4. Additional Configurations for Federated Users
Custom Attribute Mapping
Note:
Editing the list of supported attributes is only recommended for administrators who have customized the schema of their applications and systems and have first-hand knowledge of how their custom attributes are defined or if a source attribute does not automatically appear in the Microsoft Entra ID admin center UI. This sometimes requires familiarity with the APIs and developer tools provided by an application or system. The ability to edit the list of supported attributes is locked down by default, but customers can enable this capability by navigating to the following URL: https://portal.azure.com/?Microsoft_AAD_Connect_Provisioning_forceSchemaEditorEnabled=true.- Open a new browser tab and access the URL : https://portal.azure.com/?Microsoft_AAD_Connect_Provisioning_forceSchemaEditorEnabled=true
- Navigate to the previously created Enterprise Application.
- In the left menu under Manage, click Provisioning and then click Edit Provisioning.
- Under Provisioning, select Mappings, and then select Provision Microsoft Entra ID Users.
- Select the Show advanced options check box at the bottom of the Attribute Mapping screen, and then select Edit attribute list for OracleIDCS.
- Add a new entry for the mandatory custom attribute:
Name: urn:ietf:params:scim:schemas:idcs:extension:custom:User:OC_PrimaryWorkLocation
Type: String
Note:
Optionally, you can also refer to the Table 2-1 User Mappings and add other Custom attributes that are not already listed on the Edit Attribute List page.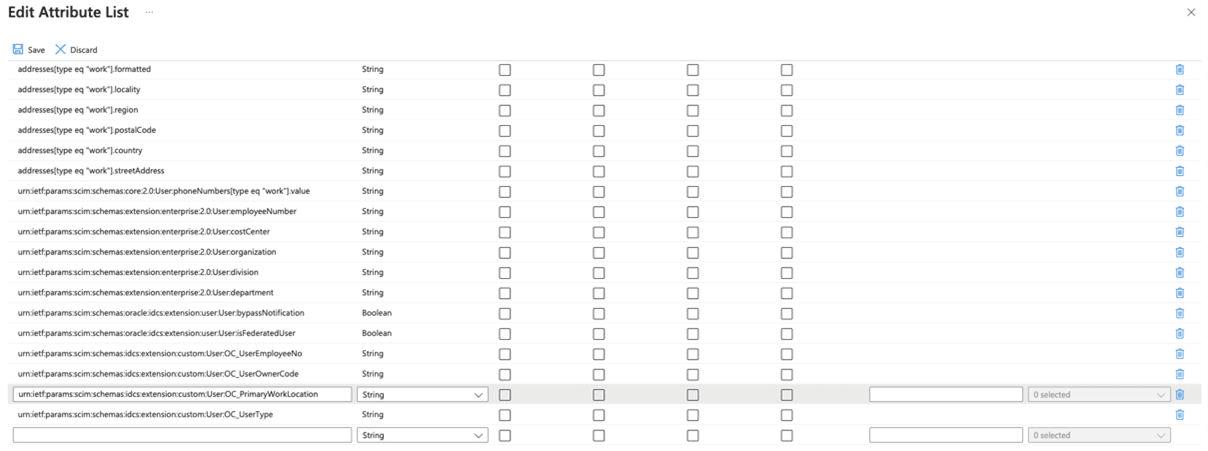
- Save the User Attribute list and close the browser tab.
User Attribute Mapping
- In another browser tab, log in to Microsoft Azure.
- Click Microsoft Entra ID.
- In the left menu, click Enterprise applications.
- Click the application you created earlier: Oracle Cloud Infrastructure Console.
- In the left menu under Manage, click Provisioning and then click Edit Provisioning.
- In the Provisioning page, click Mappings.
- Under Mappings, click Provision Microsoft Entra ID Users.
- Under Attribute Mappings, scroll down and click Add New Mapping.
Note:
- In Entra User mapping, keep only the mappings shown in the below table and remove all other mappings.
- If you cannot find the target attribute in the User Mapping in Entra, refer to the ‘Custom Attribute Mapping’ section to add the target attribute.
- Save the User Attribute Mappings and return to the Provisioning page.
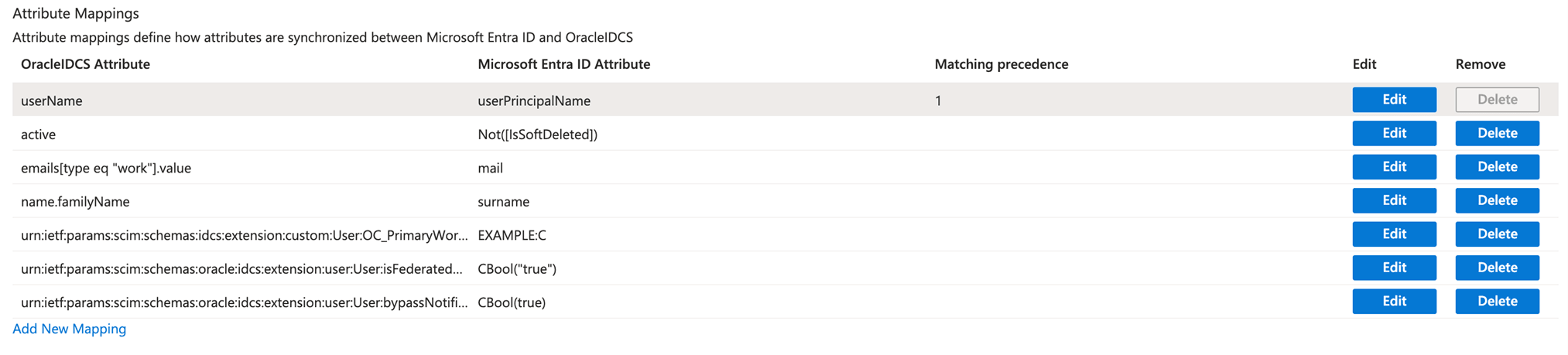
Table 2-1 User Mappings
| Entra ID User Attribute Name | OCI IAM Domain User Attribute Name | IAM Domain Attribute Type | Mapping Type | Value | Description | Mandatory |
|---|---|---|---|---|---|---|
|
userPrincip alName |
userName |
String |
Direct |
N/A |
Username |
Yes |
|
surname |
name.famil yName |
String |
Direct |
N/A |
Lastname |
Yes |
|
|
emails[type eq "work"].val ue |
String |
Direct |
N/A |
Email address |
Yes |
|
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_Primar yWorkLoca tion |
String |
Constant |
<ENTERPRI SE_ID >:E or <CHAINCO DE>:C |
Mandatory Single Valued User Attribute. Indicates the User’s primary work location. Primary Work Location can have values <ENTERPRI SE_ID >:E for multi- chain customers derived from the User profile. For customers having only a single chain, the source value can be set to constant <CHAINCO DE>:C for all users. |
Yes |
|
|
CBool(true) |
urn:ietf:par ams:scim:sc hemas:orac le:idcs:exte nsion:user: User:isFede ratedUser |
Boolean |
Expression |
CBool("true ") |
Enable Federated User flag in Identity Domain. |
Yes |
|
CBool(true) |
urn:ietf:par ams:scim:schemas:orac le:idcs:exte nsion:user: User:bypass Notification |
Boolean |
Expression |
CBool("true ") |
The bypass notification flag controls whether an email notification is sent after creating or updating a user account in Identity Domain. The bypassNotif ication must be set to "true" for Federated users. This disables us er account activation notification in IAM Identity Domain for the user. |
Yes |
|
active |
active |
String |
Expression |
Not([IsSoftDeleted]) |
User status. The attribute IsSoftDelete d is often part of the default mappings for an application in Entra ID. It is not recommen ded to remove the IsSoftDelete d attribute from your attribute mappings. |
Yes |
|
givenName |
name.given Name |
String |
Direct |
N/A |
Firstname |
No |
|
perferredL anguage |
preferredL anguage |
String |
Direct |
N/A |
User's preferred writtenor spoken language usedfor localized user interfaces. |
No |
|
displayName |
displayName |
String |
Direct |
N/A |
The display name. |
No |
|
jobTitle |
title |
String |
Direct |
N/A |
Title |
No |
|
mobile |
phoneNumbers[type eq "mobile"].value |
String |
Direct |
N/A |
User's mobile phone number. |
No |
|
extensionAt tributeUser OwnerCode |
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_UserOw nerCode |
String |
Direct |
N/A |
Unique code (typically, the sales manager's initials) for the owner. For example, oc_ownercode=First_Last_Initial. |
No |
|
employeeId |
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_UserEmployeeNo |
String |
Direct |
N/A |
Numeric or alphanumeric identifier assigned to a person, typically based on order of hire or association with an organization. |
No |
|
employeeT ype |
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_UserType |
String |
Direct |
Possible Values:
|
Used to identify the organization-to-user relationship. |
No |
|
department |
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_Department |
String |
Direct |
N/A |
Specifies the user's department. |
No |
|
telephoneN umber |
phoneNumbers[type eq "work"].value |
String |
Direct |
N/A |
User's work phone number. |
No |
|
extensionAt tributeHon orificPrefix |
name.hono rificPrefix |
String |
Direct |
N/A |
User’s Initials |
No |
|
extensionAt tributeMid dleName |
name.midd leName |
String |
Direct |
N/A |
User’s middle name |
No |
|
extensionAt tributeHon orificSuffix |
name.hono rificSuffix |
String |
Direct |
N/A |
Suffix |
No |
|
extensionAt tributeTime zone |
timezone |
String |
Direct |
N/A |
User's timezone |
No |
|
extensionAt tributeLocale |
locale |
String |
Direct |
N/A |
Used to indicate the User's default location for purposes of localizing items such as currency, date and time format, numerical representations, and so on. |
No |
|
extensionAt tributeActAs |
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_ActAs |
String |
Direct |
Possible Values:
|
OPERA Cloud attribute. Determines the Originating Application value in Blocks and Manage Block (see Managing Blocksin the OPERA Cloud User Guide) referenced by the Origin list field in Group Rooms Control (see Using Group Rooms Control in the OPERA Cloud User Guide) search and in reports. |
No |
|
extensionAt tributeActAt |
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_ActAt |
String |
Direct |
Possible Values:
|
OPERA Cloud attribute. Determines the Originating Application value in Blocks and Manage Block (see Managing Blocksin the OPERA Cloud User Guide) referenced by the Origin list field in Group Rooms Control (see Using Group Rooms Control in the OPERA Cloud User Guide) search and in reports. |
No |
|
extensionAt tributeHubs |
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_Hubs |
String array |
Direct |
N/A |
Assign one or more hubs (see Configuring Hubs in the OPERA Cloud User Guide) to a user to determine their property location access in multi- property operations. oc_hubs is a String array in IAM Domain and the Identity Provider should map a multi-valued attribute to oc_hubs. Value for oc_hubs must sent in all uppercase. |
No |
|
extensionAt tributeHub sString |
urn:ietf:par ams:scim:sc hemas:idcs: extension:c ustom:User: OC_Hubs_St ring |
String |
Direct |
N/A |
Assign one or more hubs (see Configuring Hubs in the OPERA Cloud User Guide) to a user to determine their property location access in multi-property operations. OC_Hubs_String must be sent in all uppercase as comma separated values. |
No |
Group Attribute Mapping
- Open a new browser tab and access the URL : https://portal.azure.com/?Microsoft_AAD_Connect_Provisioning_forceSchemaEditorEnabled=true
- Navigate to the Enterprise Application previously created.
- In the left menu under Manage, click Provisioning and then click Edit Provisioning.
- Under Provisioning, select Mappings, and then select Provision Microsoft Entra ID Groups.
- Scroll down and select the Show advanced options check box at the bottom of the Attribute Mappings screen and then select Edit attribute list for OracleIDCS.
- Add a new entry for the Description attribute as shown below:
Name: urn:ietf:params:scim:schemas:oracle:idcs:extension:group:Group:description
Type: String
- Save the Group attribute list and close the browser tab.
- In another browser tab, log in to Microsoft Azure and navigate to the Enterprise Application you created earlier.
- In the left menu under Manage, click Provisioning and then click Edit Provisioning.
- Under Mappings, click Provision Microsoft Entra ID Groups. Refer to
the below table to update and add the mappings for Group attributes.
Table 2-2 Group Attribute Mappings
Entra ID Attribute Name IAM Domain Group Attribute Name IAM Domain Attribute Type Mapping Type Value Description Mandatory displayName
displayName
String
Direct
N/A
Group display name
Yes
members
members
String
Direct
N/A
Members of the group
No
objectId
externalId
String
Direct
N/A
External Group Id
No
description
urn:ietf:para ms:scim:sch emas:oracle: idcs:extensi on:group:Gr oup:descript ion
String
Direct
N/A
Group description
No
- Save the Group Attribute mappings.
- Return to the Provisioning page and set the Provisioning Status to “On.”