Update General Details
- SMS Authentication & Authorization – This option is selected by default.
- LDAP Authentication & SMS Authorization - Ensure that the LDAP Servers are up and running if you select this option. You can configure multiple LDAP Servers here. While logging into the OFSAA instance, you can select the appropriate LDAP Server to process the authentication requests.
- SSO Authentication & SMS Authorization - Ensure that the SSO Server is configured if you select this option.
- SSO Authentication (SAML) and SMS Authorization
- Specify the configuration details as tabulated: The following table describes the fields in the Configuration Window.
Table 15-12 Fields in the Configuration window and their Descriptions
Field Description Number of invalid logins This field is not applicable if you select the SSO Enabled check box.
Enter the number of attempts permitted to a user to enter incorrect passwords after which the user account will be disabled.
Path for Application Packaging Enter the Application Packaging path where the JSPs generated in DEFQ are saved. Session Timeout Value (in minutes) Enter the permitted duration of inactivity after which the session will be automatically timed out and the user will be requested to login again.
Note:
- The session time out depends on the specified Session Timeout Value and Web Server Internal Session Maintenance. It may vary for different web servers.
- If SSO authentication is selected, ensure you set the Session Timeout Value equivalent to the configured server session time to avoid improper application behavior after the session expires.
Session Timeout Popup Interval (in minutes) Enter the time in the session at which a popup must appear and display a timer that shows the time remaining for the session to end.
For example, if you enter 50 minutes to the Session Timeout Value and enter 5 minutes to the Session Timeout Popup Interval, the popup appears on the screen after 45 minutes of inactivity and displays the timer (starts from 5 minutes and ends at 0) for the session timeout.
Environment Details Enter the System Environment Details such as Development, UAT, Production, and so on. The information is displayed in the Application’s top banner as the “In Setup” information. SSO Enabled Select this check box to enable SSO Authentication & SMS Authorization.
Note: If SSO is enabled, then you must configure the SSO URL for Referer Header Validation.
For more information, see the Configure Referer Header Validation Section in the OFSAA Security Guide.
Enable native authentication for REST API Select to enable Token-based Authentication for the REST APIs to authenticate the password.
For more information, see the Using REST APIs for User Management from Third-Party IDMs Section in the Oracle Financial Services Advanced Analytical Applications Infrastructure Administration Guide.
If SSO Enabled checkbox is selected: Authentication Type The options displayed for Authentication Type are:
- SSO Authentication and SMS Authorization
- SSO Authentication (SAML) and SMS Authorization
Note:
For more information about IDCS for SAML Integration, see https://docs.oracle.com/en/cloud/paas/identity-cloud/uaids/add-saml-application.html.SSO Method This field is displayed only if you have selected Authentication Type as SSO Authentication and SMS Authorization.
Select the required SSO Method. These methods are to specify how the User ID must be passed from the SSO Engine.
- HTTP Request Header - Returns the value of the specified request header as a string from the server. If selected, you need to specify the header value in the SSO Header Value Field.
For example, SM_USER and iv-user header values are supported in OAM.
- HTTP Request Remote User - Returns the login details of the User who is requesting access to the application remotely.
- HTTP Request User Principal - Returns a “java.security.Principal” object containing the name of the Current Authenticated User.
SSO Logout URL This field is displayed only if you have selected Authentication Type as SSO Authentication and SMS Authorization.
Enter the URL of the page to invalidate SSO Session.
SSO Redirect URL Enter the URL of the page to which the user must be redirected after the SSO Session is invalidated.
This field is displayed only if you have selected Authentication Type as SSO Authentication and SMS Authorization.
OFSAA as Service Provider This field is displayed only if you have selected Authentication Type as SSOAuthentication (SAML) and SMS Authorization.
Select this check box if you want to register OFSAA as the service provider. If the check box is not selected, OFSAA will act as a One-way SAML Authentication. That is, OFSAA will only assert the identity.
For more details on how to register OFSAA as Service Provider, see SSO Authentication (SAML) Configuration Section in the OFSAAI Administration Guide.
Identity Provider URL Identity Provider URL This field is displayed only if you have selected the OFSAA as Service Provider check box.
Enter the IDP SingleSignOnService URL in the Identity Provider URL Field.
Note:
- Enter the fully qualified domain URL used to access the Identity Provider.
- This is an optional field and only required if IDP URL for login and logout are different. In case this field is not configured then “Identity Provider URL” will be used for both login and logout requests.
- The following is an example for IDCS: https://<IDCS_URL>/fed/v1/idp/sso
SAML User Attribute This field is displayed only if you have selected Authentication Type as SSOAuthentication (SAML) and SMS Authorization.
Enter the user attribute name, which is used to pass User ID in SAMLResponse. If this parameter is not set, the user will be retrieved from attribute “Subject” by default.
SAML Certificate Absolute Path This field is displayed only if you have selected Authentication Type as SSOAuthentication (SAML) and SMS Authorization.
Enter the absolute path where the SAML Certificate from Identity Provider is stored, which is required for SAML Assertion. If this parameter is not set, the signature from SAMLResponse will not be verified.
SAML Logout URL This field is displayed only if you have selected Authentication Type as SSOAuthentication (SAML) and SMS Authorization.
Enter the URL of the SAML Logout Page to be called on logout operation.
SAML Request Binding This field is displayed only if you have selected Authentication Type as SSO Authentication (SAML) and SMS Authorization.
Select to use SAML Binding to transport messages within the URL.
Generate Logout Request This field is displayed only if you have selected Authentication Type as SSO Authentication (SAML) and SMS Authorization.
Select to generate a SAML Request for logout. Deselect this field to direct users to the URL specified in the SAML Logout URL Field for logout.
Sign Authentication and Logout Request This field is displayed only if you have selected Authentication Type as SSO Authentication (SAML) and SMS Authorization.
Select this field and the following fields appear, which provide capabilities to generate signed SAML Requests:
- Private Key
- X509 Certificate
- Signature Algorithm
Note:
We recommend that you use the PKCS#8 format. Do not protect the key with any passphrase.Private Key Update this field with the private key used to sign the SAML Request. X509 Certificate Update this field with the certificate to sign the SAML Request. Update the sp_metadata.xml file with the same certificate.
For more information, see the SAML Service Provider Metadata Configuration with Certificate Section in the OFSAAI Administration Guide.
Signature Algorithm Enter the URI of the algorithm. The following are a few examples from w3.org:
- http://www.w3.org/2001/04/xmldsig-more#rsa-sha256
- http://www.w3.org/2001/04/xmldsig-more#rsa-sha224
- http://www.w3.org/2001/04/xmldsig-more#rsa-sha384
- http://www.w3.org/2001/04/xmldsig-more#rsa-sha512
NOTE: If you leave this field blank, the system applies the default signature RSA-SHA256.
Authentication Type Select the required authentication type from the drop-down list. The options are :
- SMS Authentication and Authorization
- LDAP Authentication and SMS Authorization
When you select Authentication Type as LDAP Authentication and SMS Authorization, the LDAP Server Details popup is displayed. For more details, see LDAP Server Details.
JIT Provisioning Enabled Select to enable Just in time (JIT) provisioning which synchronizes the User, Group, and User-Group mapping in external systems such as LDAP, SAML, and SSO into OFSAA when a User logs in.
Note:
- JIT Provisioning is available on 8.1.1.2.0 and later versions. However, to enable it in the 8.1.1.1.0 version, apply the 33067589 One-Off Patch from My Oracle Support.
- JIT Provisioning is available on 8.1.2.0.0 and later versions. However, to enable it in the 8.1.2.0.0 version, apply the 34019691 One-Off Patch from My Oracle Support.
- JIT Provisioning is available on 8.1.2.1.0 version and further Maintenance Releases.
- Update the Group Domain Mapping in OFSAA when you create in LDAP, SAML, or SSO.
- Configure the User Group Details in the LDAP Group Details Section if you select LDAP.
- For SAML, configure the attribute name user_groups for IDCS.
- For SSO, send the mapped groups in the header with the user_groups key.
- For SAML, configure the following attributes:
- user_groups
- user_email
- user_name
- For SSO, configure the following headers:
user_groups (To add more than one User Group, specify the User Groups separated by commas.)
- user_email
- user_name
Enable JIT Unmapping Operation Before you select this check box in the UI, ensure that the JIT Provisioning Enabled check box is selected to establish a connection with the External System.
Select to enable the unmap operation of the User Groups from the External System to OFSAA during login.
Note:
- JIT Provisioning is available on 8.1.1.2.0 and later versions. However, to enable it in the 8.1.1.1.0 version, apply the 33067589 One-Off Patch from My Oracle Support.
- JIT Provisioning is available on 8.1.2.0.0 and later versions. However, to enable it in the 8.1.2.0.0 version, apply the 34019691 One-Off Patch from My Oracle Support.
- JIT Provisioning is available on 8.1.2.1.0 version and further Maintenance Releases.
Enable Group Creation during JIT Provisioning
Note:
This is not a field in the UI, it is a Parameter added to the Configuration Table in the database.Before you perform this operation in the database, ensure that the JIT Provisioning Enabled check box is selected to establish a connection with the External System.
Set the JIT_IS_GRP_CRT_ENABLED Parameter Value to Y in the Configuration Table in the database to enable the Creation of Groups during the JIT Provisioning.
The default value is N.
After setting the value to Y, commit and restart the Servers.
NOTE:
- JIT Provisioning is available on 8.1.1.2.0 and later versions. However, to enable it in the 8.1.1.1.0 version, apply the 33067589 One-Off Patch from My Oracle Support.
- JIT Provisioning is available on 8.1.2.0.0 and later versions. However, to enable it in the 8.1.2.0.0 version, apply the 34019691 One-Off Patch from My Oracle Support.
- JIT Provisioning is available on 8.1.2.1.0 version and further Maintenance Releases.
Allow user to login from multiple machines Select the check box to allow concurrent user login. Allow Data Redaction Select the check box to enable Data Redaction. For more details, see the section Data Redaction in the OFS AAI Administration Guide. Encrypt Login Password This field is not applicable if you have selected the SSO Enabled check box.
Select the check box to encrypt the login password for more protection.
Note:
For LDAP Authentication and SMS Authorization, this check box should not be selected.Enable CSRF Protection Select this check box to enable protection for the Cross Site Request Forgery (CSRF) in the application. Hierarchy Security Type Select the hierarchy security node type from the drop-down list. The available options are:
- Group-Based Hierarchy Security
- User-Based Hierarchy Security
Depending on the selection, the user/ group details are displayed in the Hierarchy Security Window.
Allowed Email Domains Enter the email domains that you want to allow. Enter multiple domains with comma-separated values if you want to allow more than one domain.
For example: oracle.com, oci.oracle.com
During User Creation in the User Definition (add mode) Window, you can add only Email IDs that belong to the allowed domains.
Dormant Days This field is not applicable if you have selected the SSO Enabled check box.
Enter the number of inactive days permitted after which the user is denied accessing the system.
Inactive Days This field is not applicable if you have selected the SSO Enabled check box.
Enter the number of inactive days permitted after which the user access permissions are removed and the delete flag status is set as “Y”.
Ensure that the number of Inactive days is greater than or equal to Dormant Days.
Note that, the user details still exist in the database and can be revoked by changing the status flag.
Working Hours This field is not applicable if you have selected the SSO Enabled check box.
Enter the working hours (From and To) to restrict the user from logging in to the system within the specified time range. The time is accounted for in 24 hours and in hh:mm format.
Frequency of Password Change This field is not applicable if you have selected the SSO Enabled check box.
Enter the number of days after which the login password will expire, and the user will be navigated directly to the Change Password Window.
Password History This field is not applicable if you have selected the SSO Enabled check box.
Enter the number of instances the old passwords need to be maintained and the user will be restricted not to use the same password again. A maximum of the last 10 passwords can be recorded.
Password Restriction This field is not applicable if you have selected the SSO Enabled check box.
Select one of the following options:
- Restricted - To impose additional rules and parameters for users while defining a password.
- Un Restricted - To allow users to define any password of their choice ensuring that the password is alphanumeric without any special characters.
Disclaimer Text Enter any disclaimer information that you want to make available for the users of the application on the Login Window. These fields are displayed only if you select the Restricted option for Password Restriction. Specify the following password restriction parameters:
- Password Length - Enter the minimum and maximum characters permitted for setting a password. The default range is between 6 and 20 characters.
- Numbers - Enter the minimum and maximum numeric characters permitted.
- Upper Case - Enter the minimum and maximum numbers of upper case characters that are permitted.
- Lower Case - Enter the minimum and maximum numbers of lower case characters that are permitted.
- Special Characters Occurrence Allowed - Select the check box if special characters are allowed in passwords.
- Special Character - Enter the minimum and maximum numbers of special characters that are permitted.
- Special character occurrence Frequency - Enter the number of times the same special character can occur in the password.
- Disallowed Special Characters - Enter the special characters (without spaces) which are not permitted in a password.
- Running Alphabets - Select the check box to allow running alphabets in a password. For example, abc, xyz, AbC, and so on.
- Sequence Of Running Alphabets- Enter the number of times the sequence is permitted.
- Running Numbers - Select the check box to allow running numbers in a password. For example, 123, 456, and so on.
- Sequence Of Running Numbers- Enter the number of times the sequence is permitted.
Email Notification Email Notifications can be sent based on the following:
- Enable batch operation notification: Notifications are sent to all users mapped to the batch monitor functionality.
- Enable batch owner notification only: Notification is sent to the user who executes the batch.
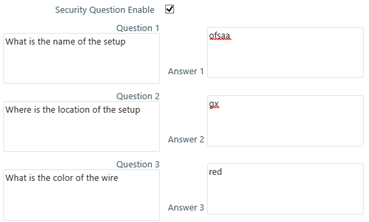
Security Question Enable Select to enable security questions that users would have to answer before they can reset their passwords. This feature enhances user authenticity validation. Enter information for the following fields:
- Question 1 – Enter the first question to be displayed on the Password Reset Page.
- Answer 1 – Enter the answer to the first question.
- Question 2 - Enter the second question to be displayed on the Password Reset Page.
- Answer 2 – Enter the answer to the second question.
- Question 3 - Enter the third question to be displayed on the Password Reset Page.
- Answer 3 – Enter the answer to the third question.
The following illustration is an example:
Figure 256: Security Question Enable Pane
Figure 15-22 Security Question Enable Pane
- Click Save and save the general tab details.