1 Security Overview
The following topics are discussed:
The dynamic and complex nature of today's IT environments, the potential fallout of security breaches in terms of the financial implications and loss of goodwill coupled with stringent regulatory requirements make security a critical area of consideration for both business and IT managers. While security considerations are important for standalone applications, the introduction of distributed system management applications can make it yet more challenging. While standardized security best practices are available for databases and application servers, there aren't any standardized security benchmarks specifically for system management products. However, Enterprise Manager has been evaluated and in the past, has received a third party security certification, by the Common Criteria Recognition Arrangement.
Securing Enterprise Manager requires working closely with System Administrators, Network Administrators, Database Administrators, Application Administrators and the Security team. This document can be used by all concerned parties to identify various security considerations and the best practices for securing Oracle Enterprise Manager deployments. The recommendations in this document are based on our experience with both customer deployments and Oracle's own internal usage of Enterprise Manager.
Security Threats
The following table briefly summarizes the primary security threats to your Enterprise Manager Cloud Control environment.
Table 1-1 Security Threats
| Threats | Security Consideration | Resolution/Best Practice |
|---|---|---|
|
Man-in-the-middle attacks |
Data confidentiality and integrity |
Data Confidentiality and Integrity
Man-in-the-Middle Attacks
 Best Practice: Secure communication between Enterprise Manager components. |
|
Denial-of-service attacks |
Data availability |
Data Availability
Denial-of-Service attacks
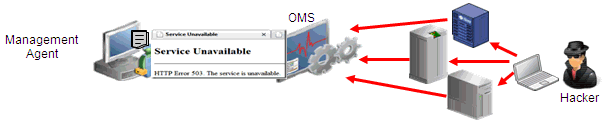 Best Practice: Secure individual Enterprise Manager components |
|
Password crack attacks |
Authentication |
Authentication
Password Crack Attacks
 Best Practice: Change passwords and enable password profiles |
|
Exploitation of authorization |
Segregation of duties |
Exploitation of Authorization
Segregation of Duties
Best Practice: Follow principle of least privileges |
|
Repudiation |
Non-repudiation |
Accountability of Actions
Repudiation
 Best Practice: Audit Enterprise Manager actions |
Security Principles
Underlying all strategies to implement effective system security are the following basic principles:
Separation of Duties and Principle of Least Privilege
The principle of least privilege and separation of duties are concepts that, although semantically different, are intrinsically related from the standpoint of security. The intent behind both is to prevent people from having higher privilege levels than they actually need. Now that their relationship has been framed, let us define the concepts.
-
Principle of Least Privilege: Users should only have the least amount of privileges required to perform their job and no more. This reduces authorization exploitation by limiting access to Enterprise Manager resources such as targets, jobs, or monitoring templates for which they are not authorized.
Example: A user whose sole responsibility is to monitor and maintain a human resources database does not need privileges to access and manage Enterprise Manager plug-ins on the Oracle Management Services (OMS).
-
Separation of Duties: Beyond limiting user privilege level, you also limit user duties, or the specific jobs they can perform with Enterprise Manager. No user should be given responsibility for more than one related function. This limits the ability of a user to perform a malicious action and then cover up that action.
Example: You have an Enterprise Manager administrator who is responsible for creating user accounts. However, that administrator may create unnecessary accounts, perhaps for unauthorized colleagues to access confidential systems. If that administrator also has the ability to view and erase the audit logs, then there is a potential problem in that it prevents a wayward administrator from being caught. In this situation, you want to separate the account creation duties from the security administration duties. The person who is the account administrator, in this case, should also not be the security administrator.
In order to be effective, the principle of least privilege and separation of duties should be enforced for all Enterprise Manager users in your organization.
Encryption
Encryption is the process of transforming data into an unreadable format using a secret key and an encryption algorithm. For Enterprise Manager, emkey is the key to encrypting and decrypting sensitive data within your Enterprise Manager environment. It is important that emkey be accessible only to authorized users.
Monitoring for Suspicious Activity (Auditing)
Whenever an Enterprise Manager administrator makes use of higher-level privileges, such as creating new Super Administrator accounts, you should be able to look at the Enterprise Manager audit logs and tell whether those account creation actions were warranted. Enterprise Manager's audit capabilities allow you to monitor and record all administrator actions that take place. You can perform activities such as:
-
Investigating suspicious activity. For example, if a user is frequently accessing systems outside their job responsibilities, then a security administrator might decide to track access to those machines.
-
Notify a supervisor of the actions of an unauthorized user. For example, an unauthorized user could be changing or deleting data, or the user has more privileges than expected, which can lead to reassessing user authorizations.
Non-repudiation
Non-repudiation is a method of establishing user action accountability by "proving" that a user performed a specific action: Users cannot falsely deny that they performed that action. Conversely, non-repudiation also protects users from later being accused of having performed a specific action.
With regard to data, non-repudiation, is a way to prove that a given sender actually sent a particular message. Non-repudiation is typically achieved through the use of digital signatures. The originator of a message uses a cryptographic tool to convert plain, readable messages or plaintext into encrypted ciphertext. While the original text is present, its appearance changes into a form that is unintelligible if intercepted. The message recipient likewise uses a cryptographic tool to decrypt the ciphertext into its original readable format.