Object Security Elements
The Oracle LSH security system is based on objects subtypes, roles, user groups, and user accounts. Object types and the "Default" object subtype for each object type are predefined. Defining additional object subtypes is optional. You must define all the other elements. Instructions are included in "Setting Up the Security System" in the Oracle Life Sciences Data Hub System Administrator's Guide. The elements are described in the following sections:
Figure 4-1 Logical Representation of the Object Security Elements and Their Relations
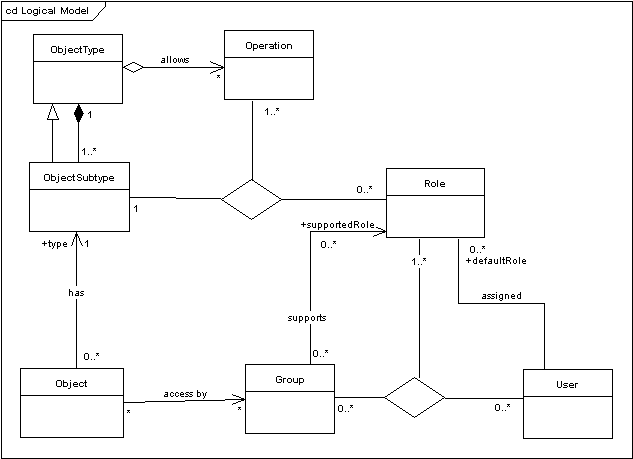
Description of "Figure 4-1 Logical Representation of the Object Security Elements and Their Relations"
As shown in the above diagram, object security elements have the following relations:
- Each object type defines which operations can be performed on objects of that type.
- Each object type must have at least one object subtype.
- Object subtypes inherit characteristics from object types (namely allowed operations).
- Each object is of one and only one subtype.
- A role specifies which operations can be performed on an object of a given subtype by a user with that role (in a user group assigned to the object).
- User groups support roles.
- A user is assigned to a user group by assigning him or her to one or more supported roles in the user group.
- User groups are assigned to objects and users gain access to an object through one or more user groups assigned to the object. The operations they can perform on an object depend on the roles they have in user groups assigned to the object.
Parent topic: Designing a Security System