8 IKE / IPSec Configuration
LAN, Internet, and Intranet IPSec Tunnel Configuration
IPsec is a common encryption protocol for IP communications. It has the capability to use multiple types of encryption for data confidentiality, as well as multiple hash algorithms to ensure data integrity. However, IPsec is a statically configured protocol and relies on other systems to negotiate security parameters. The most common protocol used is Internet Key Exchange (IKE). IKE negotiates one set of security parameters to secure its own information exchange, then negotiates an independent set of security parameters for the IPsec tunnel.
Access the IPSec configuration elements by navigating to Site, Advanced, IPSec Tunnels. Use the plus symbol (+) to add a new element and use the pencil marker symbol to edit an existing record.
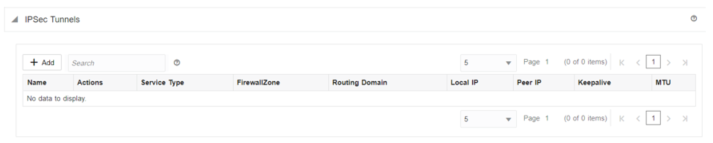
- Intranet
- LAN (default)
- Palo Alto
- Ascalar
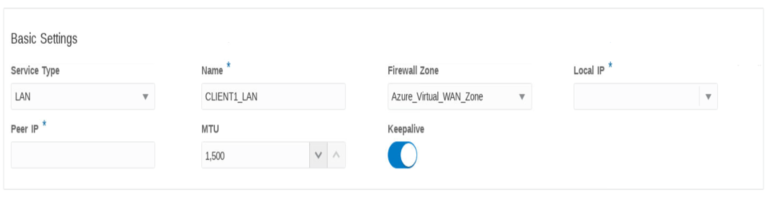
- Name—Select the auto-generated name or type in the text in the name box.
- Firewall Zone—Select an entry from drop down list.
- Local IP—Dropdown list of Virtual IPs or Interface name for a DHCP-enabled interface.
- Peer IP—The other end of the component for which IPsec tunnel needs to be established.
- MTU—The default value is 1500 bytes.
- Keepalive—Is a check box, if enabled the appliance will trigger IKE and IPSec rekey.
IKE Settings
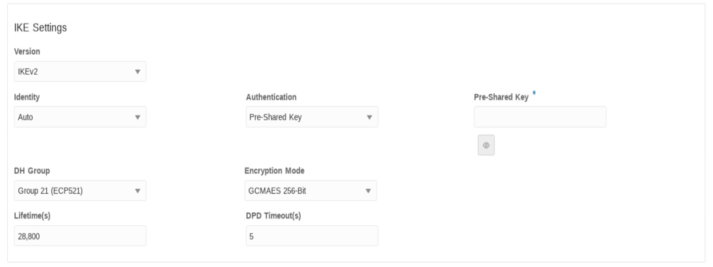
- Version—The IKE version used to initiate the ISAKMP.
Valid values:
- IKEv1
- IKEv2 (default)
- Mode (IKEv1 only)—Phase 1 parameter exchange in Main
mode or Aggressive mode. Valid values:
- Main (default)
- Aggressive
- Identity—Identity of the IKE interface. Valid
values:
- Auto (default)—IP address for PSK authentication, Certificate DN for certificate authentication
- IP Address— IP address of the appliance from which IKE interacts.
- Authentication—The mode in which peer can
authenticate the appliance. Valid values:
- Pre-shared key (default)
- Certificate
- Pre-Shared Key—This field appears only if the authentication method is Pre-shared key. This field is for secret key of the peer.
- Certificate—This field appears only if the authentication method is Certificate. Select an entry from any of the pre-configured certificate names which appear in the drop-down list.
- DH Group—Supported DH groups in the appliance MUST
select one from the drop down list. Valid values:
- Group 5 – (Modp1536)
- Group 19 – (ECP256)
- Group 20 – (ECP384)
- Group 21 – (ECP521) (default)
- Encryption Mode—Encryption algorithms used for
encryption in phase2 of ISAMKP. Valid values:
- AES 128-bit
- AES 192-bit
- AES 256-bit
- GCM AES 256-bit (default)
- Hash Algorithms (AES Encryption Mode Only)—Supported
hashing algorithms in the appliance MUST select one from the drop down list.
Valid values:
- SHA1
- SHA256 (default)
- Lifetime—Proposed IKE SA lifetime value, in seconds,
for the IKE SA established during IKE phase 1 negotiation. Valid values:
- Min: 0
- Max: 86400
- Default: 28,800
- DPD Timeout—Timer value in seconds when to send DPD
message to peer. Valid values:
- Min: 0
- Max: 86400
- Default: 5
IPSec Settings
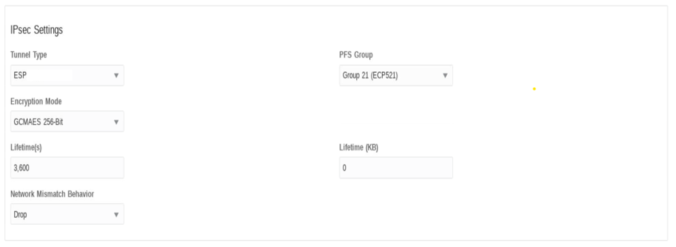
- Tunnel Type—Type of IPsec child SAs that can be
established in phase 2. Valid values:
- ESP (Encapsulating Security Payload) (default)
- ESP + Auth
- PFS Group—DH group exchange used for Perfect Forward
Secrecy. Valid values:
- <None>
- Group 5 – (Modp1536)
- Group 19 – (ECP256)
- Group 20 – (ECP384)
- Group 21 – (ECP521) (default)
- Encryption Mode—Encryption algorithms used in IPSec
SAs. Valid values:
- AES 128-bit
- AES 192-bit
- AES 256-bit
- GCM AES 256-bit (default)
- Hash Algorithms (AES Encryption Mode Only)—Supported
hashing algorithms in the appliance MUST select one from the drop down list.
Valid values:
- SHA1
- SHA256 (default)
- Lifetime—Proposed IPSec SA lifetime value in seconds
for the IPSec SA established during IKE phase 2 negotiation. Valid
values:
- Min: 0
- Max: 86400
- Default: 3600
- Lifetime (KB)—Amount of data, in kilo bytes for an
IPSec SA to exist. Values:
- Min: 0
- Max: 4194303
- Default: 0
- Network Mismatch Behavior—Choose an action to take if
a packet does not match the IP Sec tunnel’s protected network. Valid
values:
- Drop (default)
- Send unencrypted
- Use Non-IPSec Route
- IPSec Protected Networks—The allowable set of IP addresses to use IPSec tunnels.
- Source IP/Prefix—The source IP address which is allowed to use IPSec tunnels.
- Destination IP/Prefix—The destination IP address which is allowed to use IPSec tunnels.
Certificate Configuration
In order to support IKE certificate authentication, an ability to define Identity and Trusted certificates will be created in the configuration editor. To add certificates, click Sites, select a site, Advanced, Certificates. Use the plus symbol (+) to add a new element and use the pencil marker symbol to edit the existing records.
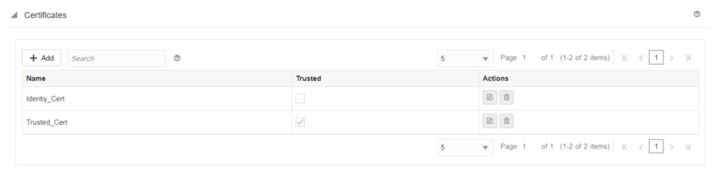
To create a new entry, click on the plus symbol (+), enter a certificate name, and paste the public and private keys.
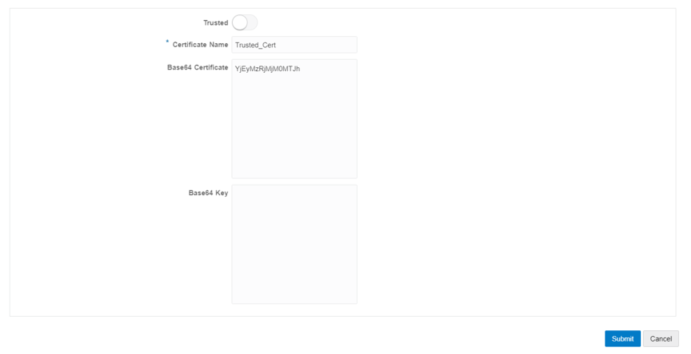
- Trusted—Toggle between Identify and Trusted type of certificate.
- Base64 Certificate—Enter or paste the base certificate. This is required for both types of certificates.
- Base64 Key—Public key if the certificate type is Identity.