5 Managing Oracle Data Miner Users
- About User Objects and Repository Objects
An Oracle Data Miner installation consists of one repository and at least one user account. The user must have access to the repository and have the privileges required for machine learning activities in the database, and appropriate access to data. - About Proxy Users for Oracle Data Miner
SQL Developer provides support for proxy users that have their own login credentials but share the same target database user account. - Setting the JVM Property
Oracle SQL Developer LDAP connections utilizing a proxy or target user protocol, can generate an SQL run time error when running the SQL Query Node. - Choosing an Access Model for Oracle Data Miner
You can choose to limit Oracle Data Miner access to a single database user, or you can enable multiple database users with access. Either way, you can create proxy users so that groups of people can share one Data Miner user account in the database. - Granting or Dropping Access Rights to Oracle Data Miner Repository
You can grant access rights to the Oracle Data Miner repository using the GUI or by running a script. You can also revoke access rights by running a script.
About User Objects and Repository Objects
An Oracle Data Miner installation consists of one repository and at least one user account. The user must have access to the repository and have the privileges required for machine learning activities in the database, and appropriate access to data.
Oracle Data Miner stores information in the schema of the Oracle Data Miner user and in the repository schema, ODMRSYS. Machine learning models and data that support workflows are stored in the user's schema. The metadata that defines the structure of projects and workflows is stored as XML documents in ODMRSYS.
- Controlling the Size of Users' Schemas
You must control the size of users’ schema to ensure conservation of storage in the schema. - Objects in Oracle Data Miner Users' Schema
Workflows create objects, tables and views. Oracle Data Miner stores these objects in the user's schema. - About Oracle Data Miner Internal Tables
Internal tables in the user's schema store information that supports workflows and machine learning activities.
Related Topics
Parent topic: Managing Oracle Data Miner Users
Controlling the Size of Users' Schemas
You must control the size of users’ schema to ensure conservation of storage in the schema.
To conserve storage in users’ schema:
-
Delete workflows when they are no longer needed.
-
Export workflows, and then delete them in the user's schema.
-
Use a separate tablespace for
ODMRSYSto isolate repository storage consumption from user tablespaces.
Related Topics
Parent topic: About User Objects and Repository Objects
Objects in Oracle Data Miner Users' Schema
Workflows create objects, tables and views. Oracle Data Miner stores these objects in the user's schema.
In the user’s schema:
-
Models, tables, and views that are directly named by the user through the Data Miner node editors. These include mining models created by the Model node and tables created by the Create Table node.
-
Tables and views that are created by Data Miner nodes to store and view generated results, but are not directly named by users through the Data Miner node editors. For example, the test results tables that are created during model build are internal. The user does not see the names of the tables, but the user can view the contents of the tables in the Test Results viewers.
Parent topic: About User Objects and Repository Objects
About Oracle Data Miner Internal Tables
Internal tables in the user's schema store information that supports workflows and machine learning activities.
The internal tables perform the following:
-
The Oracle Machine Learning engine creates tables with the
DM$prefix in the database. These tables store information about machine learning models. -
Oracle Data Miner creates tables with the
ODMR$prefix. These tables store information about workflows.
When you use SQL Developer schema navigator to view the objects owned by an Oracle Data Miner user, the internal tables and views are included in the display. You can create a filter in SQL Developer to hide the internal tables and views. When you use Oracle Data Miner interfaces to view users' schemas, the internal tables and views are automatically filtered out.
Parent topic: About User Objects and Repository Objects
About Proxy Users for Oracle Data Miner
SQL Developer provides support for proxy users that have their own login credentials but share the same target database user account.
A SQL Developer connection typically provides database access to a single user that is defined in that database. SQL Developer has several connection types that support the creation of proxy users.
A Connection is a SQL Developer object that specifies the login credentials for a specific user in a specific database. A Data Miner connection is a SQL Developer connection that includes the privileges required by a Data Miner user. Oracle Data Miner connections are listed in the Navigator on the Data Miner Connections tab.
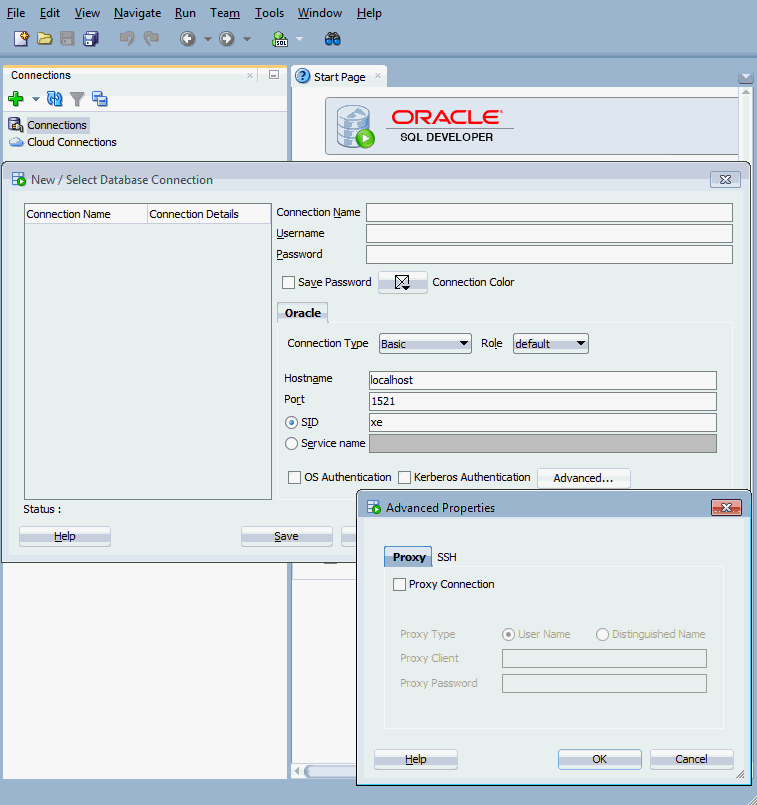
Oracle Data Miner supports proxy authentication for Basic and TNS connection types. Figure 5-1 shows the SQL Developer Advanced Properties dialog box, which allows the creation of a proxy user for an existing Basic connection.
Figure 5-1 Proxy User for a Basic Connection in SQL Developer
You can also use the SQL Developer LDAP service to create users that are functionally equivalent to proxy users. With LDAP, you create the individual (proxy) users and then associate them with an existing database user connection.
Setting the JVM Property
Oracle SQL Developer LDAP connections utilizing a proxy or target user protocol, can generate an SQL run time error when running the SQL Query Node.
oracle.jdbc.createDescriptorUseCurrentSchemaForSchemaName to true. To set the JVM property, open Oracle SQL Developer and run the following from the command prompt: C:\<SQL Developer Installation Directory>\sqldeveloper\ide\bin\sqldeveloper.exe -JDoracle.jdbc.createDescriptorUseCurrentSchemaForSchemaName=true
To make a permanent change, update the sqldeveloper.conf file and include the property definition, as follows:
sqldeveloper.conf file is shown below with the new text in bold:
IncludeConfFile ../../ide/bin/ide.conf
SetJavaHome ../../jdk
#Workaround for LDAP Proxy failure
AddVMOption
-Doracle.jdbc.createDescriptorUseCurrentSchemaForSchemaName=true
Parent topic: Managing Oracle Data Miner Users
Choosing an Access Model for Oracle Data Miner
You can choose to limit Oracle Data Miner access to a single database user, or you can enable multiple database users with access. Either way, you can create proxy users so that groups of people can share one Data Miner user account in the database.
The access model that you choose depends on the number of users that you need to support, and whether the users need to collaborate in a shared environment or work independently in a private environment.
- Single User Access
In Single User Access, there is one user schema. Either one person can use Oracle Data Miner or a group of people with proxy accounts can use Oracle Data Miner. Proxy users have access to the same models and database objects. - Multiple User Access
In Multiple User Access, there are multiple user schemas. A schema can support an individual user, or it can support a workgroup of proxy users. - Shared User Environment
Shared user environments facilitate collaboration. Oracle Data Miner uses locking mechanisms to coordinate access to workflows, when several proxy users share access to a single database account. - About the Document in Use Condition
The Document in Use message is generated when a user tries to edit a workflow while the workflow sessions are running in the database.
Parent topic: Managing Oracle Data Miner Users
Single User Access
In Single User Access, there is one user schema. Either one person can use Oracle Data Miner or a group of people with proxy accounts can use Oracle Data Miner. Proxy users have access to the same models and database objects.
All users can create, modify, and drop database objects, and all users see the results of other users' work. Single user access ensures private workspaces but does not promote collaboration.
In the absence of proxies, a user functions autonomously within its own schema. The security mechanisms of Oracle Database prevent users from modifying objects that belong to another user's schema.
Parent topic: Choosing an Access Model for Oracle Data Miner
Multiple User Access
In Multiple User Access, there are multiple user schemas. A schema can support an individual user, or it can support a workgroup of proxy users.
You can set up some combination of individual and shared access. You can also use proxy authentication for all users, even for unshared users.
Parent topic: Choosing an Access Model for Oracle Data Miner
Shared User Environment
Shared user environments facilitate collaboration. Oracle Data Miner uses locking mechanisms to coordinate access to workflows, when several proxy users share access to a single database account.
Workflows are locked while they are executing or waiting to execute, or when they are being edited.
The name space for workflows is a project. When several users work in the same project, they should take care to name their workflows in a way that distinguishes them from the workflows of other users. For example, users could agree to prefix their workflow names with their initials.
The name namespace for database objects, such as mining models and tables, is unique within the shared schema. Oracle Data Miner follows naming conventions for database objects to ensure uniqueness. If a user overrides the system-generated name for a table that is referenced in another workflow, then a warning is generated.
Parent topic: Choosing an Access Model for Oracle Data Miner
About the Document in Use Condition
The Document in Use message is generated when a user tries to edit a workflow while the workflow sessions are running in the database.
If an Oracle Data Miner client disconnects from the network (for example, if a cable is disconnected or a laptop goes into deep sleep), then the locks on the workflows are not released. The disconnected session is still locked and running in the database. If another user tries to edit the workflow, the Document in Use message is generated.
You can attempt to reclaim the lock by clicking the lock on the tool bar. If you are unable to reclaim the lock, then you must stop the database session that is holding the locks. Refer to the topic "Terminating Sessions" in Oracle Database Administrator’s Guide for instructions.
Related Topics
Parent topic: Choosing an Access Model for Oracle Data Miner
Granting or Dropping Access Rights to Oracle Data Miner Repository
You can grant access rights to the Oracle Data Miner repository using the GUI or by running a script. You can also revoke access rights by running a script.
- Granting Access Rights Using the GUI
When you install Oracle Data Miner repository using the Graphical User Interface (GUI), access rights to the repository are automatically granted to your user ID. If you logged in as a proxy or LDAP user, Oracle Data Miner automatically grants the access rights to the target user. - Granting Access Rights Using a Script
You can grant access rights to the repository by executing theusergrantsscript and specifying a user name. The repository must be already installed before you run the script. - Dropping Access Rights Using a Script
You can drop access rights to the Oracle Data Miner repository by executing thedropusergrantsscript. - Granting Access to Data
You must have read access or theSELECTpermission to data that is used for building mining models or for scoring.
Parent topic: Managing Oracle Data Miner Users
Granting Access Rights Using the GUI
When you install Oracle Data Miner repository using the Graphical User Interface (GUI), access rights to the repository are automatically granted to your user ID. If you logged in as a proxy or LDAP user, Oracle Data Miner automatically grants the access rights to the target user.
When you select a connection for the first time to a database that already has the repository installed, you are prompted to confirm that you want to grant access rights and, optionally, install the sample data.
Granting Access Rights Using a Script
You can grant access rights to the repository by executing the usergrants script and specifying a user name. The repository must be already installed before you run the script.
usergrants.sql user_access
For example, the following statement grants Oracle Data Miner access to the user dmuser1:
@usergrants dmuser1
The user name that you specify must be a target user. Any proxy or LDAP users that authenticate based on this target user automatically acquire the permissions of the target user.
Dropping Access Rights Using a Script
You can drop access rights to the Oracle Data Miner repository by executing the dropusergrants script.
dropusergrants.sql user_access
For example, the following statement drops the access rights that were granted to dmuser1.
@dropusergrants dmuser1
As with the usergrants script, the user name that you specify must be a target user. Any proxy or LDAP users that authenticate based on this target user automatically acquire the permissions of the target user. When you drop the access rights for the target user, all proxy and LDAP users that are based on that target user automatically lose access to the repository.
Related Topics
Granting Access to Data
You must have read access or the SELECT permission to data that is used for building mining models or for scoring.
You must grant SELECT permission directly to a target user. Do not grant permission indirectly to a user role. The SELECT permission must be granted directly so that Oracle Data Miner can create views on behalf of the user. If Oracle Data Miner cannot create views, then the user may not be able to access the data.