1 Feature Summary
This chapter describes the feature enhancements in this release.
Noteworthy Enhancements
This guide outlines the information you need to know about new or improved functionality in the Oracle Retail Brand Compliance Management Cloud Service update and describes any tasks you might need to perform for the update. Each section includes a brief description of the feature, the steps you need to take to enable or begin using the feature, any tips or considerations that you should keep in mind, and the resources available to help you.
Note:
Where new fields, User Interface (UI) changes, or glossary entries are introduced as part of a change, the portal owner may need to apply their own translations of the core system text.Column Definitions
-
Feature: Provides a description of the feature being delivered.
-
Module Impacted: Identifies the module impacted associated with the feature, if any.
-
Scale: Identifies the size of the feature. Options are:
-
Small: These UI or process-based features are typically comprised of minor field, validation, or program changes. Therefore, the potential impact to users is minimal.
-
Medium: These UI or process-based features are typically comprised of field, validation, or program changes. Therefore, the potential impact to users is moderate.
-
Large: These UI or process-based features have more complex designs. Therefore, the potential impact to users is higher.
-
-
Delivered: Is the new feature available for use immediately after upgrade or must the feature be enabled or configured? If no, the feature is non-disruptive to end users and action is required (detailed steps below) to make the feature ready to use.
- Customer Action Required: You must take action before these features can be used. These features are delivered disabled and you choose if and when to enable them.
Table 1-1 Noteworthy Enhancements
| Feature | Module Impacted | Scale | Delivered | Customer Action Required? |
|---|---|---|---|---|
|
All |
Small |
Yes |
No |
|
|
Admin |
Medium |
Yes |
Yes |
|
|
Supplier |
Small |
Yes |
No |
|
|
Product |
Medium |
Yes |
Yes |
Text Editor Replacement
The current CK Editor rich text editor component used for formatting text in fields, such as News items and Ingredients lists, is replaced with the Tiny MCE text editor.
JET UI Security
A new JET UI based security administration facility replaces the current ECHO UI Permissions spreadsheet upload, for the new JET UI based screens only.
The new model utilizes the existing method of allocating users combinations of Authority Profiles and Roles to determine their level of access to the application’s functionality (including navigation, actions, and APIs), and its data. The permissions are defined as sets of policies in XML files rather than a spreadsheet of rules.
The core set of default system-delivered security policies can be overridden by the client, with the system administrator having access to a new maintenance facility in the Admin area.
The overrides are applied by uploading XML files containing the custom rules. The files may represent a single rule as part of a simple flat structure, or a group of rules as part of a more complex hierarchical structure.
The enhancement includes the following features:
- The security rules are defined as policies and policy
sets, in XML files, grouped by these policy types:
- Tasks - for controlling access to menu options.
- Filters - for applying filters to data.
- Fields - for controlling access to list view columns and form fields.
- Actions - for controlling access to list view and form actions.
- Redactions - for forming subsets of data, such as to remove associated child data that is not required.
- Decisions - for controlling whether a UI component is shown or hidden.
- A predefined set of combining algorithms determine how
the policies are applied and whether the rule is to permit or deny
access:
- PermitPreferred - If any rules in the policy generate a PERMIT result, then PERMIT is the result. If any rules in the policy generate a DENY result and no rule generates a PERMIT result, then DENY is the result. If no rules are matched, then the result is NO_MATCH. Used for Tasks and Actions.
- DenyPreferred - If any rules in the policy generate a DENY result, then DENY is the result. If any rules in the policy generate a PERMIT result and no rule generates a DENY result, then PERMIT is the result. If no rules are matched, then the result is NO_MATCH. Used for Tasks and Actions.
- LastMatch - The last rule to match is chosen as the result. If there are no matches, the result is NO_MATCH. Used for Tasks and Actions.
- CombineAnd - If one rule is matched, the expression from that rule is the result in a singleton list. If multiple rules are matched, then the expressions from those rules are ANDed together as the result in a singleton list. If no matches are generated, then the result is an empty list. Used for Filters.
- CombineOr - If one rule is matched, the expression from that rule is the result in a singleton list. If multiple rules are matched, then the expressions from those rules are ORed together as the result in a singleton list. If no matches are generated, then the result is an empty list. Used for Filters.
- AllMatch - If any rules are matched, then all are returned as the result list. If no rules are matched, then an empty list is the result. Used for Redactions.
-
The system-delivered core rules may be overridden or extended by client administrators using the new Security Policies maintenance facility. The Security Policy comprises a set of Policy Override records per Policy Type (so up to 6 sets of Policy Overrides). Each Policy Override record is associated to a single Policy Type and Combining Algorithm, and has a single XML file attachment.
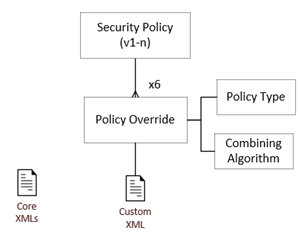
-
The Security Policies list view contains a single Security Policy record which may have multiple versions, of which just one is active. Alternative sets of new draft rules can be maintained, then activated when ready; prior sets of rules can be reverted to, by reactivating a deactivated set.
The custom rules are maintained as Policy Override records within the Security Policy. They act as a container for the XML files which contain the rules in code form. The core system policy rules can be downloaded as a set of XML files, for reference when building custom overrides.
-
The Security Policy form comprises:
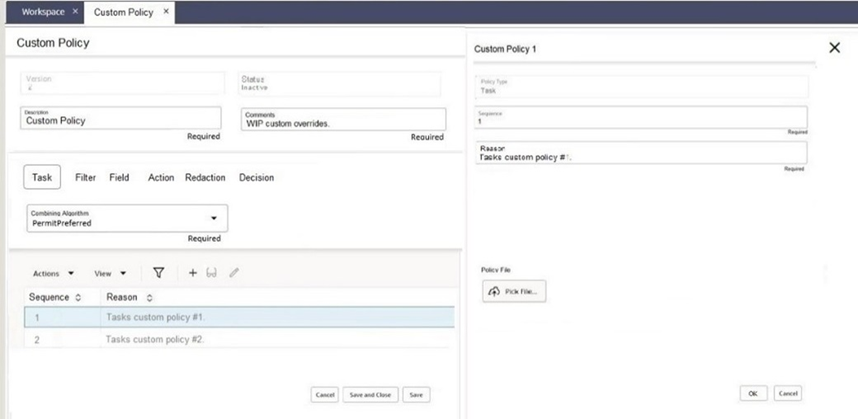
- A set of fields which represent the Security Policy record.
- A set of tabs which represent the fixed set of Policy Types: Task, Filter, Field, Action, Redaction, and Decision.
- A Combining Algorithm selector containing the option available for the policy type.
- A data grid which contains the Policy Override records for the selected policy type tab.
- The actions for maintaining the Policy Override records and exporting the XML file.
- The Policy Override record is a container for the override policy rules XML file. It contains:
- The Policy Type based on the which tab has been selected.
- The Sequence the rules are to be applied.
- A Reason or purpose of the override.
- The Policy File upload/download of a single XML file.
See also Post Release Tasks, and refer to the Security UI appendix in the Oracle Retail Brand Compliance Management Cloud Service Workspace User Guide for further details of administering the JET UI user access permissions.
Auto Prompt for Audit Submission
If the supplier forgets to submit an Audit after completing all open issues, the status is not progressed for the retailer to finalize completion of the Audit.
To avoid such delays, validation is added to the Audit to check if all Issues are Completed, and if so, to prompt the user with an option to set the status to Awaiting Approval, meaning the retailer can then progress the Audit.
The enhancement includes the following features:
- System Parameters: Prompt Supplier to Set to Awaiting Sign Off – enables the prompt for the supplier to set an Audit or Visit to Awaiting Sign Off status. Default is not enabled.
-
Audit Validation: If the system parameter is enabled, validation will be applied when a supplier user (not a retailer user) saves and exits each Issue in an Audit that is currently at In Progress, Awaiting Corrective Action, or Awaiting Amendment status.
The validation will check if all the audit’s Issues have the Completed Date entered. If so, a message will notify the user that all issues are now complete so the audit should be set to Awaiting Sign Off, with an option to change the status accordingly.
See also Post Release Tasks.
Post Launch Section
The Constructed Non Food (CNF) type Product Specification includes a section for Post Launch Information. There are cases where Post Launch information is to be captured for other specification types, and while the CNF Post Launch Information section can be added as an optional section, it cannot be specified as being a mandatory section, so must be manually added to each specification.
Therefore, a Post Launch Information section is introduced for the Food, Formulated Non Food (FNF), and Beers, Wines, and Spirits (BWS) specification types. It is not included for Produce specifications, due to their different workflow and use.
The enhancement includes the following features:
- Glossaries: Results - each specification type has a specific Results glossary.
- Locking Rules: The entire section remains editable in Active specs. The Post Launch Attachments table is locked until the specification is at Active status. The existing CNF default rules are not specification type specific, so also apply to the new Food, FNF, and BWS instances of this section.
- Email Templates: The action of saving the section with Comments entered triggers a notification email to be sent, using email templates HARDGOODS 01 RETAILER and HARDGOODS 01 SUPPLIER. The same email templates are shared by all specification types.
- Specification API and RDS data: The existing tables will include data for all specification types.
- Report Queries: Two new report queries are added which cover the Post Launch Information section for all specification types (including CNF):
- Post Launch Information Inspection Reports - the granularity of this query is the Post Launch Information Inspection Reports table; one row output per row in the Inspection Reports table.
- Post Launch Information Comments - the granularity of this query is the Post Launch Information Comments table; one row output per row in the Comments table.
The new Post Launch Information sections will be data generated in upgraded portals, so that they are available to add to the Spec Type glossaries, but they will NOT be automatically added to the Spec Type glossaries.
Clients who may already be using the CNF Post Launch Section in other specification types may now replace that with the specification-specific sections.
See also Post Release Tasks.
Post Release Tasks & Impact on Existing Installation
The following post release tasks and impact on an existing installation must be taken into account as part of this release.
JET UI Security
If the new Workspace UI is enabled, areas presented in the JET UI have their access controlled by the new Security Policies subsystem. Any custom overrides to the core access rules, including any that have previously been applied using the ECHO Permissions spreadsheet, must be applied using the new method.
See the Oracle Retail Brand Compliance Management Cloud Service Workspace User Guide for details on administering the JET UI user access permissions.
Auto Prompt for Audit Submission
To enable use of the Auto Prompt for Audit Submission feature, set the Prompt Supplier to Set to Awaiting Sign Off system parameter in the Audits tab.
Post Launch Section
To enable use of the Post Launch Information section in Food, FNF, or BWS specifications, configure the following areas:
- The Spec Types glossary to make the section available to the required specification types, and if a mandatory section.
- The contents of the Results glossary for the relevant specification types.
- The Specification Locking and Mandatory Field rules for any overrides to the default rules.
- The HARDGOODS 01 RETAILER and HARDGOODS 01 SUPPLIER Email templates for any overrides to the default templates.
- Any Custom Fields for the Post Launch Info section.
- Any System Text overrides to the default text and language translations.
- Design, build, and schedule any Reports for the Post Launch Information section.
System Text
The fix for help text not displaying (item 35859508) introduces two new System Text records:
view.food.productSpecification.page.olcSection.page.additionalPage.eanBarCodeFs=EAN/Barcode view.food.productSpecification.page.olcSection.page.additionalPage.shippingCaseCodeFs=Shipping Case Code
System text records are added automatically during the release process. Any translation overrides must be added manually by the retailer administrator.
Required Spreadsheet Updates
The Text Editor replacement requires an update to the Branding stylesheet.
- Log in as an Oracle Authorized Administrator User and go to Company > Admin > System Control. Select the Branding menu item to open the Brand page. On the Branding Themes tab, click the orbc-theme.css link to download the file.
- Open the downloaded file in a text editor, and search for the following:
.html-label ul {This should locate a CSS style matching this:
.html-label ul { list-style: disc inside none !important; }This should be updated to match the following:
.html-label ul { list-style-position: inside; } - Next, search for the following:
.html-label ol {This should locate a CSS style matching this:
.html-label ol { list-style: decimal inside none !important; }This should be updated to match the following:
.html-label ol { list-style-position: inside; } - Once the changes are made and saved to your local copy of orbc-theme.css, this needs to be uploaded back to the Branding page.
- In the Branding page, choose the Action > Edit to enable edit mode for the page.
- Click the Choose File button next to the Core Theme which should have orbc-theme.css listed.
- Select the orbc-theme.css file that was amended above and click Open. This should upload the file to the Branding record.
- Select Action > Save & Exit.
- Refresh the browser using F5. The required style sheet should now be in effect.
Enabling Identity Management Notifications
As an IDCS or OCI IAM Administrator, verify that Notifications are enabled in the corresponding Stage / Production tenant.
Enabling User Roles
If they do not already exist, configure the Power User, Account Administrator, Assistant Technologist, and Site Inspector user roles, and assign to the appropriate users.
The instructions for downloading and uploading the amended Permissions spreadsheet are as follows:
-
Log in as an Oracle Authorized Administrator user and go to Company > Admin > Roles & Permissions.
-
Open the Permissions page.
-
Download the active spreadsheet by selecting the row with true in the Active Permissions column, click Download Selected, and save locally.
-
Edit the downloaded spreadsheet, make the changes described above, then save the spreadsheet.
-
Upload the edited spreadsheet by clicking Upload Permissions, select the spreadsheet, and click Ok.
-
Apply the changes by selecting the uploaded spreadsheet row, click Process Selected, and then click Ok to confirm.
Enabling Artwork with SSO
Artwork is not a core Brand Compliance module, but a third-party add-on application. This process enables the integration with the third-party Artwork application, where it is used.
For existing installations that use the Artwork module, in order to configure single sign on (SSO) between Brand Compliance and the Artwork solution (using IDCS or OCI IAM authentication), the following steps must be taken by the Customer or their Partner:
-
Ensure the MYARTWORK external system has been created in Brand Compliance PROD and STAGE.
-
Raise an SR service requesting for creation of the Artwork Application for PROD and STAGE. The call back URLs and IDCS or OCI IAM URLs must be provided in the SR.
-
Once created, you will be able to gather the Client ID and Client Secret from IDCS or OCI IAM.
Refer to the Artwork chapter in the Oracle Retail Brand Compliance Management Cloud Service Administration Guide for the full process for enabling Artwork with SSO.
IDCS Changes
As part of the updates from release 20.0 onwards, there are a few changes into various records within the IDCS configuration. These changes should be considered in instances where you have adopted your own changes and configuration within IDCS.
Oracle Cloud Service Records
This section within IDCS is only accessible to Admin users of the IDCS tenancy. A new Cloud Service record is created for the release 20+ instance and is now named using the following naming structure:
- STAGE: RGBU_BCCS_STG1_BC (from RGBU_BCCS_UAT_PROD_BC)
- PROD: RGBU_BCCS_PRD1_BC (from RGBU_BCCS_PRD_PROD_BC)
- DEV: RGBU_BCCS_DEV1_BC (from RGBU_BCCS_DEV_PROD_BC)
Where the OPAL Artwork is utilized, a new Cloud Service record is created for the release 20+ instance and is now using the following naming structure:
- STAGE: RGBU_BCCS_STG1_ARTWORK (from RGBU_BCCS_UAT_PROD_ARTWORK)
- PROD: RGBU_BCCS_PRD1_ARTWORK (from RGBU_BCCS_PRD_PROD_ARTWORK)
IDCS Group Records
These are created automatically by the Brand Compliance application and the naming of the groups is updated to be aligned with the Oracle Cloud Service record. Standard groups are created for . . . Artwork, . . . BC_User, . . . Reports_Admin, . . . Retailer, and . . . Supplier. For example, RGBU_BCCS_PRD1_BC_User is the new release 20+ group naming structure, RGBU_BCCS_PRD_PROD_BC_User being the previous naming structure.
Note:
When creating new groups within an IDCS tenant, avoid using the RGBU_BCCS_PRD1_ or RGBU_BCCS_STG1_ prefix for the name of groups. Any groups created with either prefix may have their users removed from the group as part of the hourly IDCS sync process.