Securing Accounts Based On Region
Assume that accounts are classified as belonging to one of the following regions:
- Northwestern
- Northeastern
- Southwestern
- Southeastern
Assume the following company hierarchy exists:
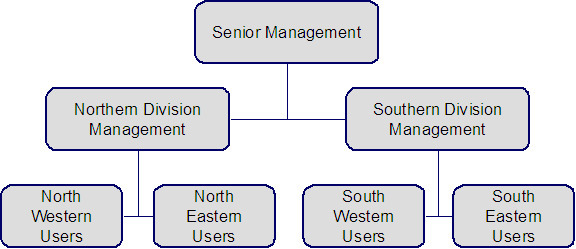
- Senior Management has access to all customers
- Northern Division Management has access to all customers in the Northwestern and Northeastern divisions.
- Southern Division Management has access to all customers in the Southwestern and Southeastern divisions.
- Northwestern Users have access to all customers in the Northwestern division.
- Northeastern Users have access to all customers in the Northeastern division.
- Southwestern Users have access to all customers in the Southwestern division.
- Southeastern Users have access to all customers in the Southeastern division.
The following diagram illustrates the access groups and data access roles required to implement these requirements:
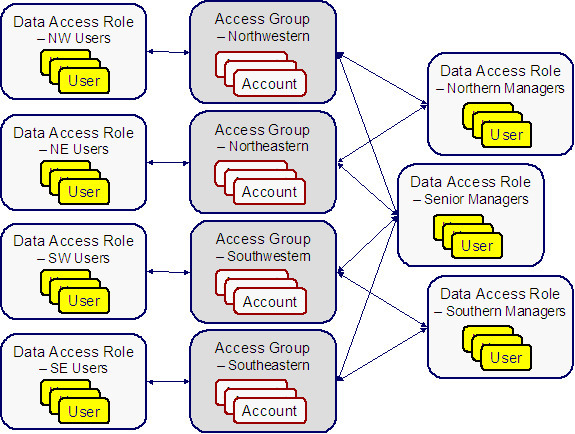
Notice the following about the above:
- There are 4 access groups because access to accounts is based on the region in which they are located (and there are 4 regions).
- There are 7 data access roles because each component of every layer of the access hierarchy requires a separate data access role.
