1 A Service Administrator's Roadmap to Oracle Blockchain Platform
Oracle Blockchain Platform Enterprise Edition Overview
Oracle Blockchain Platform gives you a pre-assembled platform for building and running smart contracts and maintaining a tamper-proof distributed ledger.
Oracle Blockchain Platform is a network consisting of validating nodes (peers) that update the ledger and respond to queries by executing smart contract code—the business logic that runs on the blockchain. External applications invoke transactions or run queries through client SDKs or REST API calls, which prompts selected peers to run the smart contracts. Multiple peers endorse (digitally sign) the results, which are then verified and sent to the ordering service. After consensus is reached on the transaction order, transaction results are grouped into cryptographically secured, tamper-proof data blocks and sent to peer nodes to be validated and appended to the ledger. Platform administrators can use the Blockchain Platform Manager to create and manage platform instances, while network administrators can use the Oracle Blockchain Platform console to configure the blockchain and monitor its operation.
Oracle Blockchain Platform Enterprise Edition provides an independently-installable version of Oracle Blockchain Platform built on Docker containers and delivered as a pre-built VM image for multiple virtualization options. The VM is delivered in an Open Virtualization Appliance (ova) format and can be imported and started using VMWare ESXi, Oracle VirtualBox, and Oracle Linux Virtualization Manager. Once the VM is running, the Blockchain Platform Manager is used for configuration, provisioning, and patching multiple Blockchain Platform instances, which can be deployed over multiple VMs to distribute the Docker containers running Oracle Blockchain Platform nodes. Similarly to the cloud PaaS, this edition is fully pre-assembled and can create new complete blockchain instances in minutes.
In addition to flexible virtualization options, the enterprise edition enables dynamic scalability to handle the evolving workloads by increasing the resources in the current VMs or scaling out to more VMs to run the additional nodes (e.g., peers, orderers.) Additional VMs and nodes can be deployed in other datacenters across a WAN for disaster recovery (DR.) Unlike typical applications, Oracle Blockchain Platform's distributed ledger and the distributed metadata database handle data replication out-of-the-box.
Feature parity with the cloud version ensures that customers can deploy chaincode and use the same chaincode APIs and extensive REST APIs across both versions. Oracle innovations in using Berkeley DB for world state with SQL-based queries, built-in transaction synchronization to off-chain rich history database, intuitive and comprehensive console with powerful operations and monitoring tools, and all the other unique enterprise-grade features are shared across the cloud and on-premise versions.
Security, Authentication, and Authorization
Introduction to Oracle Blockchain Platform Enterprise Edition Security
Oracle Blockchain Platform Enterprise Edition deals with security on several levels. At the top level is the security related to the Oracle Blockchain Platform virtual machines (VMs). Next is the security associated with the control plane that is used to manage the life cycle on Oracle Blockchain Platform instances. Control plane (the Blockchain Platform Manager) users are able to create, scale out, scale in, patch, and other life cycle operations. For each instance there are users authorized for managing, monitoring, and administering an instance. Finally there are users of the instance that access an instance either via the Fabric SDK or the Oracle Blockchain Platform REST Proxy.
All user information including their roles and passwords are stored in your authentication server. A default LDAP server is provided as part of the VM and is only intended for development purposes. It is expected that you will connect to your corporate authentication server in production.
Managing Security
Creating Oracle Blockchain Platform VMs
- Oracle VirtualBox – Primarily intended for development and testing
- Oracle Linux Virtualization Manager
- VMWare Workstation
- VMWare ESXi
Securing Data at Rest
At the time of importing the OVA file or sometime later users may want to enable disk encryption in their hypervisor to protect data at rest. This may also require that the VM be encrypted, which would also be handled by hypervisor settings.
Control Plane VM and Data Plane Clusters
A particular VM instance should be reserved for the Oracle Blockchain Platform control plane. This VM will run the provisioning server that is used to control the life cycle operations of Oracle Blockchain Platform instances within a specific Oracle Blockchain Platform platform. It is possible to deploy multiple Oracle Blockchain Platform platforms, each with its own control plane VM and clusters of data plane VMs. Each cluster of data plane VMs only supports a single Oracle Blockchain Platform instance.
Figure 1-1 Oracle Blockchain Platform
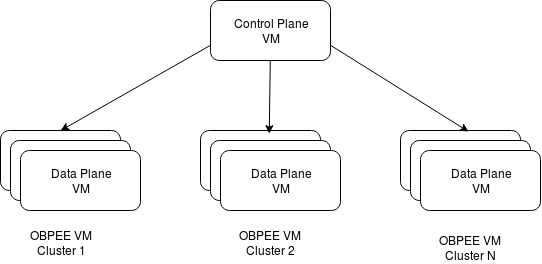
Data plane clusters are automatically added to the Docker swarm used to allow containers to communicate with each other.
Securing the VM Network
You'll initially log in with user ID oracle, and change your password as described in Add Users to Your LDAP Server Using a Script. After logging in, configure the firewall (firewalld) on the VM to protect ports that shouldn’t be exposed outside the cluster. Whitelists should be used to only allow access to and from the other VMs in the cluster, and to grant access from any external load balancers that may be used.
- Data plane console server
- Fabric-CA
- Ordering Service Nodes
- Peers
Figure 1-2 Firewall, load balancer, and instance relationship
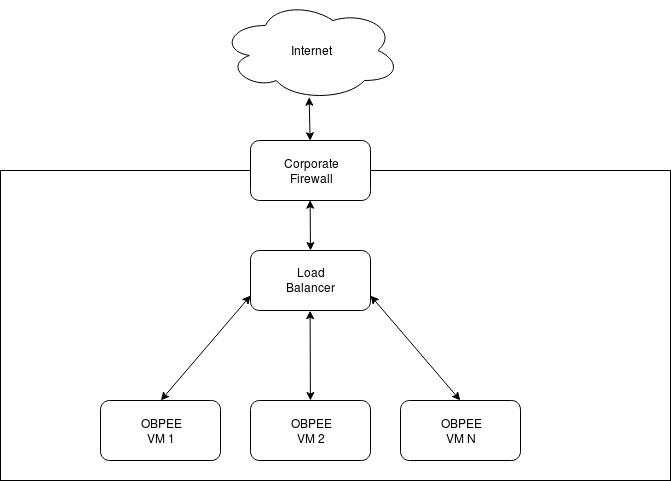
Normal Cluster Members
The VMs in a cluster need to be able to communicate with each other via Docker swarm. See the section below on which ports need to be accessible to other VMs in the cluster.
CRC Cluster Members
In production deployments, it is highly recommended that the chaincode runtime containers be placed in their own VM. Unless your chaincode needs to access external services, the VM should be configured to only be able to communicate with the other members of the cluster.
SSH Configuration
As delivered from Oracle, the VM appliance is configured with a default user of oracle and a default password of Welcome1. The password must be changed upon first login. In order to manage the VM, SSH is allowed with password-based authentication. This should be changed to public key based authentication for user oracle. No other users are required or should be configured.
VM Network Configuration
The Oracle Blockchain Platform VMs come configured and ready to run. The following ports are open on the VM. Most of these ports should not be exposed to the Internet or other unsecured hosts and access should be blocked by firewall rules on the VMs.
Internet Accessibility
Some ports may need to be accessible outside the corporate network. In particular, to have other Oracle Blockchain Platform or Fabric instances running outside the corporate network connect to an instance inside the corporate network, certain ports associated with the ordering service and peers will need to be accessible.
Corporate Network Accessibility
It is recommended that console UI ports associated with the provisioning console and instance console be restricted to at most access from inside the corporate network. Ideally they would be restricted to even a subset of that, only machines used for network management and operations.
Port Accessibility Guide
| Port | Use or purpose | Internet accessible | Corporate network accessible | Accessible by other VMs in OBPEE cluster |
|---|---|---|---|---|
| 22 | SSH | N | N[1] | N |
| 389 | Local LDAP server for development purposes | N | N | Y |
| 443 | Docker Registry | N | N | Y |
| 636 | Local LDAP server for development purposes | N | N | Y |
| 2375 | Docker Daemon | N | N | Y |
| 2377 | Docker Swarm | N | N | Y |
| 7070 | Control plane UI and REST (http)– Application connector | N | Y[2] | N |
| 7443 | Control plane UI and REST (https)– Application connector | N | Y[3] | N |
| 7946 | Docker Swarm | N | N | Y |
| 8080 | Component manager | N | N | Y |
| 10000-10200 | Ports assigned to the load balancer for the various instance containers such as peer, orderer, etc. | Y | Y[4] | Y |
[1] SSH is only required if the VM console isn’t accessible
[2] UI ports should be only accessible by machines needed for provisioning and configuring instances
[3] UI ports should be only accessible by machines needed for provisioning and configuring instances
[4] See the section on load balancer configuration
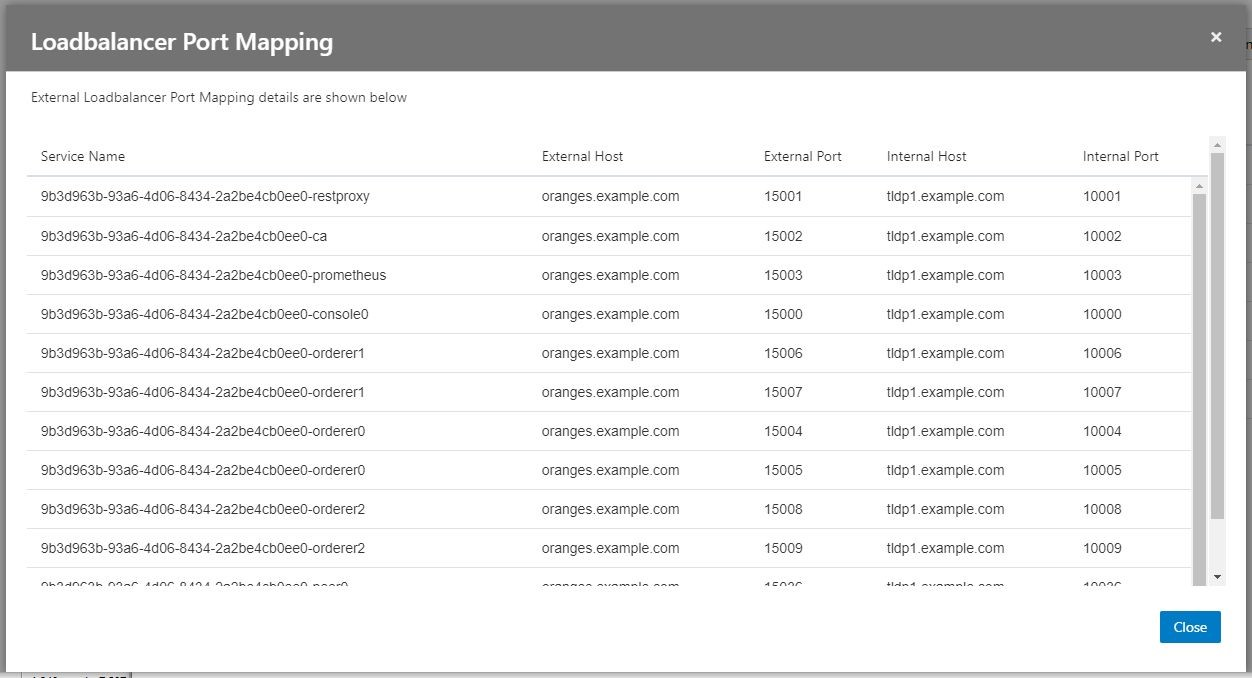
Load Balancer Configuration
If using an external load balancer, it will need to be configured to perform TLS termination and pass the ports as listed in the provisioning console to the appropriate VM host and port. Below is an example of the necessary port mappings as reported by the provisioning console:
Figure 1-3 Load Balancer Port Mapping
Configuring Authentication and Authorization
Authentication in Oracle Blockchain Platform is performed using an authentication server. Users must have an account in the authentication server in order to be able to use the service.
Users associated with certain authentication groups are granted specific privileges as defined in User Groups and Roles.
Workflow for Administering Oracle Blockchain Platform
To start using Oracle Blockchain Platform, refer to the following tasks as a guide.
| Task | Description | More Information |
|---|---|---|
| Prepare your hardware |
Read through the suggested architectural designs and decide which is appropriate for your configuration. Ensure your hardware meets the required prerequisites. |
|
| Deploy Oracle Blockchain Platform Enterprise Edition |
Deploy the Oracle Blockchain Platform Enterprise Edition virtual machine. Access Blockchain Platform Manager |
|
| Add and manage users and roles | A rudamentary LDAP server is provided with Oracle Blockchain Platform Enterprise Edition, however you'll need to use a third-party tool to add users and roles. | |
| Provision a service instance | Use the Create Instance wizard in Blockchain Platform Manager to create a service instance. | Provision an Instance using the Blockchain Platform Manager |
| Configure your blockchain network | Once your instance is created, you can use the Blockchain Platform Console to configure the network. | What's the Console? |
After you’ve created your instance and any required users, you can begin to use Oracle Blockchain Platform as described in Using Oracle Blockchain Platform