Configure Compliance Management
Before you can use the compliance features, compliance frameworks, compliance standards, and compliance standard rules must be defined for your enterprise.
The following sections describe how to define and maintain these compliance entities.
About Compliance Frameworks
A compliance framework is a hierarchical structure where any node can be mapped to one or more compliance standards, compliance standard rule folders, and compliance standard rules. Compliance frameworks provide a way to map your standards to a structure similar to the regulatory or standards-based compliance structure you use in your company.
Managing Compliance Frameworks
To manage compliance frameworks, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click Compliance Frameworks tab.
-
Highlight the compliance framework you want to manage and choose the action you want to perform.
Frameworks Provided by Oracle and User-Defined Compliance Frameworks
There are compliance frameworks provided by Oracle and user-defined compliance frameworks.
-
Compliance frameworks provided by Oracle include
-
Oracle Support Compliance is a collection of controls that check for expected environment compliance for Oracle Supportability.
-
Oracle Generic Compliance Framework is a standard set of compliance standards and associated controls for tracking changes and events taking place across your IT infrastructure for determining how well your organization is in compliance with your IT policies.
-
Security Technical Implementation Guide (STIG) is a set of standards to ensure Security Technical Implementation Guide (STIG) compliance.
-
-
User-defined compliance frameworks
You can define a compliance framework to satisfy the needs of your organization.
Compliance frameworks provided by Oracle cannot be deleted or edited. However, if you want to extend these frameworks, use the Create Like functionality to create your own user-defined frameworks based on the Oracle provided frameworks and then edit the new frameworks.
Recommendation: It is highly recommended that you create a top level compliance framework like the ones provided for STIG and Oracle Generic compliance.
Benefits of Using Compliance Frameworks
Compliance standards are defined to perform tests on targets. Examples include: testing if a configuration value is set properly, test to see if real-time file changes are occurring, and so on. A compliance framework is a way to map how different control areas of your compliance initiative are going to be affected by the results of those tests.
An organization may choose to define a compliance framework that extends an Oracle provided compliance framework. This is accomplished by creating a new compliance framework like the Oracle provided compliance framework and include new or existing compliance standards.Then each compliance standard is mapped to an appropriate framework hierarchy folder so that any violation against the standard is also mapped to that framework folder. Each folder in the framework represents one control area.
Reasons for Using Compliance Frameworks
There are a number of reasons for creating compliance frameworks including:
-
Mapping underlying IT violations to the regulatory and standard compliance controls used by your company so you can easily identify the compliance control areas that will be affected by the violations
-
Compliance auditing at compliance specification level
-
Auditing, security evaluation, and trend analysis
What Compliance Frameworks Can Do
A compliance framework can:
-
Represent industry-standard compliance control areas or can be created to match your internal frameworks in use.
Many companies may start by using an industry-standard framework, but modify it according to their own needs and auditing requirements.
-
Help in IT audits by identifying which compliance controls are at risk and may need compensating controls based on the violations. Without mapping your compliance checks to the control areas affected, it is hard to identify what the real impact would be in a compliance audit.
-
Since compliance frameworks can contain compliance standards of different types (Repository and Real-time monitoring), they provide a good way of grouping similar checks of different types for reporting purposes.
Usage Note
Evaluation Results for a repository rule may become invalidated if a compliance standard rule within a compliance framework is modified or deleted. Evaluation of a compliance standard always references the current compliance standard rule definition for each compliance standard rule within the compliance standard.
Operations on Compliance Frameworks
You can perform the following operations on a compliance framework:
- Creating a Compliance Framework
- Creating Like a Compliance Framework
- Editing a Compliance Framework
- Deleting a Compliance Framework
- Exporting a Compliance Framework
- Importing a Compliance Framework
- Browsing Compliance Frameworks
- Searching Compliance Frameworks
The following sections explain these operations.
Note:
Before you perform any of the operations on compliance frameworks, ensure you have necessary privileges. For example, when creating a compliance framework, ensure you have access to the compliance standards you will be including during the definition of the framework. See Roles and Privileges Needed for Compliance Features.Creating a Compliance Framework
To make the creation for the compliance framework easier, ensure that the compliance standards, which will be referred to by the compliance framework, are already defined in the Cloud Control. You can add system out-of-the-box and user-defined compliance standards to any hierarchical element of the compliance framework. If you do not define the compliance standards before hand, you must add them later.
To create a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- Click Create button.
- Provide the Name and Author and click OK.
- Once you have provided the information on the definition page, look at the options available when you right-click the name of the compliance framework (located at the top-left of the page). From this list you can create subgroups, include compliance standards, and so on.
- Click Save.
Usage Notes
-
Lifecycle status can be either Development or Production.
-
Development
Indicates a compliance framework is under development and that work on its definition is still in progress. While in development mode, all management capabilities of compliance frameworks are supported including editing of the compliance framework and deleting the compliance framework. Results of development compliance standards will NOT be viewable in target and console home pages, and the compliance dashboard.
Lifecycle status default is Development. It can be promoted to Production only once. It cannot be changed from Production to Development.
-
Production
Indicates a compliance framework has been approved and is of production quality. When a compliance framework is in production mode, its results are rolled up into a compliance dashboard, target and console home page.
Production compliance frameworks can only refer to Production compliance standards. A production compliance framework can be edited to add/delete references to production compliance standards only.
Lifecycle status cannot be changed from Production to Development.
-
-
All compliance frameworks with the same keyword will be grouped together when sorted by the Keyword column.
-
If you modify a repository that has been added to a compliance framework, either by editing the compliance standard directly, or by using Import to overwrite the compliance standard with new settings, the existing evaluations become invalid. That is, if this modified compliance standard was included in a compliance framework that was previously evaluated, and has evaluation results, these results are no longer viewable.
Adding a Compliance Standard to a Compliance Framework
Click on a framework folder element that you want to map a compliance standard to. Right click and select Add Standards to bring up a popup to allow you to select the standards to map to this folder.
Use the search criteria to minimize the number of compliance standards that display in the select list.
Once you make your selections, click OK. The framework hierarchy screen refreshes and shows your newly included compliance standards under the framework folder element.
Editing Importance
After you map the compliance standards that are to be part of the selected compliance framework folder, you can edit the importance of each compliance standard for this specific folder.
The importance impacts the way the compliance score is calculated for this compliance standard in this framework folder.
See Overview of Compliance Score and Importance for details on how this score is computed.
Creating Like a Compliance Framework
To create a compliance framework like another compliance framework, follow these steps:
Editing a Compliance Framework
Use the edit compliance framework feature to add new compliance standard rules to a compliance framework, or edit details of existing compliance frameworks, or remove compliance standards from the compliance framework.
To edit a compliance framework, follow these steps:
Usage Notes
-
Changing a compliance framework definition may impact trend analysis.
-
The compliance standards you add to a compliance framework may be system-defined and user-defined compliance standards as displayed on the Compliance Standard Library page.
-
If you modify a repository that has been added to a compliance framework, either by editing the compliance standard directly, or by using Import to overwrite the compliance standard with new settings, the existing evaluations become invalid. That is, if this modified compliance standard was included in a compliance framework that was previously evaluated, and has evaluation results, these results are no longer viewable. The compliance framework evaluation results will again become visible after the next evaluation happens. The new evaluation includes the changes to the compliance standard within the compliance framework.
-
The importance impacts the way the compliance score is calculated for this compliance standard in this framework folder.
-
A compliance standard can be added to more than one compliance framework, and can have a different importance when added to a different compliance framework. For example, you could have a compliance standard called Check Password Expired which flags user accounts with expired passwords. This compliance standard may be a member of two compliance frameworks: All System Passwords Secure and 30-day Password Validation. The All System Passwords compliance framework verifies a password's security, whereas the 30-day Password Validation compliance framework checks the date that this password was last set.
-
The Check Password Expired compliance standard could have Extremely High importance for the 30-day Password Validation compliance framework, since this check is warning users that their passwords are about to expire.
-
In the All System Passwords Secure compliance framework, the Check Password Expired compliance standard could have a Normal importance, and other added compliance standards that do security checks could have a higher importance within the compliance framework.
-
Deleting a Compliance Framework
To delete a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- Highlight the compliance framework you want to delete, click Delete button.
- Confirm that you want to delete the compliance framework by clicking OK.
Usage Notes
-
You can delete a single compliance framework or a list of compliance frameworks. When you delete a compliance framework, the associated metadata and evaluation results are also deleted.
-
YOU CANNOT DELETE COMPLIANCE FRAMEWORKS DEFINED BY ORACLE. These are indicated by the presence of a lock icon in front of the compliance framework name on the compliance framework listing page.
Exporting a Compliance Framework
The Export feature provides a mechanism for transporting user-defined compliance framework definitions across Management Repositories and Cloud Control instances. The export stores the definitions in an operating system file. Because the exported compliance framework definitions are in XML format, they conform to the Oracle Compliance Standard Definition (XSD) format. You can then change the definition of the compliance framework and re-import the generated compliance framework definitions into another Management Repository.
To export a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- Highlight the compliance framework you want to export.
- From the Actions menu, select Export.
- Provide the file name to which the compliance framework definition is to be exported. All leaf level rules and compliance standards are exported.
The system generates an XML representation of the compliance framework in the directory and file you specify.
Importing a Compliance Framework
Importing allows you to re-use a compliance framework that you already have, share framework definitions across multiple instances of Cloud Control, or enable offline editing of the framework.
Before you import a compliance framework, ensure the compliance framework to be imported is defined in a file. The file should be locally accessible to the browser you are using to access Cloud Control. Also ensure that you have privileges to access the compliance framework definition XML file to be imported.
Note:
When importing a compliance standard containing rules (or a framework containing standards) from the UI or command-line interface, import the xml file with <ComplianceContent> as root. This root file might have a list of rules, standards, frameworks, and standard groups.
This ensures that the framework and standard definition will be successfully imported. Also all associated targets will be re-evaluated based on the definition change made.
To import a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- From Actions menu, select Import.
- Provide the file name from which the compliance framework definition (as per Compliance Framework XSD) will be imported. Specify whether to override an existing definition if one already exists. Specify whether to import referring content as well where all leaf level rules and compliance standards are imported. Real-time monitoring facets are also imported for real-time monitoring type of rules.
- Click OK.
Browsing Compliance Frameworks
To browse a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- To view the details of a particular compliance framework, highlight the compliance framework and click Show Details.
Searching Compliance Frameworks
To search for a compliance framework, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Frameworks tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
Browsing Compliance Framework Evaluation Results
To browse compliance framework evaluation results, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Frameworks tab and then the Evaluation Results tab.
- Highlight the compliance framework and click Show Details to view the details of a particular compliance framework.
Results include the following:
-
Average compliance score for different targets evaluated for compliance standards referred to by the compliance framework
-
Count of target evaluations (critical, warning, compliant) for different compliance standards referred to by the compliance framework
-
Count of violations (critical, warning, minor warning) related to compliance standards referred to by the compliance framework
Searching Compliance Framework Evaluation Results
To search compliance framework evaluation results, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Frameworks tab and then the Evaluation Results tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
Browsing Compliance Framework Errors
To browse compliance framework errors, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Frameworks tab and then the Errors tab.
Usage Notes
The error may be an unexpected internal error or an error in the test.
Evaluation errors can often be due to configuration and installation issues. See the following manuals for information:
-
Oracle Enterprise Manager Cloud Control Basic Installation Guide
-
Oracle Enterprise Manager Cloud Control Advanced Installation and Configuration Guide
If the installation and configuration are correct and the errors persist, call Oracle for assistance.
Searching Compliance Framework Errors
To search for compliance framework errors, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Frameworks tab and then the Errors tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
Usage Notes
The error may be an unexpected internal error or an error in the test.
Evaluation errors can often be due to configuration and installation issues. See the following manuals for information:
-
Oracle Enterprise Manager Cloud Control Basic Installation Guide
-
Oracle Enterprise Manager Cloud Control Advanced Installation and Configuration Guide
If the installation and configuration are correct and the errors persist, call Oracle for assistance.
About Compliance Standards
A compliance standard is a collection of checks or rules. It is the Cloud Control representation of a compliance control that must be tested against some set of IT infrastructure to determine if the control is being followed.
Compliance standards are made up of the following in a hierarchical structure:
- Compliance standard rules
- Rule folders that can include nested rule folders and individual compliance standard rules.
Rule Folders are hierarchical structures that contain compliance standard rules. A rule folder has an importance attribute that denotes the importance of the rule folder relative to its siblings at the same level. This importance is considered when determining compliance scores being rolled up from other sibling rule folders. A certain rule folder may have multiple tests that occur, in this way a certain test can be given more weight than other tests.
- Included compliance standards. A compliance standard can include other compliance standards.
Figure 27-10 Compliance Standard Definition
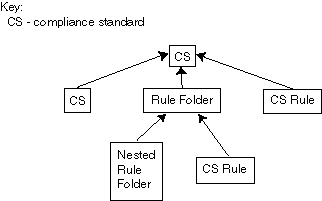
Description of "Figure 27-10 Compliance Standard Definition"
What Compliance Standards Can Do
- Can represent industry-wide standards. A compliance standard is applicable to a single target type.
- Be used as a reference configuration or a certified configuration
- Be a collection of compliance standard rules describing best practices in an enterprise
For example, when a target fails to adhere to a compliance standard, the target is not in compliance with the compliance standard.
Accessing Compliance Standards
The compliance standards, including those provided by Oracle, are available on the Compliance Standard Library page. To access this page, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
To view the compliance standard rules associated with the compliance standard, click the name of the compliance standard and click Show Details. Once the Compliance Standard Detail page appears, right click the name of the standard located at the top left of the page, and select either Collapse, Expand All Below or Collapse All Below.
Note: The compliance standards defined by Oracle cannot be changed. However, you can create a standard similar to the one provided by Oracle by using the Create Like feature.
General Usage Notes for Compliance Standards
You can override an existing compliance standard by checking the Overwrite existing compliance standards check box. As a result, evaluations of compliance standards require that the compliance standard is associated to one or more targets.
- For repository compliance standards, evaluation starts after the standard is associated with a target based on data collected from that target in the Management Repository.
- For WebLogic Server compliance standards, evaluation happens when the Management Agent-side evaluation metric is refreshed. The refresh occurs once every 24 hours for Oracle WebLogic Domain, Oracle WebLogic Java EE Server, and Oracle WebLogic Cluster targets.
- For Real-time Monitoring compliance standards, monitoring at the Management Agent starts when a compliance standard is associated to a target. A violation occurs when an observation bundle contains at least one observation that is unauthorized
Usage Note Specific to Repository Rules
If you manually type a WHERE clause in the compliance standard rule XML definition, then the < (less than) symbol must be expressed as <, to create a valid XML document. For example: <WhereClause>:status < 100</WhereClause>
Example of How to Set Up Compliance Standards for Auditing Use
For auditors to verify that database targets are in compliance with the compliance frameworks, the Cloud Control structure needs to be defined. The steps to provide this structure includes the following:
- Super Administrator creates three Cloud Control users: Compliance Author, IT Administrator, and Compliance Auditor.
- Super Administrator assigns the appropriate roles and privileges to the Compliance Author and IT Administrator.
- Super Administrator assigns the same target privileges to IT Administrator and Compliance Auditor.
- Compliance Author logs in to Cloud Control and views Oracle provided compliance frameworks, compliance standards, and compliance standard rules. The author then enables and disables the appropriate compliance standard rules and creates new compliance standard rules.
- IT Administrator logs in to Cloud Control and associates the targets for which he has target privileges with the appropriate compliance standards.
- IT Administrator sets up the correct configuration parameters and settings for the compliance frameworks, compliance standards, and compliance standard rules for a particular target. The administrator then creates a monitoring template from this target and applies it to the other targets, to which he has privileges, that require compliance standards.
- Compliance Auditor logs in to Cloud Control to view the compliance dashboard, violations and errors at the Enterprise level, for which he has view privileges, and at each target level. The auditor would then take the necessary actions to rectify the errors and violations.
Operations on Compliance Standards
You can perform the following operations on a compliance standard:
The following sections explain these operations.
Note: Before you perform any of the operations on compliance standards, ensure you have necessary privileges. For example, when creating a compliance standard, ensure you have access to the compliance standard rules you will be including during the definition of the compliance standard. See Roles and Privileges Needed for Compliance Features .)
Creating a Compliance Standard
You can use the compliance standards provided by Oracle, for example, Security Configuration for Oracle Database, or create your own standard.
Before creating a compliance standard, ensure the compliance standards and compliance standard rules, which will be referred to by the compliance standard, are defined in the Management Repository.
To create a compliance standard, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click the Compliance Standards tab.
-
Click the Create button. You will prompted for the Name, Author, target type to which the standard is applicable., and the standard type. The standard types are:
-
Repository
-
Real-time Monitoring
-
Agent-side
Click Continue.
-
-
On the resulting Properties tab, provide the property values.
Click Add to either add a keyword by which this standard is identified or use an existing keyword.
-
To further define the compliance standard, right-click the name of the compliance standard located at the top left of the page. From this menu, you can create rule folders, add rules, and included compliance standards.
By using rule folders, you can view the summary of results, categorized by the targets that were evaluated against the selected rule folder and the Compliance Standard Rules evaluated for the selected rule folder.
-
Click Save.
Once you define the compliance standard, associate the standard with a target and define the target type-specific settings.
-
While on the Compliance Standards Library page, ensure the correct compliance standard is highlighted.
-
Click the Associate Target button.
-
On the Target Association for Compliance Standard page, click Add to choose the target to be evaluated against the standard.
-
In the Search and Select: Targets popup, choose the appropriate targets.
-
Click Select.
After you associate the targets with the compliance standard, you can edit the parameters associated with the target.
-
While on the Target Association for Compliance Standard page, click Edit.
-
On the Customize Compliance Standard Parameters page, change the parameters as needed.
Note:
You can also associate a compliance standard with a target from the target home page. At the top left of the target's home page, right click the name of the target. On the resulting menu, select Compliance, then select Standard Associations.
Including a Compliance Standard into Another Compliance Standard
Use the Include Compliance Standard page to select one or more compliance standards to be included into the compliance standard. This list is prefiltered by the target type of the compliance standard.
To include a compliance standard into another compliance standard:
Usage Notes
-
Because compliance standards are hierarchical, the top node in the tree is known as the root node.
-
When you create a compliance standard, the version is 1.
-
Lifecycle status default is Development. It can be promoted to Production only once. It cannot be changed from Production to Development.
-
Development
Indicates a compliance standard is under development and that work on its definition is still in progress. While in Development mode, all management capabilities of compliance standards are supported including complete editing of the compliance standard, deleting the compliance standard, and so on. However, while the compliance standard is in Development mode, its results are not viewable in Compliance Results nor on the target or Cloud Control home page.
-
Production
Indicates a compliance standard has been approved and is of production quality. When a compliance standard is in production mode, you have limited editing capabilities, that is, you can add references to production rules, and you can delete references to rules ONLY from a compliance standard. All other management capabilities such as viewing the compliance standard and deleting the compliance standard will be supported. Results of production compliance standards are viewable in target and console home pages, and the compliance dashboard. Production compliance standards can only refer to production compliance standards and production compliance standard rules.
Once the mode is changed to Production, then its results are rolled up into compliance dashboard, target home page, and Cloud Control home page. Production compliance standards can only refer to other production compliance standards and production compliance standard rules. A production compliance standard can be edited to add and delete references to production compliance standards and production compliance standard rules only.
-
Creating Like a Compliance Standard
To create a compliance standard like another compliance standard, follow these steps:
Editing a Compliance Standard
You can customize compliance standards by editing the existing compliance standard rule settings. You can change the added rules' importance for the compliance score calculation, prevent template override, override default parameter values (when possible), and exclude objects from a compliance standard rule's evaluation (when possible).
Note: You cannot edit an Oracle provided compliance standard, that is, a compliance standard defined by Oracle.
To edit a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- Highlight the standard you want to edit and click the Edit button.
- Update the parameters as needed.
- Click Save.
Deleting a Compliance Standard
Before you delete a compliance standard, ensure the compliance standard is not in use by a compliance framework. You must remove any references to the compliance standard in all compliance frameworks.
Note: You cannot delete an Oracle provided compliance standard, that is, a compliance standard provided by Oracle.
To delete a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- Highlight the compliance standard you want to delete, click Delete button.
- Confirm that you want to delete the standard by clicking OK.
Exporting a Compliance Standard
The Export feature provides a mechanism for transporting user-defined compliance standard definitions across Management Repositories and Cloud Control instances. The export stores the definitions in an operating system file. Because the exported compliance standard definitions are in XML format, they conform to the Oracle Compliance Standard Definition (XSD) format. You can then change the definition of the compliance standard and re-import the generated compliance standard definitions into another Management Repository.
Before you export a compliance standard, ensure that you have privileges to access the compliance standard to be exported.
To export a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- Highlight the standard you want to export.
- From the Actions menu, select Export.
- Provide the file name to which the standard definition is to be exported. All leaf level rules and compliance standards are exported.
- The XML representation of the compliance standard is generated. The file is located in the directory you specify.
Importing a Compliance Standard
The Import feature uploads an XML-based compliance standard definition file containing definitions of a single user-defined compliance standard or a list of user-defined compliance standards. This upload creates a new user-defined compliance standard or a list of user-defined compliance standards. This compliance standard must have been previously exported.
The compliance standard xml definition must comply with the compliance standard XML Schema Definition (XSD) as defined in User-Defined Compliance Standard XML Schema Definition.
Before importing a compliance standard, ensure the compliance standard to be imported is defined in a file. The file should be locally accessible to the browser you are using to access Cloud Control. Also ensure that you have privileges to access the compliance standard definition XML file to be imported.
To import a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- From the Actions menu, select Import.
- Provide the file name from which the compliance framework definition (as per Compliance Framework XSD) will be imported. Specify whether to override an existing definition if one already exists. Specify whether to import referring content as well.
- Click OK.
You can override an existing compliance standard by checking the Overwrite existing compliance standards check box. As a result:
-
If you override a compliance standard, the override deletes all target and template associations, as well as evaluation results for that compliance standard.
-
If the overwritten compliance standard is part of a compliance framework, the compliance standard is updated in the compliance framework. However, the evaluation results for that compliance standard within the compliance framework are invalidated.
Browsing Compliance Standards
To browse a compliance standard, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- To view the details of a particular standard, highlight the standard and click Show Details.
Searching Compliance Standards
To search for compliance standards, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
Browsing Compliance Standard Evaluation Results
To browse compliance standard evaluation results, follow these steps:
Searching Compliance Standard Evaluation Results
To search for compliance standard evaluation results, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Standards tab and then the Evaluation Results tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
Browsing Compliance Standard Errors
To browse compliance standard evaluation errors, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Standards tab and then the Errors tab.
Searching Compliance Standard Errors
To search for compliance standard errors, follow these steps:
- From the Enterprise menu, select Compliance, then select Results.
- Click the Compliance Standards tab and then the Errors tab.
- In the Search portion of the page, provide criteria to use to narrow the search.
- Click Search.
Usage Notes
-
Use the Evaluation Errors page to view the errors that occurred as a result of metric collection, as well as those that occurred during the last evaluation.
-
Use the search filter to view only those evaluation errors that meet a set of search criteria that you specify.
-
Click the message in the Message column to decide what your course of action should be to resolve the error.
-
On initial display, the Evaluation Errors page shows all the evaluation errors.
-
Normally the results of an evaluation overwrite the previous evaluation's results. However, in the case of evaluation failure or data provider collection failure, the previous results are left untouched.
Once the underlying problem is fixed, the error is no longer reported.
Example of Search Filter
By default, all the evaluation errors in your enterprise configuration appear in the results table. However, you can specify a set of search criteria and then perform a search that will display only the evaluation errors that meet those criteria in the results table.
For example, if you choose Host in the Target Type list, contains in the Target Name list, and "-sun" in the adjacent Target Name text field, and then click Go, Cloud Control displays, in the results table, only the compliance standard rule evaluation errors for the hosts that contain "-sun" in their names.
Associating a Compliance Standard with Targets
After you create a compliance standard, you can associate the standard with one or more targets. As part of the association, you can customize parameters, that is, the importance of the standard in relation to the target, status of the compliance standard evaluation, reason for changing the evaluation status, and the thresholds.
Before you associate a compliance standard with a target, ensure you have privileges to access the targets you want to associate compliance standards to.
To associate a compliance standard with a target, follow these steps:
To further customize the evaluation of a compliance standard against a target, you can alter compliance standard parameters: importance, critical threshold, and warning threshold. Customizations can also be made on the compliance standard rules used within the compliance standards. For example, for the Secure Ports compliance standard rule, DFLT_PORT is an override parameter. You can change the default value of the port. You can also exclude objects from the evaluation, for example a particular port from the evaluation.
Note: For real-time monitoring, you can change parameters that are used in facet patterns. You can also change Automatic Change Management reconciliation settings.
By changing critical and warning thresholds, you signify how the Compliance standard score event is generated. For example, if the actual score is less than the critical threshold, then a critical score event is raised.
Best Practices
You can perform compliance association in two ways: for testing and editing, and production and mass associations.
-
For testing and editing a standard/target and standard rule, or rule folder/target association settings purposes, associate the target with a compliance standard as previously described in this section.
Using the Compliance UI, you can:
-
Test the association and remove it after testing is complete.
-
Edit the association for importance, evaluation status, and thresholds.
Note: You cannot edit an association using the Administration Groups and Template Collections page.
-
-
For production and mass associations, associate the target using the Administration Groups and Template Collections page:
From the Setup menu, select Add Target, then select Administration Groups. Click the Associations tab.
Because each Administration Group in the hierarchy is defined by membership criteria, a target is added to the group only if it meets the group's membership criteria. Therefore, when a target is successfully added to a group, it is automatically associated with the eligible compliance standards for that group. This makes it easier to associate a target to a large number of compliance standards.
Associating a Compliance Standard with a Group Target
Before you associate a compliance standard with a group target, ensure you have privileges to access the group target you want to associate the compliance standards to. For more information see: Roles and Privileges Needed for Compliance Features
Perform the following steps:
Viewing Real-time Monitoring Compliance Standard Warnings
When you associate a real-time monitoring compliance standard to targets, there is a chance that there are setup steps that were not followed on the target to enable real-time monitoring or there could be inconsistency with the configuration. Any warnings will be shown on the Associate Targets screen. This screen is reached by selecting a compliance standard and selecting Associate Targets button. If there are any warnings, there will be a warning icon with a link above the table of target associations. Clicking on this link will take you to a screen that lists all current warnings for this compliance standard.
All warnings can be fixed by correcting some configuration problem on the host/target you are monitoring or by fixing rule/facet content. Once the underlying problem is fixed, these warnings will be cleared automatically.
This list of warnings is also available on the Real-time Observations page (from the Enterprise menu, select Compliance, then select Real-time Observations) where you can pick one of three types of reports to view your observations. The bottom half of the screen shows all active warnings across all targets and compliance standards related to real-time monitoring.
Enabling Security Metrics
Because security collections are disabled by default, they must be enabled before using security features like security compliance standards, reports, and so on. To enable Security metrics, follow these steps:
- From the Enterprise menu, select Monitoring, then select Monitoring Templates.
- In the Search area, select Display Oracle provided templates and Oracle Certified templates and click Go.
- Select Oracle Certified-Enable Database Security Configuration Metrics and click Apply.
- In the Destination Targets region on the Apply Monitoring Template Oracle Certified-Enable Database Security Configuration Metrics: General page, click Add.
- On the Search and Select: Targets page, select the database instances in which you are interested and click Select.
- In the Destination Targets region of the Apply Monitoring Template Oracle Certified-Enable Database Security Configuration Metrics: General page, select the database instances in which you are interested and click OK.
After you click OK, a confirmation message on the Monitoring Templates page appears.
Considerations When Creating Compliance Standards
A compliance standard will refer to one or more Compliance Standard Rules. When creating a compliance standard, the standard should be granular enough that it can be appropriately mapped to one or more related Compliance Frameworks. For example, consider this Compliance Framework structure that exists in the Oracle Generic Compliance Framework:
-
Change and Configuration Management (compliance framework subgroup)
-
Database Change (compliance framework subgroup)
-
Configuration Best Practices for Oracle Database (compliance standard)
-
Configuration Best Practices for Oracle RAC Database (compliance standard)
-
Configuration Best Practices for Oracle Pluggable Database (compliance standard)
-
-
Many compliance standards will exist that should be mapped to this part of the Compliance Framework structure, each with their own rules to address this specific requirement. One may check that configuration settings are set properly. Another may be used to check in real-time if anyone changes a configuration setting.
In this example, the "Database Change compliance framework subgroup" can relate to many different types of targets. Oracle Database, Oracle RAC Database, and Oracle Pluggable Database all have their own types of configurations that all need to be secured. Any Standards created to monitor these target-specific configurations would map to the same "Database Changes subgroup".
If compliance standards are structured in a granular way so that they can map to existing and future compliance frameworks, then violations in a rule can be rolled up to impact the score of the compliance framework properly.
About Compliance Standard Rule Folders
Rule Folders are optional hierarchical structures used to group similar compliance standard rules within a compliance standard. You can add individual compliance standard rules to a compliance standard, or group them if you have a large number of rules in a standard. A compliance standard rule can be added to multiple Rule Folders within a compliance standard, each with different importance settings. Rule Folders can be nested within a compliance standard.
A rule folder has an importance attribute that denotes the importance of the rule folder relative to its siblings at the same level. This importance is considered when determining compliance scores being rolled up from other sibling rule folders. A certain rule folder may have multiple tests that occur, in this way a certain test can be given more weight than other tests.
The following topics address compliance standard rule folders:
Creating Rule Folders
To create a rule folder, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standards tab.
- On the Compliance Standard Library page, highlight the compliance standard and click Edit.
- On the Properties page, right-click the name of the compliance standard. The name of the standard is located in the top-left corner of the page.
- Select Create Rule Folder.
- Type the name of the folder and click OK.
- On the Properties page, provide a description, ReferenceUrl, and importance. See Overview of Compliance Score and Importance.
Managing Rule Folders in a Compliance Standard
After you create a rule folder and populate it with compliance standard rules, you can perform the following actions on the folder:
-
Edit the tree structure by re-ordering the Rule Folder, Rule Reference, and Compliance Standard Reference nodes in the tree or by deleting any of these nodes.
-
Select any node (except the top-level Compliance Standard node) object and then click Remove menu item from context menu. The Remove option is disabled on the root node. You can also select multiple objects and click Remove to delete multiple nodes.
About Compliance Standard Rules
A compliance standard rule is a test to determine if a configuration data change affects compliance. Based on the result of the test, a compliance score is calculated. These rule compliance scores are rolled up to compute the compliance standard score and then this score can be rolled up and reported along with the compliance framework scores.
Types of Compliance Standard Rules
There are three types of compliance standard rules are:
-
Used for detecting configuration problems on the agent. This enables the implementation of the Security Technical Implementation Guide (STIG) security specifications. Agent-side rules generate violations for a target which is based on the results data collected for the underlying configuration extension target.
-
Configuration Consistency rule
Determines the consistency of targets of similar target types within a composite target. For example, a user has a Cluster Database made up of 15 databases. He can use the Cluster Database Comparison Template for configuration consistency to flag databases that may have changed within the cluster.
-
Configuration Drift rule
Determines the deviation of targets of similar target types. For example, a user has 10 databases that he is monitoring. He needs to ensure that the Initialization Parameter File Permission compliance standard rule is the same across all the databases. This deviation can occur when the database configuration has been updated.
-
Manual rule
Enables you to account for checks that cannot be performed automatically, thus allowing you to account for these types of checks in the compliance framework.
For example, a common security check is "To ensure secure access to the data center". When a standard is associated to a target, each manual rule will have one violation. A user must manually attest to the positive status of the rule. In other words, a person responsible for the task ensures he has performed the task. The compliance framework records when and who clears the violation of the manual check so it can be reported.
-
Missing Patches rule
Used for detecting patches that have not been applied to the appropriate targets. This rule generates violations which appear on the compliance results UI and subsequent compliance dashboard regions. A rolled up violation count appears on the dashboard regions. The user can drill down to examine violation details and then correct the issue by applying the missing patches to the appropriate targets.
-
If the rule is based on a list of patches, then the rule checks if none of the patches are applied to the target. If any of the patches are applied, then no violation is generated. If none of the patches are applied, then one violation is generated listing the patches that are not applied.
-
The patch numbers can refer to Oracle recommended patches or manually entered patches.
-
After a patch is applied, the corresponding ORACLE_HOME configuration is uploaded. Oracle then reevaluates all associated missing patches rule for the target.
-
After you create the Missing Patches rule, you can add missing patches rules to compliance standards of type Repository. You can then associate the standard to targets by selecting a standard, and clicking the Associate Target button. Upon association, the missing patch rule will be evaluated on the applied targets.
-
If a standard with the missing patches rule is associated to a group, when new targets are added to the group, the new target is automatically evaluated for missing patches.
-
-
Real-time Monitoring rule
Monitors operating system and database level entities that store configuration data. Real-time monitoring rules define the entities to monitor, user actions to watch for, and any types of filters to apply to the monitoring. Monitoring can be filtered by: when changes occurred, who made the changes, and what process made the changes.
The real-time monitoring rule definition includes facets that are used to determine what is important to monitor for a given target type, target properties, and entity type. A facet is a collection of patterns that make up one attribute of a target type. For example, you may choose to define a facet that lists all of the critical configuration files for the Host target type. These configuration files would be the ones that, if changed, would most likely result in instability of the host. You may also create a facet that lists all users which are DBA users.
The real-time monitoring rule can be part of a compliance standard that is associated with one or more targets. The monitoring can occur on any operating system level entity, for example, file, process, user, registry, and so on. Real-time monitoring rules can additionally specify whether observations captured by the rule are automatically reconciled. This reconciliation determines whether the actions observed were authorized or not.
Change Request Management reconciliation compares open change requests to actions performed on targets. If there is a match of expected actions to actual actions, then those actions are authorized, otherwise they are unauthorized. Authorizations can also be done manually. All observations are captured and bundled by rule, target and user. Attributes can be set on the frequency of observation data collection.
-
Used to perform a check against any metric collection data in the Management Repository.
Used for checking the configuration state of one or multiple targets. A rule is said to be compliant if it is determined that the configuration items do in fact meet the desired state and the rule test failed to identify any violations. Otherwise, a rule is said to be non-compliant if it has one or more violations. The data source that is evaluated by a compliance standard rules test condition can be based on a query against the Cloud Control Management Repository. A compliance standard rules test condition can be implemented using a threshold condition based on the underlying metrics (or queries) column value or SQL expression or a PLSQL function. To use a rule, it must be associated to one or more compliance standards. The compliance standard then will be associated to one or more targets. This effectively enables this rule to be evaluated against these targets.
Operations on Compliance Standards Rules
The following sections explain the operations you can perform on compliance standard rules.
- Creating a Repository Compliance Standard Rule
- Creating a Real-time Monitoring Compliance Standard Rule
- Creating an Agent-side Rule
- Creating a Manual Rule
- Creating Like a Compliance Standard Rule
- Editing a Compliance Standard Rule
- Deleting a Compliance Standard Rule
- Exporting a Compliance Standard Rule
- Importing a Compliance Standard Rule
- Browsing Compliance Standard Rules
- Searching Compliance Standard Rules
Note:
Before you perform any of the operations on compliance standard rules, ensure you have the necessary privileges. For more information see: Roles and Privileges Needed for Compliance Features.Creating a Repository Compliance Standard Rule
To create a repository compliance standard rule to check if a target has the desired configuration state based on collected configuration data, follow these steps:
Additional Notes for Repository Rules
-
All rules are visible in the global rule library and are visible to all users.
-
Once the compliance standard rule is created, it is not automatically evaluated. Users must associate a rule to a compliance standard before it can be used. Only when a compliance standard is associated with one or more targets will a rule evaluation occur. Rules cannot be evaluated directly.
-
One rule can be associated to multiple compliance standards.
-
Various attributes of a rule can be customized through the compliance standard this rule is associated with. These customizations occur in the Compliance Standard screens. One of these attributes that can be customized per compliance standard is the importance of the rule in relationship to this standard.
-
Because the user-defined compliance standard rule is defined by a privileged user, only privileged users can modify the compliance standard rule. Violation results are available to all users.
-
To share this user-defined compliance standard rule with other privileged users, provide the XML schema definition (using the Export feature) so they can import the compliance standard rule to their Management Repository.
-
You can minimize scrolling when reading the Description, Impact, and Recommendation information by restricting the text to 50 characters per line. If more than 50 characters are needed, start a new line to continue the text.
-
Look at the context-sensitive help for information for each page in the Compliance Standard Rule wizard for specific instructions.
-
If you manually type a WHERE clause in the compliance standard rule XML definition, then the < (less than) symbol must be expressed as <, to create a valid XML document. For example:
<WhereClause>:status < 100</WhereClause>
Creating a Real-time Monitoring Compliance Standard Rule
To create a Real-time monitoring compliance standard rule to monitor for user actions that occur on a target such as file changes, user access, and process activity, follow these steps:
-
From the Enterprise menu, select Compliance, then select Library.
-
Click the Compliance Standard Rules tab.
-
Click the Create button.
-
In the Create Rule popup, select Real-time Monitoring type.
-
Click OK.
-
On the next screen, you are asked to fill out several key attributes of the rule:
-
Rule Name
Provide a unique name for the rule.
-
Compliance Rule State
Set whether the state of this rule is development or production. Development means that the rule is still being defined or tuned and is not yet ready to be used on targets yet. After you promote a rule to production, you cannot change it back to development.
-
Severity
The rule can have a severity level, which could be Critical (serious issue if this rule is violated), Warning (not a serious issue if violated), or Minor Warning (a minor issue if violated). Severity impacts the compliance score along with the importance that may be set for this rule when it is added to a compliance standard.
-
Applicable To
Target type this rule works against.
-
Entity Type
A type of object that is part of a target being monitored. For example, for the Operating System (OS), entity type may be OS File, OS Process, or OS User. For Database, an entity type may be Database Table, Database Function, Database Procedure, or Database User.
-
Target Property Filter
You can specify specific target properties that determine which targets this rule can work against when it is associated with a compliance standard. These properties are Operating System, Target Lifecycle State, Version, and Platform. When you specify a target property filter for this rule, for instance for Linux OS, it will only be applicable to targets on Linux Operating System.
-
Description
Description of the rule
-
Rationale
Text describing what this rule is checking and what the effect of a violation of this rule may be.
-
Details URL
URL to a document that describes the compliance control in more details. Many times these documents may be stored in a content management system.
-
Message
The message that will be used for the violation when an observation is determined to be unauthorized.
-
Clear Message
The message that will be used for a previous violation after it is cleared.
-
Keywords
Keywords can be assigned to a rule so that you can control how data is organized in various reports.
For additional information, see Importance of Target Property Filters for a Real-time Monitoring Rule.
-
-
Click Next.
-
On the next page, you select the facets that are to be monitored for this rule. You can include facets that are already defined or create a new facet inline with this rule creation. A facet is simply a list of patterns to monitor. For instance, a list of files, user names, processes, and so on. Facets are discussed later in the section Real-time Monitoring Facets.
-
Click Next after including existing facets or adding new facets.
-
On the next screen, you will choose the actions you want to monitor. The actions you choose will depend on what entity type you chose for the rule. For instance, for OS File Monitoring, you can watch for actions such as file create, modify, delete, rename, and so on. For OS User monitoring, you can watch for actions such as login, logout, SU, SSH, and so on. You must choose at least one action to monitor for a rule.
For additional information, see Selecting the Types of Actions You Want to Monitor.
-
Click Next.
-
On the next screen, you can optionally configure filters for monitoring. Filters are used to limit when or under what conditions you want an action to be observed. For instance, if you are monitoring a file facet FILES1, you can add a filter so that only file changes done by a specific list of users are captured, or if the change happens during a certain time window, or a certain process is used to modify the file. Filters are also facets, just of different entity types. If you are monitoring OS File entity type, you can apply an OS User, OS Process, or Time Window facet as a filter. You can include an existing facet, or create a new facet inline with the rule creation. If you cancel the rule wizard, any facet you created inline will still exist in the facet library.
For additional information, see Using Facets as Filters in Real-time Monitoring Rules.
-
Click Next.
-
On the next screen, you can configure several settings related to how the observations are handled when detected at the Management Agent.
-
Authorize Observations Manually
-
Authorize Observations Automatically using Change Request Management System
-
Collection Settings
For additional information, see Configuring Audit Status and Controlling Observation Bundle Lifetimes.
-
-
Click Next.
-
On this screen you can review the settings of the rule.
-
Click Finish to save the rule and return to the rule listing page.
Importance of Target Property Filters for a Real-time Monitoring Rule
When creating a rule, you must choose a target type for the rule. Since the Real-time monitoring capabilities on the Management Agent have some dependencies on operating system and versions of operating systems, you must be allowed to set the criteria for a rule. The target may be different on a target type, so patterns in the facets may be different. For instance, Oracle Database on Microsoft Windows is not the same as it is on the UNIX operating system.
If target property filters are not set, all rule options are available then at target-cs association time, if a target's settings do not match, then that rule and facet is ignored. If you only set, for example, the platform name, but not version, then only the options that are common across all versions of the platform are available.
The list of facets that are selectable when creating a rule are filtered by the target properties that are set when a facet is created. For instance if you have a facet, FACET1, that works on Linux or HPUX and you create a rule for Windows, FACET1 will not be available to select for your rule. This applies both when selecting the monitoring facet or using a facet as a filter. However if you create a rule for either Linux or HPUX, FACET1 will be available because the criteria for the rule at least overlapped with that of the facet.
Using Facets as Filters in Real-time Monitoring Rules
When creating a rule, facets can be used in two ways. The first is to use the facet to specify what entities to monitor in the rule. The second is to use the facet as a filter to apply on top of activities detected by the Management Agent.
You can use the same facet as a monitoring facet in one rule and a filtering facet in another rule. The benefit is once you define a collection of patterns, for example to define your administrative users, you can use that collection in many ways without having to redefine the collection again.
Filters in rules are set up to reduce the observations that are captured and reported to Cloud Control. If there are no filters defined, then all observations related to the monitoring facet(s) selected in the rule are captured. When selecting a facet as a filter, the default is to only include observations that have attributes that match. The following example IT compliance control demonstrates an example for the filtering:
IT Control: Monitor all changes to critical OS configuration files by administrators during production hours.
To implement this IT control, you can create a compliance standard rule with the following:
-
Create a rule and select the file facet "Critical OS configuration files" for the monitoring facet that has patterns covering all critical OS configuration files.
-
Select "content change" as the action types to capture.
-
Add an OS Users filter selecting facet "Administrators" that lists patterns describing all of the OS user accounts that are considered administrators.
-
Add a Time Window filter selecting facet "Production Hours" that lists patterns describing the times of the week that are considered to be production hours. For example, Every day 4am-2pm PST.
When the Management Agent sees any content change to the patterns in Critical OS configuration files, it will only report these changes back to Cloud Control if the change happened during production hours and if any user described in the Administrator's facet is the one making the change. Filters can also be inverted to monitor anyone not in the administrators group or for changes outside of production hours.
More details on how to use filters is described in the section above on Creating a Real-time monitoring rule.
Configuring Audit Status
Each observation can have an audit status. This audit status can change over time and be set manually or automatically by Cloud Control. The way audit statuses are managed is configured when creating or editing a real-time monitoring rule.
When creating a rule, on the settings page of the wizard, the user has an option of choosing whether all observations detected against this rule will get their audit status manually from the user or automatically using connector integration with a Change Request Management server.
When the user chooses to manually set audit status in a rule, there are two options available:
-
Default Audit status can be set so that all observations that are found against this rule are by default unaudited, authorized, or unauthorized. Unaudited is the same as saying they have not been reviewed and there has been no determination of whether the observation is good or bad.
-
The user can choose an informational event during manual authorizations. This is used to create a new event of informational class in the Incident Manager when a new observation bundle occurs. Based on this event, an event rule could be created to send a notification based on the observation bundle or perform any other action the Incident Manager can perform.
If the user chooses to use automatic reconciliation using a Change Request Management server, then steps must be taken to set up the Cloud Control connector for Change Management. For more information, see Additional Setup for Real-time Monitoring.
Once the connector has been configured, there will be a drop down in this settings step of the rule creation wizard to choose which connector to use for this rule. Based on attributes of the observation and observations defined in any open change requests, the observation will be automatically determined to be authorized if there are open matching change requests, otherwise it will be considered unauthorized.
When using automatic reconciliation, an additional option is available to specify that the details of any authorized observations should be annotated back into the change request in the Change Request Management Server that allowed the observation to be authorized.
Multiple observations can belong to the same Observation Bundle. Even though an observation is part of group, the determination of authorized versus unauthorized is done for a single observation, not at the group level. If a group has at least one observation that is marked as "unauthorized", then the group is considered to be a "violation" and an event or incident can be raised for this group violation.
Controlling Observation Bundle Lifetimes
Observation bundles are logical groupings of observations that occur over a relatively short period of time against the same rule on the same target and by the same user. The last three factors cannot be configured by the user because they will be how the Management Agent groups observations before sending them back to the Cloud Control server.
The user creating the rule however does have three variables that they need to be able to configure:
-
Idle timeout: The amount of time after the user has no more activity from their last activity against a specific rule on a given target. The use case for this is that a user logs into a server, starts making a few file changes and then no more file changes are made after 15 minutes. This 15 minute waiting period is the idle timeout. After this idle timeout period is reached, the current observation bundle is closed and sent to the Cloud Control server. The next time a new observation is detected, a new group will be started and the process starts over.
-
Maximum lifespan of a group: If a user were to set the idle timeout to 15 minutes and a user on a host was making one file change every 10 minutes for an indefinite period of time (say through a script or even manual), the observation bundle will never close and therefore never get sent to the Cloud Control server for reporting/processing. Setting the maximum lifespan of a group tells the Management Agent to only allow a group to accumulate for a maximum specific time. For example, this maximum lifespan may be 30 minutes or an hour.
-
Maximum number of observations in a bundle: If a rule is being triggered because of an activity that is causing a lot of observations to be detected, it may be desirable for the user to not bundle every observation together if there are too many. Bundles have a management lifecycle to them where observations can be set to authorized/unauthorized, after they arrive at the Cloud Control server. Having observation bundles with tens of thousands of observations could become hard to manage.
The user creating a rule cannot choose to turn off bundling, but if they desired to reduce delays in observation reporting to Cloud Control server, they could set the idle timeout and maximum lifespan of a bundle to be lower.
The event/incident subsystem will track only the observation bundles, not each individual observation. If one observation is marked as unauthorized, then the entire bundle will be in violation. This bundle is the entity that will be tracked by the Incident Management event.
Observation bundles are built at the Management Agent and will only be sent to the Cloud Control server when the bundle is complete according to the above criteria. In most compliance use cases, this is acceptable because you will not need to view the results immediately. Capturing and bundling results together is more important for understanding what is happening and making observations easier to manage.
When an observation becomes part of two or more bundles on the Management Agent because the same facet is used in multiple rules or multiple targets on the same host monitor the same facet with shared entities, then whenever the first bundle either hits its ending criteria (idle timeout, group maximum life, or maximum group entries), then all of the bundles containing these shared observations are closed at the same time.
To control observation bundle lifetimes, see the section above on how to create Real-time Monitoring Rules and set the appropriate settings on Settings page of the rule creation wizard.
Selecting the Types of Actions You Want to Monitor
When creating a rule, you can decide which types of observations or user actions are important to be monitored and reported back to Cloud Control. The Management Agent has a specific set of observations that are possible for each entity type. Some options may be specific to certain operating system platforms or versions. You can select one or more of these options.
The observation types that you may be able to select can also be limited by the target properties/criteria selected for the rule. For instance, some operating systems may not have every monitoring capability for files. When building the list of available observation types available, the target type, entity type, and target properties are all taken into consideration to come up with the resulting available observation types.
To select the type of observations you want to monitor in a rule, follow these steps:
Additional Notes for Real-time Monitoring Rules
-
All Rules are visible in the global rule library and are visible to all users.
-
Once the compliance standard rule is created, it is not automatically evaluated. Users must associate a rule to a Compliance Standard before it can be used. Only when a compliance standard is associated with one or more targets will a rule evaluation occur. Rules cannot be evaluated directly.
-
One rule can be associated to multiple compliance standards.
-
Various attributes of a rule can be customized through the compliance standard this rule is associated with. These customizations occur in the Compliance Standard screens. One of these attributes that can be customized per compliance standard is the importance of the rule in relationship to this standard.
-
Because the user-defined compliance standard rule is defined by a privileged user, only privileged users can modify the compliance standard rule. Violation results are available to all users.
-
To share this user-defined compliance standard rule with other privileged users, provide the XML schema definition (using the Export feature) so they can import the compliance standard rule to their Management Repository.
-
You can minimize scrolling when reading the Description, Impact, and Recommendation information by restrict the text to 50 characters per line. If more than 50 characters are needed, start a new line to continue the text.
-
Look at the context-sensitive help for information for each page in the Compliance Standard Rule wizard for specific instructions.
-
If you choose to monitor OS File entity type, you will notice one action type "File Content Modified (successful) - Archive a copy of the file [Resource Intensive]". If you select this option, every time a file modify action is observed, a copy of the file will be archived locally on the Management Agent. This can be used later to visually compare what changed between two versions of the file. There is an additional setting to set how many archived copies to store on the Actions to Monitor page of the rule creation wizard.
-
When you add a facet inline with the create rule wizard either as a monitoring facet or as a filtering facet, if you cancel the rule wizard, the newly created facets will still exist and be usable in future rules. You can delete these facets by going to the facet library. Real-time monitoring facets are discussed in a separate section later in this document.
Creating an Agent-side Rule
Note: Before you create an agent-side rule, you must create a configuration extension.
To create an agent-side compliance standard rule to check if a target has the desired configuration state based on collected configuration data, follow these steps:
Creating a Manual Rule
To create a manual compliance standard rule to check if a target has the desired configuration state based on collected configuration data, follow these steps:
Creating a Missing Patches Compliance Standard Rule
To create a missing patches compliance standard rule to detect patches that have not been applied to the appropriate targets, follow these steps:
Tips
-
Once the compliance standard rule has been created, it is not automatically evaluated. Consider adding the compliance standard rule to a compliance standard.
-
Assign a corrective action to the rule after the rule has been created.
-
On the Compliance Standard Rules tab, highlight the rule you just created.
-
From the Actions menu, select Assign Corrective Action.
-
From the Assign Creative Action popup, select an existing corrective action and click OK.
-
Creating a Configuration Consistency Rule
To create a configuration consistency compliance standard rule to determine the consistency of targets of similar target types within a composite target, follow these steps:
Creating Configuration Drift Rule
To create a configuration drift compliance standard rule to determine the deviation of targets of similar target types, follow these steps:
Creating Like a Compliance Standard Rule
To create a compliance standard rule like another compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- Highlight the rule you want to replicate.
- Click Create Like button.
- Customize the fields as needed.
- Click Save.
Editing a Compliance Standard Rule
To edit a compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- Highlight the rule you want to edit and click the Edit button.
- Step through the screens of the rule creation wizard as previously described when creating a rule.
- Click Save.
Usage Notes
-
For repository rules, you can change all the rule properties except the Rule Name, State (if it is already production), and Applicable To.
For real-time monitoring rules, you cannot change Rule Name, State (it is already production), Applicable To, Target Property Filters, and Entity Type.
-
If you change the critical rule properties for a repository rule, for example, rule query, violation condition, parameters, or severity, then editing the rule invalidates the results for compliance standards which refer to the rule. The compliance standards compliance score will be reevaluated at the next rule evaluation.
-
For rules in production mode, you have a choice to create and save a draft of the rule or to overwrite the existing production rule. If you create a draft, you can edit the draft rule, at a later point in time, test it, and then overwrite and merge it back to the original production rule the draft was made from. Note: You cannot include a draft rule into any compliance standard.
-
For Real-time Monitoring rule, if the rule being edited is referred to by a compliance standard which is associated with a target, then the rule definition will be deployed to the Management Agent monitoring the target, so that the Management Agent can evaluate the latest definition of the rule. In the case where the Management Agent is down or unreachable, the rule definition changes will be propagated to the Management Agent as soon as the Management Agent is available.
Deleting a Compliance Standard Rule
Before you delete a rule, you must ensure that compliance standard rule references have been removed from compliance standards before deleting the compliance standard rule. You cannot delete a rule that is in use by a compliance standard.
To delete a compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- Highlight the rule you want to delete, click Delete button.
- Confirm that you want to delete the rule by clicking OK.
Exporting a Compliance Standard Rule
The Export feature provides a mechanism for transporting user-defined compliance standard rule definitions across Management Repositories and Cloud Control instances. The export stores the definitions in an operating system file. Because the exported compliance standard rule definitions are in XML format, they conform to the Oracle Compliance Standard Definition (XSD) format. You can then change the definition of the compliance standard rule and re-import the generated compliance standard rule definitions into another Management Repository.
To export a compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- Highlight the rule you want to export.
- From the Actions menu, select Export.
- Provide the file name to which the standard rule is to be exported.
- The XML representation of the compliance standard rule is generated and placed in the directory and file you specified.
Importing a Compliance Standard Rule
Importing allows you to re-use a compliance standard rule that you already have, share rule definitions across multiple instances of Cloud Control, or enable offline editing of the rule.
Before you import a compliance standard rule, ensure the compliance standard rule to be imported is defined in a file. The file should be locally accessible to the browser you are using to access Cloud Control. Also ensure that you have privileges to access the compliance standard rule definition XML file to be imported.
To import a compliance standard rule, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- From Actions menu, select Import.
- Provide the file name from which the rule definition (as per Compliance Standard Rule XSD) will be imported. Specify whether to override an existing definition if one already exists. The override option is not available to Real-time monitoring rules.
- Click OK.
Browsing Compliance Standard Rules
To browse compliance standard rules, follow these steps:
- From the Enterprise menu, select Compliance, then select Library.
- Click the Compliance Standard Rules tab.
- To view the details of a particular standard rule, highlight the rule and click Show Details.
Using Corrective Actions
A corrective action is a script that fixes the problem causing a violation to a compliance standard rule.
There are two types of corrective actions:
-
Manual - Created in the context of the compliance standard rule.
-
Automatic - Created in the context of an incident rule.
Manual Corrective Action
To create a corrective action manually, perform the following steps:
-
From the Enterprise menu, select Monitoring, then select Corrective Actions.
-
On the Job page:
-
Select SQL Script in the Create Library Corrective Action field, and click Go.
-
On the General tab, type a name for the corrective action (for example, CA1), provide a description, and select Compliance Standard Rule Violation as the Event Type. Select Database Instance as the Target Type.
-
On the Parameters tab, select the default: WHENEVER SQLERROR EXIT FAILURE;. Click Save to Library.
Note: To enable intelligent remediation, pass parameters from the compliance violation to the corrective action. For example, to lock changes to Well Known Accounts, add the following SQL statement:
alter user %EVTCTX.dbuser% account lock; where dbuser is the event context parameter
You can make similar changes to any parameter. Ensure that the parameter name matches the name of the column in the SQL query.
-
Select the corrective action you just created and click Publish.
-
On the confirmation page, click Yes.
-
-
From the Enterprise menu, select Compliance, then select Library. Choose a database compliance standard rule with the rule type of agent-side or repository. In the Actions menu, select Assign Corrective Action. Select a corrective action and click OK.
You will then see the corrective action in the Show Details page for the compliance standard rule.
Automatic Corrective Action
To create a corrective action that is automatically triggered when the violation occurs, follow these steps:
-
From the Setup menu, select Incidents, then select Incident Rules.
-
On the Incident Rules - All Enterprise Rules page, click Create Rule Set. Provide a name for the rule, select All targets in the Targets region, and click Create... in the Rules region.
-
On the Select Type of Rule to Create dialog box, select Incoming events and updates to events. Click Continue.
-
For the type, select Compliance Standard Rule Violation.
-
Select either All events of type Compliance Standard Rule Violation or Specific events of type Compliance Standard Rule Violation.
-
In the Advanced Selection Options, select Corrective action completed. Click Next.
-
On the Create New Rule: Add Actions page, click Add. On the Add Conditional Actions page, click Select corrective action. Select the corrective action. Click Continue.
-
In the Create New Rule: Add Actions page, click Next. Provide a description on the Create New Rule: Specify and Description page and click Next.
-
Review the information and click Continue.
-
Click Save. Note that newly added rules are not saved until the Save button is clicked. After you click Save, verify that the rule set entity has added the new incident rule by reviewing the details.