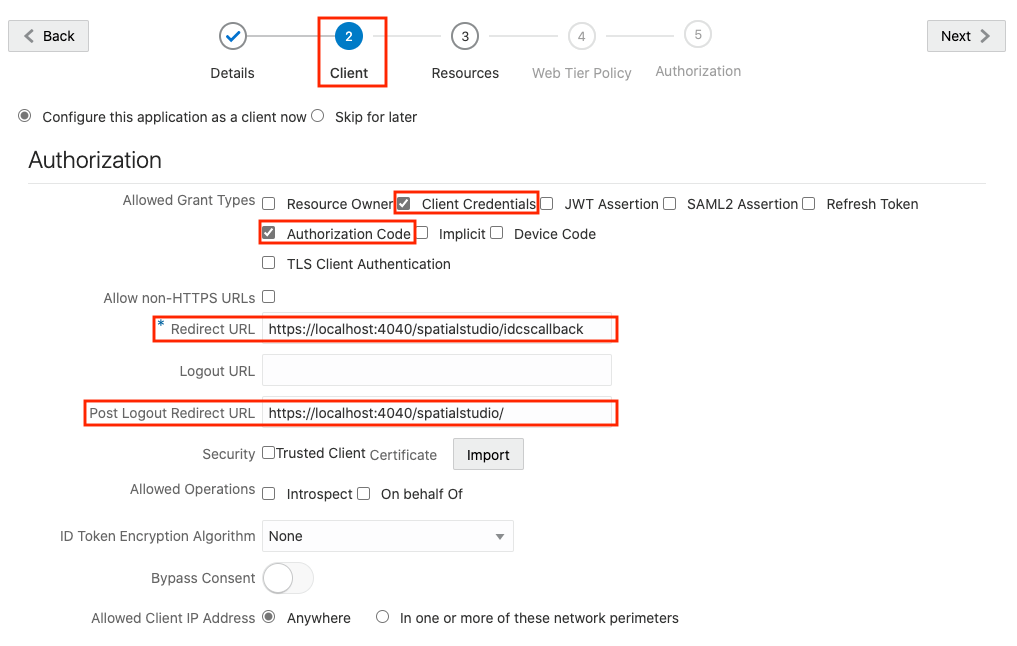
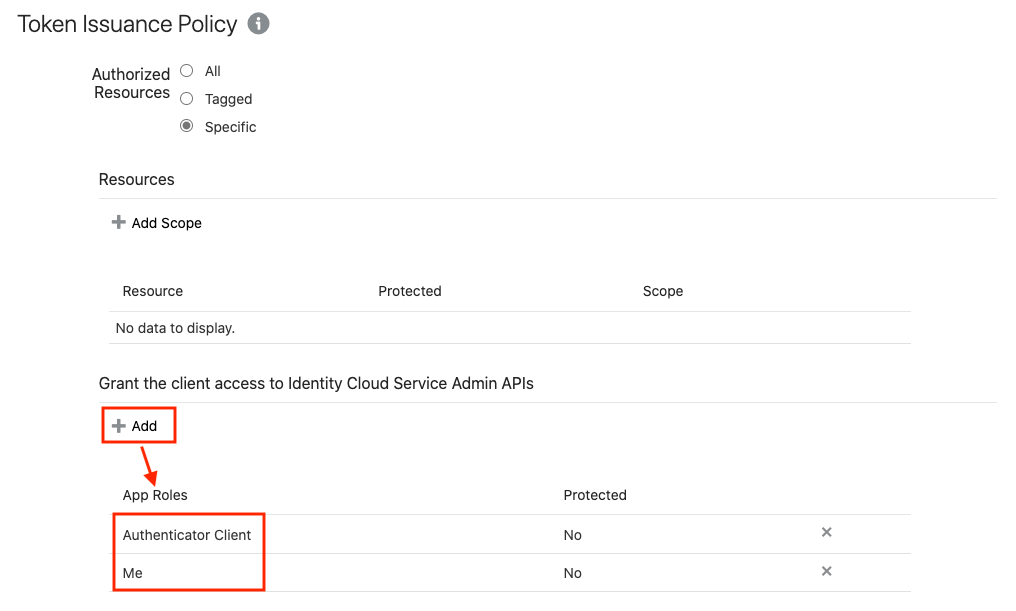
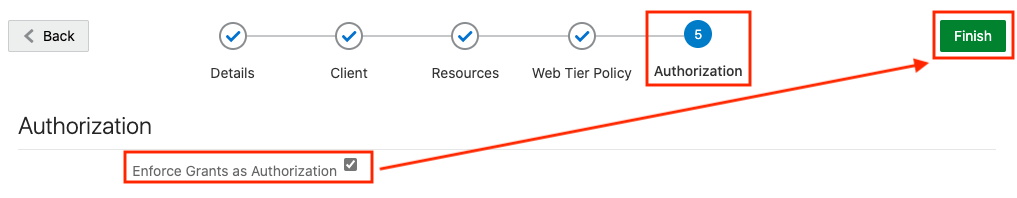
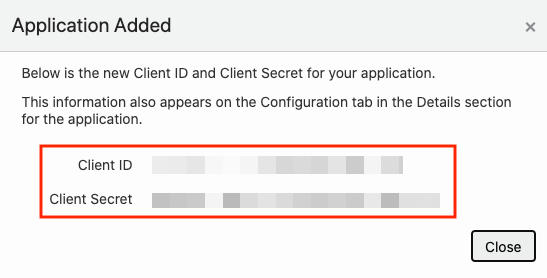
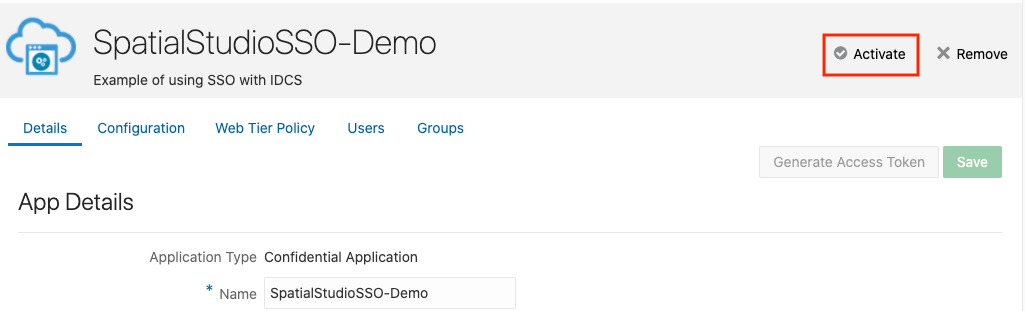
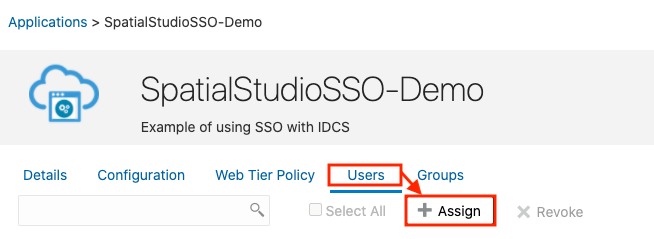
2.8.3 Creating an Application in IDCS
This section describes the steps to add the Spatial Studio application in IDCS.
Parent topic: Enabling IDCS as Identity Provider in Spatial Studio
2.8.4 Copying IDCS Settings into Spatial Studio's Configuration File
To integrate Spatial Studio with IDCS, you must add the IDCS settings
into the sgtech_config.json configuration file.
~/.sgtech/sgtech_config.json
path. You can directly append the IDCS settings into the
sgtech_config.json file. However, the best practice is
to have the IDCS settings in a separate configuration file and then import this file
into the main configuration file.
sgtech_config.json:
Parent topic: Enabling IDCS as Identity Provider in Spatial Studio
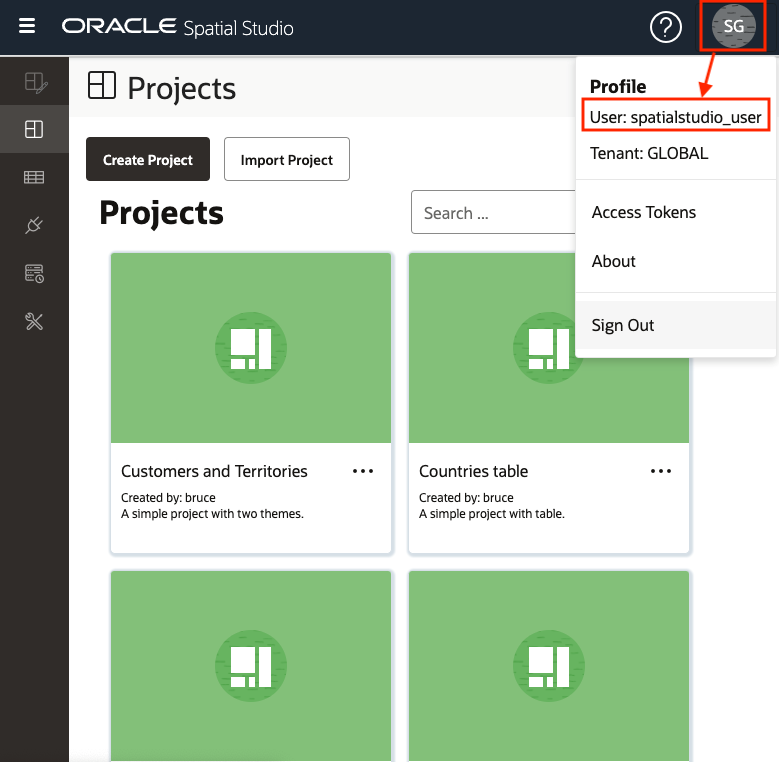
2.8.5 Testing IDCS Login
After all the setup steps are completed, you can test and verify the IDCS login.
Parent topic: Enabling IDCS as Identity Provider in Spatial Studio