IPsec VPN Termination
Expanding on the IPsec in Conduit feature introduced in 4.4, Edge 5.0 release allows third party devices to terminate IPsec VPN Tunnels on the LAN or WAN side of Oracle Talari Appliances. Now you can secure site-to-site IPsec Tunnels terminating on an Oracle Talari Appliance using a 140-2 Level 1 FIPS certified IPsec cryptographic binary.
Note: Bandwidth provisioning is not available for LAN side IPsec VPN termination.
If you plan to implement Certificates for IKE negotiation, navigate to Sites, and then Certificates and add any necessary certificates.
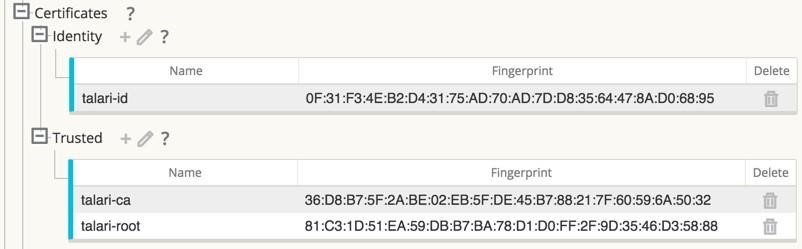
Figure 26: Certificates for IKE Negotiation
Navigate to Connections, and then [Site Name], and then IPsec Tunnels to create an IPsec Tunnel.
You can configure the following criteria, and click Apply to save your settings:
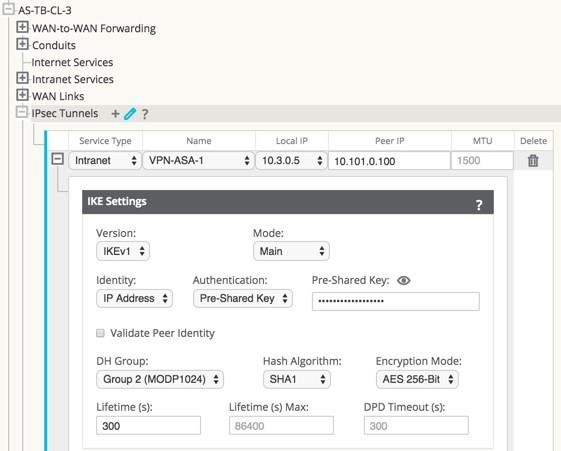
Figure 27: IPsec IKEv1 Settings
- Service Type: Choose either Intranet or VPN from the drop-down menu.
- Name: If the Service Type is Intranet, choose from the list of configured Intranet Services in the drop-down menu. If the service type is LAN, enter a unique Name.
- Local IP: Choose the Local IP address of the IPsec Tunnel from the drop-down menu of available Virtual IP Addresses configured at this Site.
- Peer IP: Enter the Peer IP address of the IPsec Tunnel.
- MTU: The default is 1500, but you can enter a different value.
- IKE Settings
- Version: Choose either IKEv1 or IKEv2 from the drop-down menu.
- Mode: For IKEv1, choose either Main or Aggressive from the Mode drop-down menu.
- Identity: Choose either Auto or IP Address from the Identity drop-down.
- Authentication: Choose
either Pre-Shared Key or Certificate from the Authentication drop-down menu.
- Pre-Shared Key: If
you are using a Pre-Shared Key, copy and paste it into this field. Click on the
Eyeball (
 ) icon to view the Pre-Shared Key.
) icon to view the Pre-Shared Key.
- Certificate: If you are using an Identity Certificate, choose it from the drop-down menu.
- Pre-Shared Key: If
you are using a Pre-Shared Key, copy and paste it into this field. Click on the
Eyeball (
- Validate Peer Identity: Click the Validate Peer Identity checkbox to validate the
IKE's Peer Identity. If the peer's ID type is not supported, do not enable this feature.
- DH Group: Choose the Diffie–Hellman group (Group 1, Group 2, or Group 5) to use for IKE key generation from the drop-down menu.
- Hash Algorithm: Choose MD5, SHA1, or SHA-256 from the drop-down menu to authenticate IKE messages.
- Encryption Mode: Choose AES 128-bit, AES 192-bit, or AES 256-bit as the Encryption Mode for IKE messages from the drop-down menu.
- Lifetime (s): Enter the preferred duration, in seconds, for an IKE security association to exist. The default is 3600 seconds.
- Lifetime Max (s): Enter the maximum preferred duration, in seconds, to allow an IKE security association to exist. The default is 86400 seconds.
- DPD Timeout (s): Enter the Dead Peer Detection timeout, in seconds, for VPN connections. The default is 300 seconds.
- IKEv2 Settings
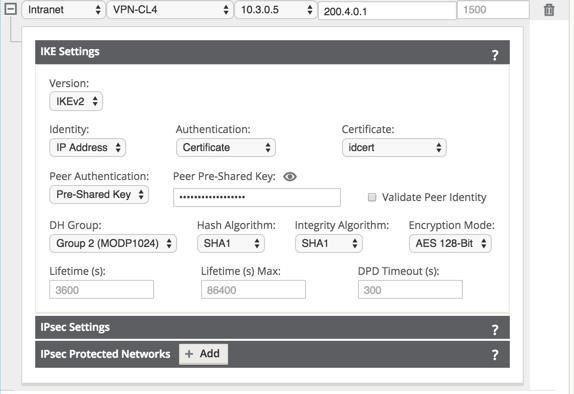
Figure 28: IPsec IKEv2 Settings
- Peer Authentication: Choose Mirrored, Pre-Shared Key, or Certificate Peer Authentication from the drop-down menu.
Peer Pre-Shared Key: Paste the IKEv2 Peer Pre-Shared Key into this
field for authentication. Click on the Eyeball (![]() ) icon to view the Pre-Shared Key.
) icon to view the Pre-Shared Key.
- Integrity Algorithm: Choose MD5, SHA, or SHA-256 as the hashing algorithm to use for HMAC verification from the drop-down menu.
- IPsec Settings
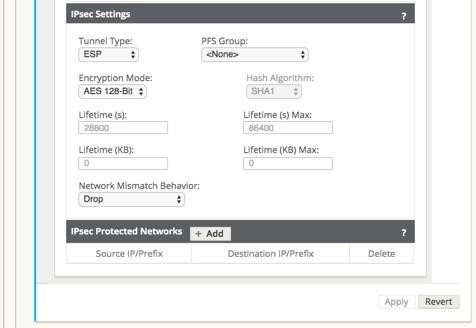
Figure 29: IPsec Settings and IPsec Protected Networks
- Tunnel Type: Choose ESP, ESP+Auth, or AH as the Tunnel Type from the dropdown menu.
- PFS Group: Choose the Diffie–Hellman group (Group 1, Group 2, or Group 5) to use for perfect forward secrecy key generation from the drop-down menu.
- Encryption Mode: If you chose ESP or ESP+ Auth, choose AES 128-bit, AES 192bit, or AES 256-bit as the Encryption Mode for IPsec messages from the drop-down menu.
- Hash Algorithm: If you chose ESP+Auth or AH as the Tunnel Type, choose MD5, SHA1, or SHA-256 from the Hash Algorithm drop-down menu to use for HMAC verification.
- Lifetime (s): Enter the amount of time, in seconds, for an IPsec security association to exist. The default is 28800 seconds.
- Lifetime Max (s): Enter the maximum amount of time, in seconds, to allow an IPsec security association to exist. The default is 86400 seconds.
- Lifetime (KB): Enter the amount of data, in kilobytes, for an IPsec security association to exist.
- Lifetime Max (KB): Enter the maximum amount of data, in kilobytes, to allow an IPsec security association to exist.
- Network Mismatch Behavior: Choose Drop, Send Unencrypted, or Use Non-IPsec Route as the desired action for your Talari WAN to take if a packet does not match the IPsec Tunnel's Protected Networks from the drop-down menu.
- IPsec Protected Networks
- Source IP/Prefix: After clicking the Add (+ Add) button, enter the Source IP and Prefix of the network traffic the IPsec Tunnel will protect.
- Destination IP/Prefix: Enter the Destination IP and Prefix of the network traffic the IPsec Tunnel will protect.