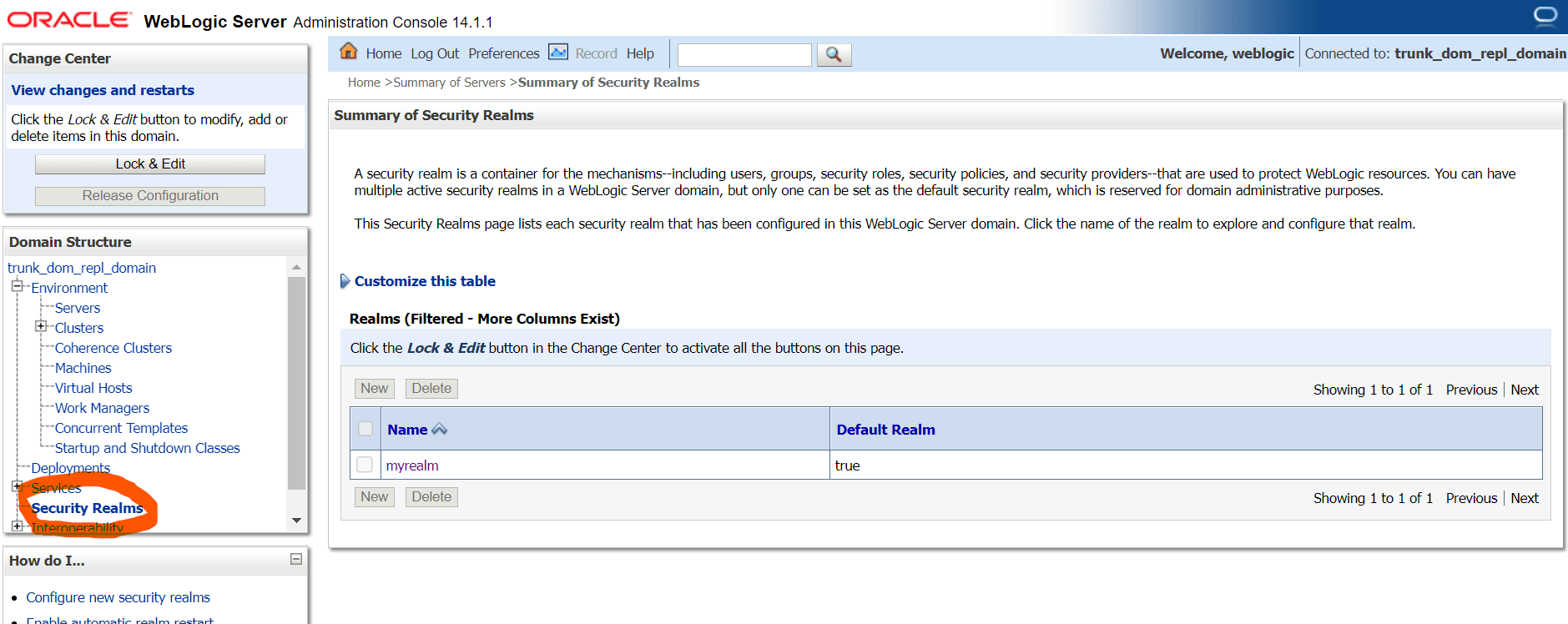
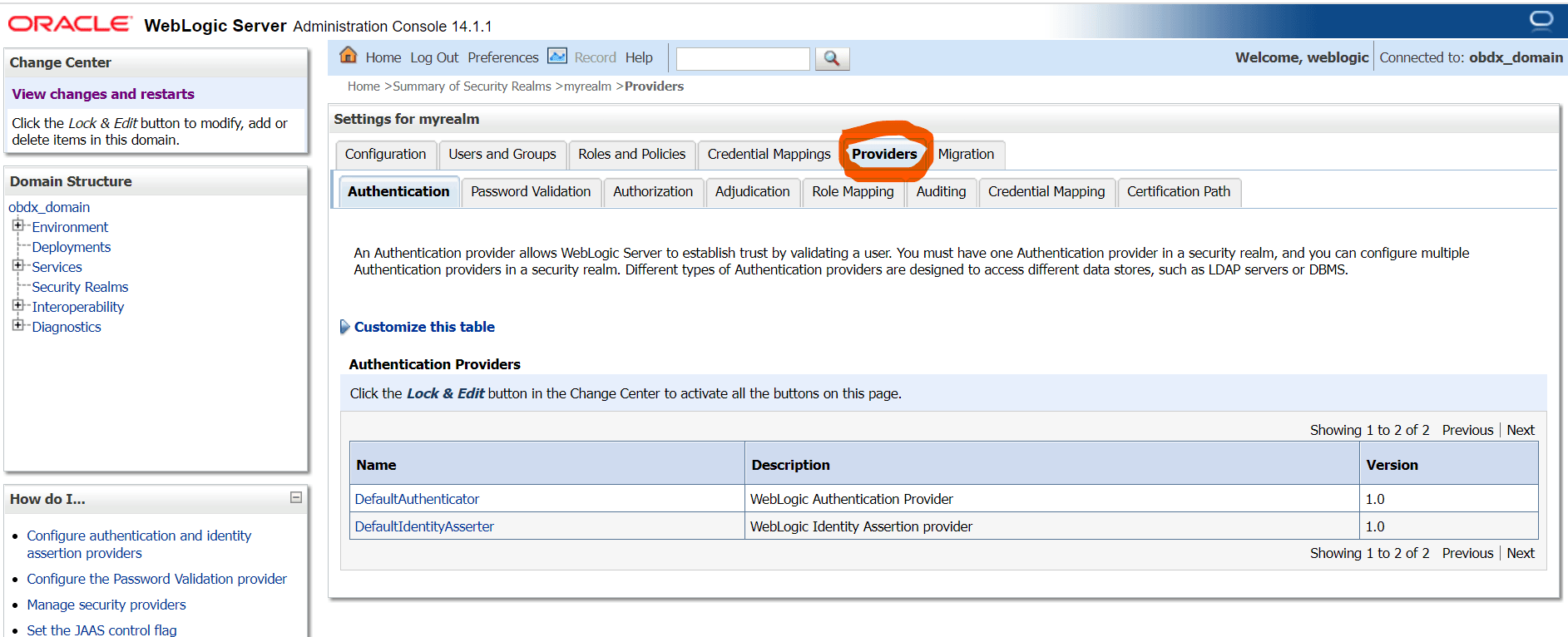
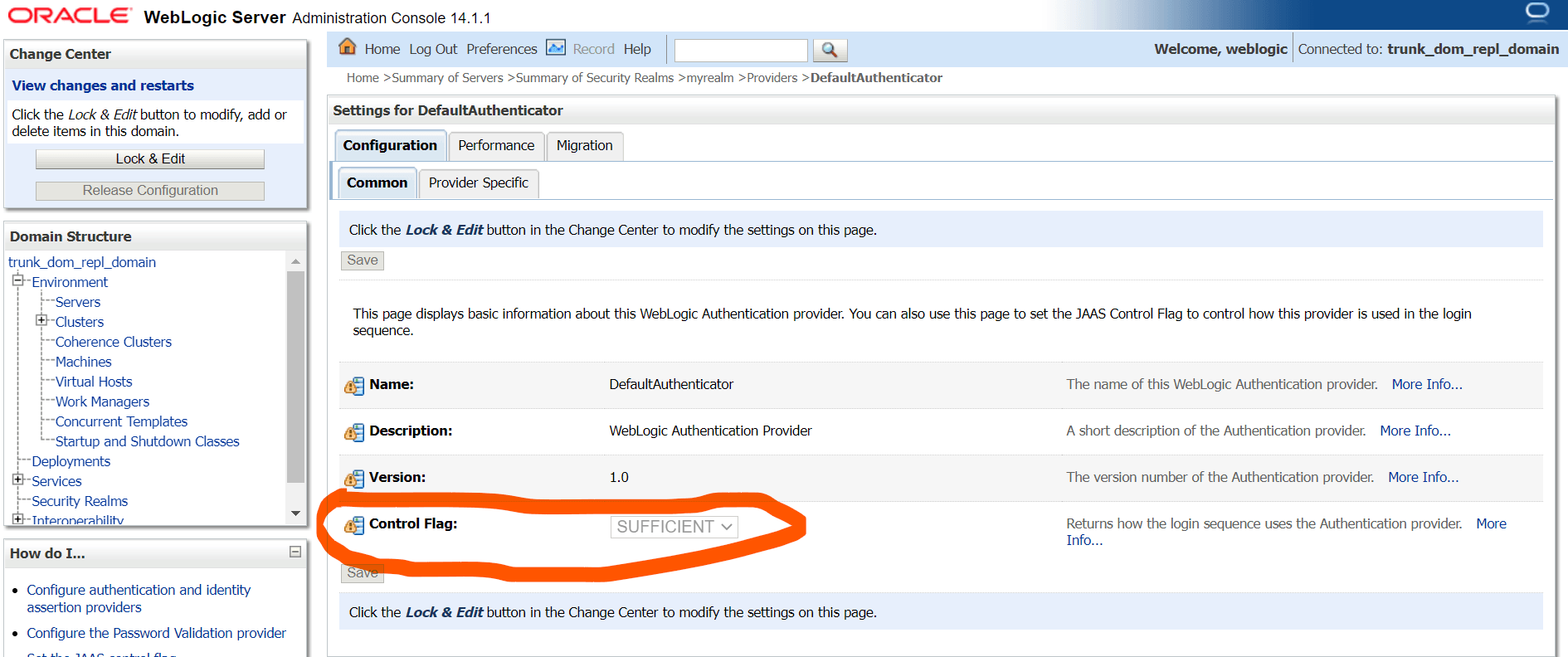
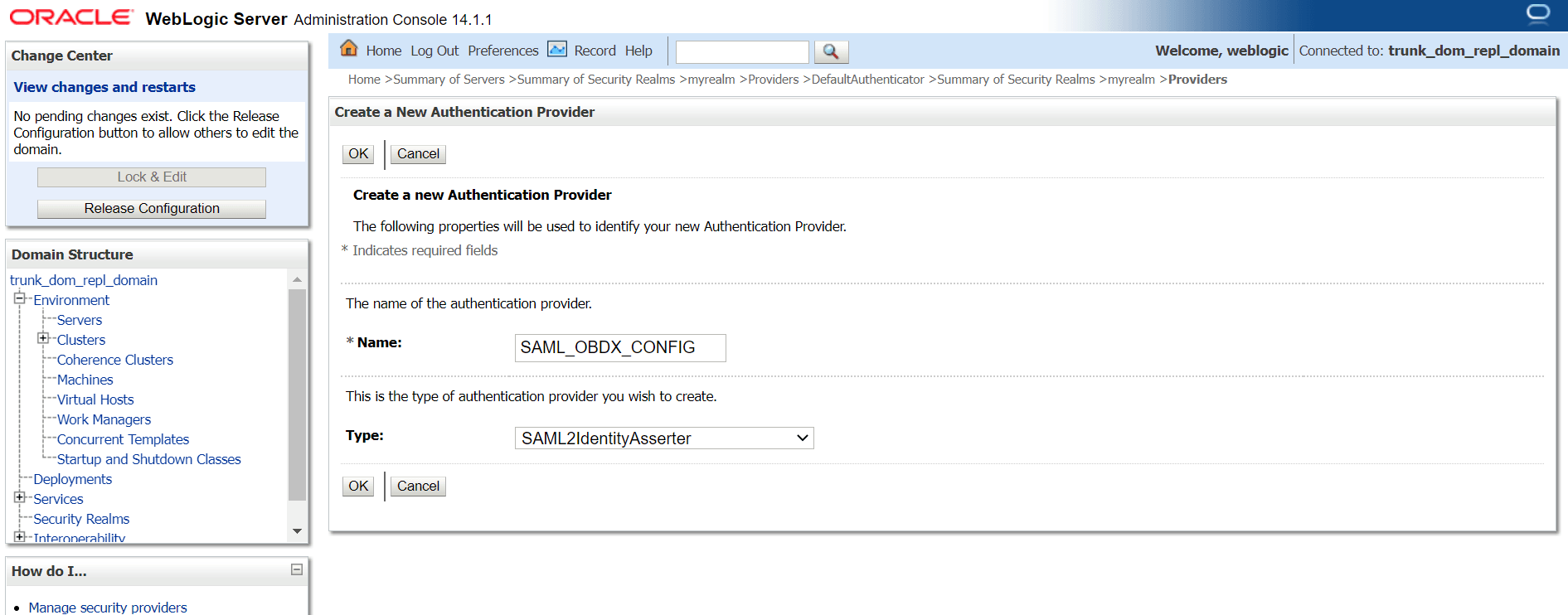
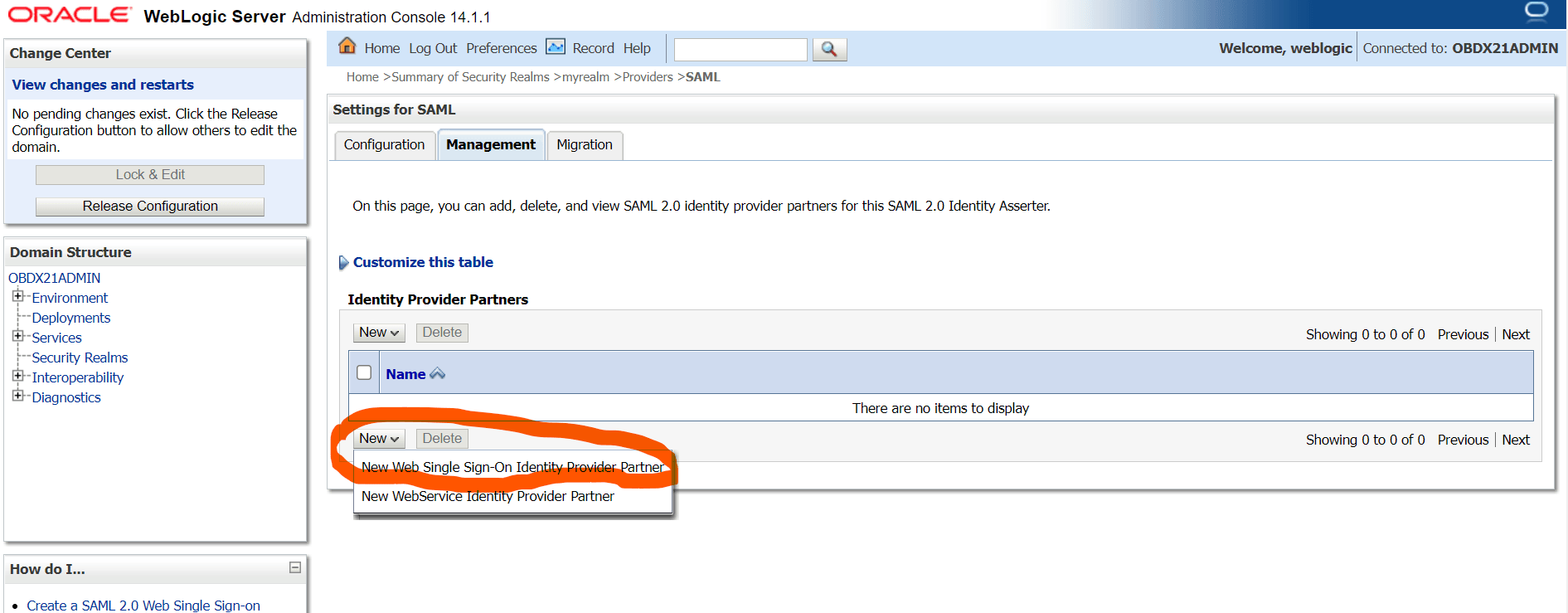
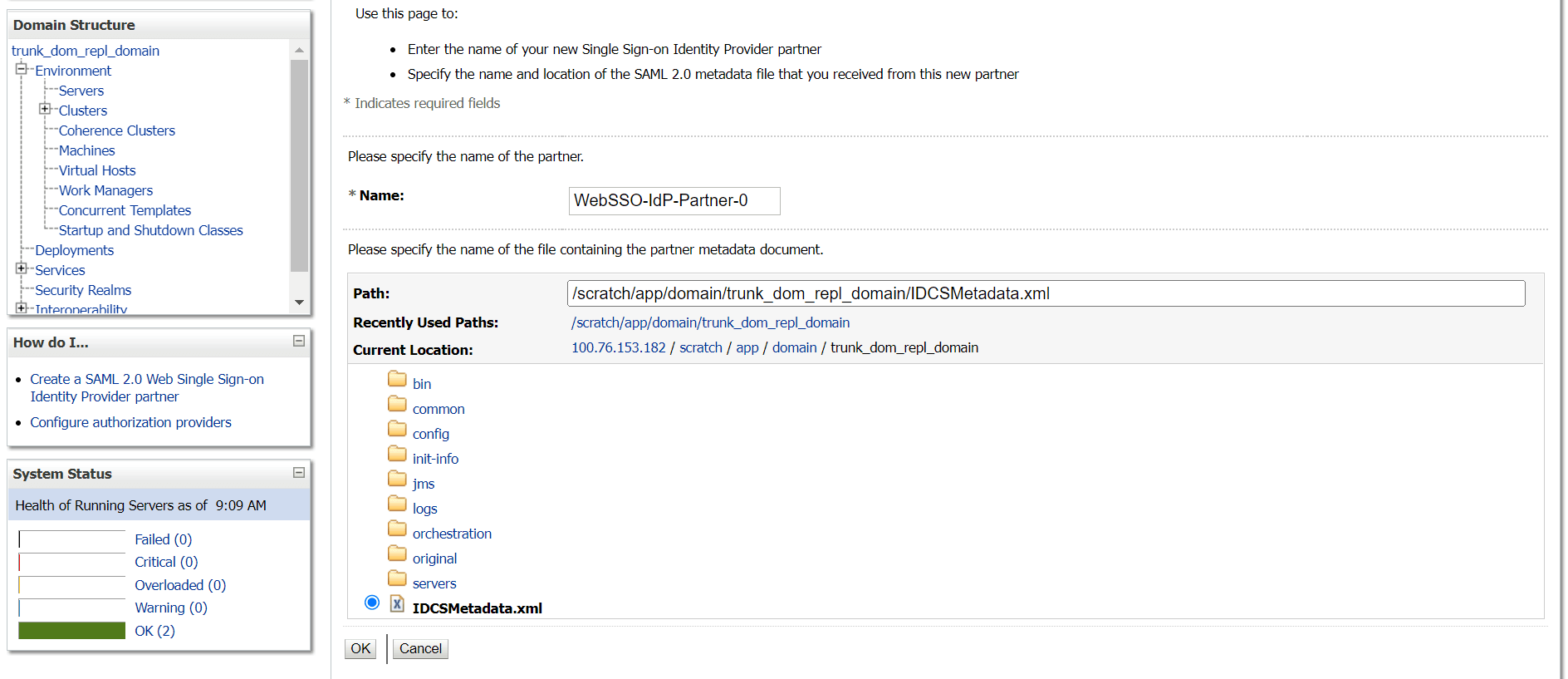
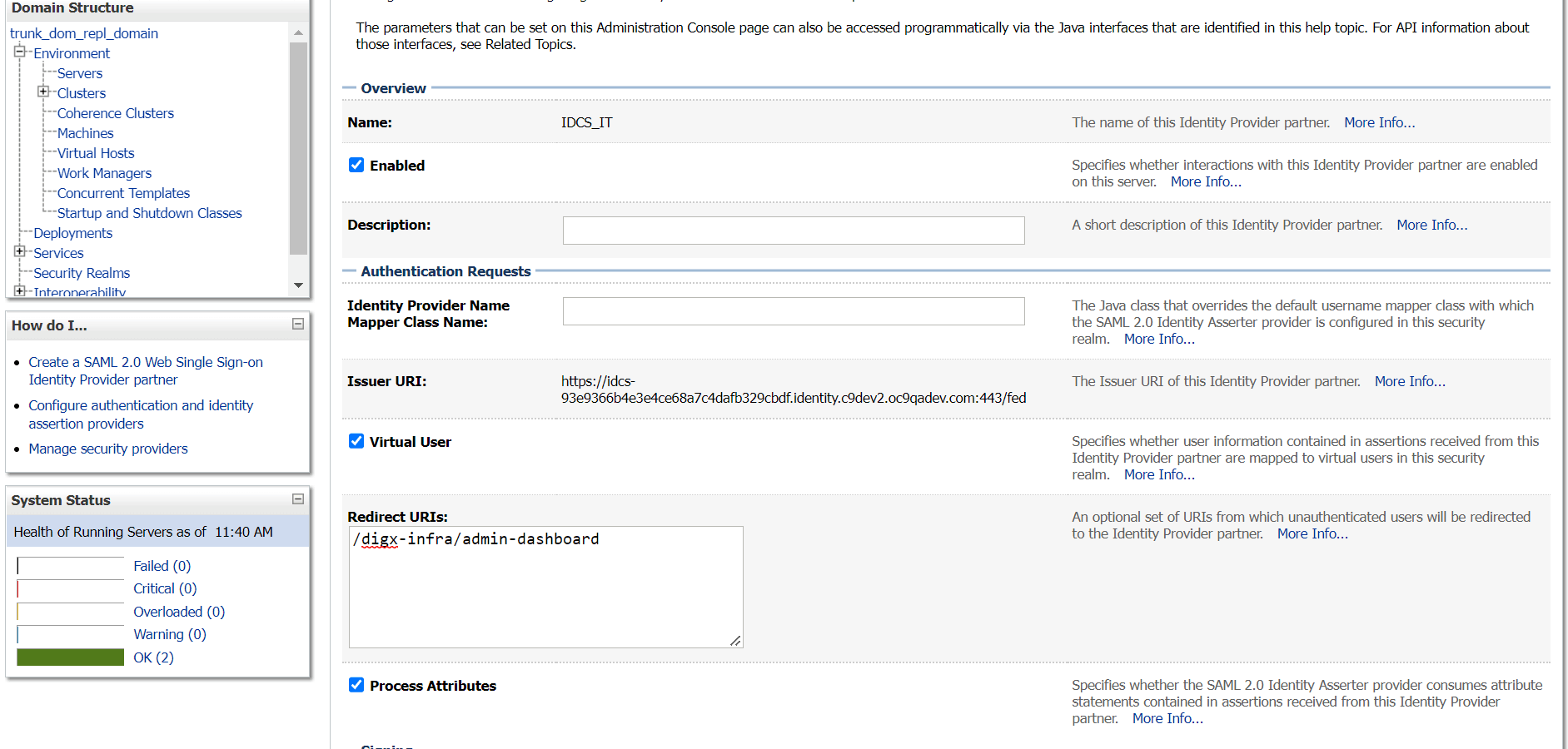
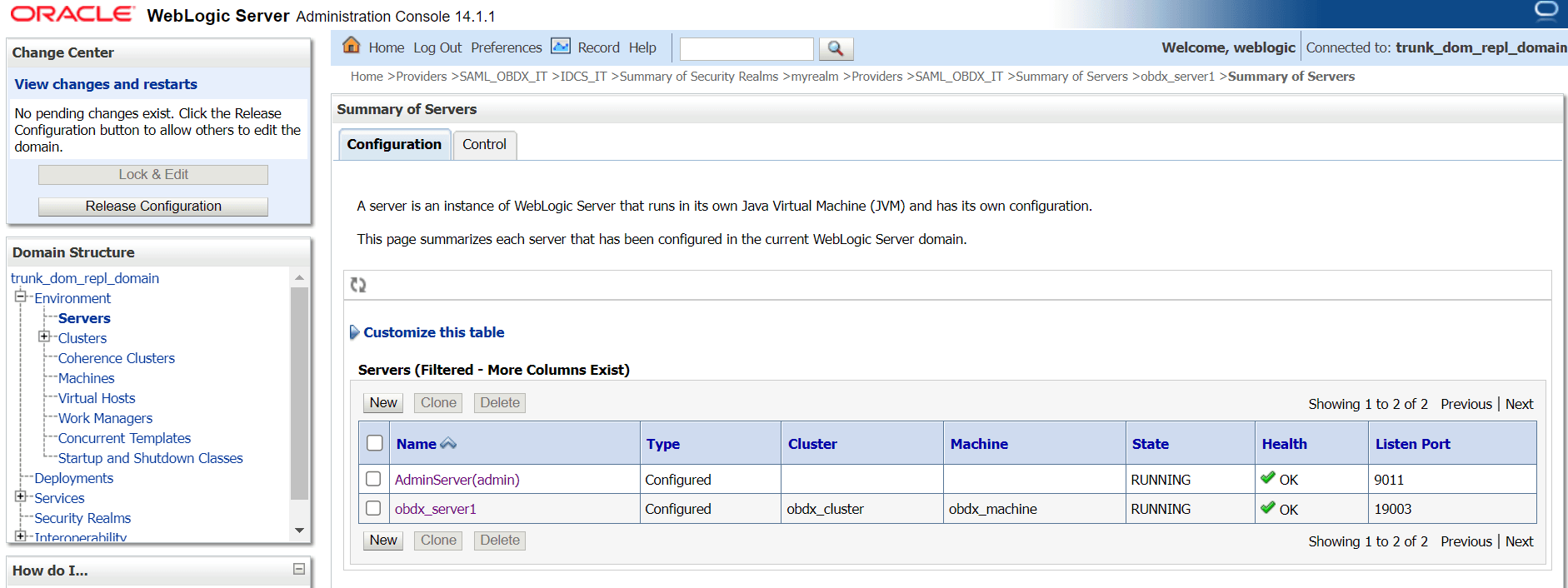
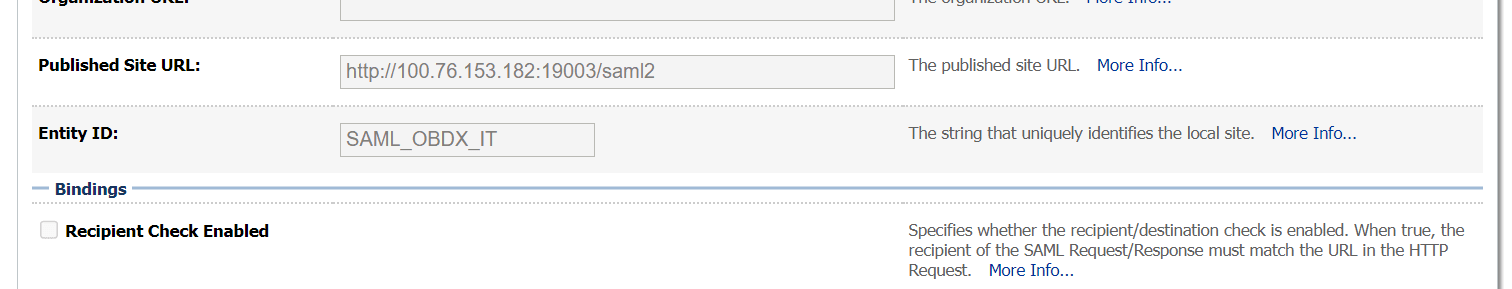
2.2 SAML Authentication Provider configuration
This topic describes the systematic instruction to SAML Authentication Provider configuration option.
Steps to configure SAML Authentication Providers changes into WebLogic console.
Parent topic: Configuration