Zscaler Integration
Zscaler is a Cloud Security Provider (CSP) that delivers key Next Generation Firewall features including Intrusion Detection System (IDS), Intrusion Prevention System (IPS), Data Loss Prevention (DLP), and Sandboxing.
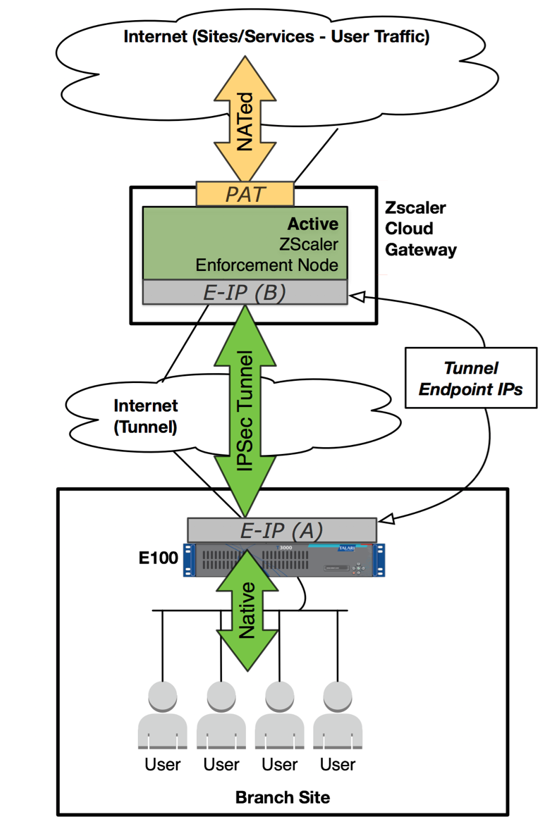
Introduced in APN R7.0 GA, users can now integrate a branch office Oracle Talari Appliance with the Zscaler Cloud Security Gateway via IPSec tunneling, for the purposes of tunneling Internet-destined traffic to Zscaler for cloud-hosted filtering and security services.
Configuration
To configure a Zscaler IPSec tunnel, navigate to Manage Network > Configuration Editor on the NCN and Import the current configuration file. Click on the Advanced tab, expand Connections > [Site Name] > IPSec Tunnels and click the (+) icon.
Select Zscaler as the Service Type, select the Local IP address, fill in the Peer IP address of the Zscaler Enforcement Node (ZEN), enter the IKE Pre-Shared Key, and click Apply.
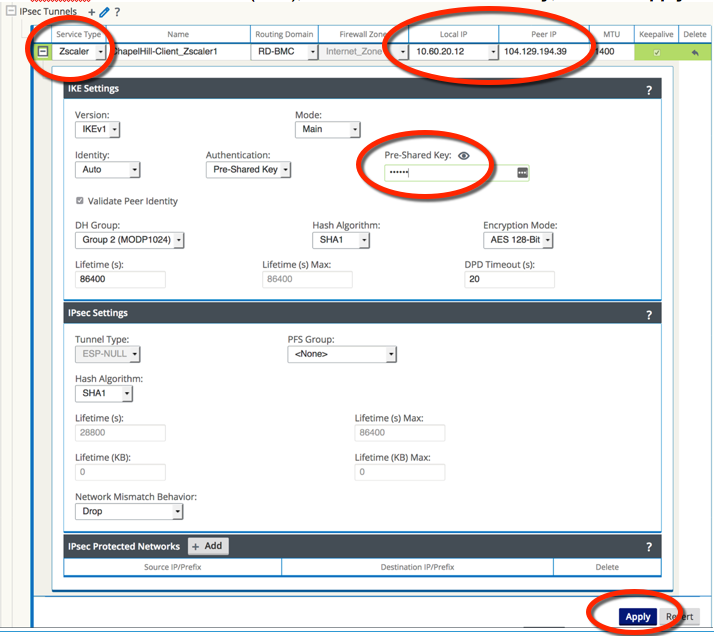
Note:
When you add an IPSec tunnel with a Service Type of Zscaler, the following default configurations will be applied that are not applied when selecting LAN or Intranet Service Types.- Firewall – Adds a Deny policy from Default_LAN_Zone to Untrusted_Internet_Zone.
- NAT – Deletes the default outbound PAT policy, if one exists.
- Routing – Adds a 0.0.0.0/0 route over the Zscaler tunnel and a /32 host-route of the tunnel Peer IP to the gateway.
Save the configuration and Export it to Change Management. Follow the Change Management process to Stage and Activate the new configuration.
Verification
Once the new configuration is running, follow the steps below to verify functionality.
1. Generate Internet traffic from a host on the LAN to a URL that has been blocked by Zscaler.
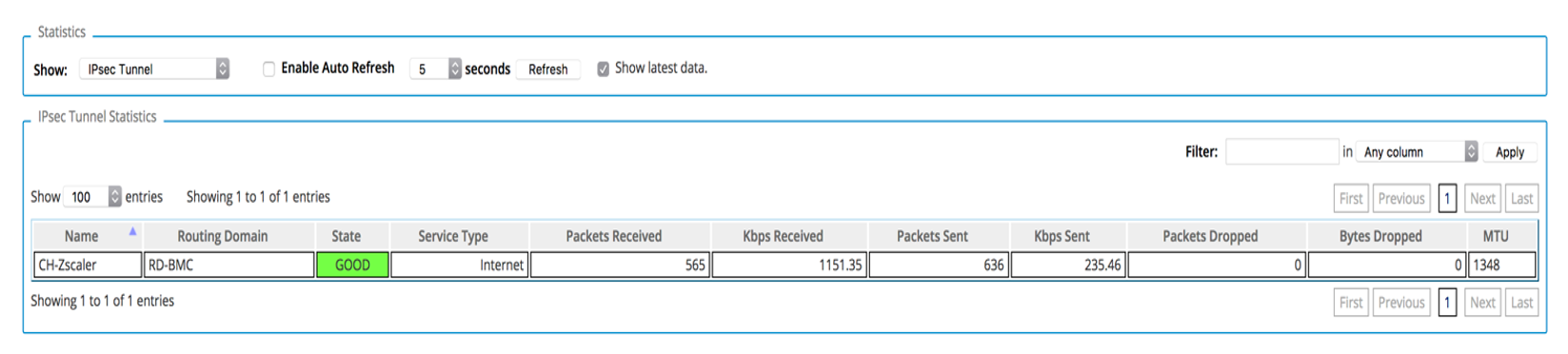
2. Verify the Zscaler IPSec Tunnel status in the web UI of the Oracle Talari Appliance under Monitor > Statistics > IPSec Tunnel.
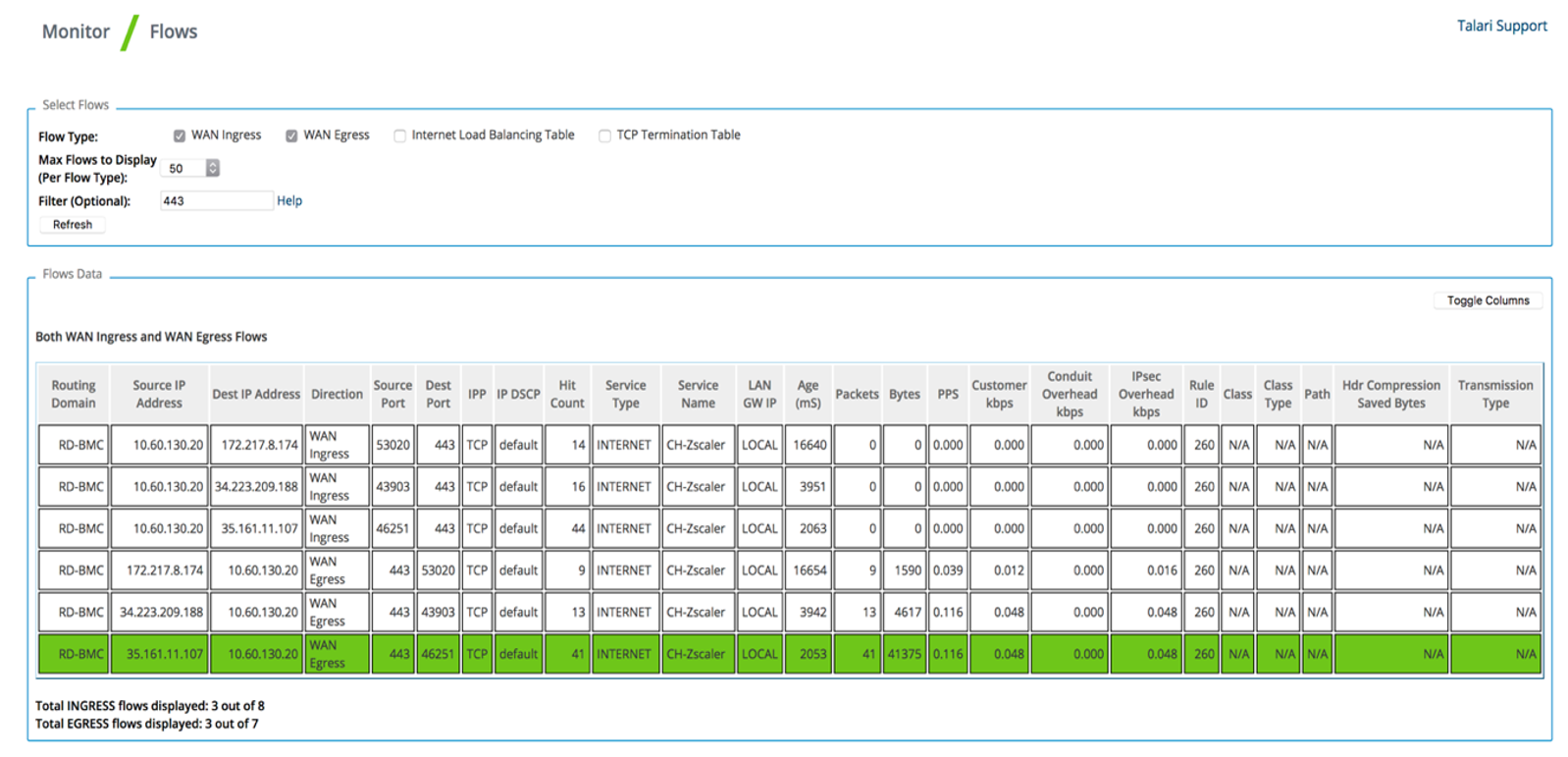
3. Verify the flow of the generated traffic through the Oracle Talari Appliance via Monitor > Flows. Once you have identified the flow, confirm the Service Type as INTERNET.
4. Verify Zscaler is blocking the traffic.
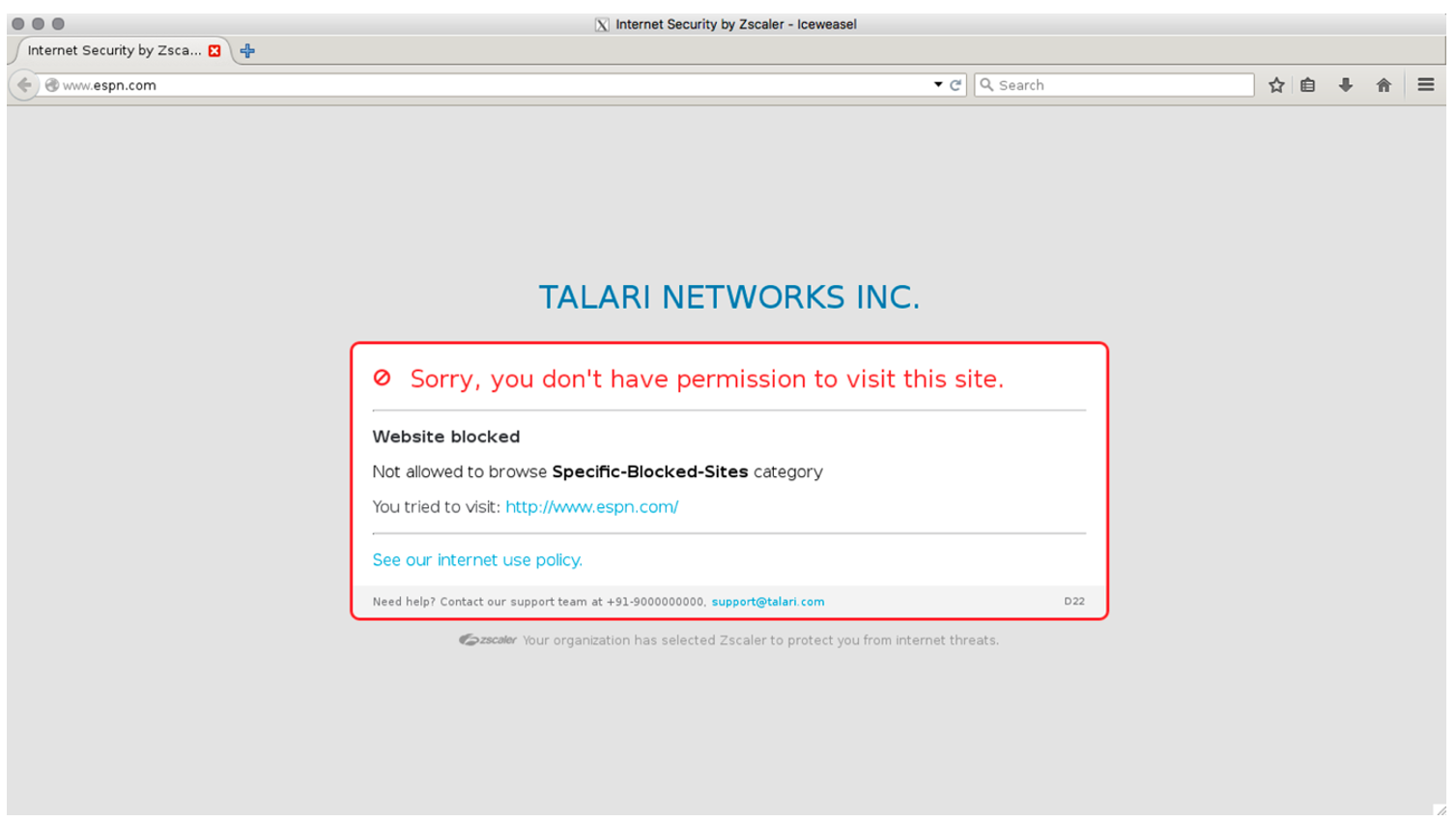
In the event the IPSec Tunnel between the Oracle Talari Appliance and the Zscaler ZEN goes down, the 0.0.0.0/0 route through the tunnel will become unreachable and pulled from the routing table. Traffic will hit the next available, reachable 0.0.0.0/0 route out to the Internet. Route reachability can be verified in the Oracle Talari Appliance's web UI under Monitor > Statistics > Routes.
Note:
R7.0 GA only supports a single VRF/routing domain for Zscaler.