1 BRM Security Overview
Learn about security in Oracle Communications Billing and Revenue Management (BRM).
Topics in this document:
Basic Security Considerations
The following principles are fundamental to using any application securely:
-
Keep software up to date. This includes the latest product release and any patches that apply to it.
The system administrator is responsible for ensuring that all the installed software dependencies are kept up to date wherever possible. Oracle supports software versions where the software vendor declares backward compatibility to the version certified with BRM, and the upgrade is a minor version increment (for example, A.B.C to A.B.D).
System administrators need to adopt this policy for software dependencies for which upgrades are related to security rather than focusing on functionality.
Review the latest product release documentation for any new guidelines to follow.
-
Restrict network access to critical services. Keep the BRM Business Process, Data Management, and Data tiers behind a firewall. The firewall provides assurance that access to these systems is restricted to a known network route, which can be monitored and restricted if necessary. As an alternative, a firewall router substitutes for multiple independent firewalls.
Oracle does not recommend placing a firewall between the Data Management and Data tiers because the connection between these two tiers is persistent. As such, it is vital that a firewall does not terminate the connection after a period of time.
Configure the TNS Listener Valid Node Checking feature, which restricts access based on IP address. Restricting database access by IP address can cause application client/server programs to fail for DHCP clients. To resolve this, consider using static IP addresses, a software/hardware VPN, or Windows Terminal Services or equivalent.
-
Limit privileges as much as possible. Give users only as much access as necessary to perform their work. Review user privileges regularly to determine relevance to current work requirements.
-
Monitor system activity. Ensuring system security requires good security protocols, proper system configuration, and system monitoring. Establish who should access which system components, and how often, and monitor those components.
See "Configuring and Using Security Audit" for more information.
-
Install software securely. For example, use firewalls, secure protocols such as secure sockets layer (SSL), transport layer security (TLS), and secure passwords.
See "Performing a Secure BRM Installation" for more information.
-
Learn and use the BRM security features. See "Managing BRM Security".
-
Keep up to date on security information. Oracle regularly issues security-related patch updates and security alerts. You must install all security patches as soon as possible.
See Critical Patch Updates, Security Alerts and Bulletins on the Oracle website.
About Protecting Data
When planning your BRM implementation, consider the following:
-
Which resources need to be protected?
Many resources in the production environment can be protected, including information in databases accessed by BRM and the availability, performance, applications, and the integrity of the BRM architecture. Consider the resources you want to protect when deciding the level of security you must provide.
-
You need to protect customer data, such as credit card numbers.
-
You need to protect internal data, such as proprietary source code.
-
You need to protect system components from being disabled by external attacks or intentional system overloads.
-
-
Who are you protecting data from?
For all BRM implementations, resources must be protected from everyone on the Internet. But what data should also be protected from the employees on the intranet in your enterprise? What data should be accessible to a system administrator?
For example, you need to protect your subscribers' data from other subscribers, but someone in your organization might need to access that data to manage it. You can analyze your workflow to determine who needs access to the data; for example, it is possible that a system administrator can manage your system components without needing to access the system data.
-
What happens if protections on strategic resources fail?
In some cases, a fault in your security scheme is nothing more than an inconvenience. In other cases, a fault might cause great damage to you or your customers. Understanding the security ramifications of each resource helps you protect it properly.
Recommended Deployment Configurations
This section describes recommended deployment configurations for BRM.
Figure 1-1 shows the general architectural recommendation using the well-known and generally accepted trusted network.
Figure 1-1 Traditional Trusted Network View
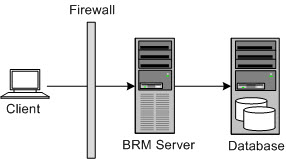
Description of "Figure 1-1 Traditional Trusted Network View"
Firewalls separating the protecting trusted networks provide two essential functions:
-
Blocking any traffic types that are known to be illegal
-
Providing intrusion containment, should successful intrusions take over processes or processors.
Note:
Oracle recommends not having a second firewall between the BRM server and the database server.