3 Media and Documentation
3.1 Media Pack
This section lists the media package for Oracle Communications Cloud Native Core 3.25.1.1xx.0. To download the media package, see MOS.
To learn how to access and download the media package from MOS, see Accessing NF Documents on MOS.
Note:
The information provided in this section is accurate at the time of release but is subject to change. See the Oracle software delivery website for the latest information.Table 3-1 Media Pack Contents for Oracle Communications Cloud Native Core 3.25.1.1xx.0
| Description | NF Version | ATS Version | Upgrade Supported |
|---|---|---|---|
| Oracle Communications Cloud Native Core, Binding Support Function (BSF) | 25.1.100 | 25.1.100 | BSF 25.1.100 supports fresh installation and upgrade from 24.3.x, 24.2.x, and 23.4.6. For more information, see Oracle Communications Cloud Native Core, Binding Support Function Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Configuration Console (CNC Console) | 25.1.100 | NA |
CNC Console 25.1.100 supports fresh installation and upgrade from 24.3.x, 24.2.x, and 23.4.x. For more information, see Oracle Communications Cloud Native Configuration Console Installation, Upgrade, and Fault Recovery Guide. Note: CNC Console supports N-2 NF versions during upgrade window. For example, CNC Console 25.1.100 supports SCP 25.1.100, 24.3.x, and 24.2.x. Any newly added features in Console which have NF dependency in latest release may not be available in previous release. Any newly added features in Console which have NF dependency in latest release may not be available in previous release. |
| Oracle Communications Cloud Native Core, cnDBTier (cnDBTier) | 25.1.103 | NA | cnDBTier 25.1.103 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, cnDBTier Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, cnDBTier (cnDBTier) | 25.1.102 | NA | cnDBTier 25.1.102 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, cnDBTier Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, cnDBTier (cnDBTier) | 25.1.101 | NA | cnDBTier 25.1.101 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, cnDBTier Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, cnDBTier (cnDBTier) | 25.1.100 | NA | cnDBTier 25.1.100 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, cnDBTier Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Cloud Native Environment (CNE) | 25.1.101 | NA | CNE 25.1.101 supports fresh installation and upgrade from 24.3.x and 25.1.100. For more information, see Oracle Communications Cloud Native Core, Cloud Native Environment Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Cloud Native Environment (CNE) | 25.1.100 | NA | CNE 25.1.100 supports fresh installation and upgrade from 24.3.x. For more information, see Oracle Communications Cloud Native Core, Cloud Native Environment Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Certificate Management (OCCM) | 25.1.100 | NA | OCCM 25.1.100 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, Certificate Management Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Network Repository Function (NRF) | 25.1.100 | 25.1.100 | NRF 25.1.100 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, Network Repository Function Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Network Slice Selection Function (NSSF) | 25.1.100 | 25.1.100 | NSSF 25.1.100 supports fresh installation and upgrade from 24.3.x. For more information, see Oracle Communications Cloud Native Core, Network Slice Selection Function Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Operations Services Overlay (OSO) | 25.1.103 | NA | OSO 25.1.103 supports fresh installation and upgrade from 24.3.x and 25.1.1xx. For more information, see Oracle Communications Cloud Native Core, Operations Services Overlay Installation and Upgrade Guide. |
| Oracle Communications Operations Services Overlay (OSO) | 25.1.102 | NA | OSO 25.1.102 supports fresh installation and upgrade from 24.3.x and 25.1.1xx. For more information, see Oracle Communications Cloud Native Core, Operations Services Overlay Installation and Upgrade Guide. |
| Oracle Communications Operations Services Overlay (OSO) | 25.1.101 | NA | OSO 25.1.101 supports fresh installation and upgrade from 24.3.x and 25.1.100. For more information, see Oracle Communications Cloud Native Core, Operations Services Overlay Installation and Upgrade Guide. |
| Oracle Communications Operations Services Overlay (OSO) | 25.1.100 | NA | OSO 25.1.100 supports fresh installation and upgrade from 24.3.x. For more information, see Oracle Communications Operations Services Overlay Installation and Upgrade Guide. |
| Oracle Communications Cloud Native Core, Service Communications Proxy (SCP) | 25.1.100 | 25.1.100 | SCP 25.1.100 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, Service Communication Proxy Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Security Edge Protection Proxy (SEPP) | 25.1.102 | 25.1.102 | SEPP 25.1.102 supports fresh installation and upgrade from 25.1.1xx, 24.3.x, and 24.2.x. For more information, see Oracle Communications Cloud Native Core, Security Edge Protection Proxy Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Security Edge Protection Proxy (SEPP) | 25.1.101 | 25.1.102 | SEPP 25.1.101 supports fresh installation and upgrade from 25.1.100, 24.3.x, and 24.2.x. For more information, see Oracle Communications Cloud Native Core, Security Edge Protection Proxy Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Security Edge Protection Proxy (SEPP) | 25.1.101 | 25.1.101 | SEPP 25.1.101 supports fresh installation and upgrade from 25.1.100, 24.3.x, and 24.2.x. For more information, see Oracle Communications Cloud Native Core, Security Edge Protection Proxy Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Security Edge Protection Proxy (SEPP) | 25.1.100 | 25.1.100 | SEPP 25.1.100 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, Security Edge Protection Proxy Installation, Upgrade, and Fault Recovery Guide. |
| Oracle Communications Cloud Native Core, Unified Data Repository (UDR) | 25.1.100 | 25.1.100 | UDR 25.1.100 supports fresh installation and upgrade from 24.3.x and 24.2.x. For more information, see Oracle Communications Cloud Native Core, Unified Data Repository Installation, Upgrade, and Fault Recovery Guide. |
Cloud Native Core Upgrade
To ensure a smooth and supported upgrade process, follow the upgrade sequence outlined in the table below. Product does not recommend skipping intermediate versions unless explicitly showed:
Figure 3-1 Cloud Native Core Upgrade
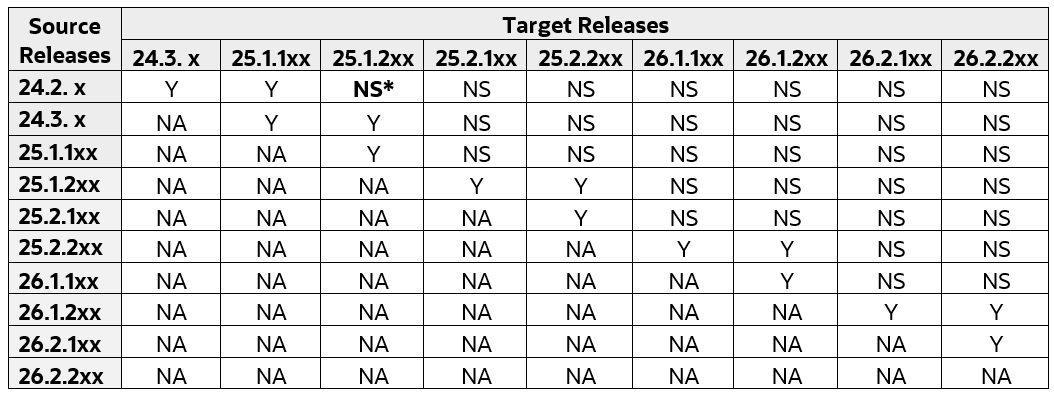
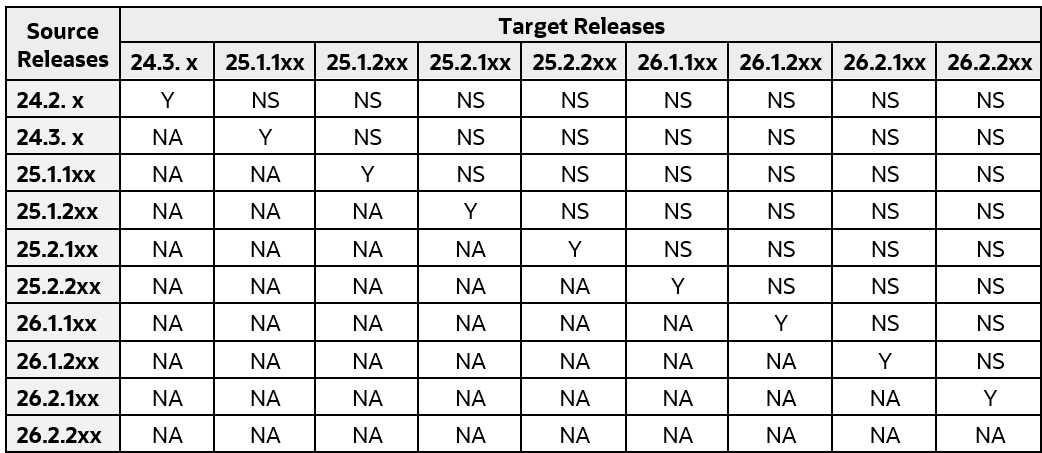
CNE Upgrade
To ensure a smooth and supported upgrade process, follow the upgrade sequence outlined in the following table:
Figure 3-2 CNE Upgrade
3.2 Compatibility Matrix
The following table lists the compatibility matrix for each network function:
Note:
- For seamless integration and optimal performance of CNC NFs on third party platform, the third party platform needs to be compatible with the specified Kubernetes version.
Table 3-2 Compatibility Matrix
| CNC NF | NF Version | CNE | cnDBTier | OSO | ASM S/W | Kubernetes | CNC Console | OCNADD | OCCM | OCI Adaptor |
|---|---|---|---|---|---|---|---|---|---|---|
| BSF | 25.1.100 |
|
|
|
1.14.6 |
|
25.1.1xx | 25.1.1xx | 25.1.1xx | NA |
| CNC Console | 25.1.100 |
|
|
|
|
|
NA | 25.1.1xx | 25.1.1xx | 24.3.x |
| cnDBTier | 25.1.103 |
|
NA | NA | NA |
|
NA | NA | NA | NA |
| cnDBTier | 25.1.102 |
|
NA | NA | NA |
|
NA | NA | NA | NA |
| cnDBTier | 25.1.101 |
|
NA | NA | NA |
|
NA | NA | NA | NA |
| cnDBTier | 25.1.100 |
|
NA | NA | NA |
|
NA | NA | NA | NA |
| CNE | 25.1.100 | NA | NA | NA | NA | 1.31.x | NA | NA | NA | NA |
| CNE | 25.1.100 | NA | NA | NA | NA | 1.31.x | NA | NA | NA | NA |
| NRF | 25.1.100 |
|
|
|
1.14.6 |
|
25.1.1xx | 25.1.1xx | 25.1.1xx | 24.3.x |
| NSSF | 25.1.100 |
|
|
|
|
|
25.1.1xx | NA | NA | NA |
| OCCM | 25.1.100 |
|
NA | NA | NA |
|
23.4.x | NA | NA | NA |
| OSO | 25.1.103 | NA | NA | NA | NA |
|
NA | NA | NA | NA |
| OSO | 25.1.102 | NA | NA | NA | NA |
|
NA | NA | NA | NA |
| OSO | 25.1.101 | NA | NA | NA | NA |
|
NA | NA | NA | NA |
| OSO | 25.1.100 | NA | NA | NA | NA |
|
NA | NA | NA | NA |
| SCP | 25.1.100 |
|
|
|
|
|
25.1.1xx | 25.1.1xx | 25.1.1xx | 24.3.x |
| SEPP | 25.1.102 |
|
|
25.1.1xx | 1.14.6 |
|
25.1.1xx | NA | 25.1.1xx | 24.3.x |
| SEPP | 25.1.101 |
|
|
25.1.1xx | 1.14.6 |
|
25.1.1xx | NA | 25.1.1xx | 24.3.x |
| SEPP | 25.1.100 |
|
|
25.1.1xx | 1.14.6 |
|
25.1.1xx | NA | 25.1.1xx | 24.3.x |
| UDR | 25.1.100 |
|
|
|
|
|
25.1.1xx | NA | 25.1.1xx | NA |
3.3 3GPP Compatibility Matrix
The following table lists the 3GPP compatibility matrix for each network function:
Table 3-3 3GPP Compatibility Matrix
| CNC NF | NF Version | 3GPP |
|---|---|---|
| BSF | 25.1.100 |
|
| CNC Console | 25.1.100 | NA |
| cnDBTier | 25.1.1xx | NA |
| cnDBTier | 25.1.100 | NA |
| CNE | 25.1.1xx | NA |
| NSSF | 25.1.100 |
|
| OCCM | 25.1.100 |
|
| OSO | 25.1.1xx | NA |
| SCP | 25.1.100 | 3GPP TS 29.500 v17.12.0 |
| SEPP | 25.1.1xx |
|
| UDR | 25.1.100 |
|
Note:
Refer to the Compliance Matrix spreadsheet for details on NFs' compliance with each 3GPP version mentioned in this table.3.4 Common Microservices Load Lineup
This section provides information about common microservices and ATS for the specific NF versions in Oracle Communications Cloud Native Core Release 3.25.1xx.0.
Table 3-4 Common Microservices Load Lineup for Network Functions
| CNC NF | NF Version | Alternate Route Svc | App-Info | ASM Configuration | ATS Framework | Config-Server | Debug-tool | Egress Gateway | Ingress Gateway | Helm Test | Mediation | NRF-Client | Perf-Info |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| BSF | 25.1.100 | 25.1.102 | 25.1.102 | 25.1.100 | 25.1.102 | 25.1.102 | 25.1.101 | 25.1.102 | 25.1.102 | 25.1.101 | NA | 25.1.102 | 25.1.102 |
| CNC Console | 25.1.100 | NA | NA | NA | NA | NA | 25.1.101 | NA | 25.1.101 | 25.1.101 | NA | NA | NA |
| OCCM | 25.1.100 | NA | NA | NA | NA | NA | 25.1.101 | NA | NA | 25.1.101 | NA | NA | NA |
| NRF | 25.1.100 | 25.1.103 | 25.1.101 | 25.1.100 | 25.1.100 | NA | 25.1.101 | 25.1.103 | 25.1.103 | 25.1.101 | NA | NA | 25.1.101 |
| NSSF | 25.1.100 | 25.1.102 | 25.1.101 | 25.1.100 | 25.1.102 | 25.1.101 | 25.1.101 | 25.1.102 | 25.1.102 | 25.1.101 | NA | 25.1.102 | 25.1.101 |
| SCP | 25.1.100 | NA | NA | 25.1.100 | 25.1.102 | NA | 25.1.101 | NA | NA | 25.1.101 | 25.1.103 | NA | NA |
| SEPP | 25.1.102 | 25.1.103 | 25.1.101 | 25.1.100 | 25.1.102 | 25.1.101 | 25.1.101 | 25.1.103 | 25.1.103 | 25.1.102 | 25.1.103 | 25.1.102 | 25.1.101 |
| SEPP | 25.1.101 | 25.1.103 | 25.1.101 | 25.1.100 | 25.1.102 | 25.1.101 | 25.1.101 | 25.1.103 | 25.1.103 | 25.1.102 | 25.1.103 | 25.1.102 | 25.1.101 |
| SEPP | 25.1.100 | 25.1.103 | 25.1.101 | 25.1.100 | 25.1.102 | 25.1.101 | 25.1.101 | 25.1.103 | 25.1.103 | 25.1.102 | 25.1.103 | 25.1.102 | 25.1.101 |
| UDR | 25.1.100 | 25.1.102 | 25.1.101 | 25.1.100 | 25.1.102 | 25.1.101 | 25.1.101 | 25.1.102 | 25.1.102 | 25.1.102 | NA | 25.1.102 | 25.1.101 |
3.5 Generic Open Source Software Compatibility on Any Platform
Note:
The Software Requirement column in the following table indicates one of the following:- Mandatory: Absolutely essential; the software cannot function without it.
- Recommended: Suggested for optimal performance or best practices but not strictly necessary.
- Conditional: Required only under specific conditions or configurations.
- Optional: Not essential; can be included based on specific use cases or preferences.
Table 3-5 Generic Open Source Software Compatibility on Any Platform
| Software | Tested Software Version | Software Requirement | Category | Sub-Category | Category Requirement | Usage Description | ||
|---|---|---|---|---|---|---|---|---|
| NF 25.1.1xx | NF 24.3.x | NF 24.2.x | ||||||
| Kubernetes | 1.31 | 1.30 | 1.29.1 | Mandatory | Orchestration | Container Orchestration | Mandatory | Kubernetes orchestrates scalable, automated NF
deployments for high availability and efficient resource
utilization.
Impact: Preinstallation is required. Without orchestration capabilities, deploying and managing network functions (NFs) can become complex, leading to inefficient resource utilization and potential downtime. |
| Helm | 3.16.2 | 3.15.2 | 3.13.2 | Mandatory | Management | Kubernetes Package Management | Mandatory | Helm, a package manager, simplifies deploying and
managing NFs on Kubernetes with reusable, versioned charts for easy
automation and scaling.
Impact: Preinstallation is required. Not using this capability may result in error-prone and time-consuming management of NF versions and configurations, impacting deployment consistency. |
| Podman | 4.9.4 | Recommended | Runtime | Containerized NF Image Management | Mandatory | Podman manages and runs containerized NFs without
requiring a daemon, offering flexibility and compatibility with
Kubernetes.
Impact: Preinstallation is required. Podman is a part of Oracle Linux. Without efficient container management, the development and deployment of NFs could become cumbersome, impacting agility. |
||
| containerd | 1.7.22 | 1.7.16 | 1.7.13 | Recommended | Runtime | Container Runtime | Mandatory | Containerd manages container lifecycles for running
NFs efficiently in Kubernetes.
Impact: A lack of a reliable container runtime could lead to performance issues and instability in NF operations. |
| Velero | 1.13.2 | 1.12.0 | 1.12.0 | Recommended | Backup | Backup and Disaster Recovery for Kubernetes | Optional | Velero backs up and restores Kubernetes clusters for
5G NFs, ensuring data protection and disaster recovery.
Impact: Without backup and recovery capabilities, customers would risk data loss and extended downtime, requiring a full cluster reinstall in case of failure or upgrade. |
| Kyverno | 1.12.5 | 1.12.5 | 1.9 | Recommended | Security | Kubernetes Policy Management | Mandatory | Kyverno is a Kubernetes policy engine that allows to
manage and enforce policies for resource configurations within a
Kubernetes cluster.
Impact: Failing to implement policy enforcement could lead to misconfigurations, resulting in security risks and instability in NF operations, affecting reliability. |
| MetalLB | 0.14.4 | 0.14.4 | 0.14.4 | Recommended | Networking | Load Balancer for Kubernetes | Mandatory | MetalLB provides load balancing and external IP
management for 5G NFs in Kubernetes environments.
Impact: MetalLB is used as LB solution in CNE. LB is mandatory for the solution to work. Without load balancing, traffic distribution among NFs may be inefficient, leading to potential bottlenecks and service degradation. |
| HAProxy | 3.0.2 | Recommended | Networking | Load Balancer/ Reverse Proxy | Mandatory | HAProxy provides load balancing and high
availability for 5G NFs, ensuring efficient traffic distribution and
reliability.
Impact: HAProxy is used as LB solution in CNE. LB is mandatory for the solution to work. Absense of effective traffic management could result in poor service distribution, impacting NF performance and leading to service interruptions. |
||
| CoreDNS | 1.11.1 | 1.11.1 | 1.10.1 | Recommended | Networking | Service Discovery for Kubernetes | Mandatory | CoreDNS is the DNS server in Kubernetes, which
provides DNS resolution services within the cluster.
Impact: DNS is an essential part of deployment. Without proper service discovery, NFs would struggle to communicate with each other, leading to connectivity issues and operational failures. |
| Multus | 3.8 | 3.8.0 | 3.8.0 | Recommended | Networking | Networking for Kubernetes traffic segregation | Conditional | Multus enables multiple network interfaces in
Kubernetes pods, allowing custom configurations and isolated paths
for advanced use cases such as NF deployments, ultimately supporting
traffic segregation.
Impact: Without this capability, connecting NFs to multiple networks could be limited, impacting network performance and isolation. |
| Fluentd | 1.17.1 | 1.16.2 | 1.16.2 | Recommended | Logging | Logging Agent | Mandatory | Fluentd is an open-source data collector that
streamlines data collection and consumption, allowing for improved
data utilization and comprehension.
Impact: Not utilizing centralized logging can hinder the ability to track NF activity and troubleshoot issues effectively, complicating maintenance and support. |
| OpenSearch | 2.11.0 | 2.11.0 | 2.11.0 | Recommended | Logging | Search/ Analytics/ Logging | Mandatory | OpenSearch provides scalable search and analytics
for 5G NFs, enabling efficient data exploration and visualization.
Lack of a robust analytics solution could lead to challenges in identifying performance issues and optimizing NF operations, affecting overall service quality. |
| OpenSearch Dashboard | 2.11.0 | 2.11.0 | 2.11.0 | Recommended | Logging | Dashboard/ Visualization for OpenSearch | Mandatory | OpenSearch Dashboard visualizes and analyzes data
for 5G NFs, offering interactive insights and custom reporting.
Impact: Without visualization capabilities, understanding NF performance metrics and trends would be difficult, limiting informed decision-making. |
| AlertManager | 0.27.0 | 0.27.0 | 0.27.0 | Recommended | Alerting | Alerting (Integration with Prometheus) | Mandatory | Alertmanager is a component that works in
conjunction with Prometheus to manage and dispatch alerts. It
handles the routing and notification of alerts to various
receivers.
Impact: Not implementing alerting mechanisms can lead to delayed responses to critical issues, potentially resulting in service outages or degraded performance. |
| prometheus-kube-state-metric | 2.13.0 | 2.13.0 | 2.10.1 | Recommended | Monitoring | Kubernetes Metrics (for Prometheus) | Mandatory | Kube-state-metrics is a service that generates
metrics about the state of various resources in a Kubernetes
cluster. It's commonly used for monitoring and alerting purposes.
Impact: Without these metrics, monitoring the health and performance of NFs could be challenging, making it harder to proactively address issues. |
| Prometheus Operator | 0.76.0 | 0.76.0 | 0.72.0 | Recommended | Monitoring | Prometheus Instance Management in Kubernetes | Conditional | The Prometheus Operator is used for managing
Prometheus monitoring systems in Kubernetes. Prometheus Operator
simplifies the configuration and management of Prometheus
instances.
Impact: Not using this operator could complicate the setup and management of monitoring solutions, increasing the risk of missed performance insights. |
| prometheus-node-exporter | 1.8.2 | 1.8.2 | 1.7.0 | Recommended | Monitoring | Node-Level Metrics for Prometheus | Mandatory | Node Exporter is a Prometheus exporter for
collecting hardware and OS-level metrics from Linux hosts.
Impact: Without node-level metrics, visibility into infrastructure performance would be limited, complicating the identification of resource bottlenecks. |
| Prometheus | 2.52 | 2.52 | 2.51.1 | Mandatory | Monitoring | Metrics/Monitoring System | Mandatory | Prometheus is a popular open-source monitoring and
alerting toolkit. It collects and stores metrics from various
sources and allows for alerting and querying.
Impact: Not employing this monitoring solution could result in a lack of visibility into NF performance, making it difficult to troubleshoot issues and optimize resource usage. |
| Grafana | 9.5.3 | 9.5.3 | 9.5.3 | Recommended | Visualization | Monitoring/Visualization Tool | Mandatory | Grafana is a popular open-source platform for
monitoring and observability. It provides a user-friendly interface
for creating and viewing dashboards based on various data sources.
Impact: Without visualization tools, interpreting complex metrics and gaining insights into NF performance would be cumbersome, hindering effective management. |
| Calico | 3.28.1 | 3.27.3 | 3.26.4 | Recommended | Networking | Networking/Network Security for Kubernetes | Mandatory | Calico provides networking and security for NFs in
Kubernetes with scalable, policy-driven connectivity.
Impact: CNI is mandatory for the functioning of 5G NFs. Without CNI and proper plugin, the network could face security vulnerabilities and inadequate traffic management, impacting the reliability of NF communications |
| metrics-server | 0.7.2 | 0.7.1 | 0.6.1 | Recommended | Monitoring | Resource Metrics for Kubernetes | Mandatory | Metrics server is used in Kubernetes for collecting
resource usage data from pods and nodes.
Impact: Without resource metrics, auto-scaling and resource optimization would be limited, potentially leading to resource contention or underutilization. |
| snmp-notifier | 1.5.0 | 1.4.0 | 1.4.0 | Recommended | Notification | SNMP Notification Service | Mandatory | snmp-notifier sends SNMP alerts for 5G NFs,
providing real-time notifications for network events.
Impact: Without SNMP notifications, proactive monitoring of NF health and performance could be compromised, delaying response to critical issues. |
| Jaeger | 1.60.0 | 1.60.0 | 1.52.0 | Recommended | Tracing | Distributed Tracing | Mandatory | Jaeger provides distributed tracing for 5G NFs,
enabling performance monitoring and troubleshooting across
microservices.
Impact: Not utilizing distributed tracing may hinder the ability to diagnose performance bottlenecks, making it challenging to optimize NF interactions and user experience. |
| CSI | NA | NA | NA | Mandatory | Storage | Distributed, Orchestrated, and Block Storage | Mandatory | Provides scalable object, block, and file storage,
with orchestration capabilities and block storage provisioning for
persistent storage in Kubernetes.
Impact: CSI is mandatory for the functioning of 5G NFs. Without CSI, managing storage could lead to data loss, inefficiencies, and challenges in scaling storage systems effectively. |
| ceph | 18.2.1 | 18.2.1 | Recommended | Storage | Distributed Storage | Mandatory | The ceph storage system offers scalable object,
block, and file storage. It is used in bm CNE solution.
Impact: Ceph is used in bm OCCNE solution. CSI is mandatory for the solution to work. Not using this distributed storage system would complicate data management, leading to potential data loss and challenges in handling large data volumes effectively. |
|
| rook | 1.15.2 | 1.13.3 | 1.13.3 | Recommended | Storage | Storage Orchestration | Mandatory | Rook is the Ceph orchestrator for Kubernetes that
provides storage solutions. It is used in bm CNE solution.
Impact: CSI is mandatory for the solution to work. Not utilizing Rook could increase the complexity of deploying and managing Ceph, making it difficult to scale storage solutions in a Kubernetes environment. |
| cinder-csi-plugin | 1.31.1 | 1.30.0 | 1.29.0 | Recommended | Storage | Block Storage Plugin | Mandatory | Cinder CSI (Container Storage Interface) plugin is
for provisioning and managing block storage in Kubernetes. It is
often used in OpenStack environments to provide persistent storage
for containerized applications.
Impact: Cinder CSI Plugin is used in OpenStack vCNE solution. Without this integration, provisioning block storage for NFs could be manual and inefficient, complicating storage management. |
3.6 Security Certification Declaration
This section lists the security tests and the corresponding dates of compliance for each network function:
3.6.1 BSF Security Certification Declaration
Release 25.1.100
Table 3-6 BSF Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
Apr 1, 2025 | No unmitigated critical or high findings |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Feb 18, 2025 | No unmitigated critical or high findings |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
Apr 1, 2025 | No unmitigated critical or high finding |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
Apr 7, 2025 | No findings |
Overall Summary: No critical or severity 1 security issues were found during internal security testing.
3.6.2 CNC Console Security Certification Declaration
Table 3-7 CNC Console Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
Mar 25, 2025 | No unmitigated critical or high findings |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Apr 2, 2025 | No unmitigated critical or high findings |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
Apr 2, 2025 | No unmitigated critical or high finding |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
Apr 2, 2025 | No findings |
Overall Summary: No critical or severity 1 security issues were found during internal security testing.
3.6.3 OCCM Security Certification Declaration
Table 3-8 OCCM Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
Apr 2, 2025 | No unmitigated critical or high findings |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Apr 2, 2025 | No unmitigated critical or high findings |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
Apr 2, 2025 | No unmitigated critical or high finding |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
Apr 2, 2025 | No findings |
Overall Summary: No critical or severity 1 security issues were found during internal security testing.
3.6.4 NRF Security Certification Declaration
Release 25.1.100
Table 3-9 NRF Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
Apr 8, 2025 | No unmitigated critical or high findings |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Apr 8, 2025 | No unmitigated critical or high findings |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
Apr 8, 2025 | No unmitigated critical or high finding |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
Apr 8, 2025 | No findings |
Overall Summary: No critical or severity 1 security issues were found during internal security testing.
3.6.5 NSSF Security Certification Declaration
Release 25.1.100
Table 3-10 NSSF Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
Feb 27, 2025 | No unmitigated critical or high findings |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Feb 27, 2025 | No unmitigated critical or high findings |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
Feb 27, 2025 | No unmitigated critical or high finding |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
Feb 27, 2025 | No findings |
Overall Summary: No critical or severity 1 security issues were found during internal security testing.
3.6.6 SCP Security Certification Declaration
Release 25.1.100
Table 3-11 SCP Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
Apr 2, 2025 | No unmitigated critical or high findings |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Apr 2, 2025 | No unmitigated critical or high findings |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
Apr 2, 2025 | No unmitigated critical or high finding |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
Apr 2, 2025 | No findings |
Overall Summary: No critical or severity 1 security issues were found or pending during internal security testing.
3.6.7 SEPP Security Certification Declaration
Table 3-12 SEPP Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
July 22, 2025 | No unmitigated critical or high findings. Scan done through Fortify. |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
April 7, 2025 | No unmitigated critical, high, medium, and low findings. Scan done through RestFuzz. |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
April 7, 2025 | No unmitigated critical or high findings. Scan done through Blackduck. |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
July 22, 2025 | No issues found. Scan done through McAfee. |
Table 3-13 SEPP Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
June 9, 2025 | No unmitigated critical or high findings. Scan done through Fortify. |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Dec 16, 2024 | No unmitigated critical, high, medium, and low findings. Scan done through RestFuzz. |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
April 7, 2025 | No unmitigated critical or high findings. Scan done through Blackduck. |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
June 9, 2025 | No issues found. Scan done through McAfee. |
Overall Summary: No critical or severity 1 security issues were found during internal security testing.
Table 3-14 SEPP Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
Apr 7, 2025 | No unmitigated critical or high findings. Scan done through Fortify. |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Dec 16, 2024 | No unmitigated critical, high, medium, and low findings. Scan done through RestFuzz. |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
Apr 7, 2025 | No unmitigated critical or high findings. Scan done through Blackduck. |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
Apr 8, 2025 | No issues found. Scan done through McAfee. |
Overall Summary: No critical or severity 1 security issues were found during internal security testing.
3.6.8 UDR Security Certification Declaration
Table 3-15 UDR Security Certification Declaration
| Compliance Test Description | Test Completion Date | Summary |
|---|---|---|
| Static Source Code Analysis
Additional Info: Assesses adherence to common secure coding standards |
Mar 31, 2025 | No unmitigated critical or high findings |
| Dynamic Analysis (including fuzz testing)
Additional Info: Tests for risk of common attack vectors such as OWASP Top 10 and SANS 25 |
Mar 31, 2025 | No unmitigated critical or high findings |
| Vulnerability Scans
Additional Info: Scans for CVEs in embedded 3rd party components |
Mar 31, 2025 | No unmitigated critical or high finding |
| Malware Scans
Additional Info: Scans all deliverable software packages for the presence of known malware |
Mar 31, 2025 | No findings |
Overall Summary: No critical or severity 1 security issues were found during internal security testing.
3.7 Documentation Pack
All documents for Oracle Communications Cloud Native Core (CNC) 3.25.1.1xx.0 are available for download on SecureSites and MOS.
To learn how to access and download the documents from SecureSites, see Oracle users or Non-Oracle users.
To learn how to access and download the documentation pack from MOS, see Accessing NF Documents on MOS.
The NWDAF documentation is available on Oracle Help Center (OHC).