6 The Configuration Tab Display and Operations
The Oracle® Enterprise Session Border Controller (ESBC) Web GUI provides access to the dialogs and controls that you need to set up, administer, and maintain the configuration objects used on your session border controller through the Configuration tab.
Note:
The Web GUI Guide does not provide instructions for setting up the configuration objects. Use the ACLI Configuration Guide to get the instructions by transposing the path given to reach the object in the ACLI onto the Web GUI and you will reach the configuration dialog. The parameters displayed in the Web GUI dialogs are the same as those in the ACLI.Configuration Tab Display and Operations
The Configuration tab displays configuration objects in the navigation pane organized much like they are on the ACLI command line. When you click a top-level object in the navigation pane, the center pane displays the sub-objects in alphabetical order. You can also click the twister by the high-level object in the navigation pane to display an alphabetical list of the sub-objects in the navigation pane. The Configuration tab header displays the system identification at the left end of the banner and the Notifications alarm and the User menu at the right end of the banner. Below the banner, the page displays the controls for View Configuration, Search, Discard, Verify, and Save.

Configuration Tab Controls
The Configuration tab displays controls to help you find, review, and work with the configurations that you set on the Oracle® Enterprise Session Border Controller.

Device Name—IP Address—Build Number—Use to identify the system and the software version. When you deploy your SBC in a High Availability (HA) pair, the system identification also states whether the device is the Active or Standby peer.
View Configuration—Use to see the configuration Inventory, Editing Configuration Short, Running Configuration Short, Configuration Version, and Realm Specifics.
Paste—Use to paste a configuration that you want to duplicate into a dialog where you can make edits, if you want, and save the configuration.
Search—Use to find and display configuration objects to edit. The first time you place the cursor in the search field, the Web GUI displays a drop-down list of all the configuration objects in alphabetical order. You can refine your search by entering a parameter, an attribute, a value, or an object. When you use Search and switch to another tab, the system retains the search criteria when you return to the Configuration tab.
Discard—Use to undo all configuration changes made in the current session. The system can only discard the changes that you saved. It cannot discard any changes that you activated.
Verify—Use to validate the configuration is valid before saving.
Save—Use to save the current configuration session. Upon Save, the system displays a prompt with a choice of whether or not to activate the configuration. If you do not activate the configuration, you can continue to make changes and Save again. When finished, you can save and activate all of the configuration changes.
View the ESBC Configuration Inventory
When you want to see aggregated information about the state of the configuration on the Oracle® Enterprise Session Border Controller (ESBC), click View Configuration on the Configuration tab. The Web GUI displays the Configuration Inventory page by default with tabs for the other views.
The following screen capture shows the default landing page after you click View Configuration.
Note:
When you set the process level or system log level to DEBUG, the Web GUI may not display any configuration information for large configurations when you click "View Configuration".
View Configuration Tabs
Inventory—Shows the Element list, Running Count, Changes Not Activated Total Count, Changes Not Activated Added Total Count, Changes Not Activated Modified Count, and Changes Not Activated Deleted Count.
Editing Configuration Short—Shows only the modified attributes in the editing configuration.
Running Configuration Short—Shows only the modified attributes in the running configuration.
Configuration Version—Shows the configuration version number table, which shows both the Current Version and the Running Version.
Realm Specifics—Allows you to set the Realm parameter and Auto Refresh interval.
Controls
Each tab, except for Realm Specifics, displays a set of controls in the upper right corner. The following list includes all of the available controls, but note that the controls vary per tab.

Refresh—Use to manually refresh the data on the tab.
Settings—Use to set the Auto Refresh Interval and to enable the option to Show Only Differences.
Download—Use to download data to the Configuration Inventory.
Description—Use to see a description of the view.
Show or Hide Advanced Configuration Objects in the Navigation Pane
Each category of configuration objects includes additional objects that are not required to complete a basic configuration. Such objects are called Advanced objects, which you use to customize your configuration. If you do not need to see the advanced objects, you can hide them from view with the Show All toggle located at the bottom of the navigation pane. The Show All toggle affects all categories of configuration objects. You can toggle between show and hide at anytime.
The following screen capture shows the navigation pane with the Show All toggle in the hide position. In this example, media-manager displays only five configuration objects because the Advanced configuration objects are hidden.

The following screen capture shows the navigation pane with the Show All toggle in the Show All position. The Web GUI displays the advanced elements in italics.

Show or Hide Advanced Configuration Parameters
Configuration dialogs can contain both Basic and Advanced parameters. You can choose to see only the Basic parameters or to see both the Basic and Advanced parameters by using the Show Advanced toggle. The Web GUI displays the toggle on every configuration dialog that contains both Basic and Advanced parameters.
The Web GUI defaults to displaying only the Basic parameters, even when a configuration contains Advanced parameters. Use the Show Advanced toggle to see all the parameters.
When all parameters in a configuration are Advanced, the Web GUI turns on Show Advanced by default.
When all parameters in a configuration are Advanced and you toggle Show Advanced off, the Web GUI hides all parameters for that configuration.
When you highlight an Advanced parameter during Search or Verify, the Web GUI activates Show Advanced and displays all the Advanced parameters for the configuration.
When an error occurs upon submission of input for an Advanced parameter, the GUI turns Show Advanced on automatically.
When you leave the Configuration tab for another tab and return to the Configuration tab, the Show Advanced state remains as it was before you left the tab.
When you turn Show Advanced on while configuring a multi-instance object and click OK, the Show Advanced state persists when you open any instance in the table. When you configure another instance and turn Show Advanced off, the off state persists when you open any instance in the table.
Show the Configured Parameters of a Configuration Object
After you add a new configuration or modify an existing one, you might want to view the settings to confirm your work before activation. Every configuration object includes the Show Configuration button in the title banner, which you can click to see the editing version of the configuration.
The following screen capture shows the Show
Configuration button, which is located at the right end
of the configuration object title banner.
Note:
The list shows only the parameters you edited.
Descriptions of the Show Configuration Controls
The Show Configuration page displays the following icons in the upper right corner that you can use to work with the configuration.

Configuration Dialogs Behavior
Drop-Down Lists
To make configuration easier, the Web GUI displays drop-down lists for selecting values for configuration parameters. Drop-down lists behave in the following ways:
System Populated—The system populates the list. You can only select an item that exists on the list and you cannot edit the list. For example, the system populates the list for the Strategy parameter in the Add Session Group configuration dialog.

User Populated—You can populate the list by configuring the objects in advance or by entering text in the field. For example, in the Add Realm configuration, the Ice Profile parameter can display a drop-down list of Ice Profiles. You create the list by configuring one or more profiles in the Ice Profile configuration.

In Realm Config, the system displays the name of each Ice profile that you created in the Ice Profile drop-down list. You can either select an entry from the list or enter the name of one that you plan to create.

Note:
Some configuration parameters allow you to select multiple items from the drop-down list.Options Fields
Options fields require you to enter each option separately with a delimiter between options. Without delimiters the system considers all of the entries as one, which can lead to unpredictable behavior. The Options text box accepts commas, semi-colons, full stops, and parens as delimiters.
To add one option:Type the name of the option.

Click outside of the text box and the GUI sets the option in its own tab.

To add multiple options:
Type the name of each option, separated with either the comma, semi-colon, or space characters. The following example shows commas as the delimiters.

Click outside of the text box and the GUI sets each option as a separate tab.

If you have a list of options in a text document and they are delimited with a comma, semi-colon, full stop, or parens, you can copy the list into the Options field and the system will add each option as a separate tab as soon as you click outside of the tab.
To delete an Option, click the X on the tab.
Unsaved Changes Persistence
While working in a configuration dialog, you can switch to another tab before you save the changes you made and expect your work to persist when you return to the dialog.
Controls for Managing Multi-instance Configurations
Some configuration objects allow you to create multiple instances of the configuration, which the system displays in a list on the configuration object landing page. You can manage multi-instance configuration objects with the buttons and controls displayed on the landing page and within the configuration dialog. Buttons display at the top of the dialog and controls display when you right-click elements of the configuration in the list.
Controls for Managing Configuration Lists
Web GUI configuration pages display controls for managing lists of multi-instance configurations. You can use certain controls to affect multiple instances, while others can affect only one instance at a time.
Global Controls
At the top of a multi-instance configuration list, the Web GUI displays the controls for managing the list. All the controls are active when you select a single row in the table. When you select multiple rows in a table, the system activates only the icons for supported actions. For example, when you select multiple rows, the Add, Delete, Upload, and Download icons remain activated. The system deactivates the Edit and Copy icons because those operations work on a single row, only.

1. Add—Click to add a configuration instance to the list.
2. Delete All—Click to delete all instances. You do not need to select the instances, just click the Delete All icon.
3. Upload—Click to upload one or more CSV configuration files to the configuration displayed.
4. Download—Click to download one or more configurations to a CSV file.
5. Edit—Click to edit the selected configuration.
6. Copy—Click to copy the selected configuration.
7. Delete—Click to delete the selected configuration.
Note:
When you Add, Edit, or Copy in a table, the table reloads and returns to the record you were on.Row Controls
You can also access the Edit, Copy, and Delete controls from a row in the list. Either click the ellipses or right-click the row. When you right-click, the menu also includes the sorting choices.

Controls for Ordering Table Rows in a Multi-Instance Configuration
Controls for Ordering Table Rows in a Multi-Instance Configuration
You can set the order of the configurations in most multi-instance configuration lists to display in either ascending or descending alphabetical order. The exception occurs in the Local Policy configuration, where you can manually set the rows in any order.
Set the Sort Order for All Lists Except Local Policy
Right-click the configuration, and the system displays the control menu that includes Sort. Click Sort, and click either Sort Ascending or Sort Descending.

You can also set the sort order by clicking the arrow in the column header.

Set the Sort Order for the Local Policy Table
Right-click the row that you want to move, and the system displays the control menu that includes Move Up and Move Down.

Controls for Showing and Hiding Column Headers
Each multi-instance configuration list supports a unique array of column headers and you can choose the ones that you want displayed and hidden. Right-click a column header to display the list of column headers that is available for the table displayed.
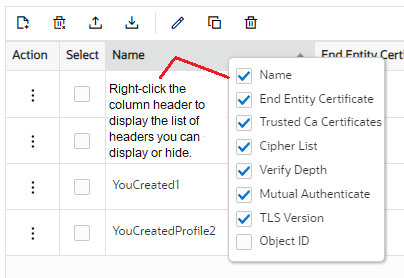
Note:
The same list displays regardless of which column you click.Configuration Error Messages
If you save a configuration that contains errors, the system displays the following error message: There were errors! Are you sure you want to activate the configuration?
The system displays a list of errors at the bottom the page. Click an error to go to the location in the configuration where the error occurred and edit the configuration as needed.
| Severity | Identifies the level of severity that the Oracle
Enterprise Session Border Controller assigns to the error. Valid values are:
|
| Message | Identifies the element field where the error, warning, or critical error occurred, and the reason for the error. |
| Object | Identifies the element and the field for that element where the error occurred. |
| Attribute Name | Identifies the attribute within the element where the error occurred. |
| Other | Identifies any other pertinent information relating to the error. |
Configuration States and Behavior
The Oracle® Enterprise Session Border Controller (ESBC) uses three states of memory to manage configuration changes, which allows you to make changes and decide when you want them to take effect.
- Editing—The editing configuration is the version that you are making changes to from the Web GUI. The editing version is stored in the ESBC volatile memory. The editing version cannot survive a system restart.
- Saved—The saved configuration is the version of the editing configuration that the system copies into the non-volatile memory when you click Save on the Web GUI. The changes do not take effect on the ESBC until you activate the saved configuration. Note that the system does not load the saved, but unactivated, configuration as the running configuration upon restart. The Saved configuration requires activation, first.
- Running configuration—The running configuration is the configuration that the system is using. When you activate the saved configuration it becomes the running configuration. Most configuration changes can take effect upon activation. Some configuration changes require a system restart. Upon restart, the system loads the running configuration.
- OK—All configuration dialogs display an OK button that saves changes to the editing memory. If you restart before the next step, the ESBC does not save the changes.
- Verify—(Optional) Oracle recommends verifying the validity of the configuration before saving because saving shows any errors after saving. Verify displays the configuration changes and any errors found, before saving.
- Save—The Save button on the Web GUI toolbar verifies the configuration, saves the current configuration to the last-saved configuration, and displays errors. Save stores the configuration on the ESBC. The system displays any errors at the bottom of the Configuration page.
- Activate—After you finish making one or more configuration changes, OK and Save from the last configuration dialog that you need to edit at this time. The system displays the Confirmation dialog containing the Activate button. When you click Activate, the ESBC activates all of the saved configuration changes and saves the new configuration to the running configuration. If you cancel the activation function, the ESBC saves the configuration in a file and does not change the running configuration. You can continue to make changes to the configuration.
Duplicate a Configuration
To save time when adding configurations to a multi-instance configuration object, you can paste an existing configuration into an editable dialog on the Web GUI as the starting point for adding the new one. You can use the copied configuration exactly or make modifications.
Create a Configuration Manually
Use the following procedure to manually create a configuration through the Web GUI.
Media Manager Configuration
Use the Media Manager configuration object to define the settings for the media steering functions performed by the Oracle® Enterprise Session Border Controller (ESBC), including timer limits, logging, and trust levels.
You can configure the following Media Manager objects from the Configuration tab on the Web GUI. See the documentation specified in the following list for explanations of these configuration objects and how to set their parameters.
| Codec Policy | Create a codec policy to specify allowed codecs, the order of codecs, and codecs to add on egress. See "Codec Policy Configuration" in the ACLI Configuration Guide. |
| DNS ALG Constraints | Configure and enable DNS ALG constraints. See the "DNS ALG Service Name Configuration" section of the "Application Gateway Services" chapter in the ACLI Configuration Guide. |
| DNS Config | Configure the DNS ALG service. See "DNS Configuration" in the ACLI Configuration Guide. |
| ICE Profile | Configure ICE profile. See "Configure ICE Profile" in the ACLI Configuration Guide. |
| Media Manager | Configure media steering functions. See "Creating Steering Pools for Multiple Interface Realms" in the ACLI Configuration Guide. |
| Media Policy | Configure a media policy and ToS settings. See "Packet Marking Configuration" in the ACLI Configuration Guide. |
| MSRP Config | Configure and enable MSRP. See "RCS Services" in the ACLI Configuration Guide. |
| Playback Config | Configure media use for playback. See "Local Media Playback" in the ACLI Configuration Guide. |
| Realm Config | Configure a realm for media management. See "Realms and Nested Realms" in the ACLI Configuration Guide. |
| Realm Group | Configure realm groups for local media playback. See "Configuring Realm Groups" in the ACLI Configuration Guide. |
| RTCP Policy | Configure an RTCP policy. See "Configuring RTCP Generation" in the ACLI Configuration Guide. |
| Static Flow | Configure static network traffic flows. See "Static Flows" in the ACLI Configuration Guide. |
| Steering Pool | Specify one or more ports for steering media flows. See "Steering Pools" in the ACLI Configuration Guide. |
| TCP Media Profile | Configure the TCP media profile and profile entries. See "Configure TCP Media Profile" in the ACLI Configuration Guide. |
Security Configuration
The Oracle® Enterprise Session Border Controller (ESBC) can provide security for VoIP and other multi-media services. ESBC security includes access control, DoS attack, and overload protection to help secure service and protect the network infrastructure. ESBC security lets legitimate users place a call during attack conditions, while protecting the service itself.
ESBC security includes the numerous features and architecture designs of the Net-SAFE framework. Net-SAFE is a requirements framework for the components required to provide protection for the ESBC, the service provider's infrastructure equipment (proxies, gateways, call agents, application servers, and so on), and the service itself.
| audit-logging | Configure the size, location, and conditions that trigger the transfer of logs to the specified location. See "Configure the Audit Log" in the "Audit Log" chapter in the Administrative Security Guide. |
| auth-params | Configure authentication protocol, strategy, and servers. See the "Authentication and Authorization" section in the "Access" chapter in the Administrative Security Guide. |
| authentication | Configure RADIUS and TACACS authentication. See "RADIUS Authentication" and "TACACS+" in the ACLI Configuration Guide. |
| authentication profile | Reserved for future use. |
| certificate record | Create or update a certificate record for either a CA or end entity. See "Certificate Configuration Process" in the ACLI Configuration Guide. See "Update a Certificate in the Web GUI Guide. |
| data-flow | Specify the pass-through data-traffic processing when using IKE. See "data-flow" in the ACLI Reference Guide. |
| dpd-params | Enable one or more sets of DPD Protocol parameters. See "dpd-params" in the ACLI Reference Guide. |
| ike-access-control | Define the allow list, blocklist, and DDoS parameters for the ike-interface that uses this parameter. See "ike-access-control" in the ACLI Reference Guide. |
| ike-accounting-param | Specify the IKE accounting parameters. |
| ike-certficate-profile | Specify the public certificate that authenticates a specific IKEv2 identity, as well as one or more CA certificates used to validate a certificate offered by a remote peer. See "ike-certficate-profile" in the ACLI Reference Guide. |
| ike-config | Define a single, global Internet Key Exchange (IKE) configuration object. See "ike-config" in the ACLI Reference Guide. |
| ike-interface | Create multiple OKE-enabled interfaces. See "ike-interface" in the ACLI Reference Guide. |
| ike-sainfo | Enable the negotiation and establishment of IPSec tunnels. See "ike-sainfo" in the ACLI Reference Guide. |
| local-address-pool | Create local address pools to provide a local (internal) address in response to remote requests for IP addresses. See "local-address-pool" in the ACLI Reference Guide. |
| tunnel-orig-params | Define a single, remote IKEv2 peer. See "tunnel-orig-params" in the ACLI Reference Guide. |
| ipsec-global-config | Configure the parameters governing system-wide IPSec functions and behavior, including IPSec redundancy. See "ipsec-global-config" in the ACLI Reference Guide. |
| security-association | Configure a security association on the Oracle Session Border Controller. See "security-association-manual" in the ACLI Reference Guide. |
| secutiy-policy | Define multiple policy instances with each policy defining match criteria and an operational action performed on matching traffic flows. See "security-policy" in the ACLI Reference Guide. |
| dtls-srtp-profile | Configure the key exchange and DTLS handshake on a media session, the role the SBC negotiates when offered alternatives, and the crypto suites to use. See the "Configure DTLS SRTP Profile" section in the "Advanced Media Termination Support" chapter of the ACLI Configuration Guide. |
| media-sec-policy | Define a policy that affects inbound and outbound traffic. See "media-sec-policy" in the ACLI Reference Guide. |
| sdes-profile | Configure the parameter values offered and accepted during SDES negotiation. See "sdes-profile" in the ACLI Reference Guide. |
| sipura-profile | Specify the materials (certificate, protocol suites, and so on) the support cryptographic operations. See "sipura-profile" in the ACLI Reference Guide. |
| password -policy | Create a password policy. See the "Password Policy" section in the "Access" chapter in the Administrative Security Guide. |
| security-config | Configure security for VoIP and other multimedia services. See the "Security" chapter in the ACLI Configuration Guide. |
| ssh-config | Configure the system for an SSH connection. See "SSH Remote Connections" in the ACLI Configuration Guide. |
| ssh-key | Add or upload an SSH key. See "SSH Remote Connections" in the ACLI Configuration Guide. |
| tls-global | Configure session caching to allow a previously authenticated client to re-connect with the unique session identifier from the previous session. See "TLS Session Caching Configuration" in the ACLI Configuration Guide. |
| tls-profile | Create a profile to define communications security for running SIP over TLS. See "Configure a TLS Profile" in the ACLI Configuration Guide. |
Update a Certificate
When you need to renew a certificate on the Oracle® Enterprise Session Border Controller (ESBC), you can go to the existing certificate record and overwrite the existing certificate with the renewed certificate. You do not need to create a new certificate record.
- Confirm that the certificate record you want to update contains a certificate.
- Send the original certificate request to the Certificate Authority (CA) for renewal.
Session Router Configuration
You can configure the following Session Router objects from the Configuration tab on the Web GUI. See the documentation specified in the following list for explanations of these configuration objects and how to set their parameters.
| Access Control | Configure a static or dynamic access control list. See the Security Guide and "System Access Control" in the ACLI Configuration Guide. |
| Allowed Elements Profile | Configure an allowed elements profile to configure SIP Allowlist which, control the passage of unknown headers and parameters in request and response traffic. Includes the Rule Sets sub-object. See the "Allowlist Lists for Managing Incoming SIP Headers and Parameters" section of the "Admission Control and QoS" chapter in the ACLI Configuration Guide. |
| Class Policy | Configure a classification profile policy. See "Using Class Profile for Packet Marking", " Class Profile and Class Policy Configuration", and " Applying a Class Policy to a Realm" in the ACLI Configuration Guide. |
| Diameter Manipulation | Configure diameter manipulation rules. See the "Diameter Rf Accounting" chapter in the Accounting Guide. |
| Enforcement Profile | Configure an enforcement profile. See "SIP Enforcement Profile and Allowed Methods" in the ACLI Configuration Guide. |
| ENUM Config | Configure an ENUM server. See "ENUM Server", and other ENUM topics in the ACLI Configuration Guide. |
| Filter Config | Configure a custom filter for SIP monitor and trace. See the "SIP Monitor and Trace" section of the "Introduction to SIP Monitor and Trace" chapter in the ACLI Configuration Guide. |
| H323 Config | Configure and enable an H.323 protocol. See the "Signaling" chapter in the ACLI Configuration Guide. |
| H323 Stack | Configure an H.323 stack. See the "Signaling" chapter in the ACLI Configuration Guide. |
| Home Subscriber Server | For future use. Not supported at this time. |
| HTTP ALG | Configure an HTTP proxy. See "Dynamic ACL for the HTTP-ALG" in the See the "Signaling" chapter in the ACLI Configuration Guide. |
| LDAP Config | Configure and enable an LDAP server. See the "Active Directory-based Call Routing" section of the "Session Routing and Load Balancing" chapter in the ACLI Configuration Guide. |
| Local Policy | Configure a session request routing policy. See "The Role of Local Policy" and "Configuring the Local Policy Attribute" in the ACLI Configuration Guide. |
| Local Response Map | Configure a local SIP response map. See "Add a Local Response Map" in the ACLI Configuration Guide. |
| Local Routing Config | Configure the parameters for the local routing table. See the "Using the Local Route Table for Routing" section of the "Session Routing and Load Balancing" chapter in the ACLI Configuration Guide. |
| Media Profile | Configure a media profile and apply it to a media type. See the various "Media Profile Configuration" topics throughout the ACLI Configuration Guide. |
| Net Management Control | Configure and enable network management controls. See "Network Management Controls" in the ACLI Reference Guide. |
| Response Map | Configure a SIP response map. See "Add a Local Response Map" in the ACLI Configuration Guide. |
| Service Health | Configure a service tag list to indicate the Session Agent Group assigned to the interface on the ESBC. |
| Session Agent | Configure and enable a session agent. See "Session Agent Configuration" and "Configuring a Session Agent" in the ACLI Configuration Guide. |
| Session Agent ID Rule | Configure the SIP header and the parameter within the specified header to use to identify the Session Agent. |
| Session Constraints | Configure and enable session constraints. See "Aggregate Session Constraints Configuration" in the ACLI Configuration Guide. |
| Session Group | Configure a session agent group. See the "Session agent Groups" section of the "Session Routing and Load Balancing" chapter in the ACLI Configuration Guide. |
| Session Recording Group | Configure a session recording server group. See the "Configuring SIPREC" section of the "Selective Call Recording SIPREC" chapter in theCall Traffic Monitoring Guide. |
| Session Recording Server | Configure and enable a session recording server. See the "Configuring SIPREC" section of the "Selective Call Recording SIPREC" chapter in theCall Traffic Monitoring Guide. |
| Session Timer Profile | Configure a session timer profile. See "Sip-Config option session-timer-support" and "ACLI Configuration" in the ACLI Configuration Guide. |
| Session Translation | Configure the translation rules for calling and called numbers. See the session translation topics in the "Number Translation" chapter of the ACLI Configuration Guide. |
| SIP Advanced Logging | Configure logging of specific SIP requests by criteria. See "Advanced Logging" in the "Maintenance and Troubleshooting" chapter of the ACLI Configuration Guide. |
| SIP Config | Configure and enable signaling and session management. See the "SIP Signaling Services" chapter of the ACLI Configuration Guide. |
| SIP Feature | Configure SIP option tag parameters. See "SIP Options Tag Handling" in the "SIP Signaling Services" chapter of the ACLI Configuration Guide. |
| SIP Feature Caps | Configure to support SRVCC handover and other ATCF functionality. See "sip-feature-caps" in the ACLI Reference Guide. |
| SIP Interface | Configure and enable a SIP interface. See "SIP Interface Configuration" in the ACLI Configuration Guide. |
| SIP Manipulation | Configure SIP manipulation. See "Configuring SIP Manipulations" in the "SIP Signaling Services" chapter of the ACLI Configuration Guide. |
| SIP Monitoring | Configure and enable SIP monitor and trace features. See the "Introduction to SIP Monitor and Trace" chapter in the Call Traffic Monitoring Guide. |
| SIP Recursion Policy | Configure a recursion policy. See the "SIP Configurable Route Recursion" section of the "SIP Signaling Services" chapter of the ACLI Configuration Guide. |
| Surrogate Agent | Configure a surrogate agent. See the Surrogate Agents topics in the "SIP Signaling Services" chapter of the ACLI Configuration Guide. |
| Survivability | Configure and enable survivability. See the "Remote Survivability" chapter in the ACLI Configuration Guide. |
| Translation Rules | Configure and apply session translation rules to an agent and a realm. See the "Translation Rules" section of the "Number Translation" chapter in the ACLI Configuration Guide. |
System Configuration
You can configure the following System objects from the Configuration tab on the Web GUI. See the documentation specified in the following list for explanations of these configuration objects and how to set their parameters.
| Capture Receiver | Enable and configure a capture receiver. See the "Capture Receiver" section of the ACLI Reference Guide. |
| Fraud Protection | Enable and configure fraud protection. See the "Telephony Fraud Protection" section of the "System Configuration" chapter in the ACLI Configuration Guide. |
| Host Route | Add one or more host routes. See the "Host Routes" section of the "System Configuration" chapter in the ACLI Configuration Guide. |
| HTTP Client | Use to specify the interface and IP address from which the E-SBC makes HTTP requests. See "Configure the HTTP Client" in the ACLI Configuration Guide. |
| HTTP Server | Use to enable the REST API or the Web interface. See "HTTP Server" and "Enable the HTTP Server" in the ACLI Configuration Guide. |
| Network Interface | Add one or more network interfaces. See the "Network Interfaces" section of the "System Configuration" chapter in the ACLI Configuration Guide. |
| Network Parameters | Configure SCTP and TCP parameters for the network. See the "Stream Control Transfer Protocol Overview" and "System TCP Keepalive Settings" sections of the "System Configuration" chapter in the ACLI Configuration Guide. |
| NTP Config | Add one or more NTP servers and authentication servers. See the "NTP Synchronization" section of the "System Configuration" chapter in the ACLI Configuration Guide. |
| Phy Interface | Add one or more physical interfaces. See the "Phy Interfaces" section of the "System Configuration" chapter in the ACLI Configuration Guide. |
| Redundancy Config | Enable redundancy and add one or more peers. See the "SIP Server Redundancy" section of the "SIP Signaling Services" chapter in the ACLI Configuration Guide. |
| SNMP Address Entry | Add one or more SNMP addressees. See "SNMP-Address-Entry" in the ACLI Reference Guide. |
| SNMP Community | Add and specify one or more Simple Network Management Protocol (SNMP) communities. See "SNMP v1 v2 Community Configuration" in the ACLI Configuration Guide and "SNMP-Community" in the ACLI Reference Guide. |
| SNMP Group Entry | Add one or more SNMP groups. See "SNMP-Group-Entry" in the ACLI Reference Guide. |
| SNMP User Entry | Add one or more SNMP users. See "SNMP-User-Entry" in the ACLI Reference Guide. |
| SNMP View Entry | Add one or more SNMP views. See "SNMP-View-Entry" in the ACLI Reference Guide. |
| SPL Config | Add an SPL option and one or more plug-ins. See the "SPL Plug-in Language" chapter in the ACLI Configuration Guide. |
| System Access List | Add one or more system access lists. See "System Access List" in the ACLI Reference Guide. |
| System Config | Configure the system settings for MIBS, SNMP functions, syslog servers, comm monitor, and more. See the "System Configuration" chapter in the ACLI Configuration Guide. |
| TDM Config | Enable and configure Time Division Multiplexing (TDM). See the Time Division Multiplexing Guide. For the Acme Packet 1100, only. |
| Threshold Crossing Alert | Configure an alarm threshold type to indicate the resource to monitor. See "Configurable Alarm Thresholds and Traps" section in the "System Configuration" chapter in the ACLI Configuration Guide. |
| Trap Receiver | Add one or more trap receivers. See "Trap Receiver" in the ACLI Reference Guide. |