2 Identity and Access Management Overview
This chapter provides an introduction to working with Oracle Cloud Infrastructure Identity and Access Management (IAM) with Identity Domains.
Oracle Cloud Infrastructure tenancy is provisioned to customers with subscriptions to Oracle Utilities cloud services. Identity and Access Management (IAM) is a built-in part of the Oracle Cloud Infrastructure, and it governs the access to Oracle Cloud Infrastructure resources and Oracle Cloud Services. Identity domains are part of IAM and is where users and access to Oracle Cloud Services are configured and managed.
Each cloud service subscription includes at least one Identity Domain. The identity domains are managed exclusively by the customer (see Identity Domains below for more information).
About This Section
The Identity and Access Management section of this guide contains the following:
- Quick Start Guide provides an overview of the end user provisioning process, with references to additional information in the following chapters.
- Security Administrator Account describes how to set up a security administrator account for user provisioning.
- User Management Procedures describes general procedures related to managing users and groups.
- User Provisioning for Oracle Utilities Cloud Services describes specific tasks related to user provisioning for Oracle Utilities cloud services.
- User Provisioning for Oracle Utilities Analytic Insights describes specific tasks related to user provisioning for Oracle Utilities Analytic Insights.
- User Management for Oracle Utilities Analytic Insights describes specific tasks related to user management for Oracle Utilities Analytic Insights.
- Using Federated Single Sign-On describes tasks required when using an external identity management system to provide authentication for the application instances within your cloud subscription.
Identify Domains
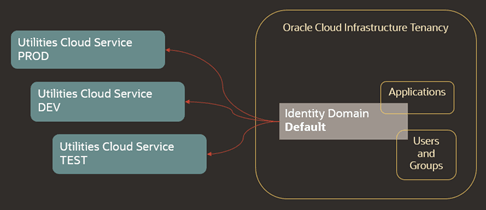
The Oracle Utilities Cloud Service configurations are defined and maintained in an Identity Domain. Initial provision of the service results in all environments being connected to a single Identity Domain (usually a Default domain).
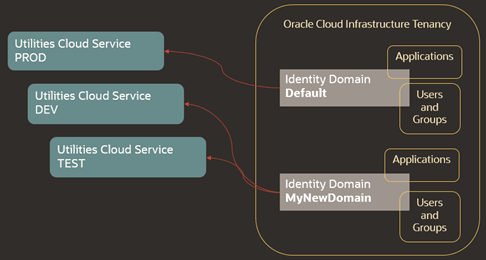
This topology may be modified in the future. For example, you may create an additional Identity Domain that is dedicated for production environment. In this scenario, you should submit a request for the re-connection to the Oracle support team.
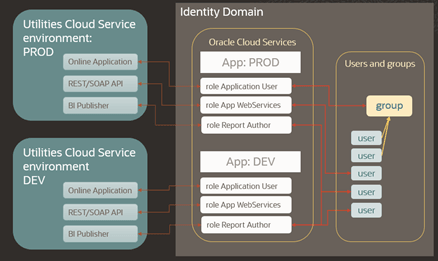
The following configurations are necessary to perform the identity and access management for the Oracle Utilities Cloud Services
- Application: For Oracle Utilities cloud services the application represents a single environment, Production or non-Production. Applications are created by the service provisioning process.
- Application Role: The Application Role represents an entitlement to access one of the components within the environment. By assigning user or groups to an Application Role the security administrator is authorizing access to the corresponding component(s). Application Roles are created by the service provisioning process.
- User: Users represent a human or non-human entity that is accessing the environment. User records are created and managed by the Security Administrator.
- Group: Groups comprise of one or more users. Groups are created and managed by the Security Administrator.