Online User Management
To manage online users, several facilities must be configured:
• The security repository and rules must be configured in Oracle WebLogic to enable authentication. Refer to Oracle WebLogic Administration Guides for more information.
• The product group used to connect users to Oracle WebLogic resources should be created in the security repository and configured in the product configuration. The default value for this setting is cisusers. Refer to the Server Administration Guide for more information on this setting.
• Users need to be connected to the product group within the security repository to indicate that they can access the Oracle WebLogic resources.
The process for managing online users is outlined in the following process: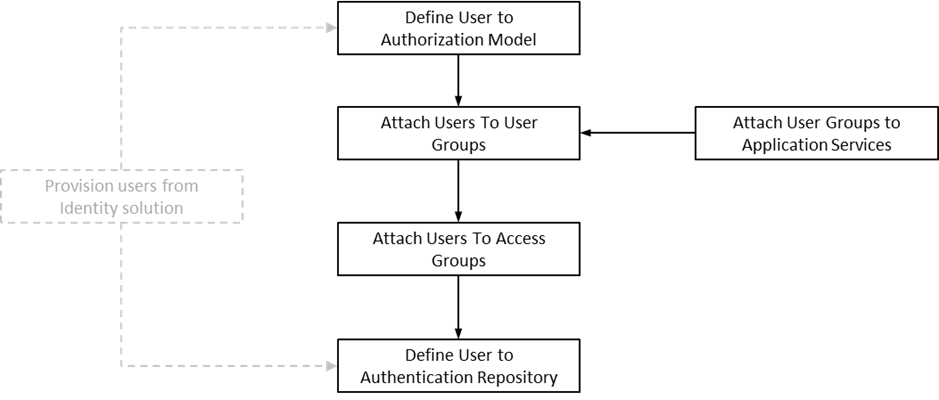

• Users should be defined to the authorization model to define their profile and permissions within Oracle Utilities Work and Asset Management. Refer to the User Management section of this chapter for more details.
• Attach user groups to Application Services to define the subset of service and actions valid for that group of users. Refer to Defining User Groups to Application Services for more details of this process.
• Attach Data Access Groups to the users. This defines the subset of data that the user has access to. Refer to Defining Users to Data Access Groups for more details of this process.
• Attach users to the appropriate user groups to define the subset services and valid actions the user can perform within Oracle Utilities Work and Asset Management. Refer to Defining Users to User Groups for more details of this process.
User Management
The User object in Oracle Utilities Work and Asset Management is used to record the security information used for identification of the user and their permissions.
Oracle Utilities Work and Asset Management provides a maintenance function to maintain these definitions within the product. To maintain the users the following is performed:
• Navigate to the user menu option on the Administration menu. Using the Add User option on the menu allows navigation to the add function.
• The User maintenance object is displayed which maintains the security information for a user.
Field | Comments |
|---|---|
Userid | This is the unique user identifier used within the product used for authorization activities. Limited to eight (8) characters in length. |
Login Id | This is the unique user identifier used within the product used for authentication purposes. This must match the value used in the security repository to successfully use the product. Limited to 256 characters in length. This value can be the same or different to the Userid. |
Last Name | Last Name of user. Limited to 50 characters in length. |
First Name | First Name of user. Limited to 50 characters in length. |
User Enable | Whether the user is active in the security system or not. Valid Values: Yes (default) – User is active and can use the system, No – User is disabled and cannot use the system. Refer to User Enable and Disable for more details. |
User Type | The type of user. Valid Values: Blank = Normal user, Template = Template Users. |
Language | Default Language used for user. For non-English languages, Language pack must be installed to use specific languages. |
Display Profile Id | The display profile associated with the user. This controls the display of currency, dates, and so on. |
Time Zone | Time Zone allocated to user account. Note: This feature is only applicable to specific products. Check your product online documentation for more details about applicability. |
Email Address | Optional Email address associated with user. This is used by utilities and can be used for interfaces requiring email addresses. |
Dashboard Width | Default width for Dashboard Portal. Setting this value to zero (0) will disable the dashboard altogether. |
Dashboard Location | Preferred location of the Dashboard Portal. This capability is only enabled for relevant platforms only. |
Dashboard State | Preferred initial state of the Dashboard Portal. This capability is only enabled for relevant platforms only. |
Home Page | The default home page associated with the user. |
Portals Profile User Id | The userid used to inherit portal definitions from. Refer to Template Users for more information. |
Favorites Profile User Id | The userid used to inherit favorite definitions from. Refer to Template Users for more information. |
To Do Summary Age Bar | The settings for the color coding of the To Do Summary portal in the dashboard. This can be used to indicate relative age of to do entries. |
User Groups | This is a list of user groups and their associated expiration dates. Refer to Defining Users to User Groups for more information. |
• Save the additions/changes for the user using the Save function on the top of the screen.
Template Users
By default, portal preferences and favorites are set at an individual user level. It is possible to inherit the portal and favorites from other users to reduce the maintenance effort for security information. Changes to the profile user are automatically inherited to any users where the profile user is attached to.
To use this functionality the following must be performed:
• Set up each user to be used as a template and set the User Type to Template.
• For any user that will inherit the portal preferences and favorites, specify the appropriate template user in the following fields:
• Portal Preferences: Use the Portals Profile User Id to specify the Template User to be used to inherit the portal preferences.
• Favorites: Use the Favorites Profile User Id to specify the Template User to be used to inherit the favorites preferences.
Once any changes are made to the Template Users’ portal preferences and favorites, these changes automatically apply to any attached users.
Assigning To Do Types
Note: To Do records can be assigned to explicit users or groups of users. This section covers the latter condition.
Note: Refer to the online Administration Help for a discussion about the To Do function. To Do Roles must be set up prior to using this function.
Oracle Utilities Work and Asset Management generates To Do records for any function or error condition that requires human intervention. The To Do record contains a type and role to be used assist in assigning the appropriate resources to work on the condition indicated by the To Do.
For security purposes, users need to be attached to the relevant roles for the To Do facility to limit which To Do Types an individual user can work upon. To manage the To Do Roles to be assigned to users, navigate to the To Do Roles tab of the User Maintenance function and select the Add or Delete icon. You can use the Search icon to find existing To Do Roles. Once users have been attached to the To Do Roles, they can access the associated To Do Types assigned to the role or any To Do directly assigned to them.
Assigning User Portal Preferences
Note: Refer to the online Administration Help for a discussion about the Portal/Zone functionality. Portals and Zones must be setup prior to using this functionality.
Note: Portal Preferences can be inherited from other users if Template Users are used. In this case the ability to set for portal preferences for users attached to a template user are disabled.
The user interface of Oracle Utilities Work and Asset Management is made up of Portals containing individual Zones. Each of the portals and zones can be associated with an application service for security purposes. Users that are attached to User Groups that are also attached to those Application Services can view and use the portals and zones.
The order of display and other factors are defined at an individual user basis. To define the portal preferences for a user, navigate to the Portal Preferences tab of User Maintenance function. This will display a screen with a list of the portals the user has access to, via the user groups they are attached to.
To maintain the preferences for a specific portal, expand the portal entry in the list by clicking the name of the portal or using the Expand All functionality. For example:
The following zone preferences can be set for the user:
Zone Preference | Description |
|---|---|
Display | Whether the zone is included or not in the portal. This allows specific zones to be displayed at startup time while other zones can be hidden and only displayed upon conditions in other zones. See Zone Visibility in the online Administration guide for more information. |
Initially Collapsed | Whether the zone is displayed collapsed on initial load. Zones are only executed when they are expanded. Marking zones as Initially Collapsed can prevent them from being executed and can speed up portal rendering times. |
Sequence | Defines the relative order of the zones within the portal. A value of zero (0) takes the default sequence from the portal definition. |
Refresh Seconds | Defines the zone auto refresh rate (this is only applicable to a subset of zone types). A value of zero (0) disables auto-refresh. |
Security Access | This is an information field that indicates whether the user has access to the zone or not (while unlikely, it is possible to have a portal contain zones not permitted for access to an individual user). Refer to the online documentation for more information. |
Assigning Bookmarks
You can attach bookmarks to your user profile to access pages including the context of the pages. You can use the Bookmark button to define bookmarks that attach the page and context to the user profile.
Note: Bookmarks are added at runtime by end users using the Bookmark button. This function only displays or deletes the bookmarks assigned by the user.
It is possible to view and remove bookmarks on the user profile by navigating to the Bookmarks tab of the User Maintenance function. You can set your bookmark preferences through the following fields:
Field | Description |
|---|---|
Sequence | Internal sequence used for sorting. |
Name | The name of the bookmark. The URL for the bookmark is hidden and not editable. |
You can use the Delete icon to remove existing bookmarks from your list.
Assigning Favorite Links
Users can set several favorite functions or menu items that they can access using keyboard shortcuts or via the Favorites zone on the Dashboard.
Note: Favorites can be inherited from other users if Template Users are used.
Configuration of favorite functions or menu items is through the Favorite Links tab of the User Maintenance function. Users can set favorite link preferences through the following fields:
Field | Description |
|---|---|
Sequence | The relative sequence number of the favorite link used for sorting purposes. |
Navigation Option | The Navigation Option to display the favorite links. This can reference the zone or maintenance function to display after selecting the favorite link. |
Security Access | Indicates whether the Navigation Option is accessible or not to the user. |
To manage the Favorites to be assigned to users, select the Add icon to assign the favorite link with the appropriate Navigation Option and Sequence or select the Delete icon to remove an existing Navigation Option from the list. You can use the Search icon to find existing Navigation Options.
Favorites are then available to be displayed in the Favorites zone on the Dashboard.
Assigning Favorite Scripts
Users can set several Favorite BPA Scripts that they can access using the Favorite Scripts zone on the Dashboard.
Note: Favorites can be inherited from other users if Template Users are used.
Configuration of favorite scripts is through the Favorite Scripts tab of the User Maintenance function. Users can set favorite script preferences through the following fields:
Field | Description |
|---|---|
Sequence | The relative sequence number of the favorite used for sorting purposes. |
Script | The BPA Script to use in order to display the favorite function or menu items. |
Security Access | Indicates whether the BPA Script is accessible or not to the user. |
To manage the Favorites to be assigned to users, select the Add icon to assign the favorite link with the appropriate Script and Sequence or select the Delete icon to remove an existing Script from the list. You can use the Search icon to find existing BPA scripts.
Favorites are then available to be displayed in the Favorite Scripts zone on the Dashboard.
Assigning User Characteristics
Oracle Utilities Work and Asset Management can extend objects within itself through Characteristics, which act as additional data attributes for providing supplementary information or custom algorithms for processing.
Note: Oracle Utilities Work and Asset Management ships with a predefined set of Characteristic Types.To use User Characteristics, the appropriate characteristic types must be created and attached to the User object. Refer to the online Administration documentation for more information.
The User object in Oracle Utilities Work and Asset Management can also be customized using Characteristics. This can be achieved by navigating to the Characteristics tab of the User Maintenance function. The following fields can be set for the favorites:
Field | Description |
|---|---|
Characteristic Type | The characteristic type associated with the User object. This is a drop-down list of the valid characteristic types associated with the object. |
Sequence | The relative sequence number of the characteristic used for processing purposes. |
Characteristic Value | Depending on the configuration of the Characteristic Type, this value may be free-formatted, an attachment, in a specific format or a specific set of values. |
To manage Characteristics to be assigned to users, select the Add icon to assign the characteristic (indicating Characteristic Type) with the appropriate Sequence or select the Delete icon to remove an existing characteristic from the list.
Defining Users to User Groups
Access to Oracle Utilities Work and Asset Management services requires User Group connections that are connected to Application Services. The connections define the linkage for functions that are accessible to users.
The attributes of the user to user groups links are as follows:
• The link is subject to an expiration date to allow representation of transient security configurations.
• Each link is owned and subject to Data Ownership Rules. By default, all site-created links are owned as Customer Modifications.
• User Groups are set up according to site preferences. These can be job-related, organization level-related or a combination of factors.
• Users must be members of User Groups to access the system. A user can be a member of multiple groups.
• Users can be members of groups with overlapping permissions to Application Services. In cases of overlapping permissions, the highest valid permission is used.
You can manage the user and User Group link by navigating to the Main tab of the User Maintenance function. You can use the Add icon to insert a User Group with the appropriate expiration date or use the Delete icon to remove existing User Groups from the list. Use the Calendar icon to select the expiration date and set the link’s effective date. Use the Context Menu icon to navigate to the User Group details to review more information. The user's security is referenced for menu and function access regardless of the access channel (online, web service, or batch) used.
Defining User Groups to Application Services
One of the fundamental Oracle Utilities Work and Asset Management security configurations is to define User Groups to Application Services. An Application Service can represent an Oracle Utilities Work and Asset Management service, a menu or an object. Linking a User Group to a service allows Access Mode configuration, which defines the valid actions the User Group can perform.
Note: Oracle Utilities Work and Asset Management ships with all the Application Services predefined for base functions. These can be used or replaced with custom definitions. A starter set of User Groups is loaded withOracle Utilities Work and Asset Management that can be used as basis for further security User Groups.
Additionally, each service can specify Security Types that allow for custom security rules to be applied at runtime. Refer to Security Types for supplementary information.
There are two methods to maintain the links established between User Groups and Application Services: the Application Service Portal and the User Group Maintenance. These are valid for most sites and can be used to manage information distinctively.
Application Service Portal
The Application Service Portal enables you to define an Application Service and to set its Access Modes and User Groups.
You can configure the following Main tab settings by navigating to the Application Service option on the Administration menu:
Setting | Description |
|---|---|
Application Service | The unique identifies of the Application Service used in configuration of security on objects, menus, services, and so on. For custom definitions, Oracle recommends adding a “CM” prefix to distinguish these from Application Services provided by Oracle Utilities Work and Asset Management. |
Description | A brief description for documentation purposes that appears on security screens when the Application Service is specified. |
Access Modes | Lists the valid modes to access the Application Service. The modes must match the internal actions supported by the objects used by the Application Service. Use the Add icon to insert an Access Mode. Note that an Access Mode can only be defined once on an Application Service. Use the Delete icon to remove an existing Access Mode from the list. The Access Mode link to the Application Service is ownership-controlled and by default all created links are owned as Customer Modifications. Refer to Data Ownership Rules for more information. |
You can also configure the following zones in the Application Security tab to display the User Group membership and manage that relationships:
Zone | Description |
|---|---|
Application Service Details | Summarizes the Access Modes and Security Types of the Application Service. |
User Groups With Access | Lists the User Groups with access to the Application Service, along with the associated expiration dates, Access Modes, Security Types and associated authorization levels. Use the Deny Access function to limit the access of User Groups to the Application Service. |
User Groups Without Access | Lists those User Groups without access to the Application Service. Use the Grant Access function to allow User Groups to access the Application Service. |
After granting access to User Groups, you can set the Access Mode and security group specification for the User Group:
Field | Description |
|---|---|
Expiration Date | Specifies the date when access to the User Group expires. |
Access Mode | Shows the Access Mode as defined on the Application Service definition. Use the Add icon to insert an Access Mode or use the Delete icon to remove an existing Access Mode from the list. |
Owner | Ownership of link. Refer to Data Ownership Rules for more information. |
Security Type | The Security Type code associated with the Application Service. Use the Add icon to insert a Security Type or use the Delete icon to remove an existing one from the list. |
Authorization Level | The Authorization Level assigned to the User Group when running the Application Service for the Security Type. |
User Group Maintenance
The User Group Maintenance allows you to define the Application Services that User Groups can access and to connect users to User Groups. You can manage the User Groups by navigating to Administration, selecting the User Group menu item, and performing the following actions:
• Use the Context Menu icon to edit existing permissions.
• Use the Delete icon to remove the association between User Group and Application Service.
• Use the Add icon to associate a User Group with an Application Service.
Adding or editing associations automatically displays the Application Services tab, which enables you to maintain the Access Modes and Security Types for the association through the following fields:
Field | Description |
|---|---|
Expiration Date | Indicates the date on which access to the User Group expires. |
Access Mode | Valid Access mode as defined on Application Service definition. Use the Add icon to add a new Access Mode or use the Delete icon to remove an existing Access Mode from the list. |
Owner | Ownership of the link. Refer to Data Ownership Rules for more information. |
Security Type | The Security Type code associated with the Application Service. Use the Add icon to insert a Security Type or use the Delete icon to remove an existing one from the list. |
Authorization Level | The Authorization Level assigned to the User Group when running this Application Service for the Security Type. |
You can also manage users associated with the User Groups through the Users tab fields:
Field | Description |
|---|---|
User | The authorization user identifier to associate with the user group. |
Expiration Date | Indicates the date on which the association between the user and the User Group expires. |
Owner | Ownership of the link. Refer to Data Ownership Rules for more information. |
Defining Users to Data Access Groups
Data Access Groups define the subset of data objects accessible to users. The levels of data access definition are as follows:
• Data Access Roles: User are connected to Data Access Roles which defines the groups of data permissions the user has access to. Data Access Roles are connected to Data Access Groups (a.k.a. Access Groups).
• Data Access Groups: Data Access Groups are tags that are attached to entities in Oracle Utilities Work and Asset Management to implement data security. Data Access Groups are maintained using Access Group maintenance. Refer to the online Administration Guide for more details of this facility.
Note: Only some services support Data Access Roles and Data Access Groups. Refer to the online Administration Guide for more details.
Note: Attaching a Data Access Group to a product entity does not automatically implement data security. Queries for that object must be altered to consider the Data Access Group. Refer to the Oracle Utilities SDK for more details.
The figure below illustrates the relationship between Data Access Roles and Data Access Groups: 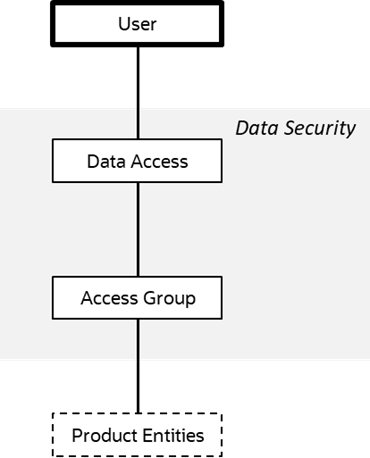

You can maintain Data Access Roles and Data Access Groups in the Access Security tab of the User Maintenance function. Use the Add icon to insert a Data Access Role and configure its settings or use the Delete icon to remove an existing Data Access Role from the list. The screen will allow the definition and display of the following information:
Field | Description |
|---|---|
Default Access Group | When this user creates a new object that is subject to Access Security then this default is used for the value of the Access Group of the new object. This can be overridden by logic within the object if necessary. |
Data Access Role | List of Data Access Roles this user is attached to. |
Expiration Date | Indicates the date on which the association between the user and the Data Access Role expires. |
User Enable and Disable
One feature of security is to attach user records to some objects (automatic or configurable) for audit purposes. You cannot delete a user record if the user performs any work in Oracle Utilities Work and Asset Management and is attached to some audit objects across Oracle Utilities Work and Asset Management.
The User Enable function on the User object allows you to activate or deactivate a user by setting the appropriate value for User Enable, which has the following implications:
Value | Implications |
|---|---|
Enable | • The user can access the system. • The user can process records according to the authorization model. • The user must be active in the Security Repository to fully accessOracle Utilities Work and Asset Management. |
Disable | • The user cannot access the system regardless of the security setup. • The user record is retained for audit purposes only. • The user does not have to exist in the Security Repository. • The key use cases for this option are as follows: • Support for personnel (permanent or temporary) leaving: Manually deactivate users once they leave the organization yet keep the information for auditing purposes. • Logical deletion: If the user needs to be deleted for any reason, selecting this option removes the user record, preventing access to the system. • Temporary disablement: If business rules need to isolate the user record, selecting this option for the appropriate users can effectively deactivate their access to Oracle Utilities Work and Asset Management. Note: Deactivation of the user record will take effect when the user logs in to the system or after the security cache refreshes. |