Setting Kerberos/RADIUS-based Named Credentials as Preferred Credentials
Beginning with Enterprise Manager Cloud Control 13c Release 5 Update 9 (13.5.0.9), two credential sets have been created specifically for Oracle database, RAC database, and PDB target types.
The credential sets are:
- Normal Database Credentials (Advanced)
- SYSDBA Database Credentials (Advanced)
You can associate predefined Named Credentials of type Kerberos/Kerberos Keytab or RADIUS to these credential sets.
Note:
If you define a Named Credential with Role SYSDG, then these Named Credentials can be associated with the SYSDBA Database Credentials (Advanced) credential set as it is assumed that you are using SYSDG-based user credentials in lieu of accessing the database targets as a user with SYSDBA role.There are three ways to set Kerberos/RADIUS credential types as Preferred Credentials on database targets.
- Set Named Credentials from the Enterprise Manager Console
- Define and Set a Kerberos/RADIUS Credential as a Preferred Credential via the One-Time Database Login Option
- Set Kerberos/RADIUS credentials as Preferred Credentials using emcli
Set Named Credentials from the Enterprise Manager Console
You can set RADIUS/Kerberos credential types as Preferred Credentials on databases and related targets directly from the Enterprise Manager console. To access the Preferred Credentials page, from the Setup menu, select Security and then Preferred Credentials.
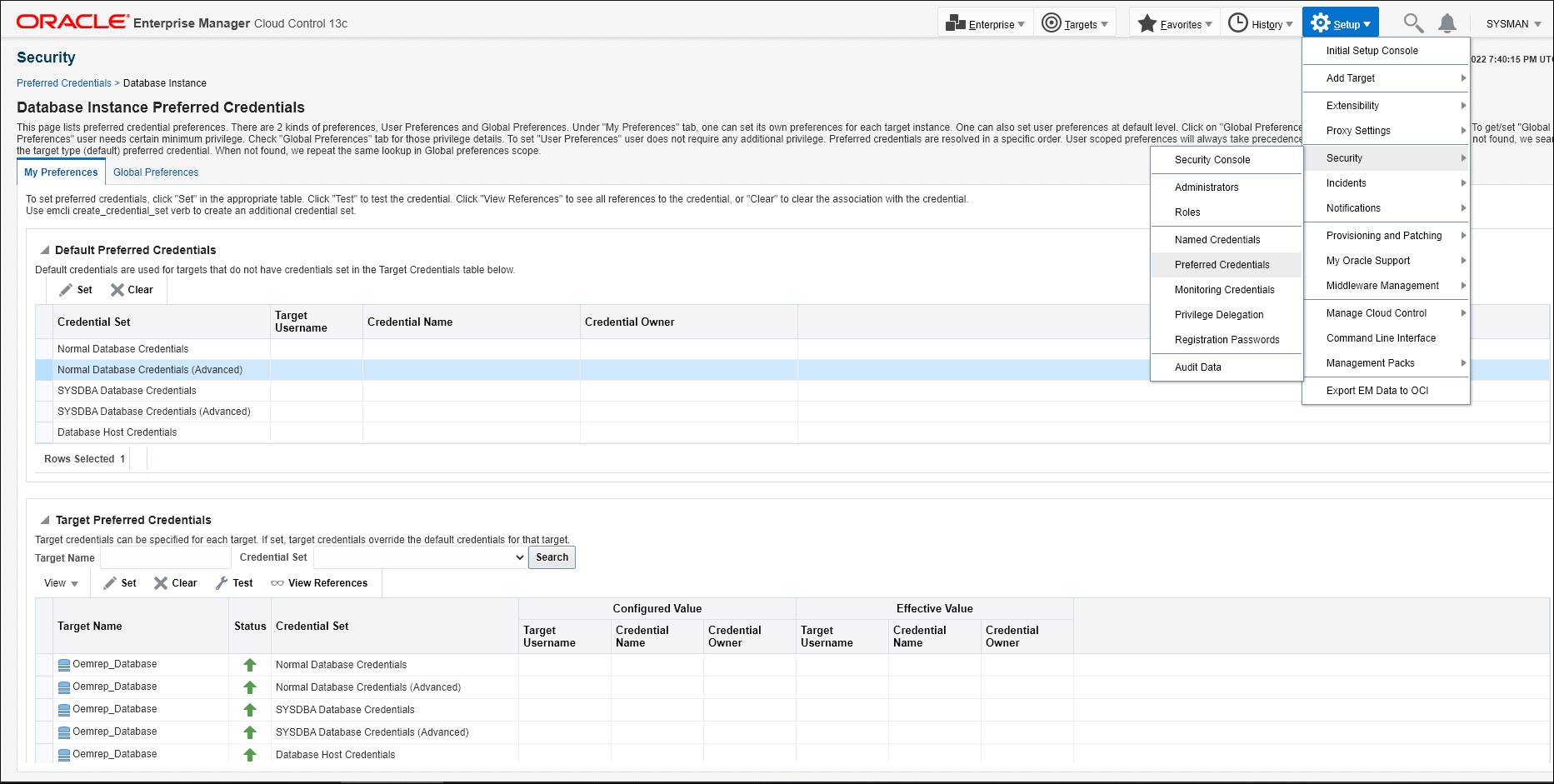
Note:
Named Credentials of type RADIUS or KERBEROS must have already been created and saved before they can be selected and set as Preferred Credentials in the Preferred Credentials page above. You cannot create a new credential of type RADIUS or Kerberos and then save this as a preferred credential via this page in the same step.Define and Set a Kerberos/RADIUS Credential as a Preferred Credential via the One-Time Database Login Option
You can set the following OMS properties to enable a one-time database login using a new RADIUS/Kerberos credential type.
emctl set property -name oracle.sysman.db.enable_radius_auth -value true
emctl set property -name oracle.sysman.db.enable_kerberos_auth -value true
emctl set property -name oracle.sysman.db.multiCredTypeLogin -value true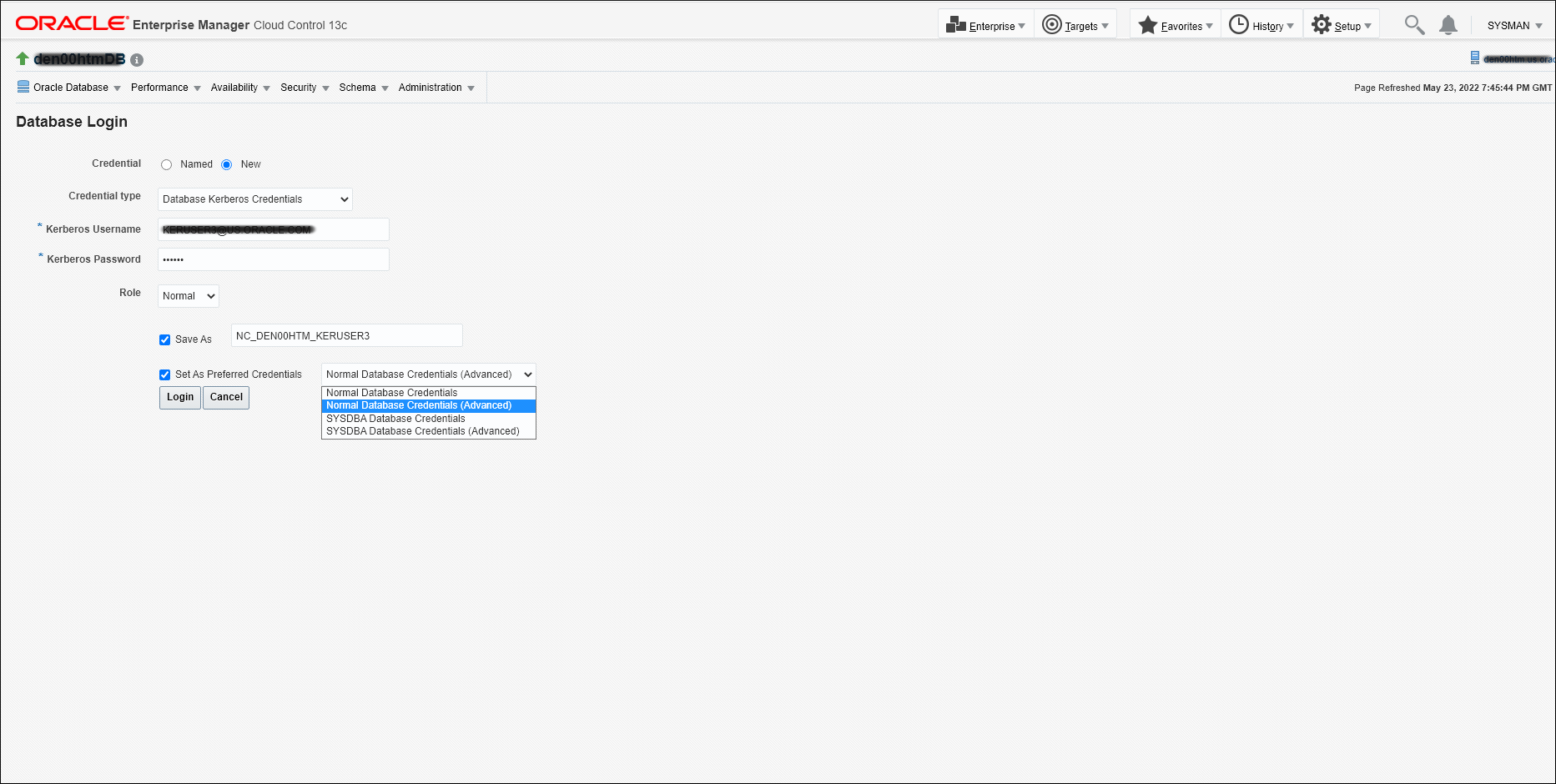
Once the above Preferred Credentials are set on the database and/or related target, they can be used for underlying jobs (like ExecuteSQL or SQLScript) that support these advanced credentials types.
Logging in from the Enterprise Manager console to the target is similar to using regular database (username/password) Preferred Credential sets. For example if Normal Database Credentials (Advanced) is set as a Preferred Credential for a given database target (and Normal Database Credentials is NOT set), navigating to any Enterprise Manager console page for this database target (requiring a database login as a user with Normal role) will result in an auto-login to the database target as this Kerberos/RADIUS user that is represented by the Preferred Credential being set.
Set Kerberos/RADIUS
Credentials as Preferred Credentials Using
emcli
You can use emcli to associate
Kerberos/RADIUS-based Named Credentials as Preferred Credentials on
a database or related target using emcli commands
shown in the following examples.
To set a SYSDBA Kerberos-based Named Credential as a Preferred Credential on the database target emdb020DB:
emcli set_preferred_credential -set_name="DBCredsSYSDBAASO" -target_name="emdb020DB" -target_type="oracle_database" -credential_name="NC_EMDB020D_KEYTAB_SYSDBA" To set a Normal RADIUS based Named Credential as a Preferred Credential of type Normal Database Credentials (Advanced) on the database target den01csgDB:
emcli set_preferred_credential -set_name="DBCredsNormalASO" -target_name="den01csgDB" -target_type="oracle_database" -credential_name="NC_DEN01CSG_ASO" Propagation of Kerberos/RADIUS Subject and Role Across Database Logins
When you log into a database target as a Kerberos/RADIUS user and then navigate to a UI page in the Enterprise Manager console to access another database target that requires a database login with a specific role, Enterprise Manager will log in automatically using the original Kerberos user and role if that user is a valid user on the second database.
However, if there is a Preferred Credential defined for the second database with the appropriate role, then that Preferred Credential will be used for the DB login instead of the cached Kerberos credentials.
Example:
The DataGuard Administration page requires a database login with as a SYSDBA user. If there is a Kerberos/RADIUS Preferred Credential set defined for the database target under SYSDBA Database Credentials (Advanced) and no SYSDBA database credentials are defined, then accessing the DataGuard Administration page for the first time on a database target will result in an auto-login using the Kerberos/RADIUS credentials defined as a Preferred Credential on defined as a Preferred Credential for the SYSDBA Database Credentials (Advanced) credential set.
If both SYSDBA Database Credentials AND SYSDBA Database Credentials (Advanced) are defined on the same target, then the regular SYSDBA database credential set will take precedence.