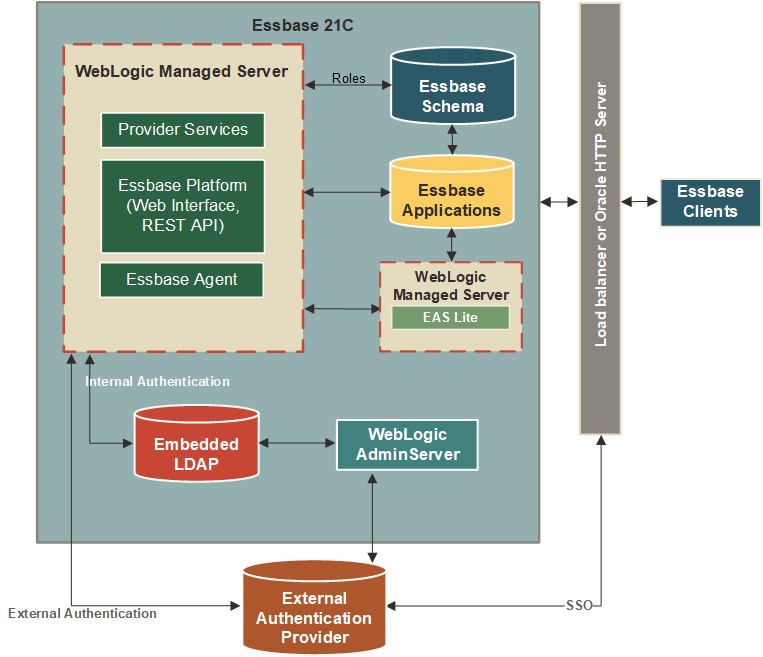
WebLogic Authentication
Here are various options for configuring WebLogic authentication, which is the default mode. You can optionally use an external LDAP or identity provider.
If you're using WebLogic authentication, it's recommended to federate users to an external authentication provider, such as Microsoft Active Directory, which is suitable for large production environments. If you use WebLogic with the internal LDAP that is included with it, it is called "WebLogic Embedded LDAP." This configuration is not recommended for production use.
After you federate users to an external provider, native users remain in WebLogic, but only the WebLogic administrative user can log in to Essbase. Use the WebLogic administrative user to assign Essbase roles to federated users.
Configure WebLogic to Use LDAP
You can integrate Essbase WebLogic with LDAP.
See Configuring Weblogic to use LDAP.
Configure WebLogic to use Microsoft Active Directory
You can integrate Essbase WebLogic with Microsoft Active Directory (MSAD). Users and groups are then managed using MSAD administration tools, and user roles are assigned in the Essbase web interface or using REST APIs.
Configure WebLogic-based Single Sign-On
Configure Oracle HTTP Server-based SSO
If you use a load balancer or a web server, such as Oracle HTTP Server (OHS), you can also configure it to point to the same external security provider for SSO use cases. Note that this only addresses an SSO-based use case. You must still configure WebLogic to point to the external authentication provider.
Essbase WebLogic Authentication Diagram