Configure External User Authentication
- A RADIUS server provides centralized Authentication, Authorization, and Auditing/Accounting (AAA) security protocol management for users who connect and use a network service.
- An AD domain controller provides a directory service in a Windows domain type network using Lightweight Directory Access Protocol (LDAP) versions 2 and 3, Microsoft's version of Kerberos, and DNS.
An external domain user group must be mapped to an internal (local) user group in OCSDM so that this external domain user group and its users inherit the authorization privileges that are specific to the local user group.
Note:
Internal and external users are both supported simultaneously. However, external users do not have corresponding stored user records or username and password information.Determine the RADIUS Group that Your Devices are Using
If you are using a RADIUS server for external authentication and authorization, there is an additional step that you may not have completed. The RADIUS server must be configured to send a user group attribute along with its accept message. This user group attribute contains a configured group policy. The default user group attribute name is Filter-Id, however the RADIUS server administrator may have used a different name for the user group attribute. If the user group attribute name used on your RADIUS server is different than the commonly used default (Filter-Id) user group attribute, you can change the default user group attribute name in SDM in the following Configure a RADIUS Server section.
To determine the name of the user group policy that was configured on your RADIUS server that you will use later to add and map a local SDM user group to the external domain user group, use the Test group membership tool in OCSDM. See the Find an External Domain User Group section for more information.
Configure a RADIUS Server
This task is used to configure a RADIUS server domain for external user authentication.
- The RADIUS server must be configured to use the same shared secret string for all cluster nodes.
- The RADIUS server must be configured to return one or more attribute values in the authentication response message to represent the groups to which a user belongs.
Configure an Active Directory Domain Controller
This task is used to configure an active directory (AD) domain controller (domain server) for external user authentication.
- The Active Directory must be configured for LDAP over SSL if the Active Directory is enabled in Oracle Communications Session Delivery Manager.
- Active Directory must support version 5, if the Kerberos protocol is used.
- Each user object in your Active Directory must store the groups of each member using the memberOf attribute.
- Only child groups may be mapped to local groups when group nesting is in use. This limitation is due to the memberOf attribute not containing a recursive list of predecessors when nesting.
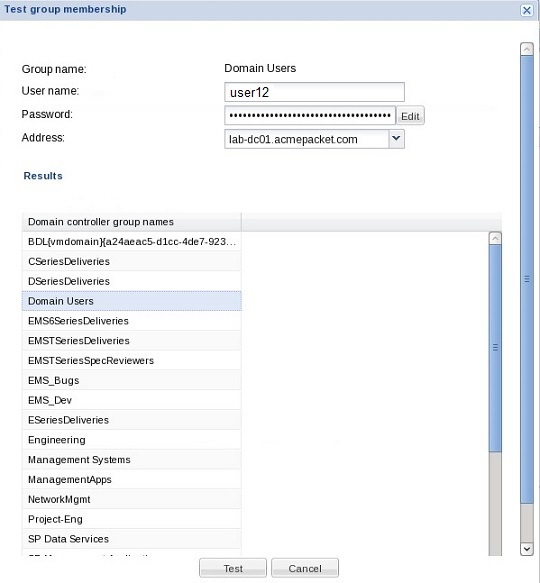
Find an External Domain User Group
Use the external membership tool to find the name of an external domain user group so that it can be later mapped to a local (internal) user group.
If you are using RADIUS for external authentication, you can use this tool to test external users once an external domain server is configured and returns a list of external domain user groups to which the external domain user was assigned. This makes finding the proper external domain user group names that you need to map to the local user group easier so that the external domain user group can inherit its authorization privileges. Once you find the external domain user group you want, see the Add and Map a Local User Group to an External Domain User Group section of this chapter to continue.
Add and Map a Local User Group to an External Domain User Group
Use this task to allow the external domain user belonging to the external domain user group to inherit the group-based authorization privileges of the local user group.
The external domain user is authenticated by a domain server, such as a RADIUS server or Active Directory domain controller. You must map the external domain user group to the local (internal) user group that was created for this purpose.
See the Find an External Domain User Group section for more information about finding the external domain user group name that you need for this task.