Configuring Single Sign-On
You can determine to use the Single Sign-On feature by setting the common profile switch in Oracle Argus console.
To configure Single Sign-On:
- Go to
Argus Console > System Configuration > System Management (Common Profile Switches). - From the list of switches in the left navigation pane, click Single Sign-On.
- Check the Enable Single Sign-On checkbox.
- Enter the Single Sign-On HTTP Header that the Oracle Argus application uses for authentication.
This field can contain a maximum of 40 characters.
- (Optional) Enter the Single Sign-On Logout URL.
- Click Save.
Modules that uses Single Sign-On feature:
The following table lists dialog boxes in the Oracle Argus Application that require passwords. In such cases, the system Single Sign-On feature redirects the password to Oracle Argus for validation. When single sign-on is enabled, the system locks the user account if the user enters an incorrect password three consecutive times. You must then unlock the account to enable the user to log in to the application.
| Function | Section | Procedure |
|---|---|---|
|
Case Locking |
Activities|Lock |
Locking a case |
|
Case Unlocking |
Activities|Lock |
Unlocking a case |
|
Case Closing |
Activities|Close |
Closing a case |
|
Case Unclosing |
Activities|Close |
Unclosing a case. |
|
Case Unblinding |
General|Blinding Status |
Breaking a blind |
|
E2B Incoming Accept |
Reports|Incoming E2B Reports |
Accepting E2B Reports |
|
E2B Incoming Reject |
Reports|Incoming E2B Reports |
Rejecting E2B Reports |
|
E2B Incoming Follow-up Accept |
Reports|Incoming E2B Reports |
Accepting E2B Follow-up Reports |
|
E2B Incoming Follow-up Reject |
Reports|Incoming E2B Reports |
Rejecting E2B Follow-up Reports |
|
E2B Incoming Nullification Accept |
E2B Incoming Nullification Accept |
Accepting E2B Nullification Reports |
|
E2B Incoming Nullification Reject |
E2B Incoming Nullification Reject |
Rejecting E2B Nullification Reports |
|
LAM Incoming |
Local Affiliate Incoming Review |
Accepting an Affiliate Event |
|
Workflow Routing |
Workflow Routing on Password on Route |
Workflow Routing on Password on Route |
The following modules do not use the Single Sign-On feature:
- Oracle Argus Safety Services
- Oracle Argus Interchange Services (ESM)
- Oracle Argus Interchange Mapping (ESM Mapping Utility)
Configuring Single Sign-On re-authentication
You can also configure Single Sign-On re-authentication. Make sure that the Service Provider IDM (for example, Oracle Access Manager) supports Re-Authenticate URL and sets the last re-authentication header every time a user is re-authenticated.
When configured, re-authentication is performed for critical activities, which requires user to re-authenticate to perform the operation.
To configure Single Sign-On re-authentication:
- Go to
Argus Console > System Configuration > System Management (Common Profile Switches). - From the list of switches in the left navigation pane, click Single Sign-On.
- Check the Enable Single Sign-On checkbox.
- Check Enable Re-Authentication checkbox.
- Make sure the Open Access Manager option is
selected.
WARNING:
DO NOT select the Open ID Connect option.The Open ID Connect configuration for re-authentication will be available in the future release. It will also include the Authority URL, Redirect URI, Authorization Endpoint, Token Endpoint, Client ID, and Client Secret configuration parameters.
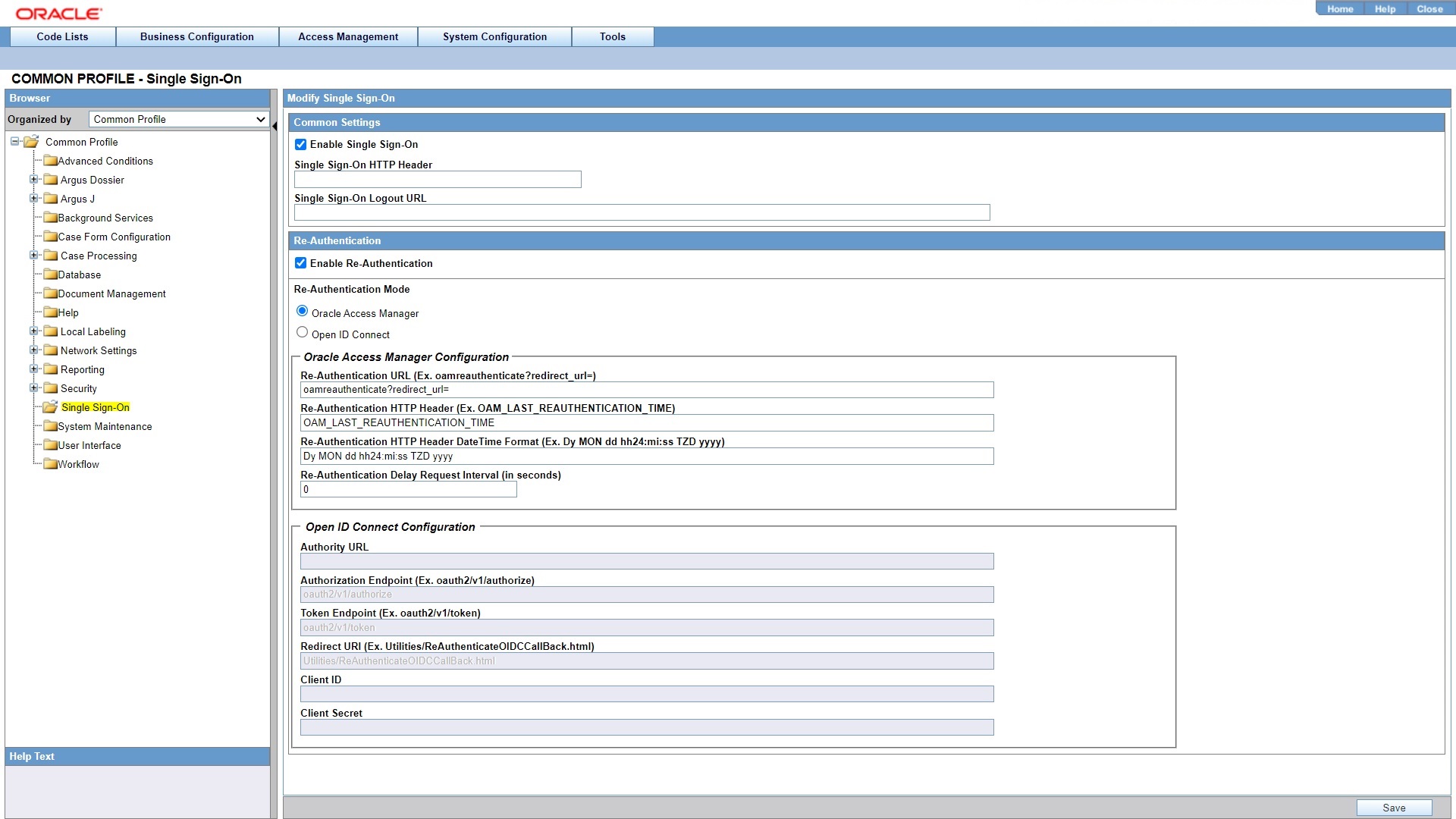
- Enter the followinf fields, and click Save.
- Re-Authentication URL—Enter the re-authentication URL of
the corporate LDAP system. The URL must be in the following format:
(for example,<protocol>://<hostname>:<port>/oamreauthenticate?redirect_url=https://acme.idm.com:8787/oamreauthenticate?redirect_url=). - Re-Authentication HTTP Header—Auto-populated by default.
The default setting is
OAM_LAST_RE-AUTHENTICATION_TIME. - Re-Authentication HTTP Header Date Time
Format—Auto-populated by default. The default setting is
Dy Mon dd hh24:mi:ss TZD yyyy.
- Re-Authentication URL—Enter the re-authentication URL of
the corporate LDAP system. The URL must be in the following format:
If re-authentication is enabled, user association with LDAP is not required, and you can configure Oracle Argus Safety users without providing LDAP details.
Single Sign-On re-authentication has the following impact on the LDAP
settings at the user configuration level, which you can access under
Console > Access Management > Argus > Users:
- The Enable LDAP Login checkbox is available,
if either LDAP is enabled at the system level (under
Argus Console > System Configuration > System Management > Security > LDAPnode), or Single Sign-On re-authentication is enabled. If neither is enabled, then the checkbox is disabled. - The LDAP Server Alias drop-down list is disabled and blank when the Enable Re-Authentication checkbox is checked.
- If both re-authentication and LDAP are configured, then priority is given to re-authentication.