12 Settings
The Oracle® Communications Security Shield Cloud Service (Security Shield) Settings page displays information that you need for installing the Cloud Communication Service and provides links to system-wide settings.
Settings Controls and Actions
Oracle® Communications Security Shield Cloud Service (Security Shield) Settings provides links to dialogs where you set thresholds, behaviors, and enforcement actions for call traffic. Before you install the Cloud Communication Service (CCS), refer to the CCS Configuration link which provides information that the CCS installation script requires you to supply.
The following screen capture shows the Settings landing page, which defaults to the CCS Configuration page.
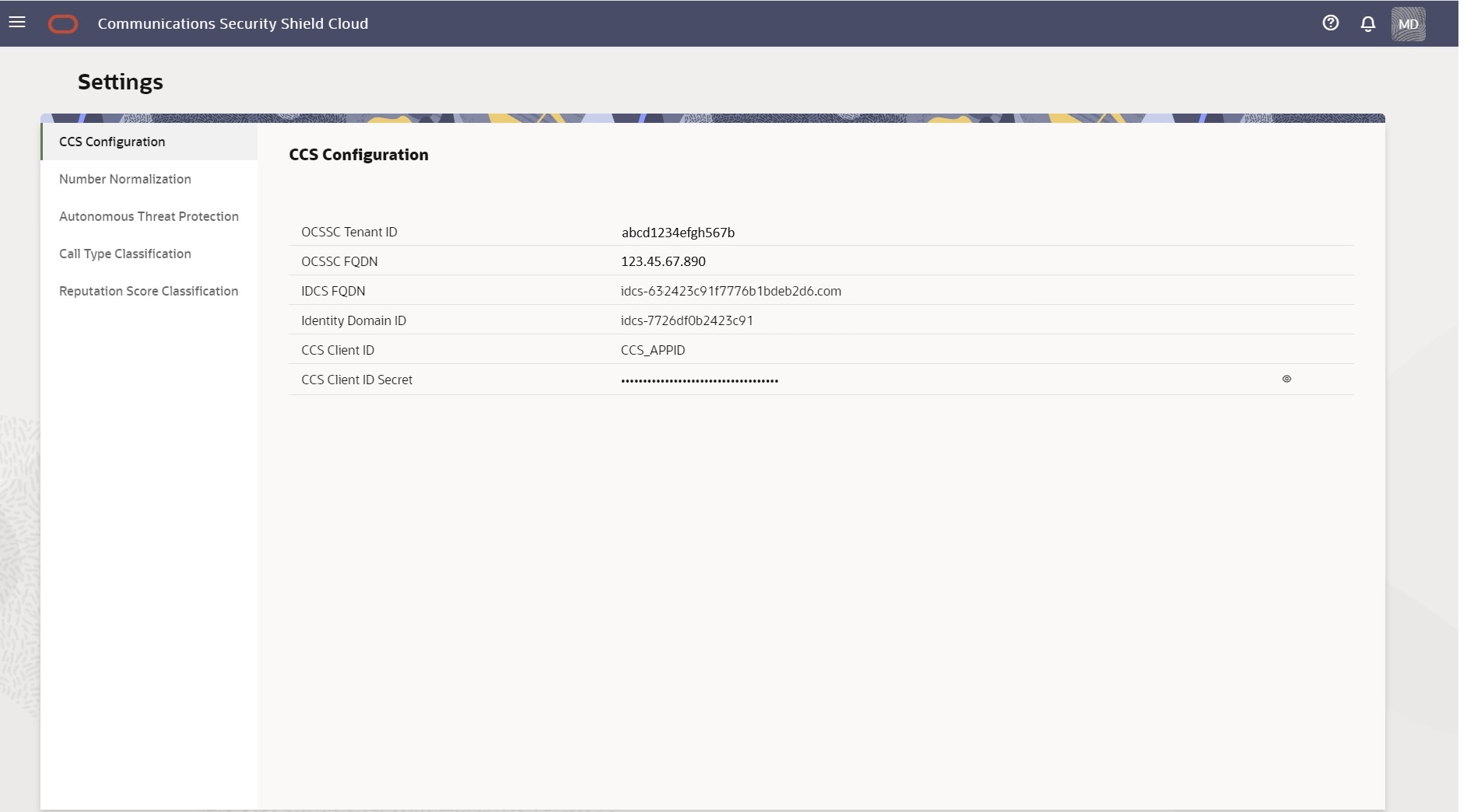
CCS Configuration—Displays information that you need to provide when installing the Cloud Communication Service. (You cannot edit the information displayed here.)
Number Normalization—Displays a table of Inbound Calling Number Normalization rules. The system provides two default rules. You can create up to twenty-three more rules.
Autonomous Threat Protection—Displays configuration dialogs for configuring General (settings), Threat Vector Thresholds, and Domain Thresholds.
Call Type Classification—Displays descriptions of call type classifications and provides configurable enforcement settings.
Reputation Score Classification—Displays descriptions of reputation score classifications and provides configurable enforcement settings.
Cloud Communications Service Configuration Settings
When you download Oracle® Communications Security Shield Cloud Service (Security Shield) software and unpack the archive.tgz file, the system populates the CCS Configuration fields on the Settings page with information you need when you run the Cloud Communications Service (CCS) installation script.
Access the Settings page and click CCS Configuration to see the CCS Configuration page. The following screen capture shows the CCS Configuration page with sample configuration entries.

Note:
You cannot edit this page from Security Shield. Make edits through your Oracle Cloud Infrastructure (OCI) account.See "Install, Configure, and Activate the Cloud Communication Service" in the Security Shield Installation and Maintenance Guide.
Inbound Calling Number Normalization Settings
Oracle® Communications Security Shield Cloud Service (Security Shield) uses the E.164 format for phone numbers sent in the look-up API from the Oracle Communications Session Border Controller (SBC). Because Security Shield is often deployed in scenarios that use phone number formats other than E.164, Security Shield provides a way to normalize inbound calling numbers through translation rules.
Inbound calling number normalization rules translate phone numbers into the E.164 format when your SBC receives traffic that uses other phone number format conventions. Security Shield can normalize inbound phone numbers from multiple SIP trunk providers, as well. In this way, Security Shield can work with different countries, formats, and SIP Trunk providers.
To see the Number Normalization page, go to the Settings tab and click Number Normalization in the navigation pane. The following screen capture shows the Number Normalization page, which displays the Enable-Disable toggle and the Add Normalization Rule button. The following screen capture shows the Number Normalization page before any rules exist.
The following screen capture shows the Number Normalization page with examples of entries. Depending on the number of entries, you may need to scroll to see all of them.
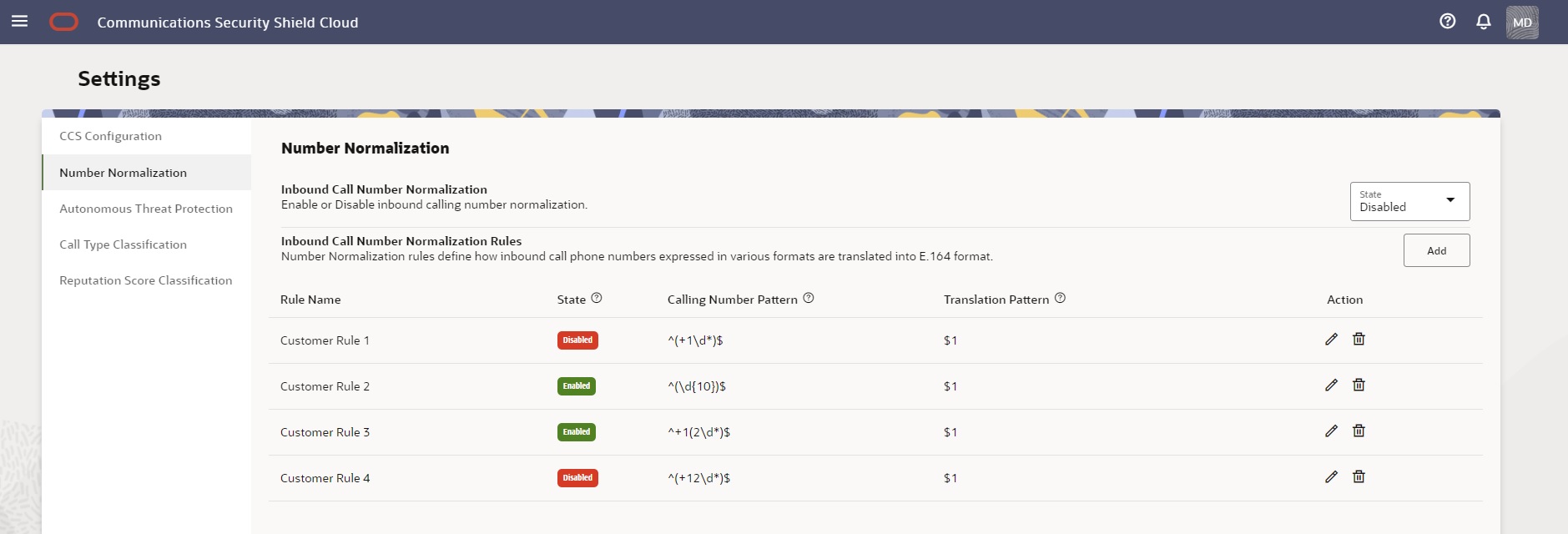
- Rule Name—Shows the list of rules in alphabetical order with no order of precedence for enforcement.
- State—Shows whether the rule is enabled or disabled. Regardless of the state, you can add, edit, and delete the rule.
- Calling Number Pattern—The regular expression that specifies a phone number for non-normalized inbound calling numbers that you want normalized into E.164 format. For example, the calling number pattern regular expression ^0(\d{6,9})$ describes phone numbers that start with 0 and are 7 to 10 digits long.
- Translation Pattern—The regular expression that specifies how to translate non-normalized inbound calling numbers that match the calling number pattern regular expression into E.164 format. The regular expression consists of Country Code to prepend (if specified) and $1. $1 captures the characters in the calling number regular expression included in side the parenthesis. For example, the translation pattern regular expression 31$1 adds a prefix of 31 to the captures (the phone number patterns characters in parenthesis.
- Action—The pencil icon displays the Edit Number Normalization Rule drawer where you specify the parameters of the rule. The trash can icon deletes the rule.
Using number normalization rules is optional, and Security Shield defaults to the disabled state. When no Number Normalization rule exists, Security Shield uses the calling number as received in either the FROM or PAI. When Number Normalization rules exist, Security Shield applies the rule to the calling number in the FROM and PAI. Phone number normalization works regardless of optional Header Manipulation Rules (HMR) on the Oracle Communications Border Controller that may manipulate the number.
Only a user assigned to the OCSS Configuration Editor role can add, edit, or delete phone Number Normalization rules. Security Shield supports up to twenty-five number normalization rules, including the two default rules.
Note:
The Activity log captures changes to number normalization and provides a filter called Inbound Call Number Normalization to help you find the changes.See Syntax for Inbound Number Normalization Regular Expressions and Add New Inbound Phone Number Normalization Rules.
Default Inbound Calling Number Normalization Rules
Oracle® Communications Security Shield Cloud Service (Security Shield) provides two default inbound calling number normalization rules. A user assigned to the OCSS Configuration Editor role can enable, disable (default), and edit the rules.
International rule for North America and Caribbean
When the calling number of an inbound call includes an International Direct Dialing (IDD) prefix of 011, remove the 011 prefix. For example: translate 01144206555121 to 44206555121.
- Rule Name—International Inbound Calls in North America and Caribbean with 011 IDD Prefix (Remove IDD prefix)
- State—Enabled
- Calling Number Pattern—^011(\d*)$
- Translation Pattern—$1
National rule for North America and Caribbean
National rule for North America and Caribbean. When the calling number of an inbound call is a ten digit E.164 number, prepend it with 1. For example, translate 2065551212 to 12065551212.
- Rule Name—North America and Caribbean Domestic Calls (Prepend 1)
- State—Enabled
- Calling Number Pattern—^(\d{10})$
- Translation Pattern—1$1
Inbound Calling Number Normalization Configuration Parameters
When you create a rule for inbound calling number normalization, Oracle® Communications Security Shield Cloud Service (Security Shield) uses the settings in the Add Number Normalization Rule drawer to create the regular expressions needed for normalizing phone numbers. You can add, edit, and delete rules with the service enabled or disabled.
The following screen capture shows the Add Number Normalization Rule drawer for creating Inbound Calling Number Normalization rules.
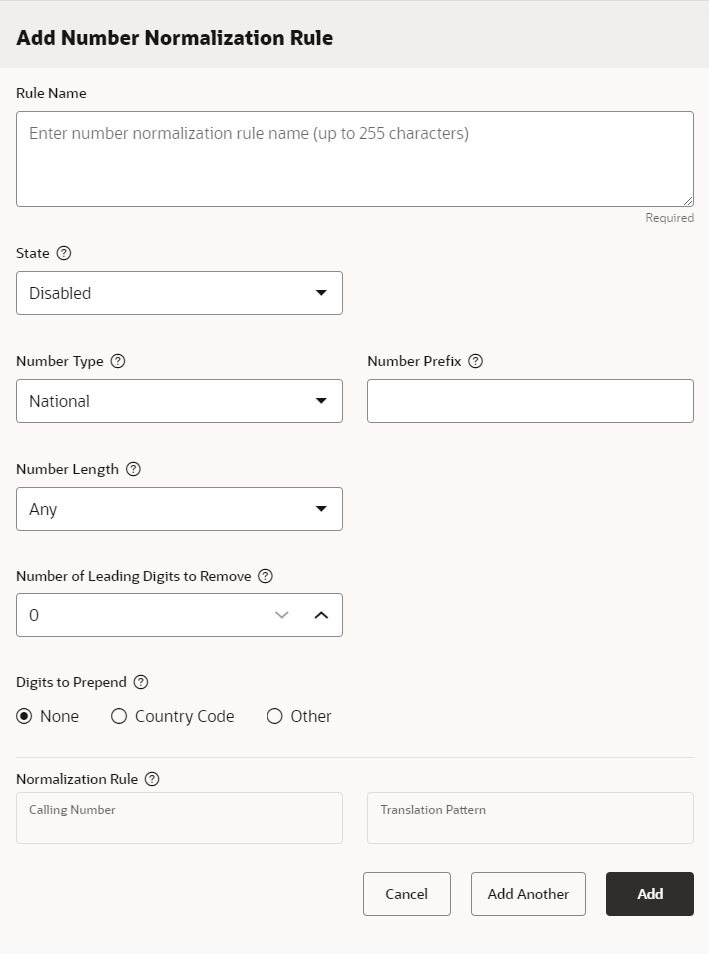
Number Normalization Rule Configuration Parameters
Rule Name—The rule name can contain up to 255 characters, so you can make the name descriptive and unique. The table on the Number Normalization page lists the rules in alphabetical order. Security Shield enforces the rules in the following order of precedence:
State—The state of the rule, either enabled or disabled.
- National—The dialog displays the Number Length and Digits to Prepend fields.
- International—The dialog hides the Number Length and Digits to Prepend fields.
Number Prefix—The leading digits (including the + character) of the inbound calling numbers that you want the calling number pattern to match.
- When you select Range, the dialog displays counters for setting the minimum and maximum number of digits.
- When you select Exactly, the dialog displays a counter for setting the number.
Number of Leading Digits to Remove—The number of leading digits you want removed (including the + character).
- None—Hides the digits entry field.
- Country Code—Displays the "Select Country" field and drop-down list.
- Other—Displays a blank field where you can enter 1-15 digits.
Calling Number Pattern—Not directly configurable. Shows the regular expression for capturing non-conforming inbound calling numbers that you want Security Shield to normalize into the E.164 format. Security Shield generates and displays the pattern in the Add and Edit dialogs as you configure the rule. For example, the calling number pattern regular expression ^0(\d{6,9})$ describes phone numbers that start with 0 and are 7 to 10 digits long.
Translation Pattern—Not directly configurable. Shows the regular expression for how to translate non-conforming inbound calling numbers that match the calling number pattern into the E.164 format. Security Shield generates and displays the pattern in the Add and Edit dialogs as you configure the rule. The regular expression consists of the Country Code or a 1-15 digit number (if specified) and $1. $1 captures the characters in the Calling Number Pattern regular expression included inside the parenthesis. For example, the translation pattern regular expression 31$1 adds a prefix of 31 to the captures (the phone number pattern characters in parenthesis), which translates the calling number 0206551212 to 31206551212.
Note:
Security Shield automatically generates both the Calling Number Pattern and Translation Pattern regular expressions as you configure the rule using the Number Prefix, Number Length, Number of Digits to Remove, and Country Code to Append values you specify. See Syntax for Inbound Number Normalization Regular Expressions.Syntax for Inbound Number Normalization Regular Expressions
Oracle® Communications Security Shield Cloud Service (Security Shield) uses regular expressions to specify the patterns for inbound phone number normalization calling number matching and translation.
Security Shield automatically generates or updates the regular expressions for both the Calling Number pattern and Translation pattern from the Number Prefix, Number Length, Number of Digits to Remove, and Country Code to Append values that you specify when you Add New Inbound Phone Number Normalization Rules or Edit an Inbound Calling Number Normalization Rule. The following information describes the characters and syntax used in the regular expressions.
Regular Expression Syntax
Anchors
- ^ Matches the start of a line, not including the first character of the line.
- $ Matches the end of a line, not including the last character or the line.
Marked Group
- ( ) Used to group expressions and to capture a set of characters for use in a back-reference.
Shorthand Character Classes
- \d Matches a numeric digit (0-9)
Repeaters
- * Match the preceding character or expression from zero to unlimited times.
- [n] Match the preceding character or expression exactly n times.
Enable and Disable Inbound Calling Number Normalization Operations
A user assigned to the OCSS Configuration Editor role can enable or disable the Oracle® Communications Security Shield Cloud Service (Security Shield) inbound calling number normalization feature as needed. The default state is enabled.
- Confirm that you are assigned to the OCSS Configuration Editor role.
Note:
You can enable or disable inbound calling number normalization rules individually.- Access the Settings page and click Number Normalization.
- On the Number Normalization page, click
State and do one of the
following:
- Click Enabled. (Default)
- Click Disabled.
Add New Inbound Phone Number Normalization Rules
To specify how Oracle® Communications Security Shield Cloud Service (Security Shield) transposes phone numbers from a variety of formats into the E.164 format, you can create up to twenty-three rules for inbound phone number normalization in addition to the two default rules.
- Confirm that you are assigned to the OCSS Configuration Editor role
- Enable and Disable Inbound Calling Number Normalization Operations
Use the following procedure to add Number Normalization rules.
- Access the Settings page and click Number Normalization.
- On the Number Normalization page, click Add Normalization Rule.
- In the Add Normalization Rule drawer, do the following:
- Name—Enter up to 255 characters to create a unique name or description for the rule.
- State—Set the state for the rule. Valid values: Enabled | Disabled.
- Number Type—Set the geographic scope of the number you want normalized. When you select National, the dialog displays the Number Length and Digits to Prepend fields. When you select International, the dialog hides the Number Length field and Digits to Prepend fields. Valid values: National | International.
- Number Prefix—Set the leading digits (including the + character) you want removed from the inbound calling number. The number of digits (including the + character) you set here must match the number you set in the Number of Leading Digits to Remove parameter. For example, if you enter the prefix +44 here, you must set the Number of Leading Digits to Remove parameter to 3.
- Number Length—Set the rule for matching the number length. When you select Range, the dialog displays controls for setting the minimum and maximum number of digits. Valid values: Any | Exactly | Range.
- Number of Leading Digits to Remove—Set the number of leading digits you want removed (including the + character). The number you set here, must match the number of digits (including the + character) you entered in the Number Prefix parameter.
- Digits to Prepend—Set a choice for the number of digits to prepend. Valid values: None—Hides the digits entry field. | Country Code—Displays the "Select Country" field and drop-down list. | Other—Displays a blank field where you can enter 1-15 digits.
- Calling Number Pattern—Not directly configurable. As you configure the number normalization rule, Security Shield auto fills this field based on your input from the preceding parameters.
- Translation Pattern—Not directly configurable. As you configure the number normalization rule, Security Shield auto fills this field based on your input from the preceding parameters.
- Do one of the following:
- Click Add —Adds the rule to the table and closes the dialog.
- Click Add Another—Adds the rule to the table, keeps the dialog displayed, and clears the settings so you can create another rule.
Edit an Inbound Calling Number Normalization Rule
A user assigned to the OCSS Configuration Editor role can edit an Oracle® Communications Security Shield Cloud Service (Security Shield) inbound calling number normalization rule. Security Shield updates the Calling Number Pattern and Translation Pattern as you edit the rule.
- Confirm that you are assigned to the OCSS Configuration Editor role.
Use the following procedure to edit Number Normalization rules.
Delete an Inbound Calling Number Normalization Rule
A user assigned to the OCSS Configuration Editor role can delete an Oracle® Communications Security Shield Cloud Service (Security Shield) inbound calling number normalization rule.
- Confirm that you are assigned to the OCSS Configuration Editor role.
Use the following procedure to delete Number Normalization rules.
Autonomous Threat Protection Settings
After you install the Oracle® Communications Security Shield Cloud Service (Security Shield) service components, you can optionally change the default Security Shield settings that control and manage call activity passing through your Oracle Communications Session Border Controller (SBC). The default settings allow the Security Shield service to pass calls and perform services without further configuration or intervention. The default settings may or may not suit your business needs, so Oracle recommends that you consider the settings according to your needs and revisit them regularly. Adjusting the settings is a continuous process to engage in as your business evolves. You can make assessments and adjust the settings as needed, for example, to allow for marketing campaigns and daily call peaks.
The Settings page provides the entry point to the dialogs that you use to configure the General, Threat Vector Thresholds, and Domain Thresholds settings.
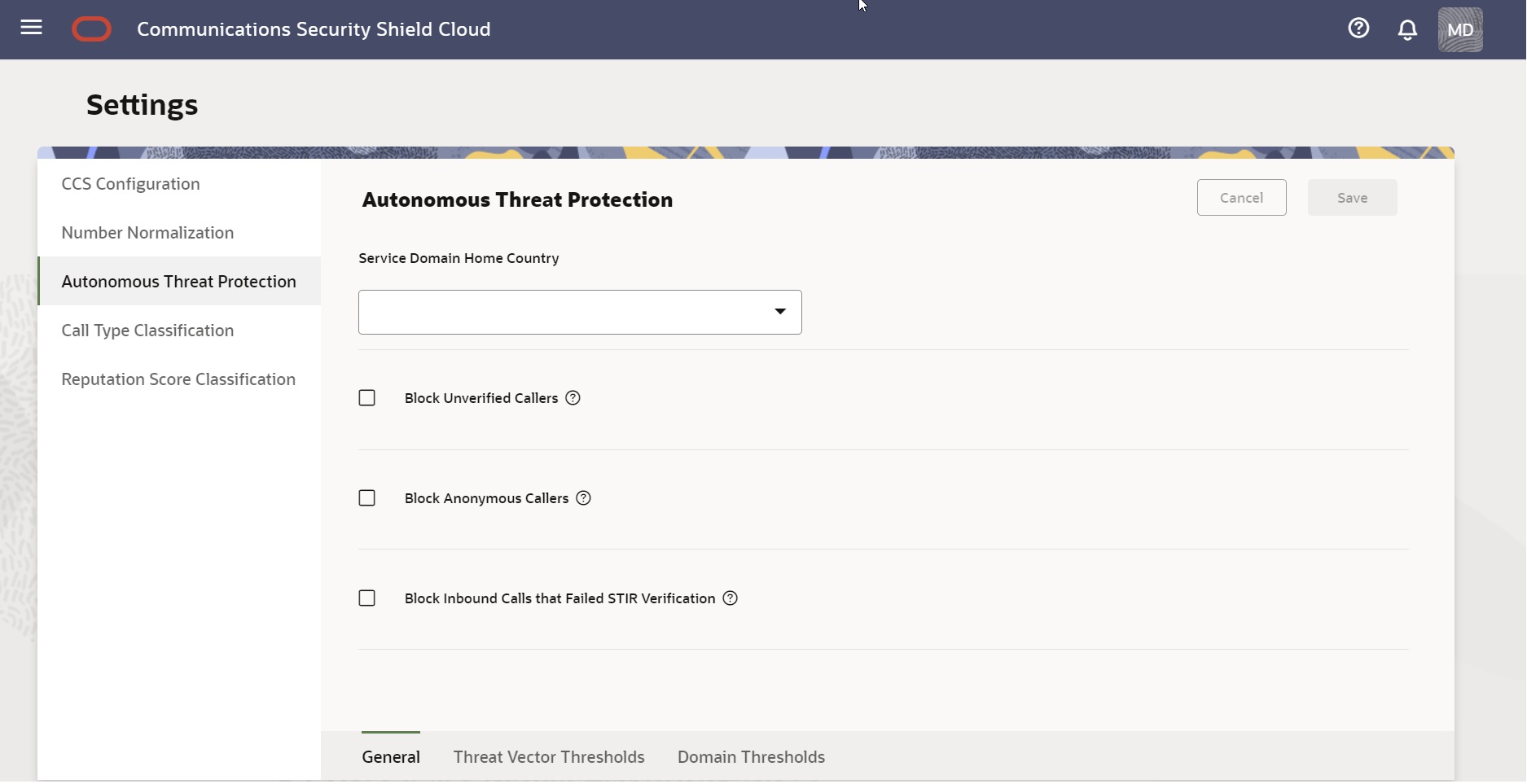
See the following topics for information about the types of Autonomous Threat Protection settings shown in the preceding screen capture.
Autonomous Threat Protection General Settings
On the Settings page, click General to display the autonomous threat protection settings that affect your deployment globally. Oracle recommends that you revisit these settings regularly because adjusting them is a continuous process as your business needs change. For example, you might need to adjust the settings to allow for marketing campaigns and daily call peaks.

Service Domain Home Country—Your physical geographical location. The Security Shield verifies that a call uses the same country code as the home country, which defines all other calls as international. No default.
Block Unverified Callers—When enabled, the Security Shield blocks inbound, unverified callers. Default: Disabled.
Block Anonymous Callers—When enabled, the Security Shield blocks inbound calls that contain Anonymous in one or both of the FROM and P-Asserted Identity headers and one or both of the user name and host name parts. For example, suppose a fraudster removes the user identity and inserts anonymous@, private@, restricted@, user@example1.edu, null@ or other such entries in the FROM or the P-Asserted Identity (PAI) headers. The result makes the caller identification anonymous and unverifiable. You can block such calls. Also, when the FROM header includes a phone number and PAI is either not present or shows a phone number and the Privacy header includes any of the privileged values, such as: "ïd", "user", or "header",Security Shield, blocks the call. Default: Disabled.
Note:
The STIR validation indicator is received from the SIP Trunk provider or Communication Service Provider (CSP) in the INVITE. The STIR validation is not an action by Security Shield. The CSP checks for presence of the parameter, and based on the value, determines whether the STIR validation failed in the service provider network.Edit General Settings
Provisioning the Oracle® Communications Security Shield Cloud Service (Security Shield) requires you to set the Service Domain Home Country to define which calls to consider as in-country. The other settings on the Settings tab are optional.
Use the following procedure to set global settings for your call traffic.
Threat Vector Thresholds
The Threat Vector Thresholds dialog on the Autonomous Threat Protection tab contains settings for managing risky call traffic and call flooding. Oracle sets the defaults for the thresholds, which you can change at any time with no reboot required. Oracle recommends that you revisit the Autonomous Threat Protection settings regularly because adjusting them is a continuous process as your business evolves. You can adjust the settings as needed, for example, to allow for marketing campaigns, daily call peaks, and other reasons for tightening or loosening control of call traffic volume.
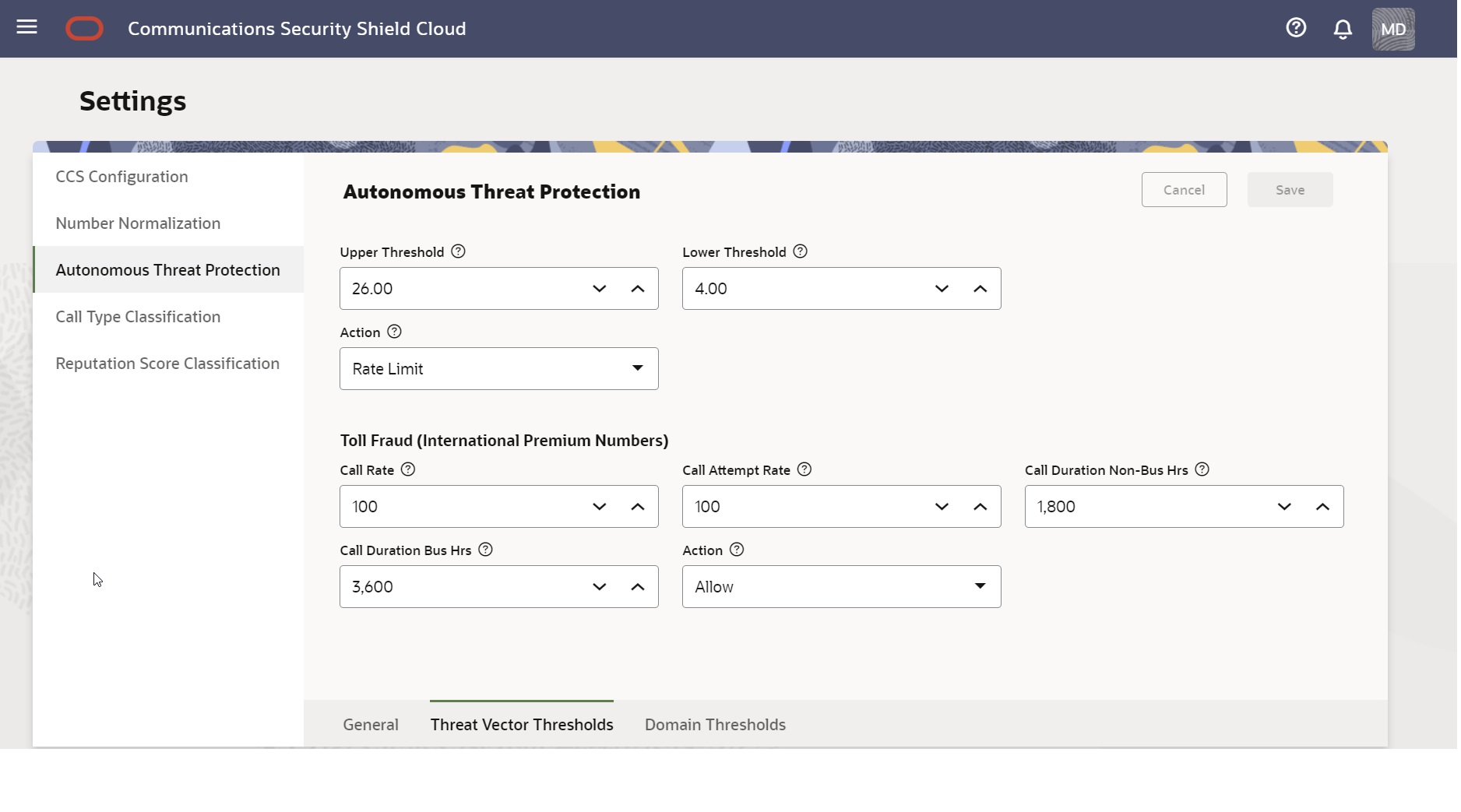
- Call Attempt Rate for Business Hours
- Upper Threshold—Set the number of call attempts per second at which you want the session border controller to recognize call flooding and start performing the configured action during business hours. Default: 25.00 Valid values: 1.00-100.00
- Lower Threshold—Set the number of call attempts per second at which you want the session border controller to resume allowing all calls after a call flooding incident that occurred during business hours. Default: 20.00 Valid values: 1.00-100.00
- Call Attempt Rate for Non-Business Hours
- Upper Threshold—Set the number of call attempts per second at which you want the session border controller to recognize call flooding and start performing the configured action during non-business hours. Default: 25.00 Valid values: 1.00-100.00
- Lower Threshold—Set the number of call attempts per second at which you want the session border controller to resume allowing all calls after a call flooding incident that occurred during non-business hours. Default: 20.00 Valid values: 1.00-100.00
- Action—Set the action you want the session border controller to perform when Security Shield detects call flooding. Default: Continue. Valid values: Continue | Block | Rate Limit.
- Call Rate—The number of active calls to international premium numbers that you want to allow. Default: 100. Valid values: 1-10,000.
- Call Attempt Rate—The number of call attempts to international premium numbers per session border controller per second that you want to allow. Default: 1000. Valid values: 1-100,000.
- Call Duration Non-Bus Hrs—The total call duration (in seconds) for all calls to premium rate services, toll free numbers, and international destinations per second during non-business hours. Default: 1,800. Valid values:1-1,000,000.
- Call Duration Bus Hrs—The total call duration (in seconds) for all calls to premium rate services, toll free numbers, and international destinations per second during business hours. Default: 3,600. Valid values:1-1,000,000.
- Action—The action to take when the Security Shield detects Toll Free Fraud. Default: Allow. Valid values: Allow | Block.
Enforcement Action Descriptions
The following enforcement actions apply to the preceding parameters
- Block—Terminates the calls to prevent them from traversing the session border controller.
- Continue—Lets call evaluation continue to the next stage even when Security Shield detects threats, anomalies, or incidents. No enforcement action is applied for the threat, anomaly, or incident until further processing of the reputation score indicates that the call is in a high-risk category. Security Shield then applies the enforcement action you configured for the risk category.
- Rate Limit—Drops calls randomly when the incoming call rate exceeds the configured call rate until the rate of calls no longer exceeds the configured rate.
Edit Threat Vector Thresholds
Oracle provides the Oracle® Communications Security Shield Cloud Service (Security Shield) software with default threat vector settings so the system is ready to run the threat algorithms, detect potential threats, and perform protective actions without further input. If you want to change any of the defaults, you can reset them.
The following procedure lists the defaults, ranges, and valid values that you can set according to the needs of your deployment. You do not need to restart the system after making changes, but you do need to save the changes.
- Block—Terminates the calls to prevent them from traversing the session border controller.
- Continue—Lets call evaluation continue to the next stage even when Security Shield detects threats, anomalies, or incidents. No enforcement action is applied for the threat, anomaly, or incident until further processing of the reputation score indicates that the call is in a high-risk category. Security Shield then applies the enforcement action you configured for the risk category.
- Rate Limit—Drops calls randomly until the rate of calls traversing the session border controller matches the configured Call Attempt Rate Limit.
Domain Thresholds
The Domain Thresholds dialog contains settings that inform the Oracle® Communications Security Shield Cloud Service (Security Shield) about how you want to manage risky call traffic within the Security Shield domain. Domain means all of the components and configurations used by, and affected by, the Security Shield. The Security Shield domain does not refer to, or equate to, the domain used for your Oracle Communications Session Border Controller, for example. Oracle recommends that you revisit these settings regularly because adjusting them is a continuous process as your business evolves. You can make assessments and adjust the settings as needed, for example, to allow for marketing campaigns and daily call peaks.
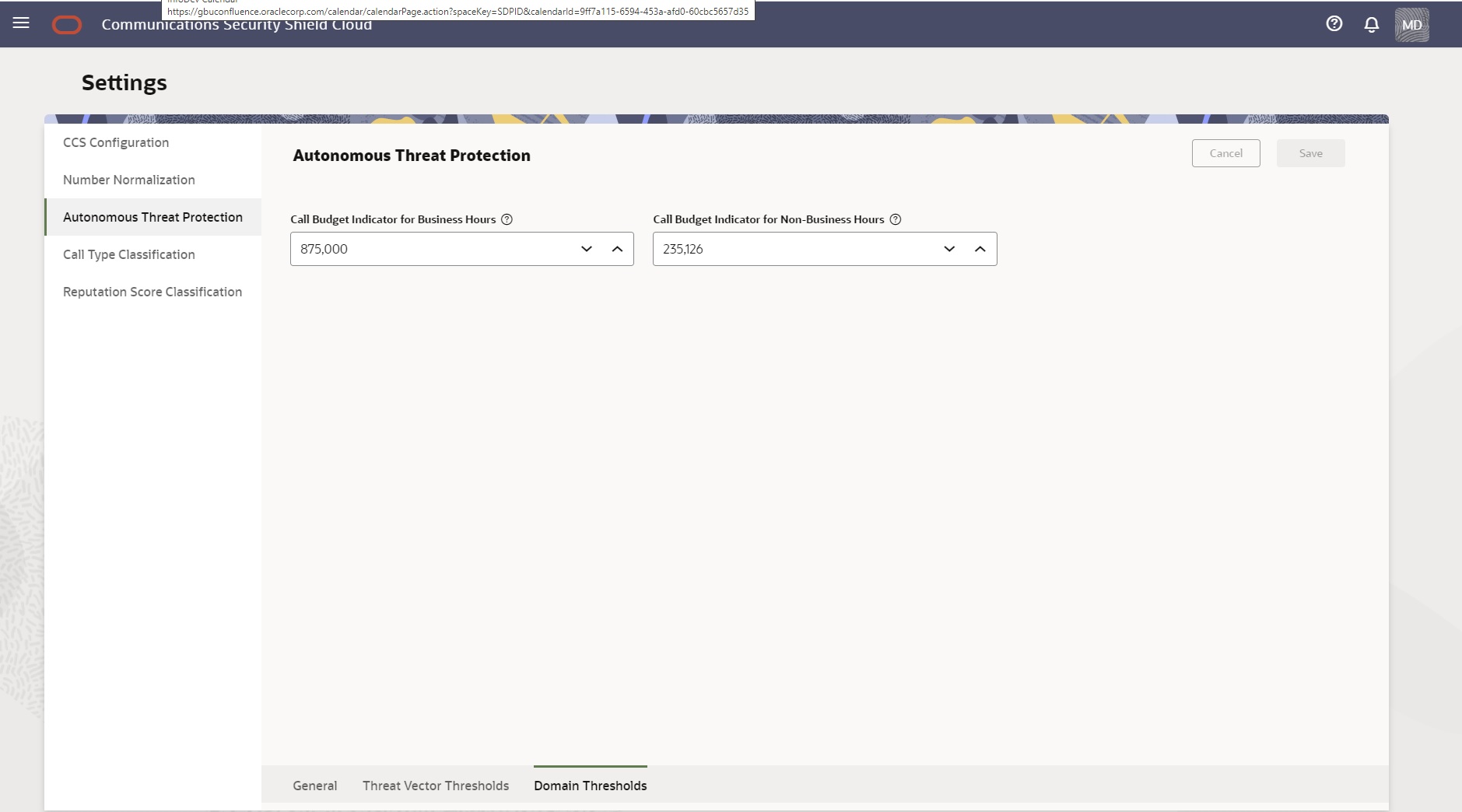
Call Budget Indicator for Business Hours—The threshold for detecting unusual spikes to high-cost destinations during business hours. Default: 10,000. Range: 1-1,000,000.
Call Budget Indicator for Non-Business Hours—The threshold for detecting unusual spikes to high-cost destinations during non-business hours. Default: 1,000. Range: 1-1,000,000
Edit Domain Thresholds
The Oracle® Communications Security Shield Cloud Service (Security Shield) provides settings for your domain that help control unusual spikes to high-cost calling destinations. You can set thresholds for business hours and non-business hours.
Use the following procedure to set call-budget thresholds according to the needs of your deployment.
Call Type Classifications
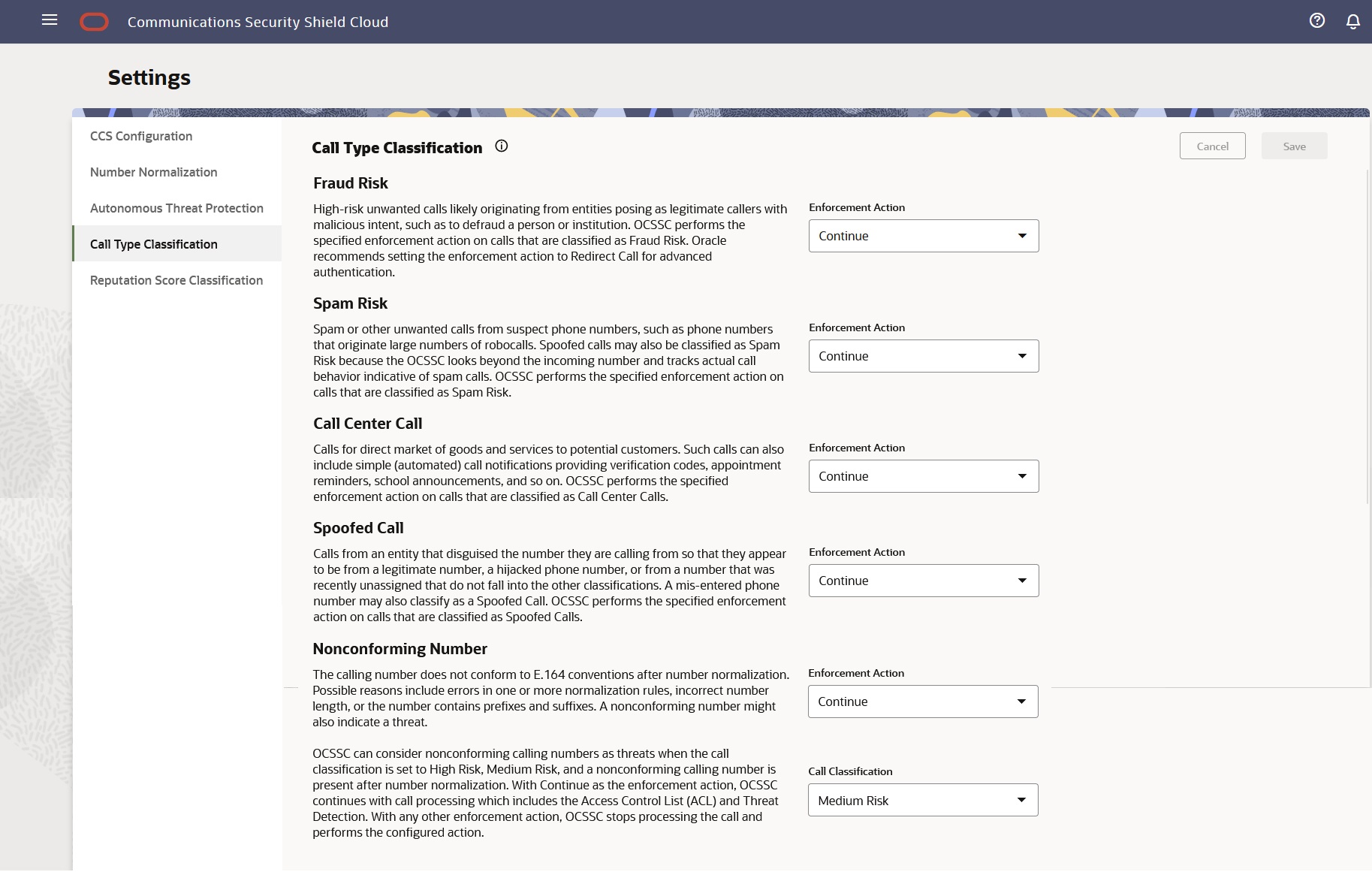
Certain incoming calls might represent low-value, no-value, or other unwanted calls to your business and you might want to get a more accurate understanding of such traffic so you can mitigate the subsequent unwanted effects on your call center. The Oracle® Communications Security Shield Cloud Service (Security Shield) Settings page displays a set of call type classifications and definitions for low-value or no-value calls, along with configurable enforcement actions. You can monitor the success of your enforcement actions on the Dashboard and then return to the Call Type Classifications page to change enforcement actions as needed.
The following screen capture shows the Call Type Classification page for Premium subscribers.
The following screen capture shows the Call Type Classification page for Standard subscribers.
Call Classifications and Descriptions
- Fraud Risk (Premium subscribers)—High probability of a fraudulent call, likely originating from entities posing as legitimate callers with malicious intent, such as to defraud a person or institution. Security Shield performs the specified enforcement action on calls classified as Fraud Risk. Oracle recommends setting the enforcement action to Redirect Call for advance authentication.
- Spam Risk (Premium subscribers)—High probability of a robocall or other bad actor. Spoofed calls may also be classified as Spam Risk because Security Shield looks beyond the incoming number and tracks actual call behavior indicative of Spam calls. Security Shield performs the specified enforcement action on calls that are classified as Spam Risk.
- Call Center Call (Premium subscribers)—High
probability of a call center call such as a
telemarketer or call alerts. Such calls can also
include simple (automated) call notifications
providing verification codes, appointment reminders,
school announcements, and so on. Security Shield performs
the specified enforcement action on calls that are
classified as Call Center Call.
Note:
Telemarketing calls can be a nuisance, but legal and useful. Although this category includes companies trying to sell services and goods, it also includes schools calling parents about a snow day or healthcare providers calling to make appointments for vaccinations. Use caution about selecting the Block enforcement action. - Spoofed Call (Premium subscribers)—Calls from an entity that disguised the number they are calling from so that they appear to be from a legitimate number, a hijacked phone number, or from a number that was recently unassigned that do not fall into the other classifications. A mis-entered pone number may also classify as a Spoofed Call. Security Shield performs the specified enforcement action on calls that are classified as Spoofed Call.
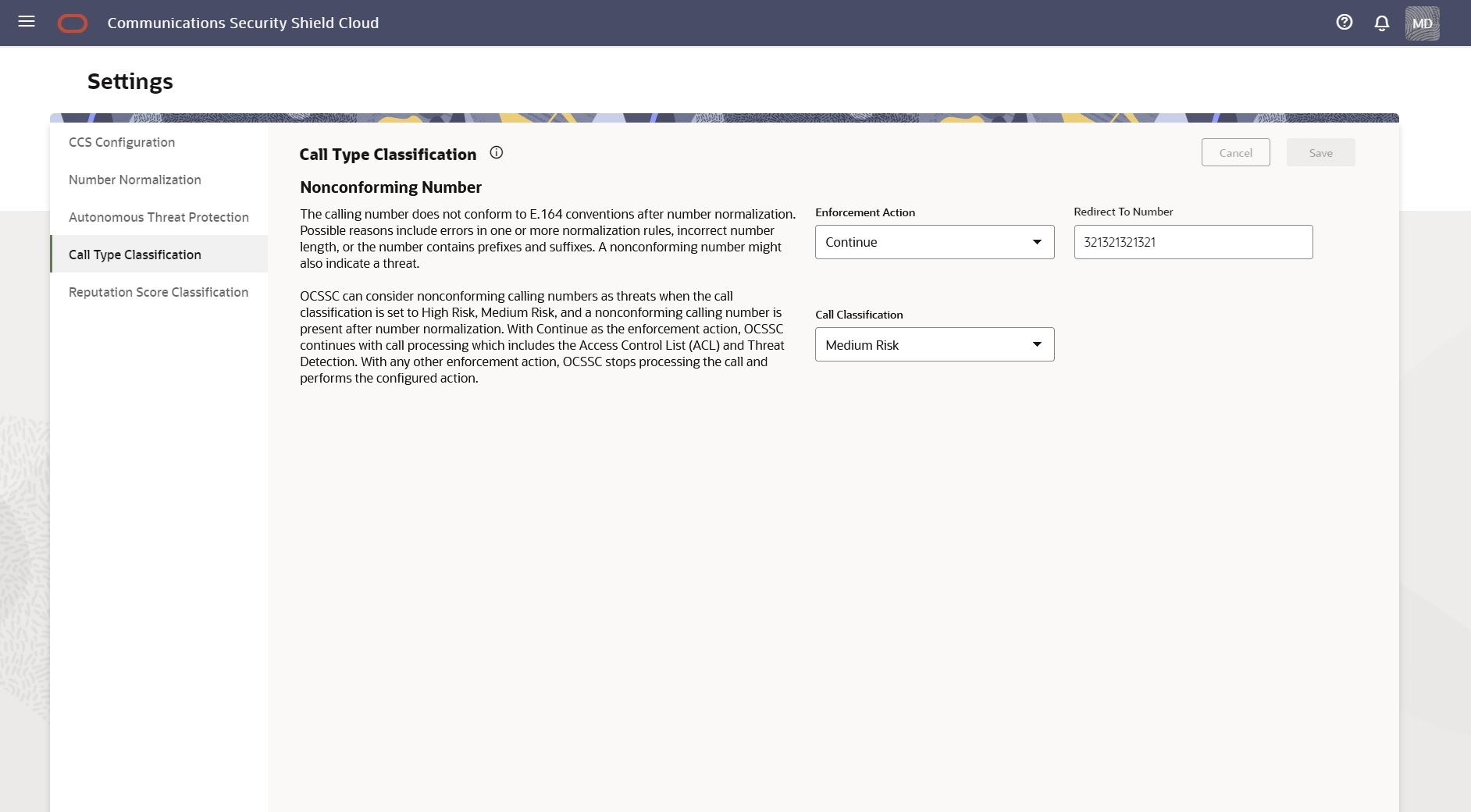
- Nonconforming Number (Premium and Standard subscribers)—The calling number does not conform to E.164 conventions after number normalization. Possible reasons include errors in one or more normalization rules, incorrect number length, or the number contains prefixes and suffixes. A nonconforming number might also indicate a threat. Security Shield can also consider nonconforming calling numbers as threats when the call classification is set to High Risk or Medium Risk and a nonconforming number is present after number normalization. With Continue as the enforcement action, Security Shield continues with call processing which includes the Access Control List and Threat Detection. With any other enforcement action, Security Shield stops processing the call and performs the configured action.
Enforcement Actions
- Block Call—Denies the call.
- Redirect Call—Redirects the call to the phone number that you specify.
- Continue—
- If the Access Control List enforcement is set to Allow, Security Shield allows the call regardless of the enforcement action set for the reputation score.
- If the response code from the call look up is anything but Continue, Security Shield performs the specified action.
- If the response code from the call lockup is Continue, the call type is reported and no call enforcement is associated with this detection. Call enforcement depends on other threats detected or the reputation score enforcement and associated settings.
Note:
When there is a conflict between the Call Classification Type action and the Reputation Score Classification action, the Call Classification Type setting takes precedence.Reputation Score Classification
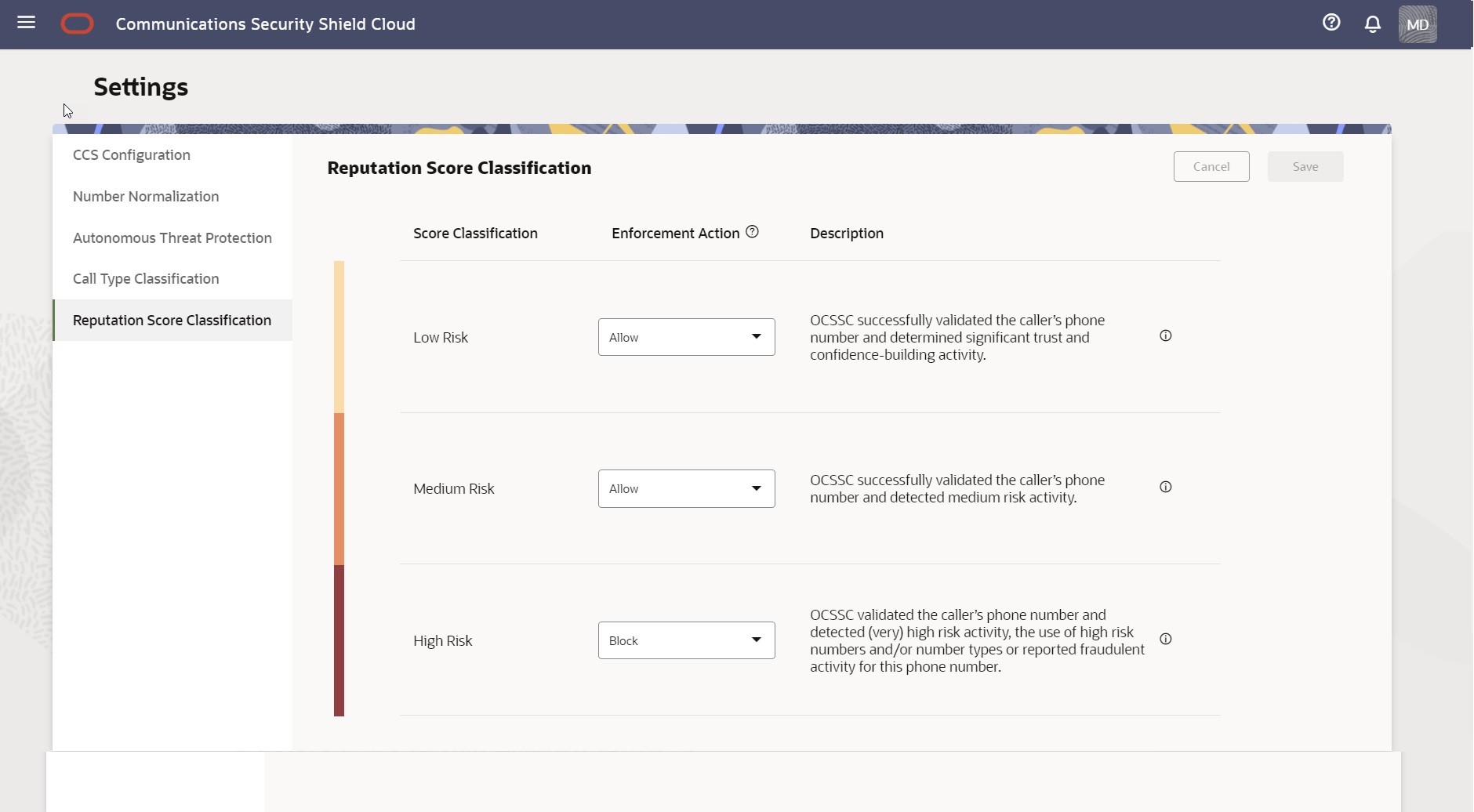
From the Oracle® Communications Security Shield Cloud Service (Security Shield) Settings page, you can learn about reputation score classifications and set the enforcement action that you want the system to apply to each classification.
When you click Reputation Score Classification, Security Shield displays the reputation score call classifications, the possible enforcement actions, and descriptions. The iHelp explains the criteria for each classification.
The following screen capture shows an example of the Reputation Score Classification page.
Classification Criteria
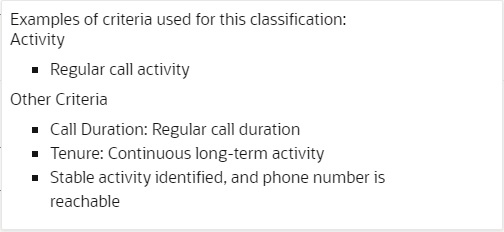
Low Risk classification criteria:
Medium Risk classification criteria:

High Risk classification criteria:
