2.2 Authenticator Application Workspace Setup
This topic describes the systematic instruction to Authenticator Application Workspace Setup option.
- Unzip and navigate to iOS workspace as shipped in installer.
- Open the workspace as shown below and find and replace the following
generated UI files from “ui/dist” folder:
- components
- css
- framework
- images
- pages
- resources
- Double click on OBDXSecureAuthenticator.xccodeproj to open the
project in Xcode.
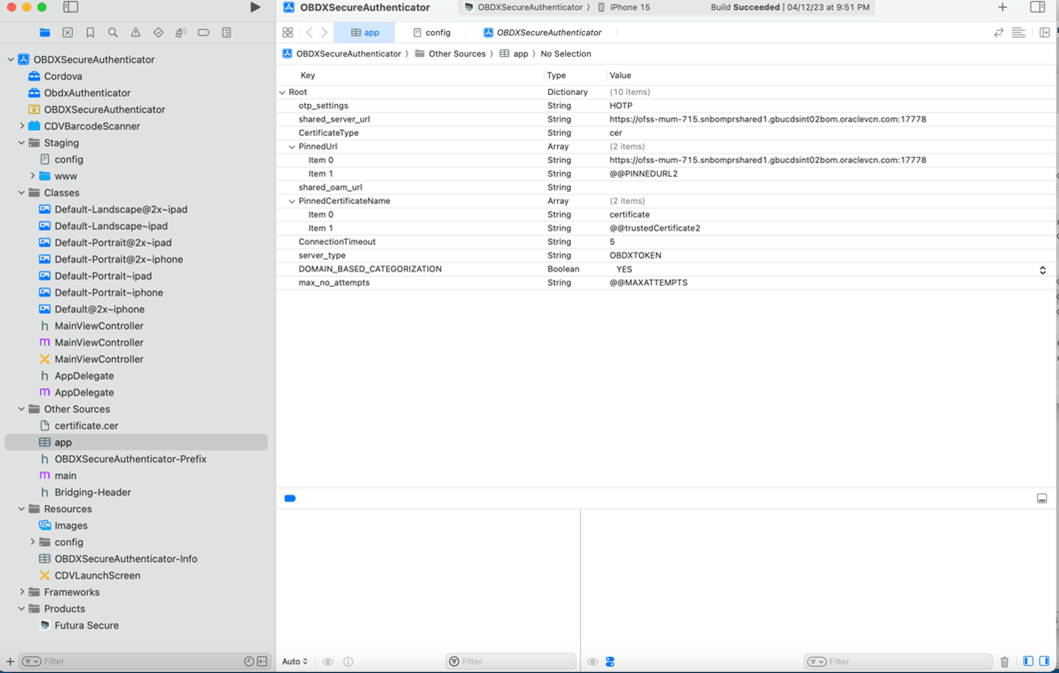
- Update HOTP or TOTP as per Bank’s configured authentication mechanism in above screenshots for “otp-settings” key in “app.plist”. HOTP is for Random Based Soft Token authentication. TOTP is for Time based Soft Token Authentication.
- shared_server_url_url = <bank’s https URL>
- Set value of max_no_attempts to value greater than 0.
Server_type - OBDXTOKEN. Do not change this.
- DOMAIN_BASED_CATEGORIZATION – YES. Do not change this.
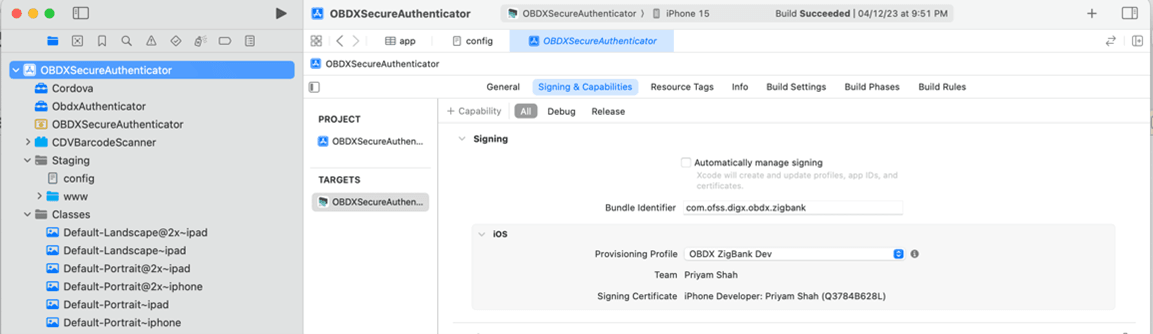
- Create certificates and profiles on Apple Developer account. Use the bundle identifier in project settings and select appropriate profile in the application
- Bundle identifiers need to be added in the Info.plist of each the frameworks
- For example, let us assume that the bundle identifier used is
abc.def.ghi.jkl. The steps to be followed are,
- Right click on ObdxAuthenticator.xcframework(in Xcode’s Project Navigator) → Show in Finder
- When the Finder directory click on ios-arm64 folder → ObdxAuthenticator.framework.
- Open Info.plist and set Bundle identifier as abc.def.ghi.jkl.ObdxAuthenticator
- Follow same for Cordova.xcframework and set Bundle identifier for Cordova.framework: abc.def.ghi.jkl.Cordova
- Also, set the identifiers and select appropriate profile in the target → Signing & Capabilities tab as show below:
- The application contains frameworks for devices and simulator both. Run the application directly on simulator without copying any other additional frameworks.
- For SSL pinning settings follow section 2.4_Using_SSL_in_Authenticator_App. Note: SSLPinning will get enabled after setting the certificate and Pinned URL. There is no additional flag to enable disable SSLPinning. It is expected to have a valid SSL certificate on the server. This certificate needs to be issued from an authorized authority. Self-signed SSL certificates are by default rejected by Apple OS.
- The application can be archived using steps in section: Archiving Authenticator Application for running on device.
- For production application, it is recommended to disable “NSAllowsArbitraryLoads” in “OBDXSecureAuthenticator-Info.plist”.
- InspectableWebView property is set to false in config.xml for production ready
application.
- App icons, splash images are updated.
- Update App Icons, Splash Images in the workspace as per bank’s
requirement.
Parent topic: OBDX Authenticator Application (Futura Secure)