2 External Connection
Oracle utilizes a combination of a VPN solution and TLS to secure communications between Oracle Advanced Services Gateway, located within the customer's environment, and the Oracle Services Support center locations. The VPN is primarily used for tasks such as facilitating patching requirements from Oracle Services Support center locations to Oracle Advanced Services Gateway and TLS is used for transporting the monitoring telemetry from Oracle Advanced Services Gateway to the Oracle Services Support center locations.
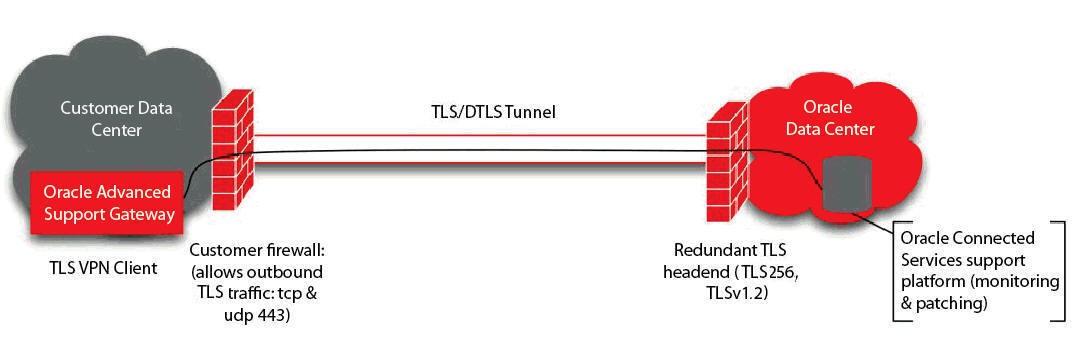
TLS VPN and Oracle Advanced Services Gateway
The Oracle Advanced Services Gateway is configured with a software TLS-based VPN client.
When the Gateway boots up, it opens an outbound connection to one of three Oracle Services Support centers, establishing a TLS VPN tunnel. At that point, this connection is used for inbound connectivity between the Oracle Services Support center and the Gateway. No inbound firewall port openings are required, as the initial connection is outbound. The Gateway is assigned a unique ID and password and connects to one of three Oracle VPN concentrators. The TLS-based VPN has the following features:
- Connection based on TLS 1.2, AES256 symmetric encryption to ensure traffic integrity and confidentiality;
- Continuous VPN connection availability through the use of active/passive VPN cluster servers at the Oracle Services Support centers. Any hardware or software issues on the active VPN server failover all connections to the backup VPN.
- Disaster recovery processes that use multiple clusters around the world. Any connection issue with one of the Oracle Services Support centers failover client connections to the other Oracle Services Support centers.
Figure 2-1 A TLS-Based VPN Client Connection from Oracle Advanced Services Gateway to Oracle
Note:
The TLS VPN is the standard method for establishing the connection with Oracle. Alternative connection methods are available on an exception, customer-by-customer basis that is summarized in external-connection.html#GUID-B5F4312B-0031-47F6-BB8A-0CE56D684EB4__GUID-9E64D6C9-5751-424D-B1BD-88B031C637A7. If you wish to explore these options further, please contact your Oracle Implementation Manager.Alternative External Connection Option
Oracle offers an alternate method for establishing a connection using IPSec. The connection is terminated on the customer's existing VPN hardware. This option generally requires an extended implementation cycle and is approved on an exception basis. If the customer chooses to use their existing VPN device (for example, firewall or VPN concentrator) as a termination point, the VPN overall requirements described above remain the same. The encryption domain requirements for this connection will create a more complex configuration.
The requirements include, but are not limited to:
- A public IP per Gateway connection supplied by the customer for use inside the VPN encryption domain;
- Access to three /26 subnets and multiple /32 addresses inside the encryption domain;
- Network Address Translation (NAT) between the host and the Oracle resources over the tunnel is not supported (the Gateway must communicate directly to the public IP addresses inside the Oracle VPN.)